今天老师上课讲到ARP的原理,于是我把我的IP地址改成教室网关地址不知道有没有用.......
1.百度地图存在反射型XSS漏洞,但是被人利用,可以变成持久型XSS漏洞
2.存在XSS的连接
3.解码之后得到:
4.上面这个连接
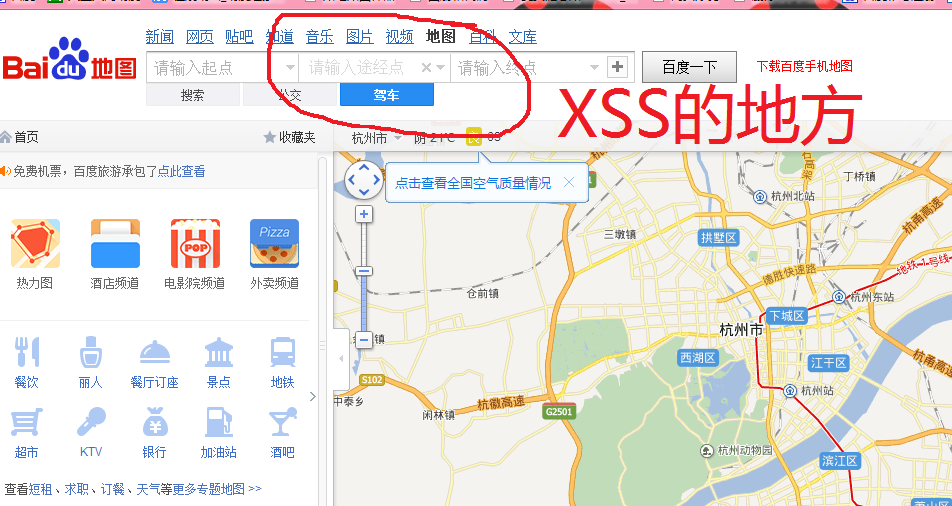
是在搜索驾车路线,添加中途地点那个位置,如图
5.这个地方如果直接在输入框添加代码,再点分享,会因为不存在这个地点出错,返回页面是空的,如图
(1)输入框输入字符串
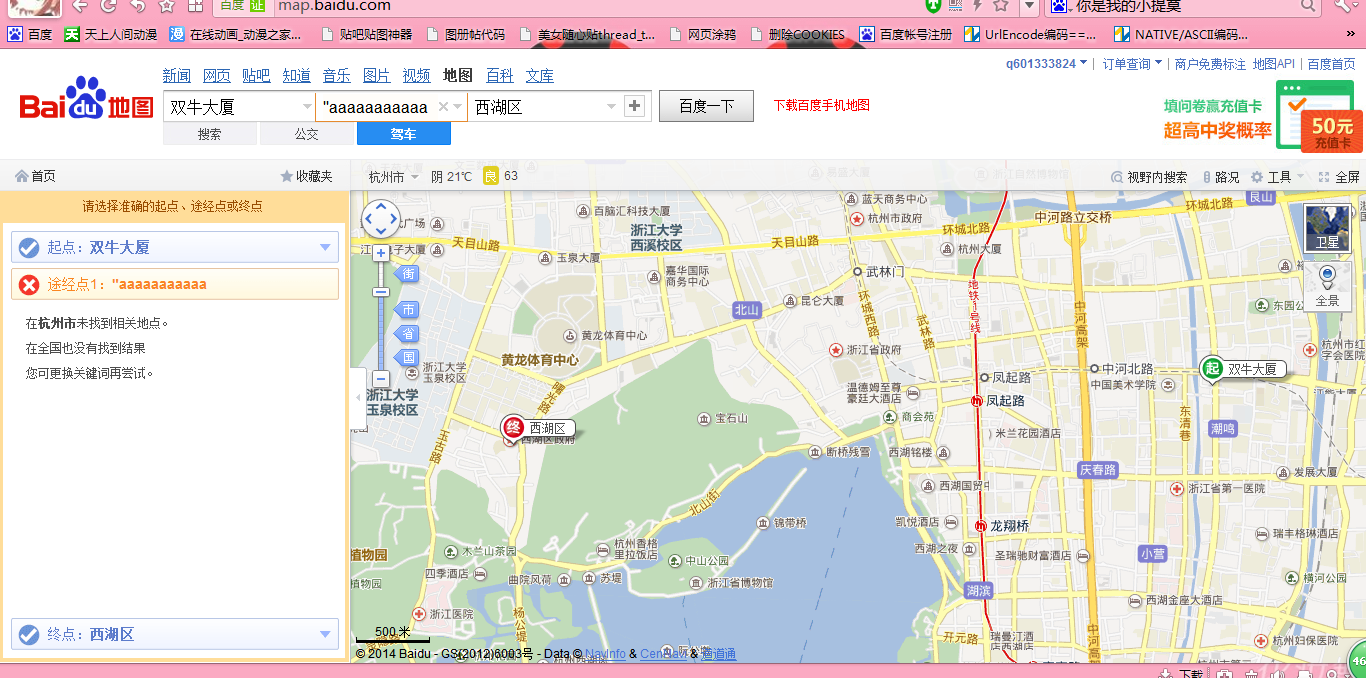
(2)分享返回页面因不存在这个地点所以清空了。
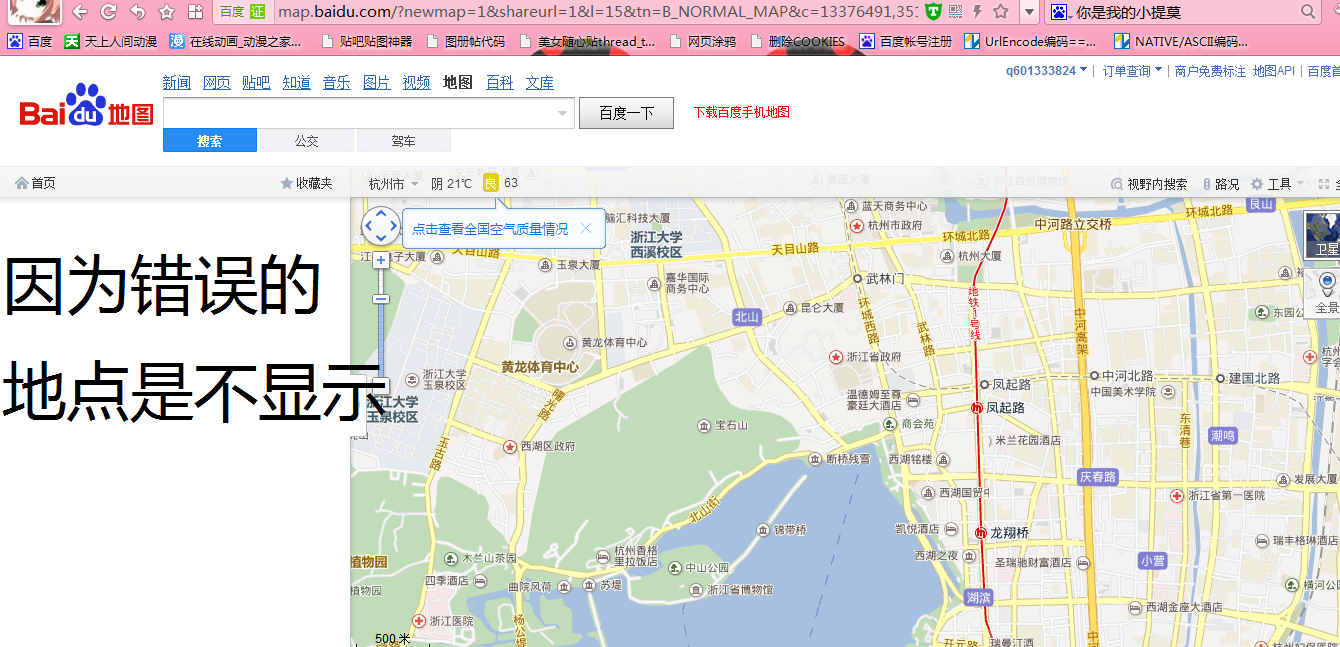
---------------------------------------------------------------------------------------
6.这个时候可以搜索正确的地点,然后修改参数就不会清空了,如图
(1)搜索正确并且存在的地点
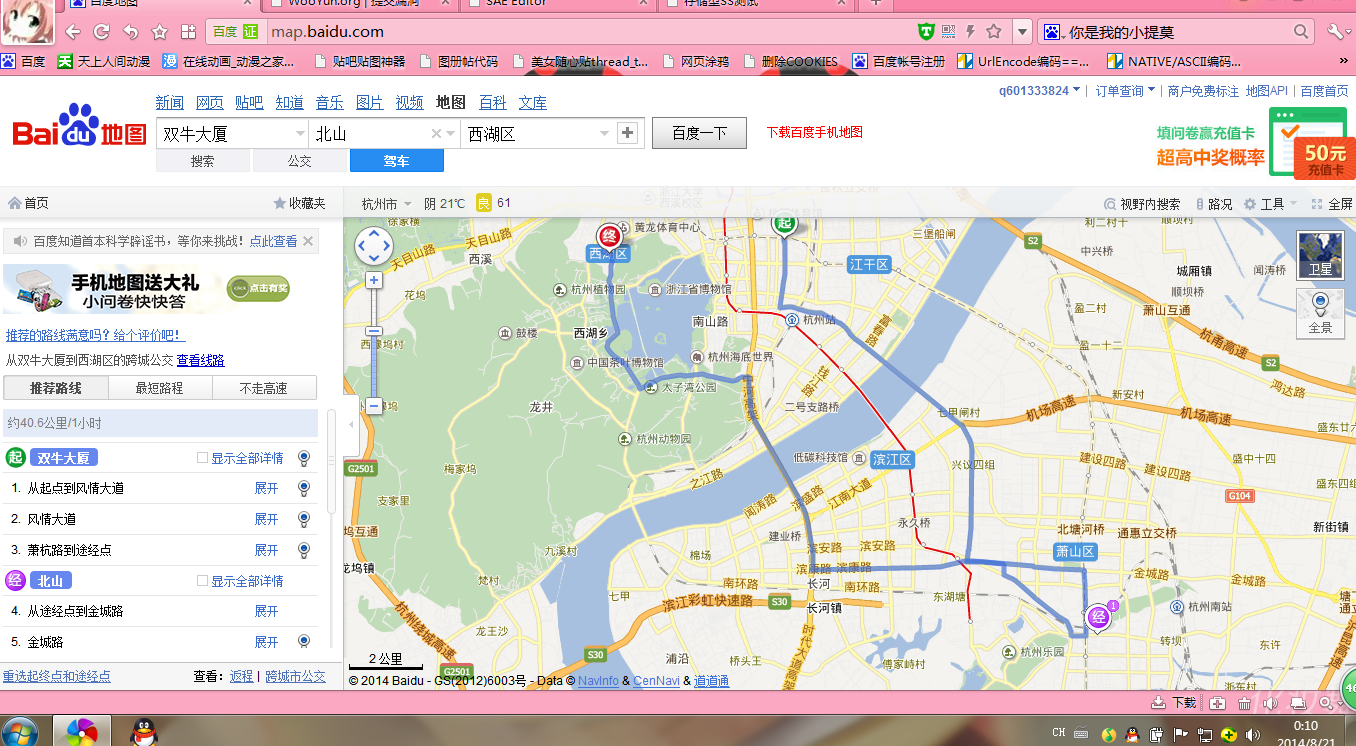
(2)然后点击
分享地点,得到连接
(3)然后把上面<!XSssssssssssssssS!>修改成XSS代码,就不会出现清空的情况了,如图
,这里的<span>标签没有对双引号过滤,存在XSS漏洞
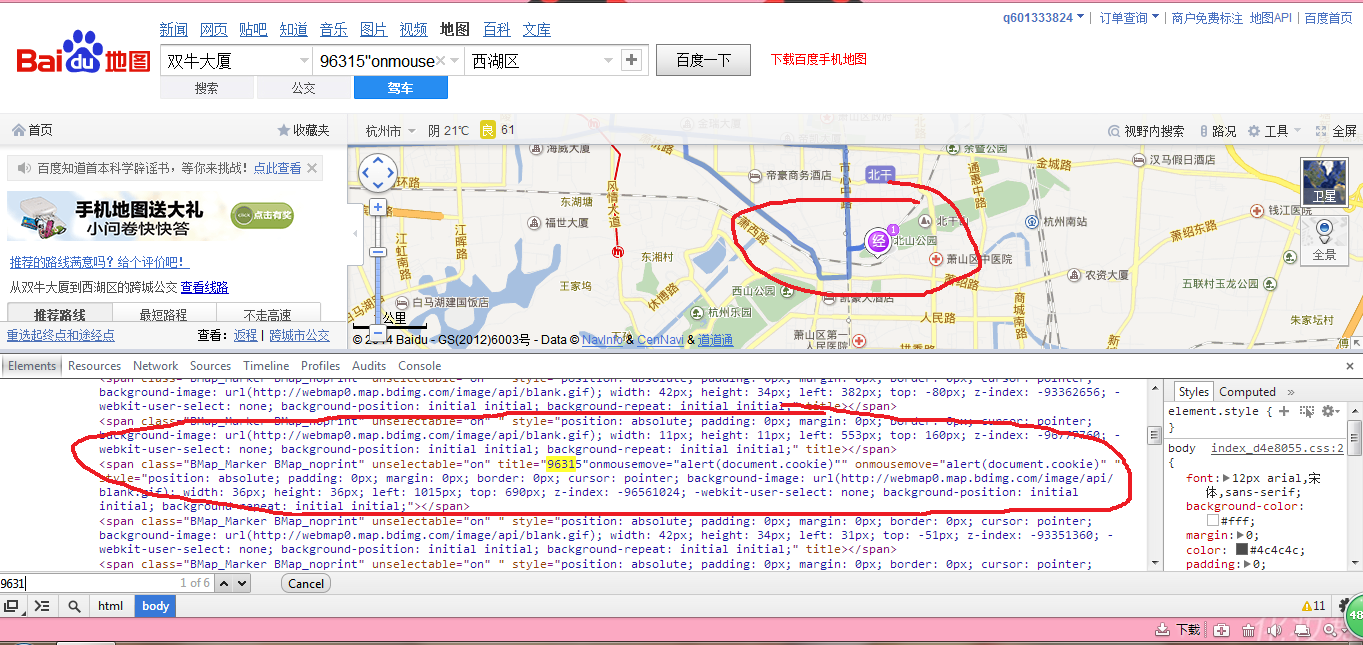
------------------------------------------------------------------------------------
7.我自己的猜测的是,那个连接会获取你输入框的地方坐标,当你输入的地方不存在的时候,获取不到坐标,返回错误,又设置了返回错误清空内容,所以我自己猜测,如果事先先填写个对的地方,获取坐标,然后再修改参数就不会有影响
那些$$$$之间的参数,大概是地图上的坐标(纯属猜测)
---------------------------------------------------------------------------------
9.和上次一样,存在=等于号,就清空,所以编码两次就不会清空
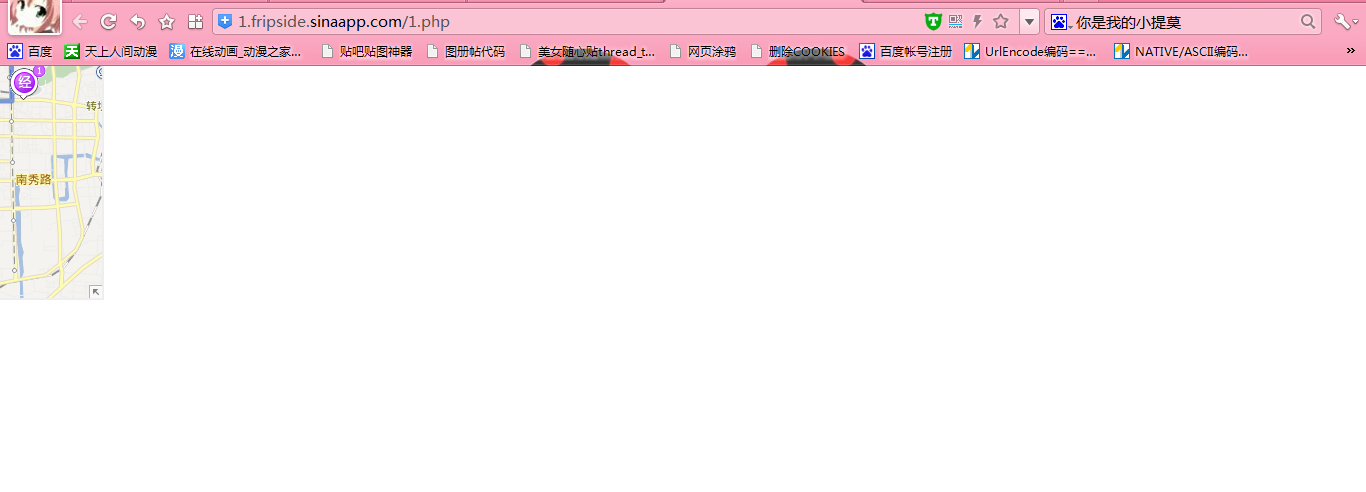
8.这个地方XSS,太小,一般人不会去注意,所以创建了两个网页,代码如下
(1)
第一段代码效果,如图:
(2)
配合第一个网页,第二段代码效果,如图:
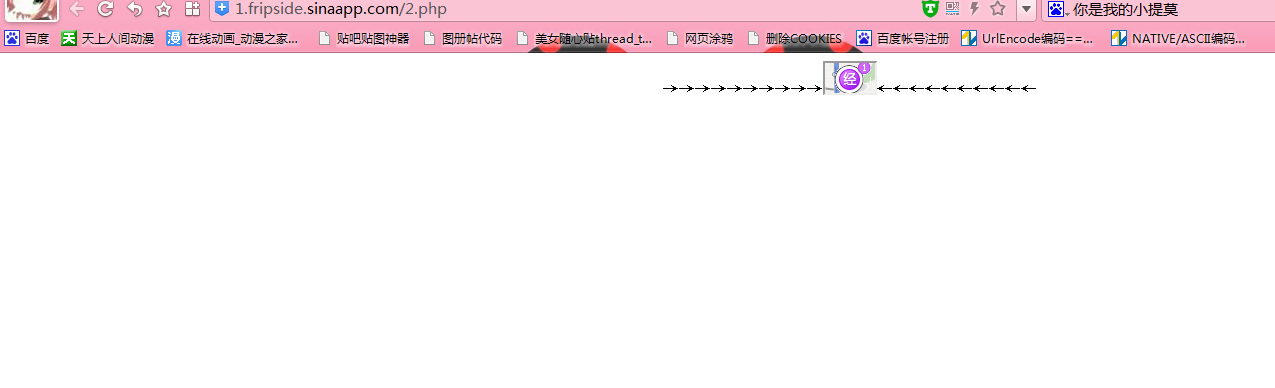
9.上面两个代码的,说简单点就是,第一个网页,调整XSS位置和大小。
第一个网页iframe设置了绝对位置,不能随便移动,但是可以第二个网页设置嵌入第一个网页,就可以随意调整位置
10.最终效果,可以访问这个连接看效果,我设置了滚动效果,可以被人挂在网站当按钮使用
11.最终效果图