#1 跨域数据劫持(csrf token formhash盗取)
下载远程附件功能不会对文件内容(文件格式)进行检测导致可以上传恶意的swf文件(扩展名还是图片扩展名),进而进行跨域数据劫持:
伪造图片CrossDomainDataHijack.jpg相关代码:
POC页面相关代码:
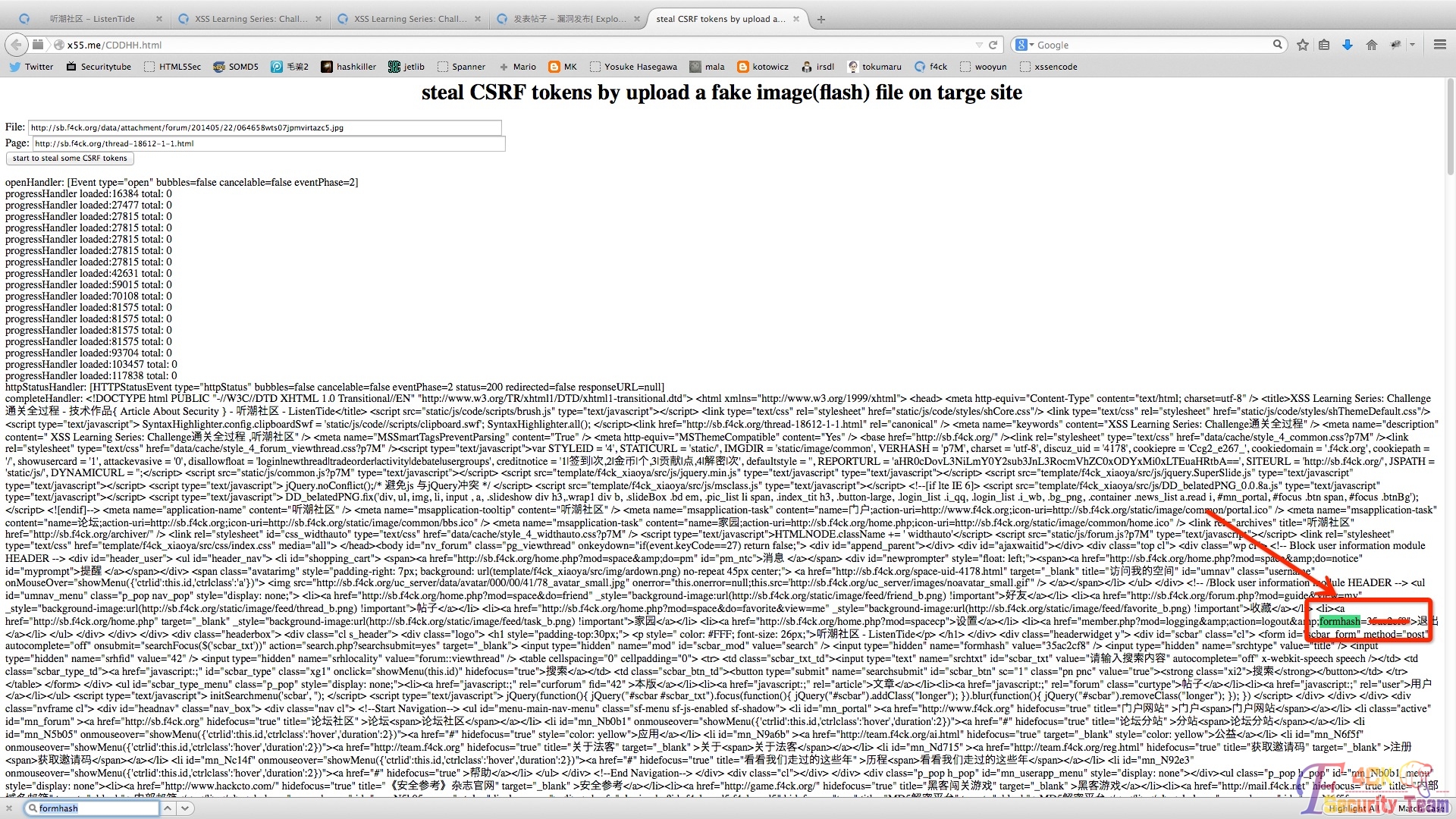
获取formhash截图:
#2
绕过附件类型限制用到的是上次有讲到的Hacking with Unicode上面的小trick。这个算BUG吧,算不上安全漏洞 起码暂时我还没能把它联系到漏洞上面。可以选择性修复:
测试:
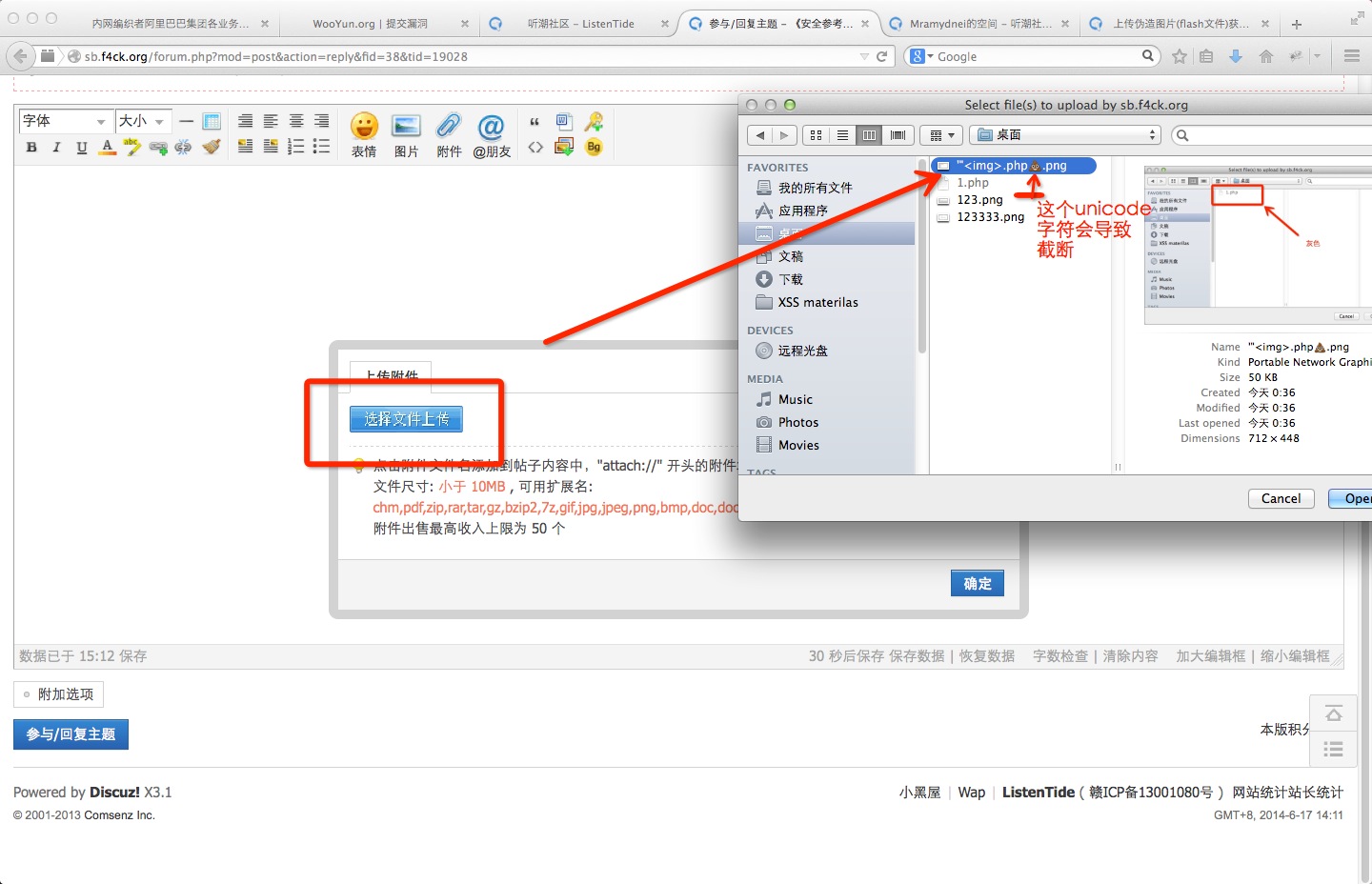
成功绕过: