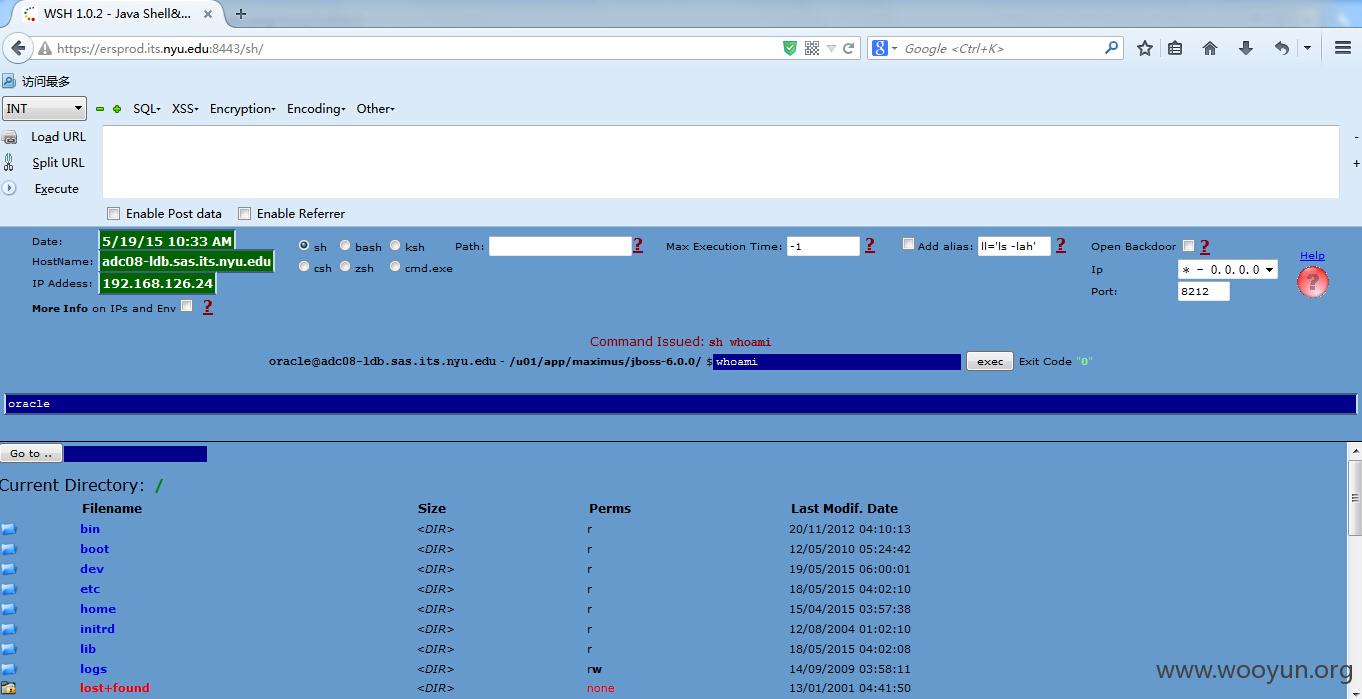
纽约大学(New York University),简称NYU,是一所位于美国纽约市的私立研究型大学;也是美国一座坐落于纽约心脏地带的世界顶尖名校。学校于1831年成立,今日已经成为全美国境内规模最大的私立非营利高等教育机构,在各类大学排名中均名列前茅,被列为新常春藤校之一。
# Do not remove the following line, or various programs
root:x:0:0:root:/root:/bin/bash
纽约大学(New York University),简称NYU,是一所位于美国纽约市的私立研究型大学;也是美国一座坐落于纽约心脏地带的世界顶尖名校。学校于1831年成立,今日已经成为全美国境内规模最大的私立非营利高等教育机构,在各类大学排名中均名列前茅,被列为新常春藤校之一。
# Do not remove the following line, or various programs
root:x:0:0:root:/root:/bin/bash