漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0100794
漏洞标题:便利店365框架漏洞
相关厂商:中国联合网络通信有限公司辽宁省分公司
漏洞作者: 路人甲
提交时间:2015-03-12 16:15
修复时间:2015-04-26 16:16
公开时间:2015-04-26 16:16
漏洞类型:命令执行
危害等级:中
自评Rank:10
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-12: 细节已通知厂商并且等待厂商处理中
2015-03-17: 厂商已经确认,细节仅向厂商公开
2015-03-27: 细节向核心白帽子及相关领域专家公开
2015-04-06: 细节向普通白帽子公开
2015-04-16: 细节向实习白帽子公开
2015-04-26: 细节向公众公开
简要描述:
详细说明:
通过一个小漏洞,发现邮箱,然后登录进了网站,余额竟然还有2w多
网址:http://www.bld365.com/
存在Struts 2漏洞,查看配置文件,用的dubbo,根本不懂,只看到一个smtp的账号密码,
<bean id="mailSender" class="org.springframework.mail.javamail.JavaMailSenderImpl">
<property name="host" value="smtp.ym.163.com"/>
<property name="username" value="[email protected]"/>
<property name="password" value="123gogogo"/>
</bean>
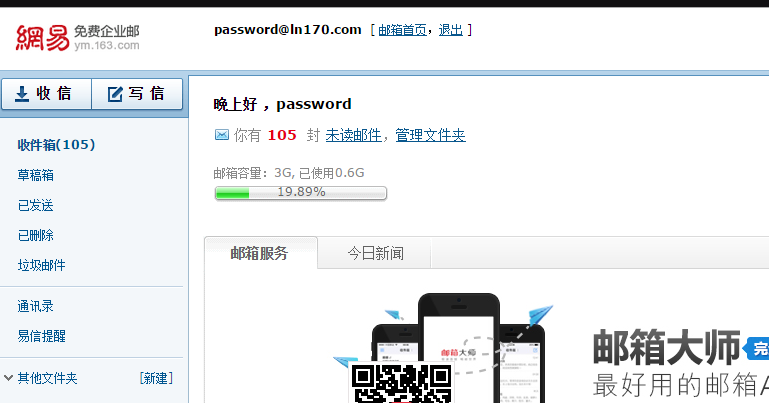
是163的企业邮箱,登录尝试:
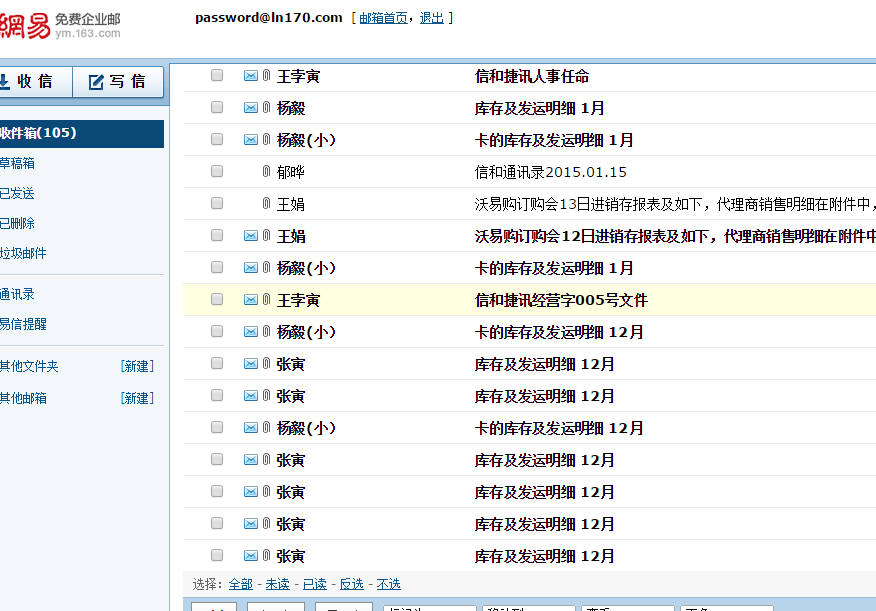
居然成功了,还有许多联系方式,入库出库清单
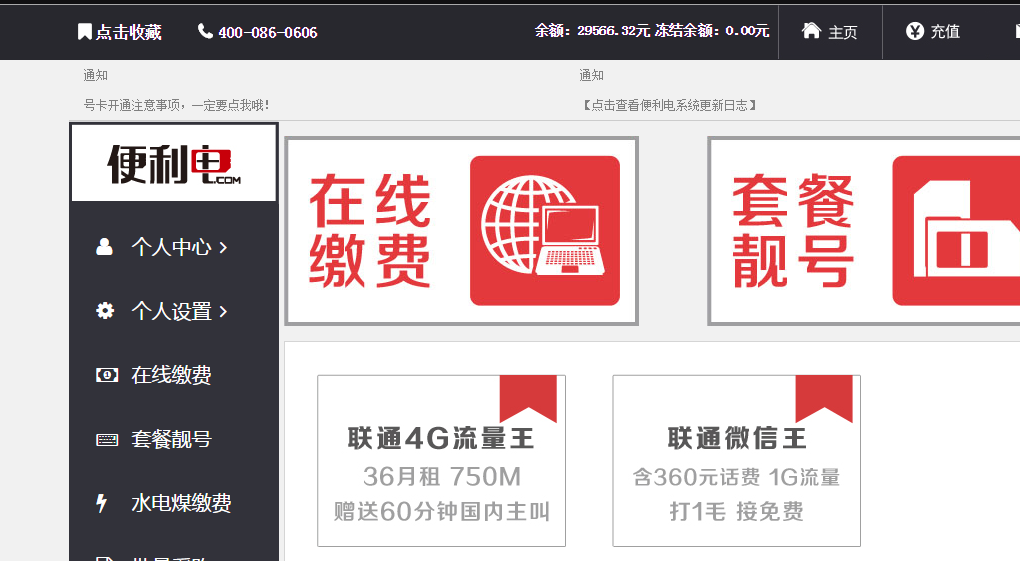
利用此密码,尝试登录网站,账号 admin 密码 123gogogo
登录成功,并且余额还有29566.32 接近三万块钱
看了看系统,发现充值还需要一个充值密码,但在系统中看到这样一个请求
http://www.bld365.com/ajax/getMemberInfo.action?temp=1426082592354
返回的数据中有两个md5加密的密码。
界面,然后就可以任意充值手机话费了。。。
漏洞证明:
网址:http://www.bld365.com/
存在Struts 2漏洞,查看配置文件,用的dubbo,根本不懂,只看到一个smtp的账号密码,
<bean id="mailSender" class="org.springframework.mail.javamail.JavaMailSenderImpl">
<property name="host" value="smtp.ym.163.com"/>
<property name="username" value="[email protected]"/>
<property name="password" value="123gogogo"/>
</bean>
是163的企业邮箱,登录尝试:
居然成功了,还有许多联系方式,入库出库清单
利用此密码,尝试登录网站,账号 admin 密码 123gogogo
登录成功,并且余额还有29566.32 接近三万块钱
看了看系统,发现充值还需要一个充值密码,但在系统中看到这样一个请求
http://www.bld365.com/ajax/getMemberInfo.action?temp=1426082592354
返回的数据中有两个md5加密的密码。
界面,然后就可以任意充值手机话费了。。。
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-03-17 11:47
厂商回复:
CNVD确认所述情况,已经转由CNCERT下发给分中心,由其后续协调网站管理单位处置。
最新状态:
暂无