漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0132411
漏洞标题:奥鹏教育网络学习云平台多处SQL注入(POST)
相关厂商:open.com.cn
漏洞作者: 路人甲
提交时间:2015-08-07 17:00
修复时间:2015-09-21 17:36
公开时间:2015-09-21 17:36
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-07: 细节已通知厂商并且等待厂商处理中
2015-08-07: 厂商已经确认,细节仅向厂商公开
2015-08-17: 细节向核心白帽子及相关领域专家公开
2015-08-27: 细节向普通白帽子公开
2015-09-06: 细节向实习白帽子公开
2015-09-21: 细节向公众公开
简要描述:
刚才提交的说重复,请审核的管理员看看,这次提交的四处SQL注入点,是不是全部重复,如果都重复,我在提交新的注入点,这就是我孜孜不倦的精神。
详细说明:
话不多说。
漏洞证明:
奥鹏教育网络学习云平台4处SQL注入(POST)(不知这四处注入点是否和平台已有全部重复,麻烦审核人员了)
http://os.open.com.cn/
提交的POST数据如下:
注入点1(realName):
注入点2(titleCode):
注入点3(educationCode):
注入点4(userName):
使用SQLMAP测试,结果包含7个数据库:
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
available databases [7]:
[*] DBExchange
[*] master
[*] model
[*] msdb
[*] Open2u
[*] Open2U_Publish
[*] tempdb
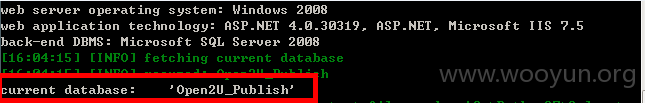
当前数据库为Open2U_Publish:
Open2U_Publish数据库包含76个表:
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
Database: Open2U_Publish
[76 tables]
+-------------------------------+
| Base_AdmissionsCategory |
| Base_Course |
| Base_CourseCategory |
| Base_CourseTeacher |
| Base_EducationalLevel |
| Base_ForeignLanguage |
| Base_Level |
| Base_OccupationalGroup |
| Base_StudyLength |
| Base_StudyWay |
| Base_Subject |
| Dic_CertificateType |
| Dic_Education |
| Dic_Nation |
| Dic_OrganizationType |
| Dic_Political |
| Dic_Subject |
| Dic_Title |
| Dic_UserType |
| EDU_StudyProgress |
| Edu_Announcement |
| Edu_AnnouncementLog |
| Edu_Batch |
| Edu_ChooseCourseWay |
| Edu_Class |
| Edu_CourseBulletin |
| Edu_DegreeBatch |
| Edu_DesgreeEnglish |
| Edu_DesgressApply |
| Edu_ExemptLearn |
| Edu_GraduateApply |
| Edu_GraduateInfo |
| Edu_GraduationBatch |
| Edu_ImportTask |
| Edu_SchoolRollChange |
| Edu_Semester |
| Edu_SignUp |
| Edu_SignUpBatch |
| Edu_StudentActive |
| Edu_StudentCourse |
| Edu_StudentCourseChangeBak |
| Edu_StudentEnrolment |
| Edu_StudentUpdateLog |
| Edu_TeachPlan |
| Edu_TeachPlanCourse |
| Exam_Batch |
| Exam_StudentGrade |
| Organization |
| Organization_Area |
| Organization_Relation |
| Organization_Station |
| Organization_University |
| Security_Function |
| Security_Manager |
| Security_Module |
| Security_OrganizationFunction |
| Security_Role |
| Security_RoleFunction |
| Security_Student |
| Security_Teacher |
| Security_User |
| Security_UserRole |
| Study_CourseBrowse |
| Study_Favorites |
| Study_Praise |
| Study_QuestionAnswer |
| Study_QuestionAnswerLocation |
| Sys_ImportOrExport |
| Temp_RollRegister |
| Temp_StudentStation |
| View_QuestionAnswerInfo |
| View_StudentCourseInfo |
| View_StudentEnrolmentInfo |
| View_StudentUserInfo |
| View_TeacherCourseInfo |
| View_UserQuestionAnswerInfo |
+-------------------------------+
随便看了下Security_Student表:
Database: Open2U_Publish
Table: Security_Student
[19 columns]
+---------------------+------------------+
| Column | Type |
+---------------------+------------------+
| Address | nvarchar |
| Birthday | datetime |
| CertificateNumber | nvarchar |
| CertificateTypeCode | nvarchar |
| Company | nvarchar |
| CreateTime | datetime |
| CreatorID | uniqueidentifier |
| Email | nvarchar |
| ID | uniqueidentifier |
| ModifierID | uniqueidentifier |
| ModifyTime | datetime |
| NationCode | nvarchar |
| PoliticalCode | nvarchar |
| PostCode | nvarchar |
| QQ | nvarchar |
| RealName | nvarchar |
| Sex | int |
| Status | int |
| Telephone | nvarchar |
+---------------------+------------------+
先提交再说,坐等审核。
修复方案:
你们说了算。
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2015-08-07 17:35
厂商回复:
新上的项目,我们会联系研发进行处理
最新状态:
暂无