漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0104145
漏洞标题:TCL多分站多漏洞集合打包
相关厂商:TCL集团财务有限公司
漏洞作者: Taro
提交时间:2015-03-29 23:31
修复时间:2015-04-03 23:32
公开时间:2015-04-03 23:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-29: 细节已通知厂商并且等待厂商处理中
2015-04-03: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
rt...
详细说明:
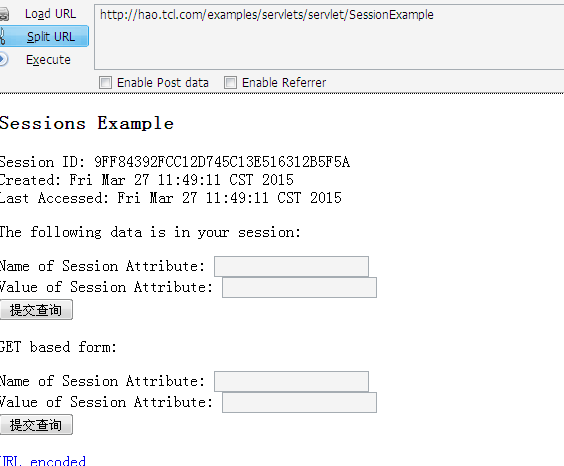
1.信息泄漏漏洞
TCL海外事业部
http://hao.tcl.com/examples/servlets/servlet/SessionExample
http://hao.tcl.com//examples/servlets/index.html
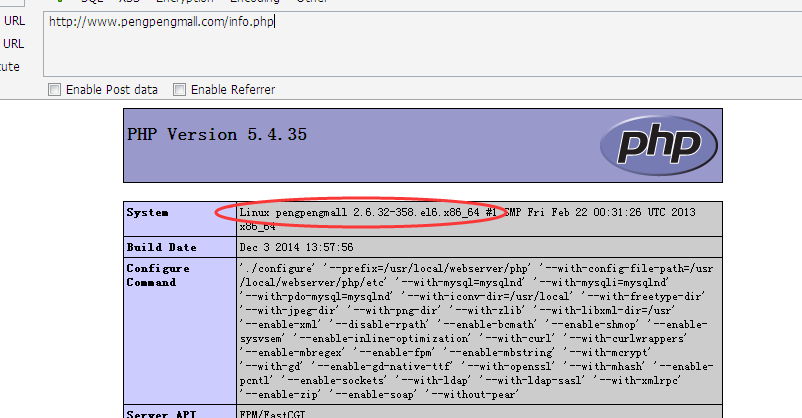
碰碰猫
http://www.pengpengmall.com/info.php
2.SQL注入
惠州TCL金能电池
http://battery.tcl.com//read_products.php?smname=1
http://battery.tcl.com/news_gs.php?offset=1
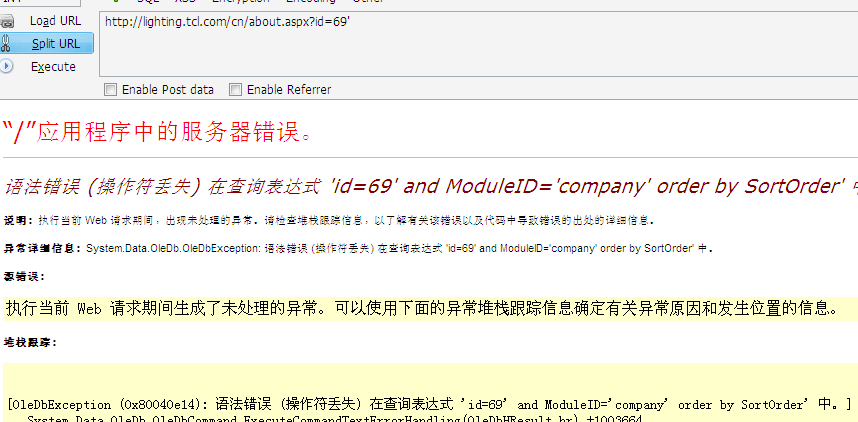
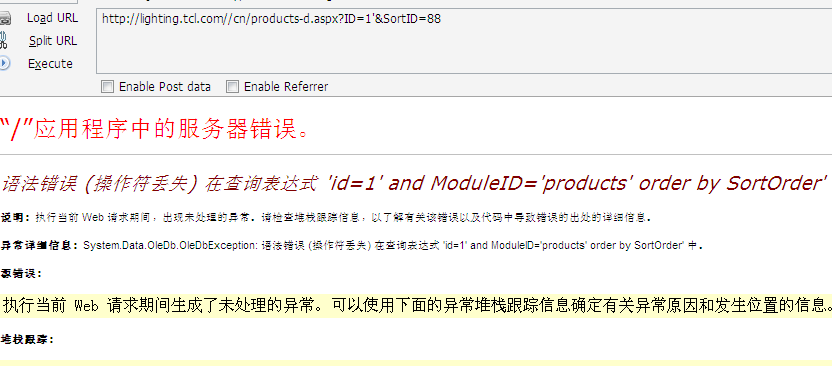
惠州TCL照明电器
http://lighting.tcl.com/cn/about.aspx?id=69
http://lighting.tcl.com//cn/products-d.aspx?ID=1'&SortID=88
TCL显示器(惠州)有限公司
http://www.tcldisplay.com/news/gb/listclass.asp?bigclassid=9
这里可以获取到管理员的账号密码,但是不小心搞得数据库连接出错,导致没法访问
http://www.tcldisplay.com/sortlist.asp?sortID=-1
http://www.tcldisplay.com/listclass.asp?ClassName=%B9%AB%CB%BE%B6%AF%CC%AC&SmallCID=12
http://www.tcldisplay.com/list.asp?ClassName=%B9%AB%CB%BE%B6%AF%CC%AC&ID=37%20AND%203*2*1%3d6%20AND%20360%3d360
漏洞证明:
修复方案:
版权声明:转载请注明来源 Taro@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-04-03 23:32
厂商回复:
最新状态:
暂无