漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国电信某短信业务存在命令执行可getshell
提交时间:2015-04-24 16:27
修复时间:2015-06-12 09:58
公开时间:2015-06-12 09:58
漏洞类型:命令执行
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-04-24: 细节已通知厂商并且等待厂商处理中
2015-04-28: 厂商已经确认,细节仅向厂商公开
2015-05-08: 细节向核心白帽子及相关领域专家公开
2015-05-18: 细节向普通白帽子公开
2015-05-28: 细节向实习白帽子公开
2015-06-12: 细节向公众公开
简要描述:
中国电信挂机短信业务存在命令执行可getshell
详细说明:
中国电信挂机短信业务存在命令执行可getshell
站点:http://116.228.55.149:8082/helpdesk/privilege/loginAction!login2.action
st2 就不多说 写了个shell
shell地址:http://116.228.55.149:8082/helpdesk/jiushao.jsp jiushao 菜刀
敏感信息:
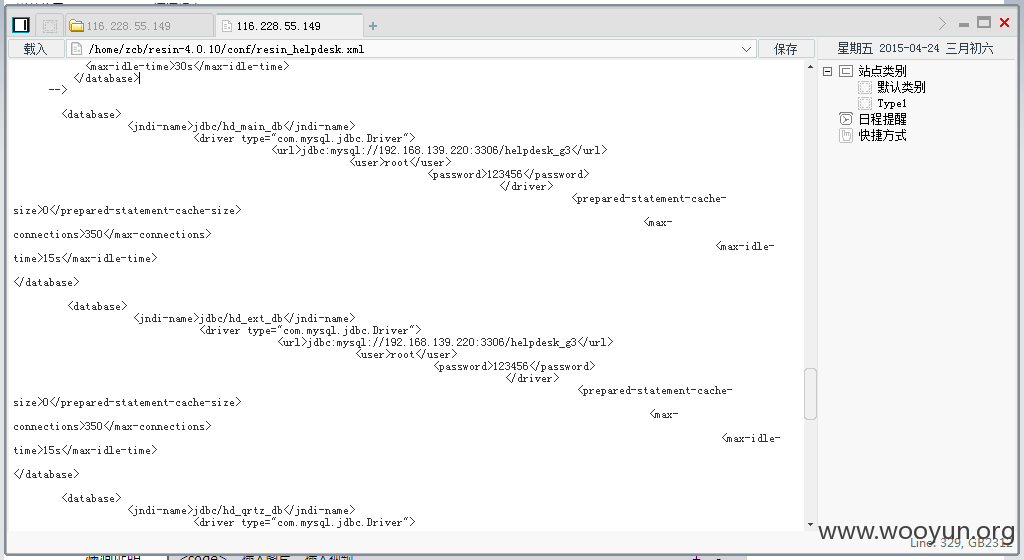
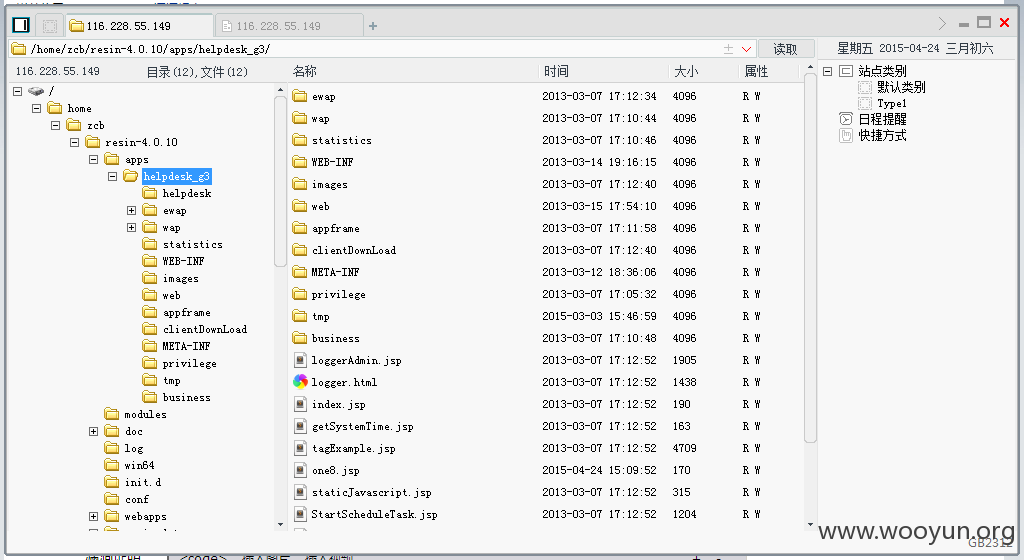
肯定有人问我为啥知道这是电信的业务 我只能说 从这来进去的 公司有账号 所以登陆就到st2地址了 。http://card.118114.net:8080/sdm/
漏洞证明:
中国电信挂机短信业务存在命令执行可getshell
站点:http://116.228.55.149:8082/helpdesk/privilege/loginAction!login2.action
st2 就不多说 写了个shell
shell地址:http://116.228.55.149:8082/helpdesk/jiushao.jsp jiushao 菜刀
敏感信息:


肯定有人问我为啥知道这是电信的业务 我只能说 从这来进去的 公司有账号 所以登陆就到st2地址了 。http://card.118114.net:8080/sdm/
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-04-28 09:57
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向中国电信集团公司通报,由其后续协调网站管理部门处置.
最新状态:
暂无




