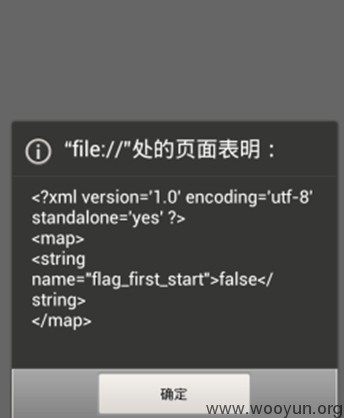
利用符号链接,可以绕过文件同源性策略的限制,调用com.qihoo.lightapp.WebAppFakeBrowserLightActivity组件解析执行特定的JavaScript脚本,可以窃取任意私有文件的内容。
具体利用可参考刚公布出来的firefox此类漏洞的利用,详细url参看: https://viaforensics.com/mobile-security/chained-vulnerabilities-firefox-android-pimp-browser.html
POC如下(借鉴x3xtxt的代码):