漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0105398
漏洞标题:上海计生所存在SQL注入漏洞
相关厂商:cncert国家互联网应急中心
漏洞作者: Looke
提交时间:2015-04-03 12:45
修复时间:2015-05-23 08:18
公开时间:2015-05-23 08:18
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-03: 细节已通知厂商并且等待厂商处理中
2015-04-08: 厂商已经确认,细节仅向厂商公开
2015-04-18: 细节向核心白帽子及相关领域专家公开
2015-04-28: 细节向普通白帽子公开
2015-05-08: 细节向实习白帽子公开
2015-05-23: 细节向公众公开
简要描述:
上海市计划生育科学研究所(SIPPR)成立于1978年,隶属上海科学院,是由上海市政府与国家人口和计划生育委员会部市共建的社会公益类科研机构。自1983年起连续被世界卫生组织(WHO)确定为WHO人类生殖研究合作中心。研究所是“国家人口计生委计划生育重点实验室”、“上海市生殖健康药具工程技术研究中心”、“中国生育调节药物毒理检测中心”和“上海市计划生育与生殖健康研究会”等学术机构和团体的依托单位,其主要职责是:为落实人口政策和提高群众生殖健康水平提供技术支撑、为政府制定人口和计划生育相关政策提供决策咨询、为社会提供生殖健康行业服务和科普宣传等公共服务。
详细说明:
上海计生所登陆页面存在post注入:
===============================================================
================================================================
username参数存在SQL注入:
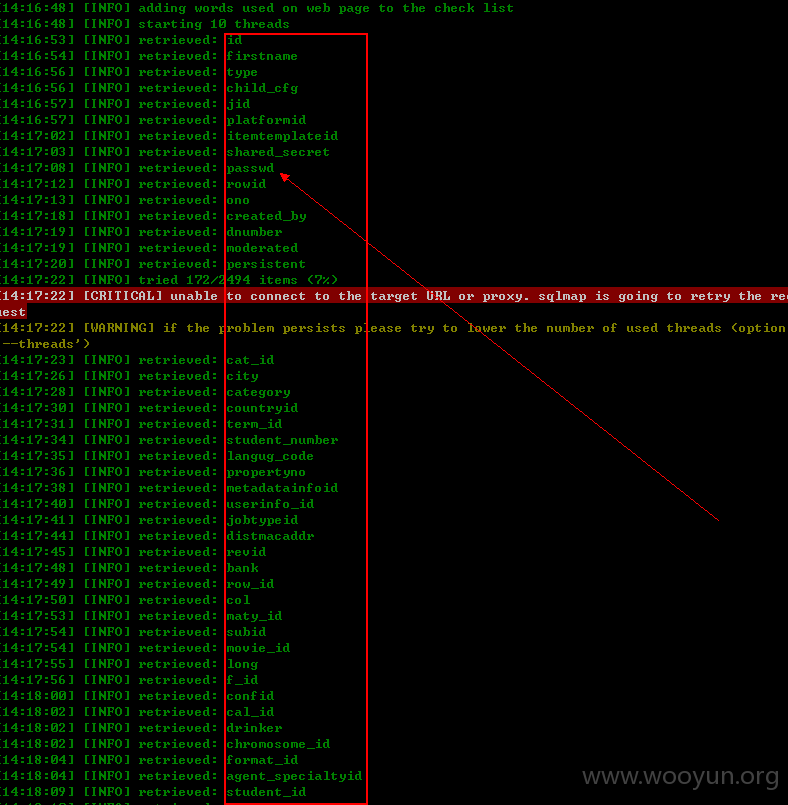
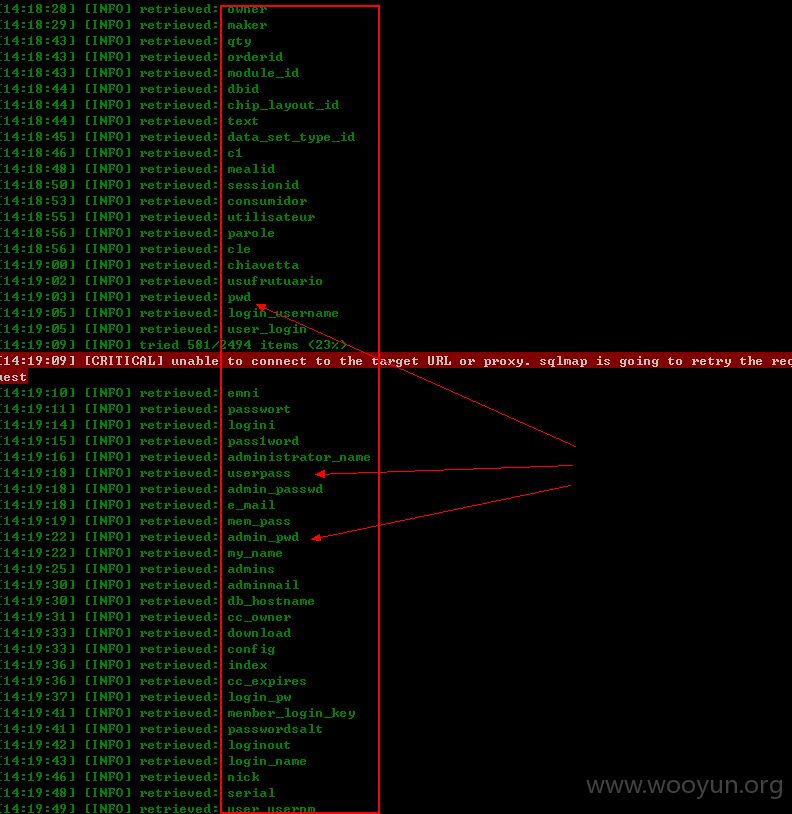
漏洞证明:
修复方案:
对参数进行严格过滤
版权声明:转载请注明来源 Looke@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-04-08 08:17
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给上海分中心,由其后续协调网站管理单位处置。
最新状态:
暂无