漏洞概要
关注数(24)
关注此漏洞
漏洞标题:金山KingGate防火墙存在设计缺陷可直接获取权限控制设备(附POC)
提交时间:2015-08-19 15:39
修复时间:2015-11-17 16:22
公开时间:2015-11-17 16:22
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-08-19: 细节已通知厂商并且等待厂商处理中
2015-08-19: 厂商已经确认,细节仅向厂商公开
2015-08-22: 细节向第三方安全合作伙伴开放
2015-10-13: 细节向核心白帽子及相关领域专家公开
2015-10-23: 细节向普通白帽子公开
2015-11-02: 细节向实习白帽子公开
2015-11-17: 细节向公众公开
简要描述:
用户购买设备想获取安全保障,身为安全厂商偏偏给用户带来未知的安全威胁!!!Why?
该设计缺陷新旧版本的KingGate防火墙通杀,开发团队可以正式宣布解散。。
详细说明:

金山旗下"KingGate"硬件防火墙产品存在设计缺陷无需登录情况下可任意添加管理员&任意下载系统配置文件(包含明文账号密码)【新旧版本通杀】
漏洞证明:
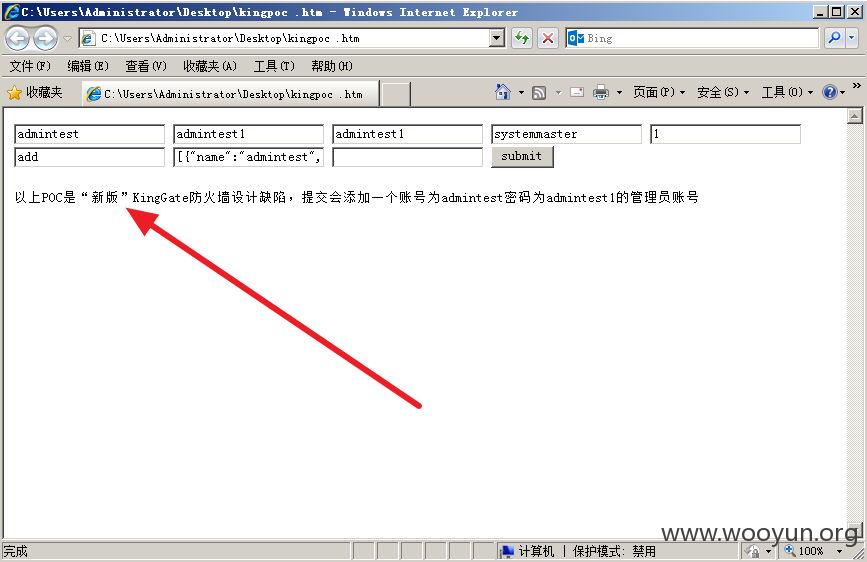
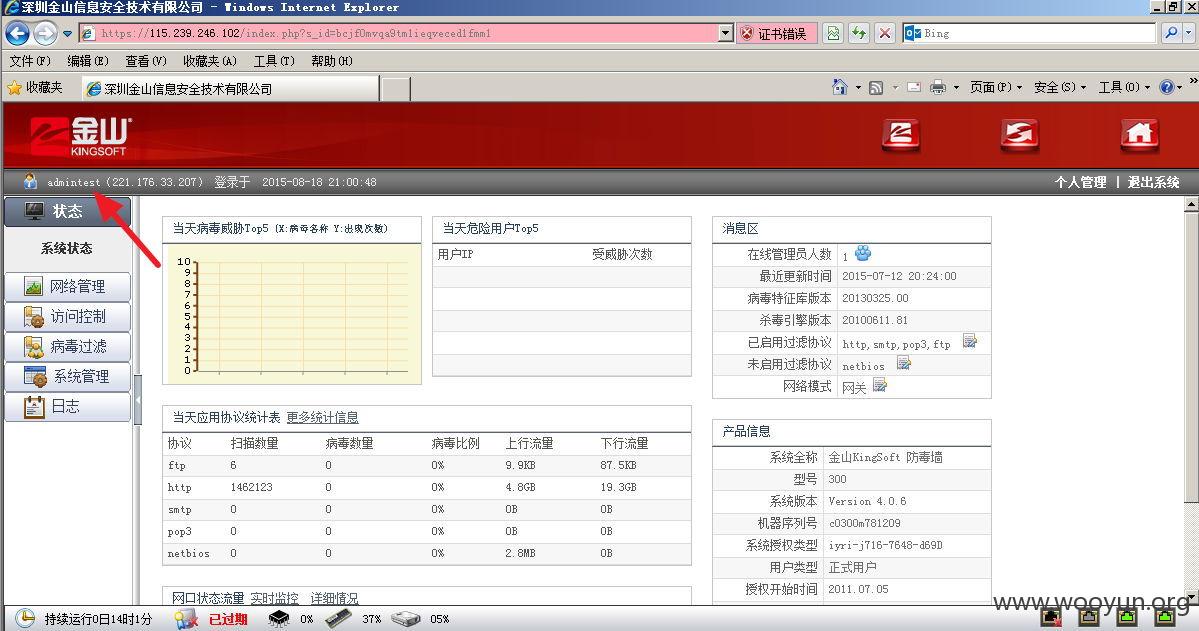
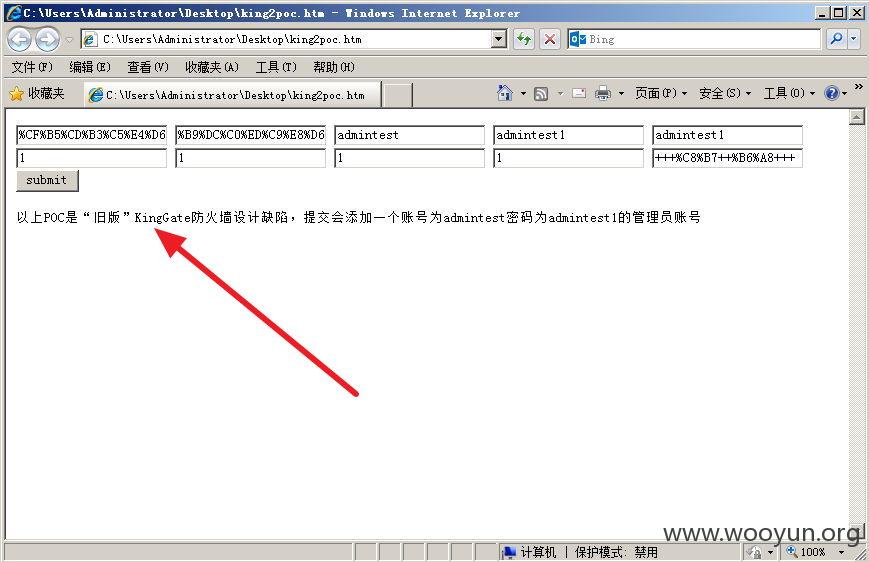
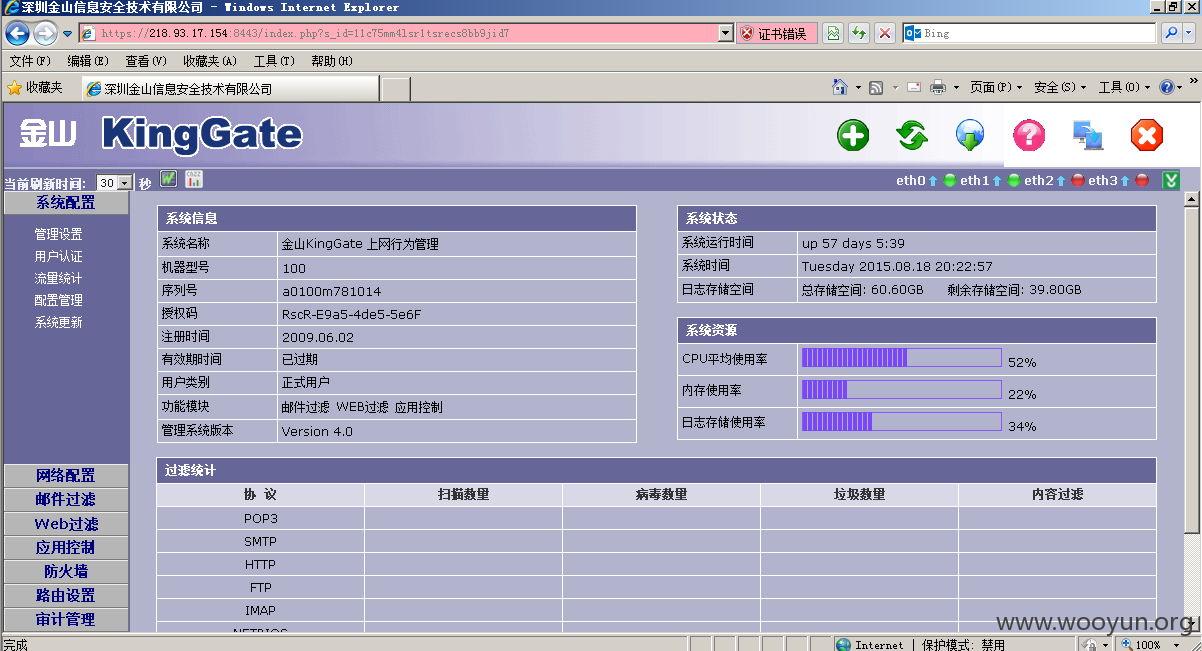
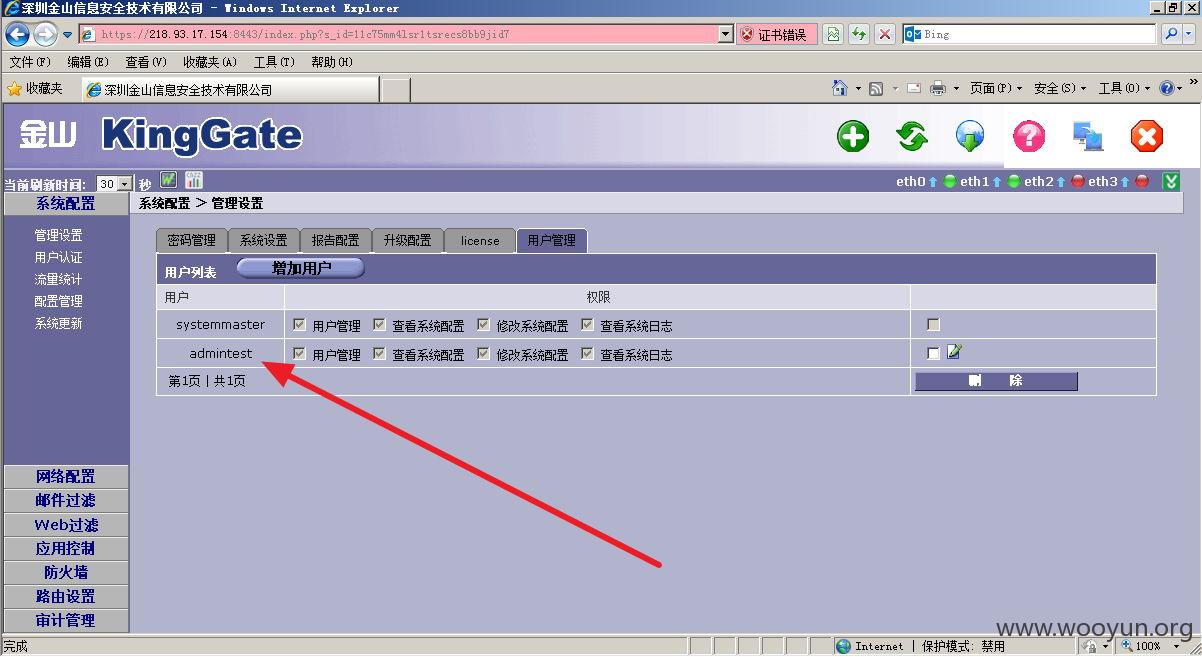
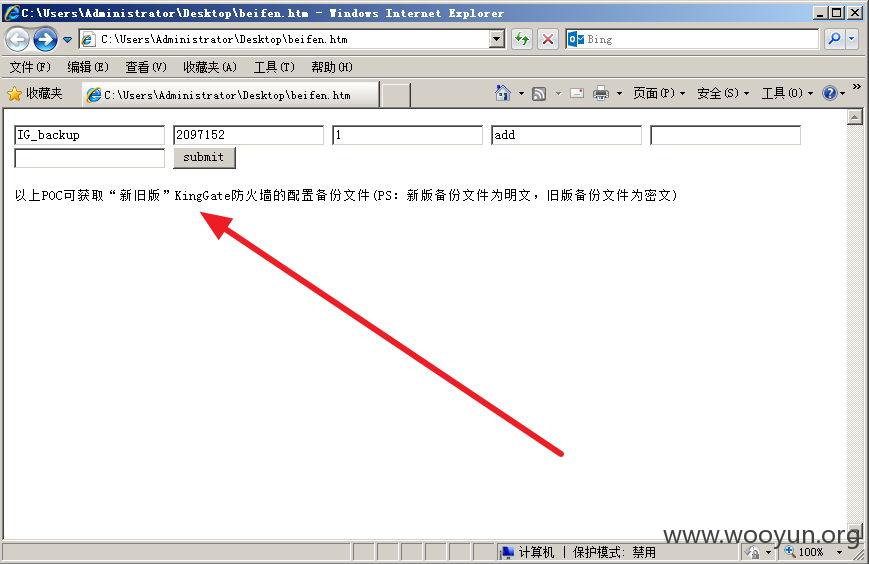
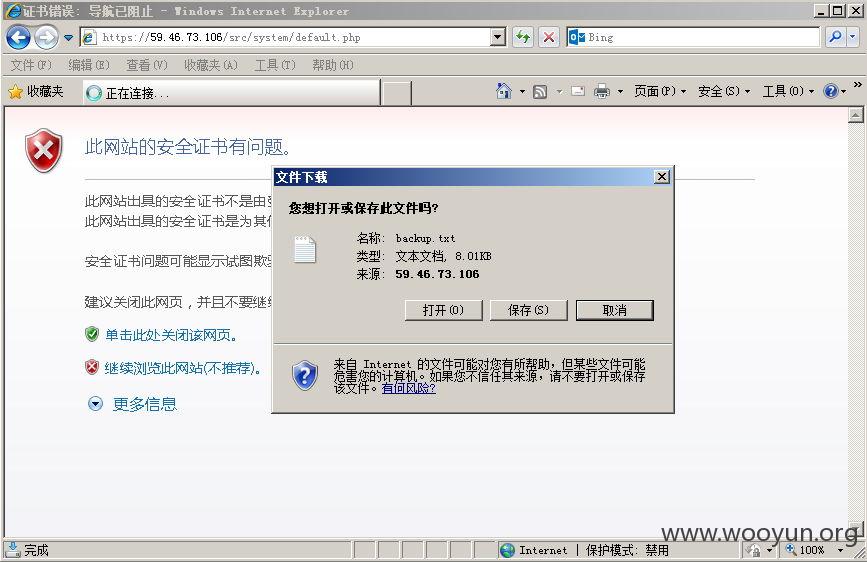
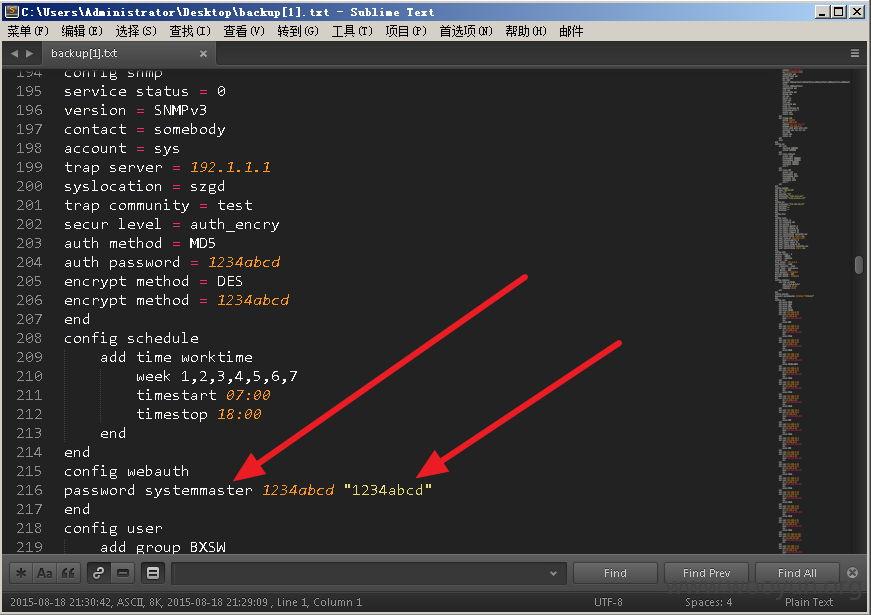
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-08-19 16:21
厂商回复:
非常感谢提交!马上跟进
最新状态:
暂无











