漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0103021
漏洞标题:某建站程序三处SQL注入漏洞
相关厂商:百成网络
漏洞作者: 路人甲
提交时间:2015-03-24 11:06
修复时间:2015-05-08 11:08
公开时间:2015-05-08 11:08
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-24: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-05-08: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RT
详细说明:
第一处:
http://www.sookoo.cn/newShow.asp?ID=291
http://www.hb-lhyy.com/newShow.asp?ID=290
http://www.tatanchina.com/jituan/newShow.asp?ID=200
http://www.schneidersell.com/newShow.asp?ID=106
http://www.sjzslndx.com/newshow.asp?ID=230
http://www.lmtzjt.com/newshow.asp?ID=292
http://www.mmty.com.cn/newShow.asp?ID=265
http://www.ouyalighting.com/newShow.asp?ID=146
http://www.jintaoshiye.com/newShow.asp?ID=262
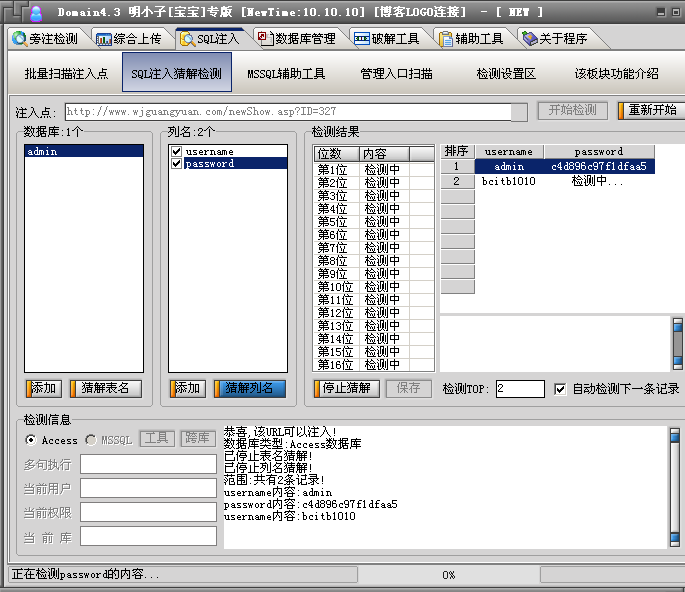
http://www.wjguangyuan.com/newShow.asp?ID=327
http://www.sxwhcbo.com/newshow.asp?ID=237
http://www.chaoguangnet.com/newShow.asp?ID=278
http://www.qmxjypx.com/newshow.asp?ID=289
http://www.tugaojiancai.com/newShow.asp?ID=320
http://www.hebheli.com/newShow.asp?ID=205
http://www.yktouzi.com/newshow.asp?id=279
http://www.maxiyays.com/newshow.asp?ID=267
http://www.hbzichuan.com/newShow.asp?ID=133
http://www.fkcyygs.com/newShow.asp?ID=288
http://www.xqccheb.com/newshow.asp?id=183
http://www.tszyqj.com/newshow.asp?ID=283
http://www.sjzdydz.com/newShow.asp?ID=171
第二处:
http://www.sookoo.cn/news.asp?BC=40
http://www.hb-lhyy.com/news.asp?BC=1
http://www.sjzslndx.com/news.asp?BC=1
http://www.lmtzjt.com/news.asp?BC=1
http://www.wygold9999.com/news.asp?BC=5
http://www.mmty.com.cn/news.asp?BC=38
http://jihua3502.com/news.asp?BC=38
http://www.wjguangyuan.com/news.asp?BC=48
http://www.qmxjypx.com/news.asp?BC=39
http://www.hongxudichan.com/news.asp?BC=17
http://www.tugaojiancai.com/news.asp?BC=38
http://www.chaoguangnet.com/news.asp?BC=38
http://www.yktouzi.com/news.asp?BC=38
http://www.maxiyays.com/news.asp?BC=38
http://www.fkcyygs.com/news.asp?BC=60
http://www.xqccheb.com/news.asp?BC=43
http://www.tszyqj.com/news.asp?BC=38
http://www.hbzichuan.com/news.asp?bc=1
http://www.sjzdydz.com/news.asp?BC=1
http://huian.w221-e1.ezwebtest.com/news.asp?BC=38
http://www.hbjxzj.com/news.asp?BC=69
http://www.tsxdzzyjd.com/news.asp?BC=46
第三处:
http://www.mmty.com.cn/product.asp?BC=22
http://jihua3502.com/product.asp?BC=82
http://www.ouyalighting.com/product.asp?BC=22
http://www.jintaoshiye.com/product.asp?BC=80
http://www.wjguangyuan.com/product.asp?BC=49
http://www.qmxjypx.com/product.asp?BC=44
http://www.chaoguangnet.com/product.asp?BC=80
http://www.tugaojiancai.com/product.asp?BC=80
http://www.hebheli.com/product.asp?BC=23
http://www.yktouzi.com/product.asp?BC=22
http://www.xqccheb.com/product.asp?BC=29
http://www.maxiyays.com/product.asp?BC=22
http://www.fkcyygs.com/product.asp?BC=22
http://www.sjzdydz.com/product.asp?BC=23
http://www.tszyqj.com/product.asp?BC=39
http://www.hbjxzj.com/product.asp?BC=70
http://www.tsxdzzyjd.com/product.asp?BC=38
http://www.hbhengjinxiangsu.com/product.asp?BC=51
http://www.sjz-zs.com/product.asp?BC=23
http://www.dayepowder.com/product.asp?BC=30
http://www.hebeijinwen.com/product.asp?BC=38
用SQLMAP直接死了。用萝卜头直接死了。,
用明小子把。
1.测试第一处:http://www.wjguangyuan.com/newShow.asp?ID=327
以上均可复现的。是一个asp程序。不要忽略。
漏洞证明:
修复方案:
参数过滤。
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝